Maldoc XLS Invoice with Excel 4 Macros
This week I got an email claiming to be a YellowPages invoice with an XLS attachment containing an Excel 4.0 macro which has similarity to [1][2].
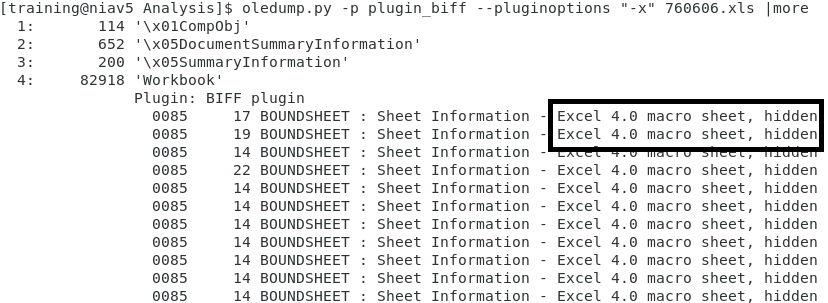
Using Didier's oledump.py tool, I checked the spreadsheet using plugin plugin_biff with option -x which show Excel 4 macros:
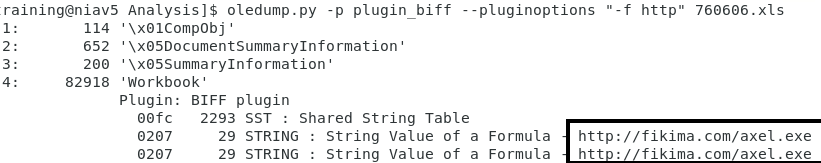
Next step will be to check for any embeded URL in this XLS document. I'm using plugin_biff's find option -f to see if any URL are embedded in this file:
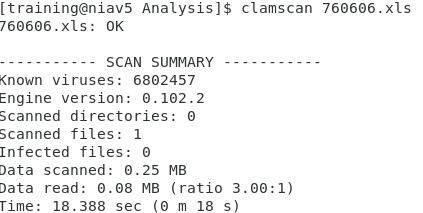
Unfortunately the embedded URL http[:]]//fikima[.]com/axel[.]exe was taken down soon after receiving this email [3]. I checked Virustotal hash database [4] and there are no record this file was submitted before the domain was taken down. As a final step, I scanned the file with ClamAV with negative results.
[1] https://isc.sans.edu/forums/diary/Maldoc+Excel+40+Macros/24750/
[2] https://isc.sans.edu/forums/diary/Malicious+Spreadsheet+With+Data+Connection+and+Excel+4+Macros/25880/
[3] https://urlhaus.abuse.ch/url/332764
[4] d5bd8d4a3841d0e6d455ba244be1f4d5 760606.xls
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu




Comments
Anonymous
Apr 6th 2020
5 years ago