.rar Files and ACE Exploit CVE-2018-20250
Reader Carlos submitted an email with attached RAR file.
In the past, when you received a RAR file as attachment in an unexpected email, it often contained a single malicious Windows executable. For the infection to occur, one would have to open the attachment and double-click the executable.
Nowadays, a RAR file can also be an ACE exploit, like the popular CVE-2018-20250. Infection typically occurs by opening the attachment, and then restarting the computer or performing a logoff/logon cycle.
With oledump.py and plugin plugin_msg.py, one can inspect .msg files:
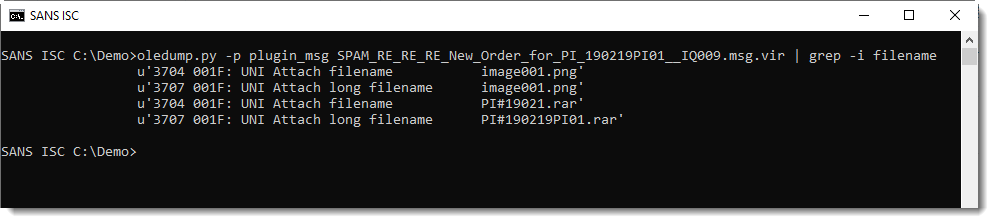
There's an attachment with extension .rar:
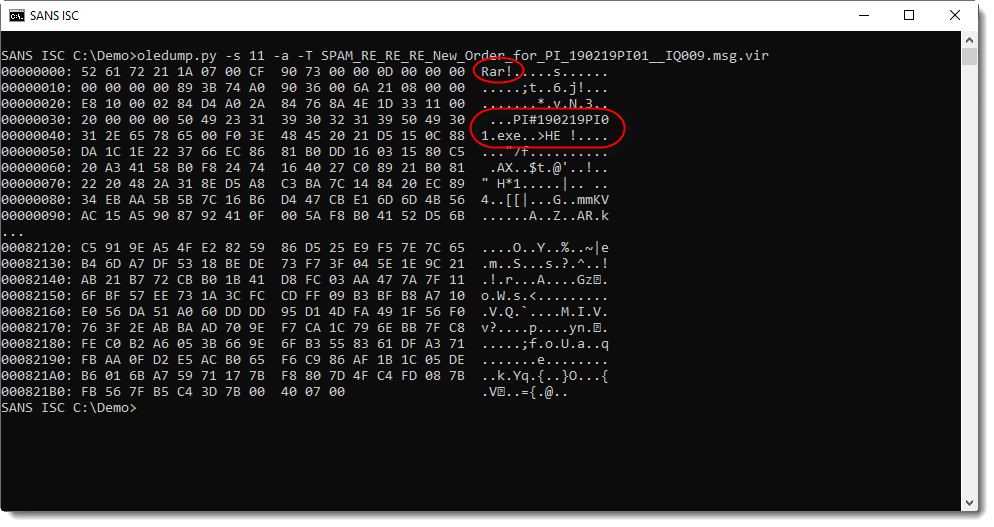
And it is indeed a RAR file containing an executable.
If it would be an ACE file masquerading as a RAR file (.rar extension in stead of .ace), one would see the following:
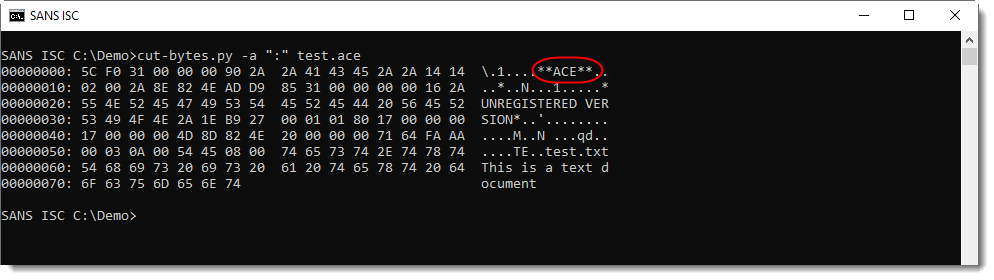
The binary data does not start with "Rar!", instead, one will see "**ACE**" a few bytes into the binary data.
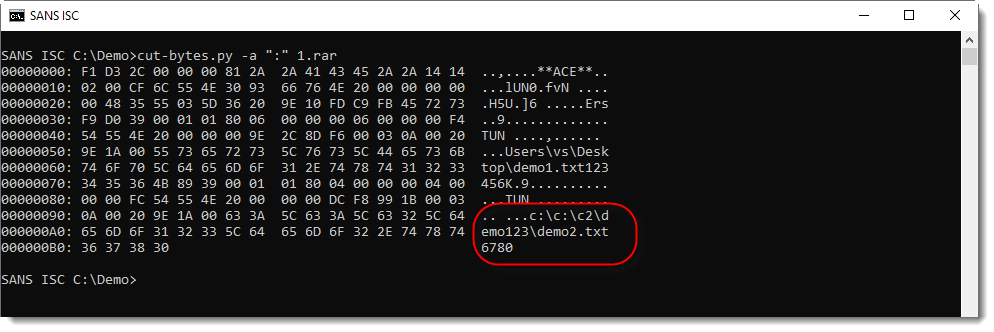
The example above is a normal ACE file. ACE files with a path traversal exploit will have an abnormal path stored in the ACE file:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments
Anonymous
Apr 22nd 2019
6 years ago