Weblogic Exploit Code Made Public (CVE-2018-2893)
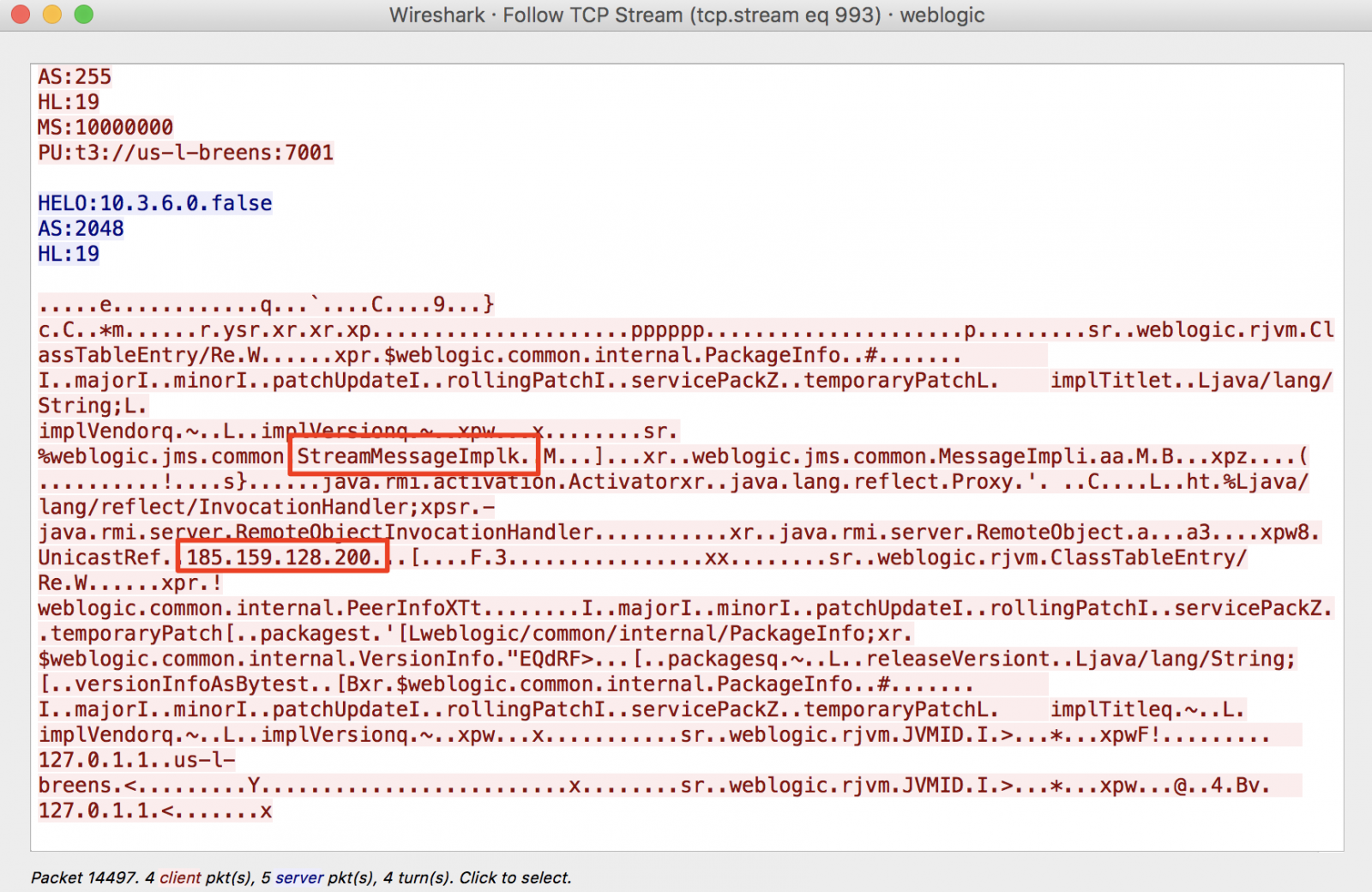
[UPDATE] We do see first exploit attempts. The exploit attempts to download additional code from 185.159.128.200 . We are still looking at details, but it looks like the code attempts to install a backdoor. The initial exploit came from 5.8.54.27.
Possible exploit code:
On 18-JUL-2018 Oracle released a Critical Patch Update (https://isc.sans.edu/forums/diary/Oracle+Critical+Patch+Update+Release/23886/) Yesterday exploit targeting CVE-2018-2893 impacting Oracle Weblogic Server appeared publicly.
Scanning activity targeting port 7001 peaked in May of 2018 when another Weblogic vulnerability went public, unsurprisingly it was used to install crypto miners then (https://isc.sans.edu/diary/WebLogic+Exploited+in+the+Wild+%28Again%29/23617)
Keywords: weblogic
0 comment(s)
×
![modal content]()
Diary Archives



Comments