Yet another rogue anti-virus
Remember four years ago when the "Fake Codec" scam managed to infect even large corporations? The bad guys still try this approach every now and then, but their most successful "invention" to date is clearly the fake anti-virus. We've been covering it repeatedly for the past two, three years now, and still is going strong. If an attack vector stays the same for years, it can only mean one thing: It is netting the bad guys enough money that they don't feel the urge to innovate.
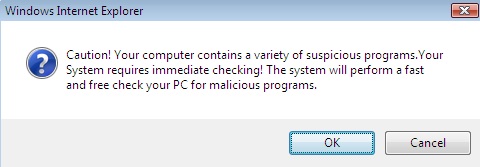
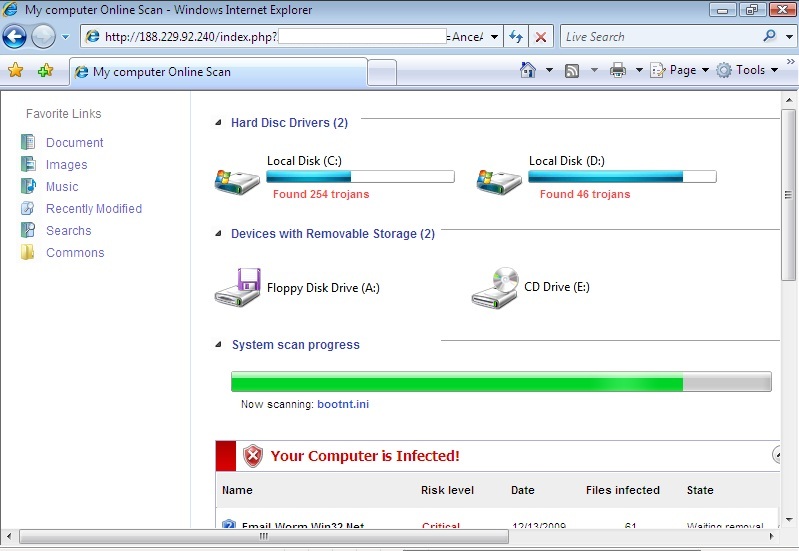
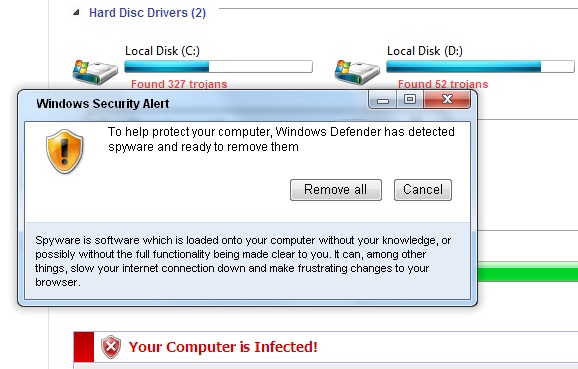
The following popped up earlier today when some readers surfed to a perfectly OK web site that had apparently been hacked and "amended". The site that seems to start the dive down the FakeAV rabbit hole at the moment is (dontclick!) baullka-dot-com/red.php . The goodies then come from 91.216.122.x which is known to provide unsolicited anti-virus "help". Another netblock involved - 188.229.88.x and 188.229.92.x - seems to be a recent addition to the FakeAV universe.
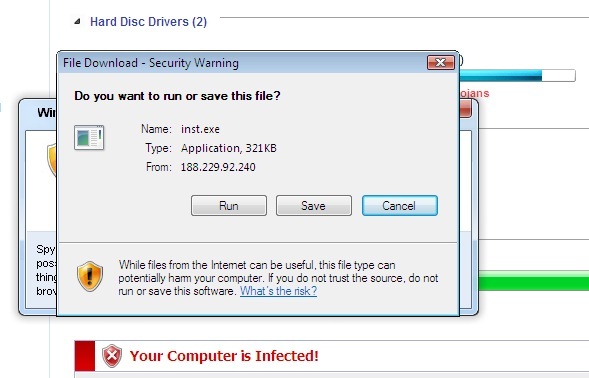
I'm including a couple screenshots below, it never hurts to know what the current incarnation of FakeAV looks like ... *especially* since their current EXE registers with a mere 6/43 on the Virustotal scale.
Stay safe!



Comments
M4tt
Jan 18th 2011
1 decade ago
KBR
Jan 18th 2011
1 decade ago
alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"ET CURRENT_EVENTS FAKEAV CryptMEN - Landing Page Download Contains .hdd_icon"; flow:established,to_client; content:".hdd_icon"; classtype:bad-unknown; sid:2011921; rev:1;)
alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"ET CURRENT_EVENTS FAKEAV CryptMEN - Random Named DeObfuscation JavaScript File Download"; file_data; content:"encrypt|3a| function|28|m, e, n|29|"; depth:64; classtype:bad-unknown; sid:2011922; rev:2;)
They usually use the name inst.exe but now they have changed it to pack.exe. This campaign is also tracked and net ranges are added to the RBN list. They typically buy out a /24 and rotate through the IP's in that /24 throughout the week/month.
Eoin Miller
Jan 19th 2011
1 decade ago