Another quickie: Discovering patterns in network traffic with silk
by Manuel Humberto Santander Pelaez (Version: 1)
When we perform a forensic analysis in network traffic, in some occasions we do not have major clues about what to look for and it is necessary to deepen the descriptive analysis and profiling of the obtained packages. One way to do this is with network flows, which are packets related to the same flow or connection saved into a single record. Some of the info that can be found in records are the following fields: source IP address, destination IP address, source port, destination port, Internet Control Message Protocol [ICMP] type/code (when appliable), transport protocol, bytes, packets in flow, accumulated TCP flags, start time, duration and end time.
Let's use an example. The following capture is suspected to have inside bittorrent traffic. First step is to convert pcap file intro network flows. We will use the rwp2yaf2silk command:
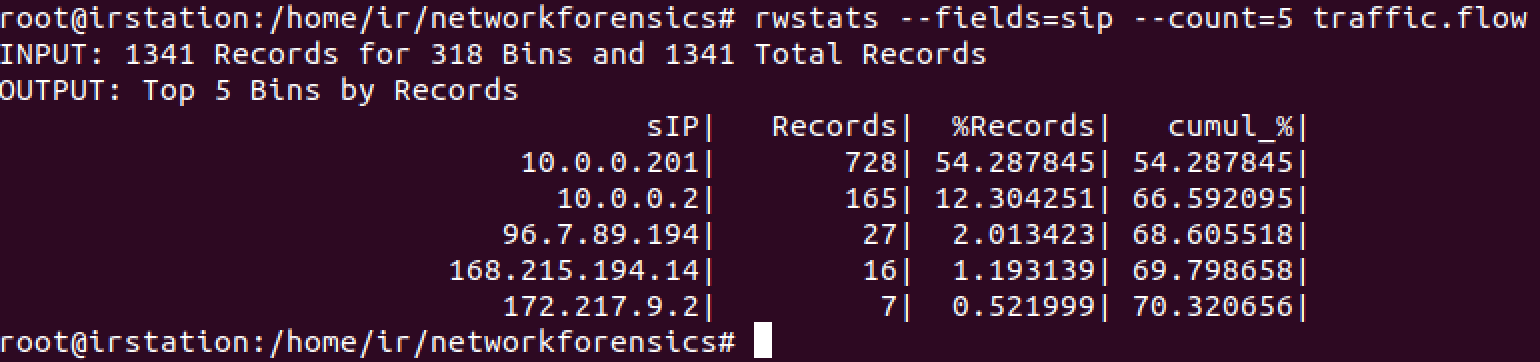
One of the most useful criteria to always look for are the top talkers in the network. Let's search based on the number of flow records with rwstats command:
