MSG Files: Compressed RTF
Reader Salil asked for help with the analysis of a .MSG file. We talked about the analysis of .MSG files before, and Salil was able to use my oledump.py tool to look into the .msg file, but still had a problem finding URLs he knew were inside the email.
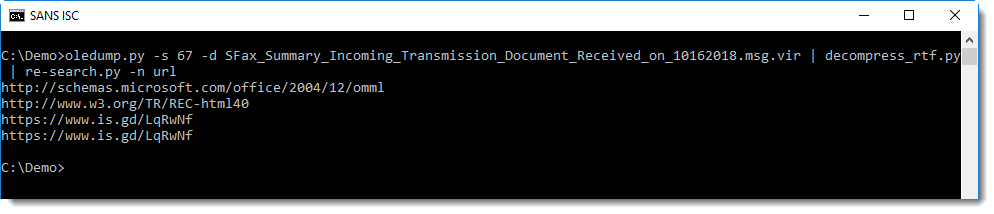
I took a look, and found the URLs inside compressed RTF.
Running oledump.py with the MSG plugin plugin_msg.py and grepping for string body allows me to find streams that (might) contain the message body:
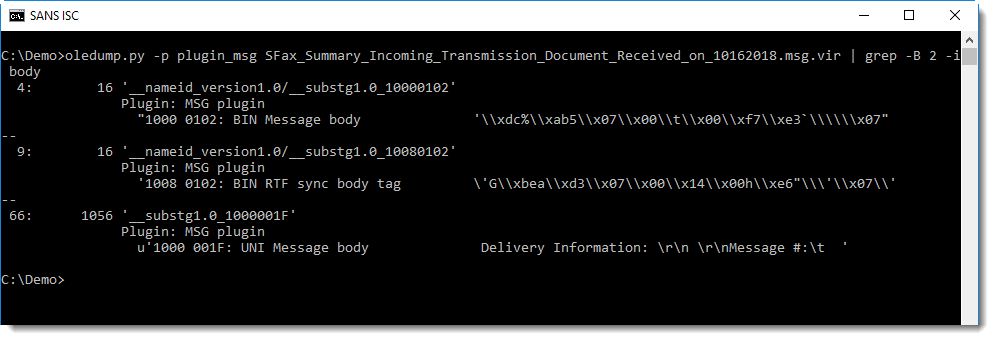
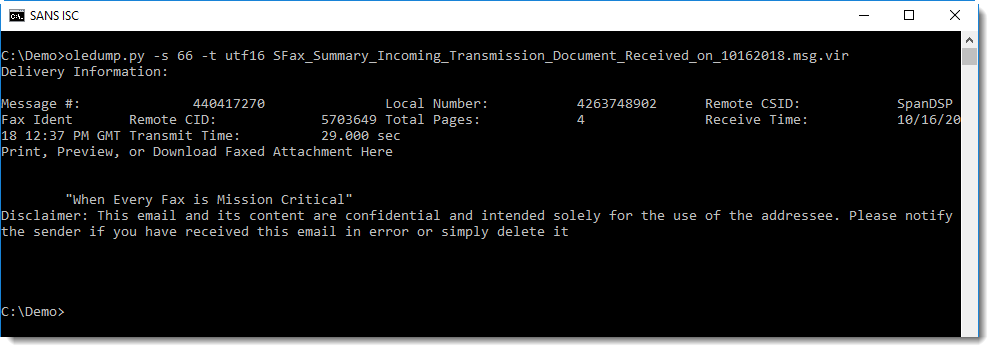
As Salil noted, stream 66 contains the message body, but without URLs:
Grepping with a bit more context reveals stream 67, also noticed by Salil:
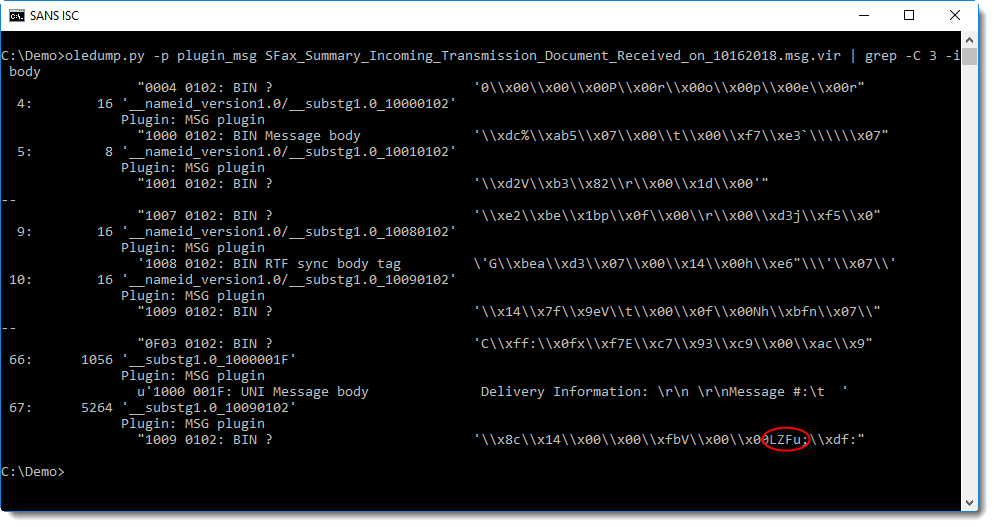
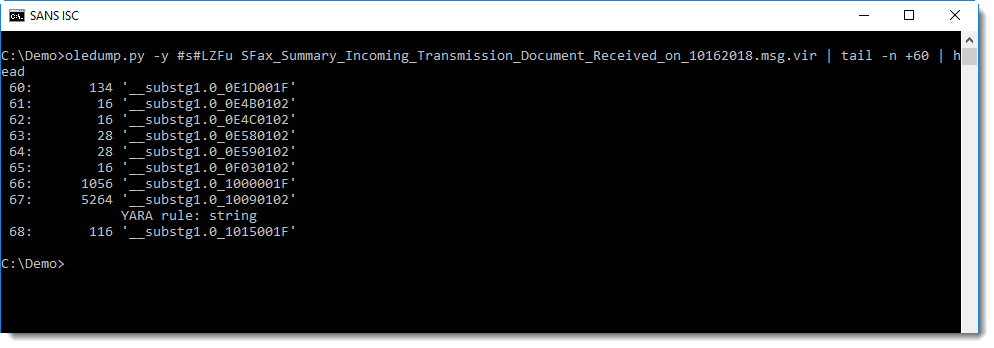
Notice the string LZFu at position 0x08 inside the stream: this indicates that this stream contains compressed RTF.
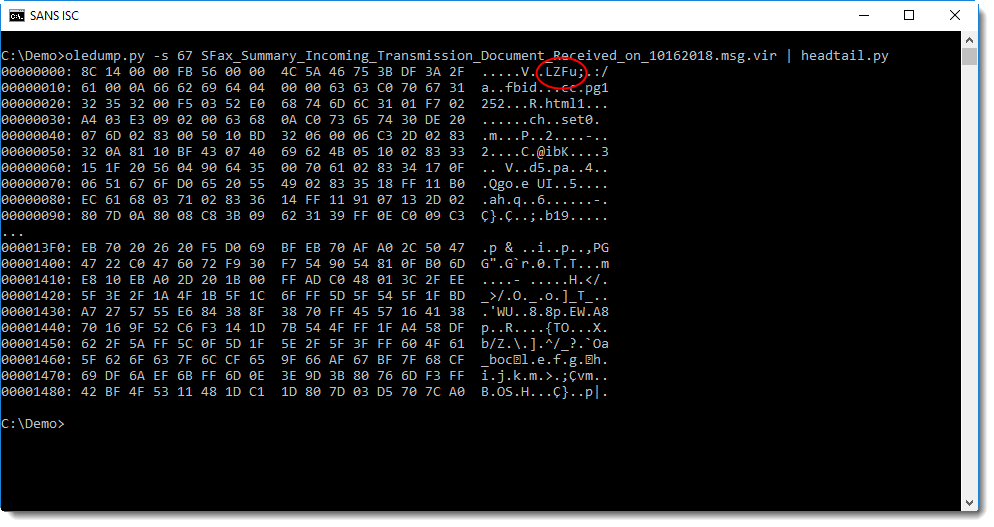
