Finding Metasploit & Cobalt Strike URLs
Metasploit and Cobalt Strike generate shellcode for http(s) shells. The URLs found in this shellcode have a path that consist of 4 random alphanumeric characters. But they are not completely random: their 8-bit checksum is a member of a small set of constants.
The 8-bit checksum is the sum of the ASCII value of the 4 characters of the path. Take the least significant byte of the sum, and compare it with this table:
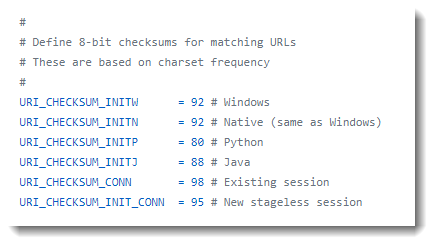
If the checksum is equal to one of these values, the URL could be generated by Metasploit or Cobalt Strike.
I illustrate this with Brad's capture file of Qakbot & Cobalt Strike traffic and my tool metatool.py.
Wireshark's command-line tool tshark is what I used to produce a complete packet tree for each packet. The URLs we are looking for will be somewhere in this output:
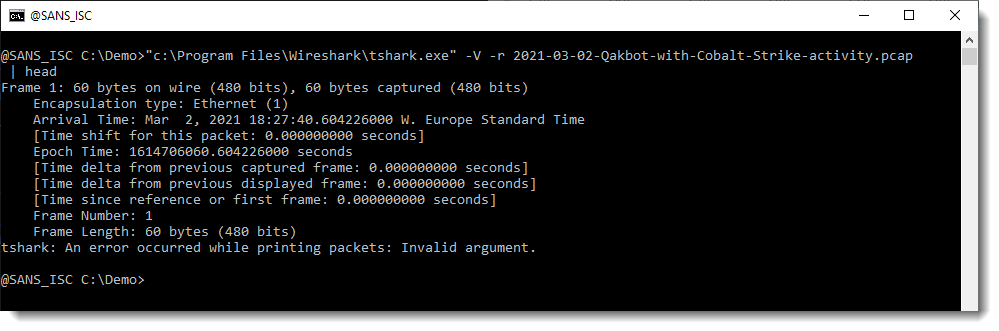
And then I pipe this output into my metatool.py with command url8:
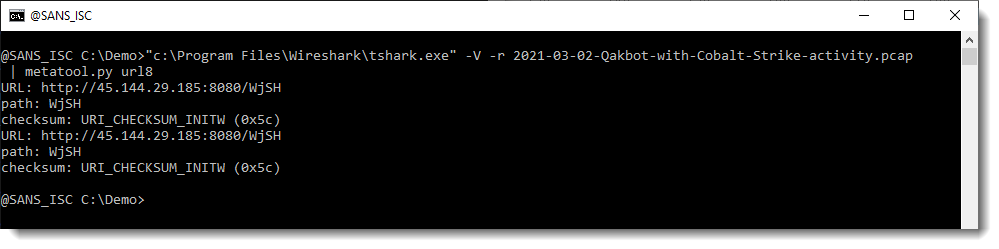
metatool found 2 (identical) URLs whose path has an 8-bit checksum equal to 0x5C (92), or URI_CHECKSUM_INITW, i.e. the 8-bit checksum for a Windows payload.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments
I also wonder why I'd be seeing queries on my web server for this sort of URL (rather than seeing them in squid proxy logs for users having been tricked into clicking on a malicious URL). I guess I should add that all my webserver replies for these are 404's of course! I'm not serving up malware.
It's such a simple check, though, I think I'll be adding it to my log analysis module for my log daemon (for the squid logs anyway - grin). Hmm. I also don't know why this reply says it's posted by "anonymous". I'm logged into ISC - it says "Welcome back, Brent" on the web page after all. :-)
Anonymous
Mar 16th 2021
4 years ago
Thanks
John
Anonymous
Mar 19th 2021
4 years ago