Scanning for Microsoft Exchange eDiscovery
Scanning for Microsoft Exchange eDiscovery
In the past week, I have notice more scans looking for the following Exchange URL over port 443: /ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application
What I have also noticed, all these scans for this URL are all from the same subnet (AS14061) DIGITALOCEAN-192-241-128-0.
This activity is likely linked to April Patch Tuesday (CVE-2021-28481) where "Also of significant note are the Microsoft Exchange Server Remote Code Execution vulnerabilities across versions 2013 - 2019. No known exploits are being reported however the CVSS score sits at 9.8, tread carefully. With a Critical rating, and a high CVSS score, those patches are worth reviewing in depth."[1]
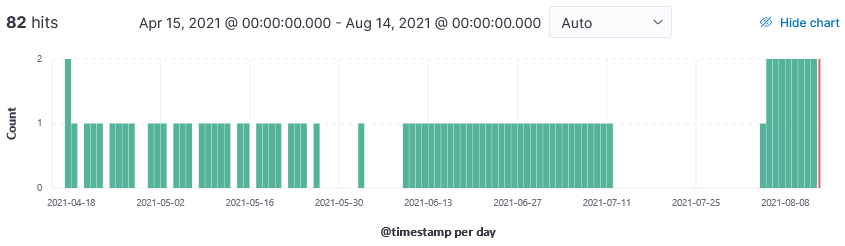
Based on this graph, these scans started almost immediately (17 April 2021) after April patch Tuesday and are still ongoing today.
Sample Log
20210812-170532: 192.168.25.9:443-192.241.216.240:48302 data
GET /ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application HTTP/1.1
Host: XX.XX.28.221
User-Agent: Mozilla/5.0 zgrab/0.x
Accept: */*
Accept-Encoding: gzip
Indicators of Compromise
192.241.128.0/17 → AS14061
Have you noticed an increase in scans for this URL?
[1] https://isc.sans.edu/forums/diary/Microsoft+April+2021+Patch+Tuesday/27306
[2] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-28481
[3] https://isc.sans.edu/forums/diary/Microsoft+Releases+Exchange+Emergency+Patch+to+Fix+Actively+Exploited+Vulnerability/27164
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
I reached-out to Digital Ocean to request they exclude our IP block but that did not seem to reduce these scans.
Anonymous
Aug 16th 2021
4 years ago
I reached-out to Digital Ocean to request they exclude our IP block but that did not seem to reduce these scans.
Anonymous
Aug 16th 2021
4 years ago