Emotet epoch 1 infection with Trickbot gtag mor84
Introduction
URLhaus is a great resource to check for malicious URLs associated with malware. I use it frequently to get a URL for a Word doc related to Emotet so I can generate a full chain of events for an Emotet infection. The flow chart for an Emotet infection looks like this:

Shown above: Flow chart for Emotet activity covered in this diary.
I generated an Emotet infection on Monday 2020-01-27. This diary reviews traffic and malware associated with the infection.
Of note, you might see the terms epoch 1, epoch 2, or epoch 3 associated with information about Emotet. Each "epoch" identifies a botnet distributing Emotet. Epochs 1, 2, and 3 each have their own infrastructure, so Windows executable files and Word documents associated with Emotet should fall under one of these three epochs.
You might also see the term gtag associated with Trickbot. This is a tag used by Trickbot to identify the campaign distributing this family of malware. Currently, gtags starting with mor identify Trickbot distributed through an Emotet infection. On Monday 2020-01-27, we saw gtag mor84 for this Trickbot campaign. On Tuesday 2020-01-28, we should see gtag mor85.
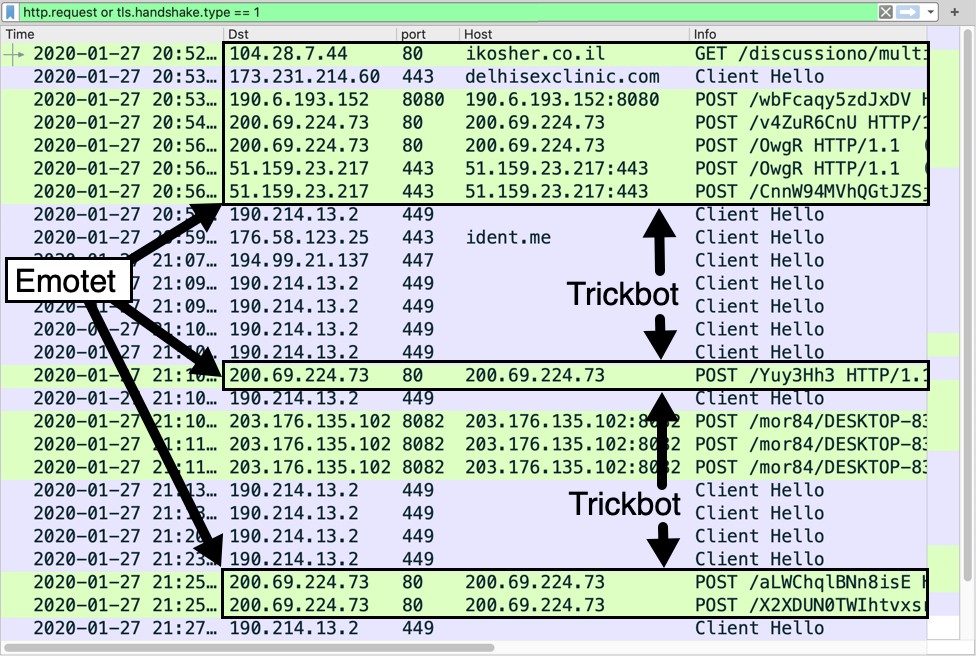
Infection traffic
I saw infection traffic typical of Emotet and Trickbot infections. For anyone who keeps tabs on Emotet, this should no suprise.
Indicators of compromise (IOCs)
The following are indicators from the Emotet and Trickbot infection I generated on Monday 2020-01-27:
HTTP request for the initial Word doc:
- 104.28.7[.]44 port 80 - ikosher.co[.]il - GET /discussiono/multifunctional-section/close-4hfy6o73iy-06x/383167265-j3LVOCu77d3B/
HTTPS traffic for Emotet binary after enabling Word macro:
- 173.231.214[.]60 port 443 (HTTPS traffic) - delhisexclinic[.]com - GET /zds/jUzItNFoNN/
Emotet post-infection traffic:
- 190.6.193[.]152 port 8080 - 190.6.193[.]152:8080 - POST /wbFcaqy5zdJxDV
- 200.69.224[.]73 port 80 - 200.69.224[.]73 - POST /v4ZuR6CnU
- 200.69.224[.]73 port 80 - 200.69.224[.]73 - POST /OwgR
- 51.159.23[.]217 port 443 - 51.159.23[.]217:443 - POST /OwgR
- 51.159.23[.]217 port 443 - 51.159.23[.]217:443 - POST /CnnW94MVhQGtJZSjR
- 200.69.224[.]73 port 80 - 200.69.224[.]73 POST /Yuy3Hh3
- 200.69.224[.]73 port 80 - 200.69.224[.]73 - POST /aLWChqlBNn8isE
- 200.69.224[.]73 port 80 - 200.69.224[.]73 - POST /X2XDUN0TWIhtvxsrt
Trickbot post-infection traffic:
- port 443 - ident[.]me - HTTPS traffic, IP address check caused by Trickbot (not inherently malicious)
- 190.214.13[.]2 port 449 - HTTPS traffic caused by Trickbot
- 194.99.21[.]137 port 447 - HTTPS traffic caused by Trickbot
- 203.176.135[.]102 port 8082 - 203.176.135[.]102:8082 - POST /mor84/[string with host name and other info]/81/
- 203.176.135[.]102 port 8082 - 203.176.135[.]102:8082 - POST /mor84/[string with host name and other info]/90
Malware info:
SHA256 hash: c963c83bc1fa7d5378c453463ce990d85858b7f96c08e9012a7ad72ea063f31e
- File size: 155,379 bytes
- File location: hxxp://ikosher.co[.]il/discussiono/multifunctional-section/close-4hfy6o73iy-06x/383167265-j3LVOCu77d3B/
- File name: Dat 2020_01_27 48060.doc
- File description: Word doc with macro for Emotet (epoch 1)
SHA256 hash: 006d5fda899149df4cc5d6d1b1ae52e9fcc4ade7541c1dd4391e0429d843b4d5
- File size: 356,475 bytes
- File location: hxxps://delhisexclinic[.]com/zds/jUzItNFoNN/
- File location: C:\Users\[username]\797.exe
- File location: C:\Users\[username]\AppData\local\[2- or 3-word combo]\[same 2- or 3-word combo].exe
- File description: Emotet malware binary (epoch 1)
SHA256 hash: dd20506b3c65472d58ccc0a018cb67c65fab6718023fd4b16e148e64e69e5740
- File size: 495,693 bytes
- File location: C:\ProgramData\[random alpha-numeric string].exe
- File location: C:\Users\[username]\AppData\Roaming\windirect\[Armenian text].exe
- File description: Trickbot gtag mor84
Final words
Overall no surprises here, but a reminder of this activity is useful for people who don't normally investigate Emotet or Trickbot infections. An up-to-date Windows host with the latest version of Microsoft Office should not succumb to these sorts of infections. To infect a vulnerable computer, people would have to click through various warnings, and they would also need to bypass many of the default security settings in recent versions of Windows 10.
A pcap of the infection traffic and the associated malware can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments
user@machine 09:13:04 ~> host ikosher.co.il
ikosher.co[.]il has address 104.28.6[.]44
ikosher.co[.]il has address 104.28.7[.]44
ikosher.co[.]il has IPv6 address 2606:4700:3036::681c[:]62c
ikosher.co[.]il has IPv6 address 2606:4700:3036::681c[:]72c
Anonymous
Jan 28th 2020
5 years ago