Now let's see the IP address and source port for at least the 10% of the records using the same command:
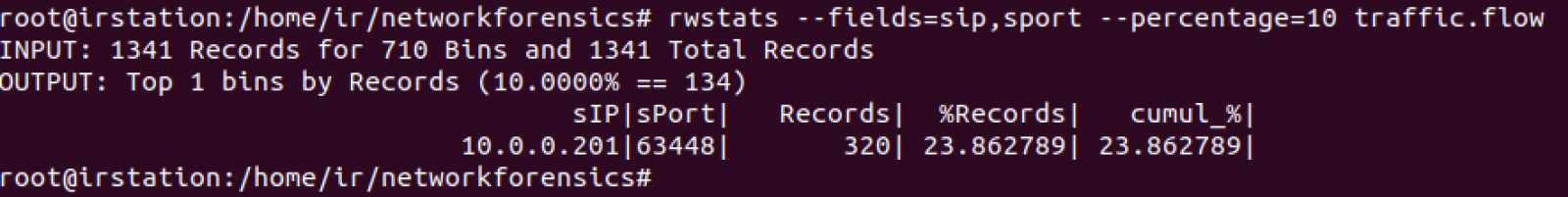
We have high ports. Let's see communications for at least 512KB:
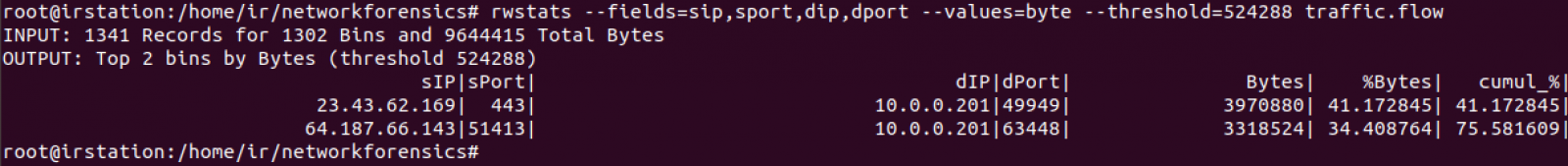
First transfer is https but second one shows related to a high port and to an IP located into an ISP with no bad reputation, which is consistent to a possible point to point transfer between both IPs. Let's see if any other IP transmitted to port 63448 of 10.0.0.201 (snippet):
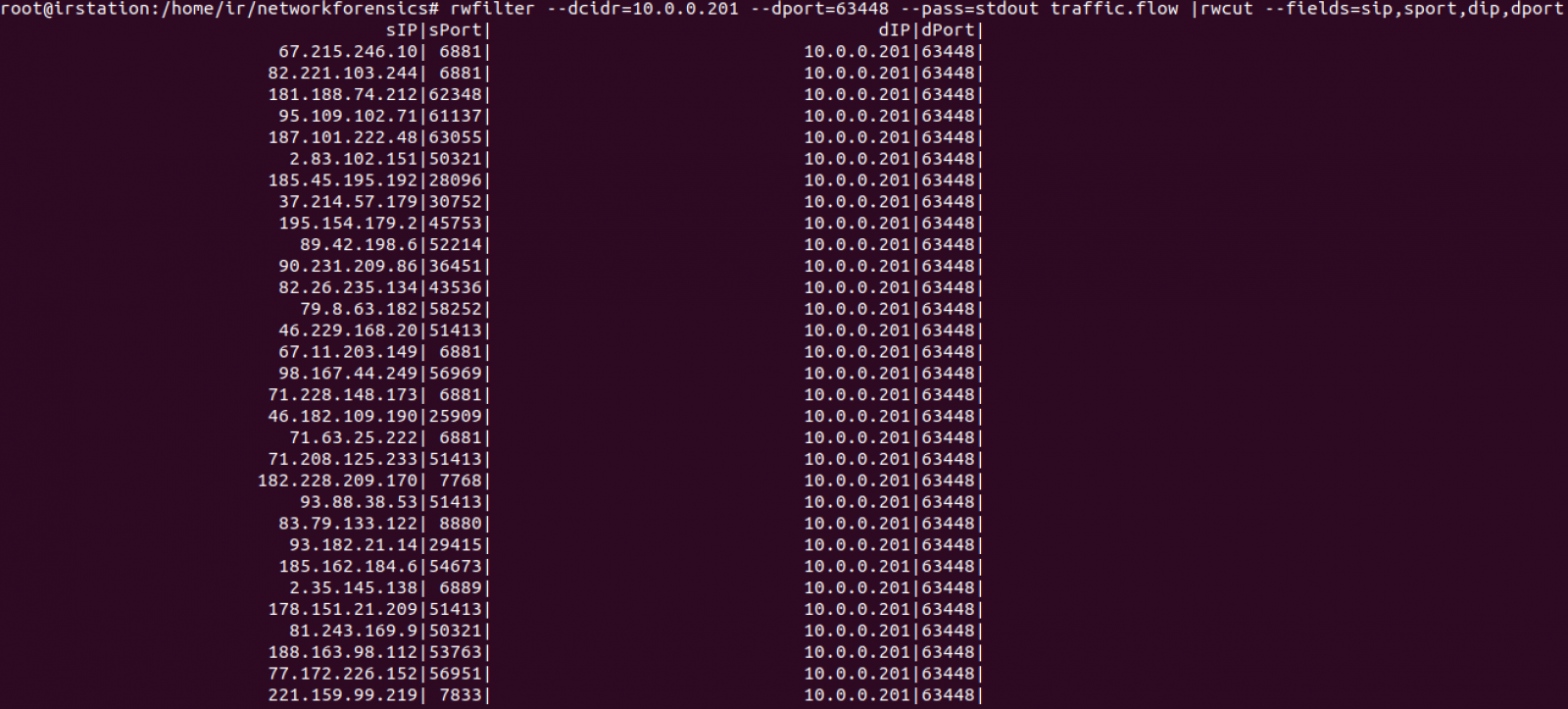
Too many records were returned. Let's count how many are there:
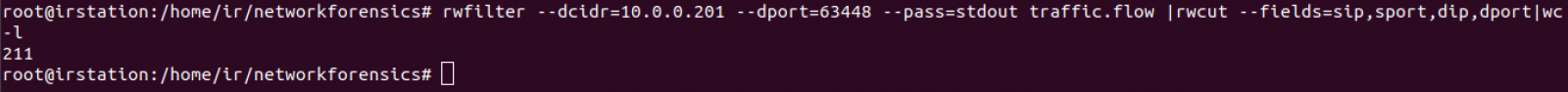
Taking out header, we count 210 IP endpoints. This can be confirmated with rwuniq command:
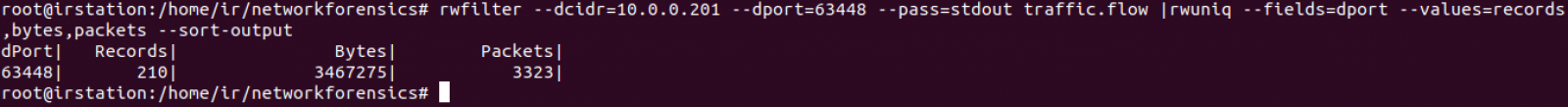
We can conclude 10.0.0.201 established several point to point transfers with 210 endpoints using source port 63448. 64.187.66.143 provided 3318524 bytes and the remaining 209 ones provided 148751 bytes.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name



Comments