This stream can be decompressed with my new tool decompress_rtf.py, by dumping it and piping it into decompress_rtf.py:
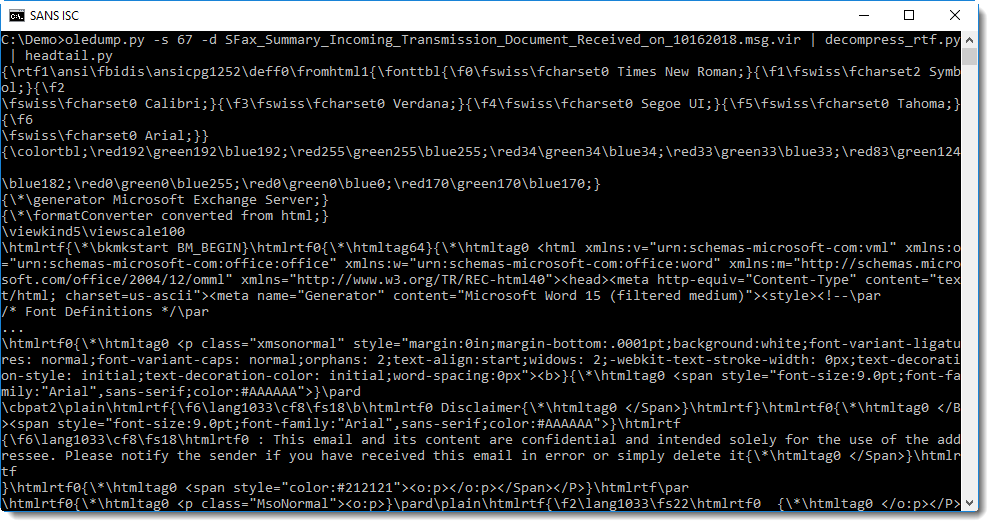
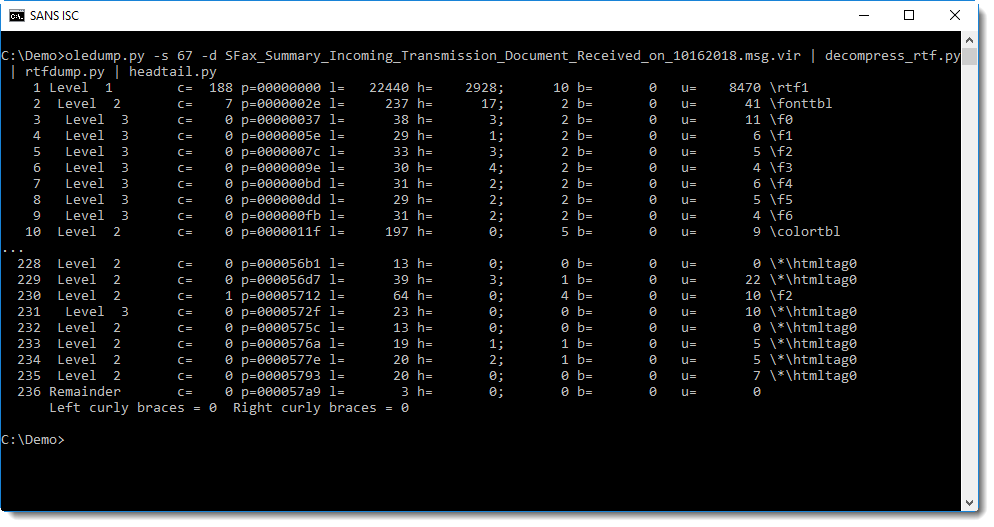
Piping this decompressed RTF file into rtfdump.py confirms that it is indeed a valid RTF document:
One way to extract the URLs, is too pipe the RTF document into my tool re-search.py with the URL regex:
To quickly check if a .MSG file contains compressed RTF, one can use an ad-hoc YARA rule to search for string LZFu:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments