Crypto Mining Is More Popular Than Ever!
We already wrote some diaries about crypto miners and they remain more popular than ever. Based on my daily hunting statistics, we can see that malicious scripts performing crypto mining operations remain on top of the sample I detected for the last 24h:
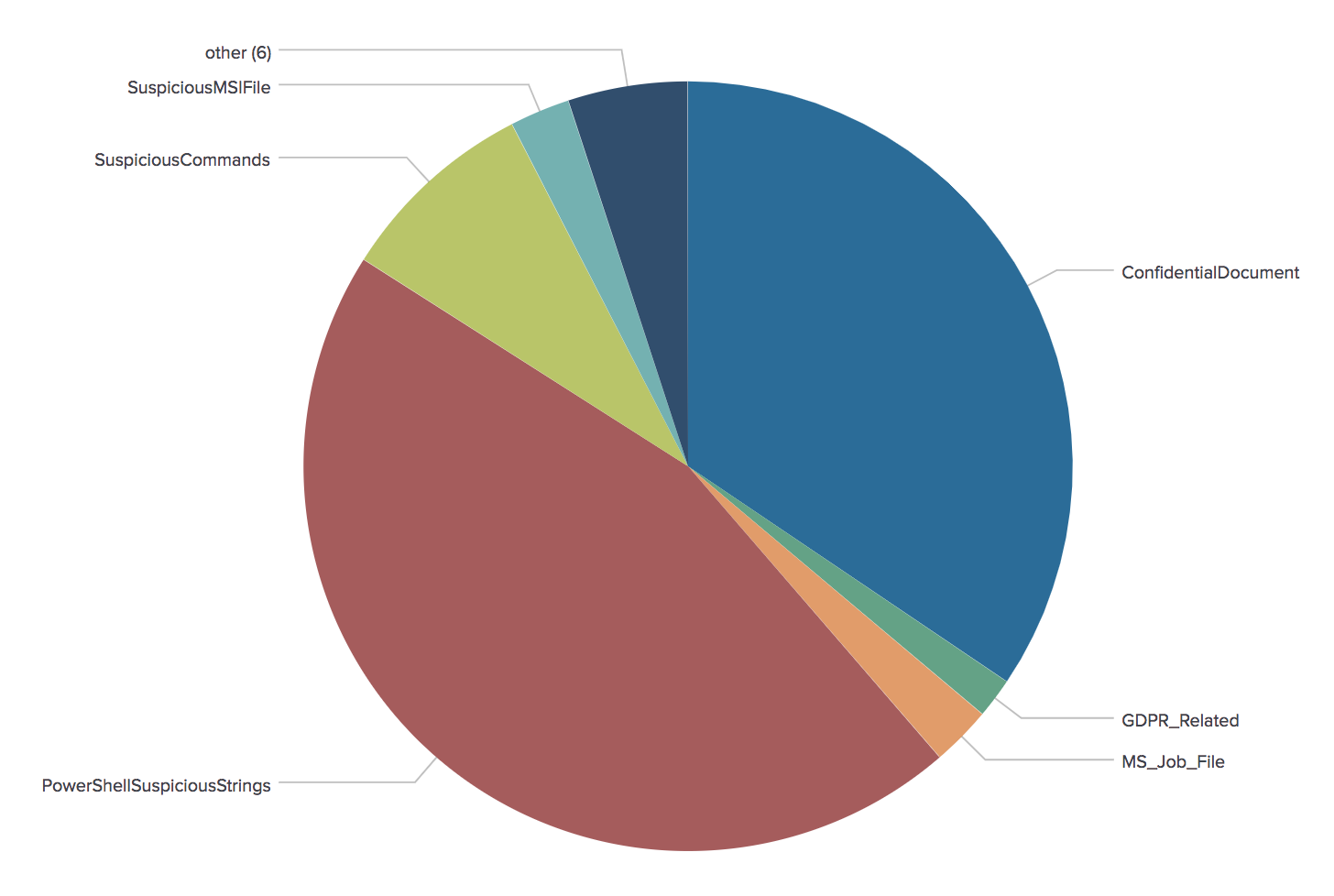
(They are represented by the ‘PowershellSuspiciousStrings’ category)
But crypto miners are not only installed on workstations, servers are juicy targets too... because that’s where the real CPU power is available! The recent Apache Struts remote code execution vulnerability (amongst other like SOLR reported by Renato a few months ago[1]) is heavily used to drop crypto miners on vulnerable systems[2].
The classic behaviour of a crypto miner dropper is to try to gain as much as available resources. To do so, they usually try to kill competitors (See my previous diary[3]).
Yesterday I came across another shell script which drops a Monero crypto miner unknown on VT (SHA256:b565d406dbb6a3aa80bc1e514b176e9ee6415eb0f425d013154e0cde555374e7). The script has nothing fancy, it downloads a Monero crypto miner and adds persistency via a cron job. However, this one improved the detection of other CPU intensive processes!
Here are some examples extracted from the sample:
It kills processes containing the following IP addresses on the command line:
It removes the memory segment used by JBoss:
rm -rf /dev/shm/jboss
Here is the list of substrings searched to kill processes using the 'pkill' command:
$ grep ^pkill b565d406dbb6a3aa80bc1e514b176e9ee6415eb0f425d013154e0cde555374e7.vir | awk '{ print $NF }'|sort -u
./AnXqV.yam
./BI5zj
./Carbon
./Duck.sh
./Guard.sh
./JnKihGjn
./KGlJwfWDbCPnvwEJupeivI1FXsSptuyh
./NXLAi
./XJnRj
./accounts-daemon
./acpid
./askdljlqw
./atd
./bonn.sh
./bonns
./carbon
./conn.sh
./conns
./crypto-pool
./ddg
./donns
./gekoCrw
./gekoCrw32
./gekoba2anc1
./gekoba5xnc1
./gekobalanc1
./gekobalance
./gekobalanq1
./gekobnc1
./ir29xc1
./irpbalanc1
./jIuc2ggfCAvYmluL2Jhc2gi
./jaav
./jva
./kw.sh
./kworker34
./kxjd
./lexarbalanc1
./lower.sh
./lowerv2.sh
./lowerv3.sh
./minerd
./minergate
./minergate-cli
./minexmr
./mixnerdx
./mule
./mutex
./myatd
./performedl
./polkitd
./pro.sh
./pubg
./pvv
./root.sh
./rootv2.sh
./rootv3.sh
./servcesa
./sleep
./sourplum
./sshd
./stratum
./vsp
./watch-smart
./wget
./ysaydh
/tmp/httpd.conf
/tmp/m
/tmp/wa/httpd.conf
AnXqV.yam
BI5zj
Carbon
Duck.sh
Guard.sh
JnKihGjn
KGlJwfWDbCPnvwEJupeivI1FXsSptuyh
NXLAi
XJnRj
accounts-daemon
acpid
askdljlqw
atd
bb
bonn.sh
bonns
carbon
conn.sh
conns
crypto-pool
ddg
donns
gekoCrw
gekoCrw32
gekoba2anc1
gekoba5xnc1
gekobalanc1
gekobalance
gekobalanq1
gekobnc1
ir29xc1
irpbalanc1
irqba2anc1
irqba5xnc1
irqbalance
irqbnc1
jIuc2ggfCAvYmluL2Jhc2gi
jaav
jva
kw.sh
kworker34
kxjd
lexarbalanc1
lower.sh
lowerv2.sh
lowerv3.sh
minerd
minergate
minergate-cli
minexmr
mixnerdx
mule
mutex
myatd
performedl
polkitd
pro.sh
pubg
pvv
root.sh
rootv2.sh
rootv3.sh
servcesa
sleep
sourplum
stratum
tratum
vsp
watch-smart
wget
yam
ysaydh
You can see that the list keeps growing! Note that the script also tries to optimize the system performance by altering the memory paging mechanism[4]:
proc=`grep -c ^processor /proc/cpuinfo` cores=$(($proc+1)) num=$(($cores*3)) /sbin/sysctl -w vm.nr_hugepages=`$num`
Yes, the battle for more CPU cycles is still ongoing!
[1] https://isc.sans.edu/forums/diary/Apache+SOLR+the+new+target+for+cryptominers/23425
[2] https://www.volexity.com/blog/2018/08/27/active-exploitation-of-new-apache-struts-vulnerability-cve-2018-11776-deploys-cryptocurrency-miner/
[3] https://isc.sans.edu/forums/diary/The+Crypto+Miners+Fight+For+CPU+Cycles/23407
[4] https://wiki.debian.org/Hugepages
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Aug 30th 2018
7 years ago
Crypto miners in the browser being mainly pieces of JavaScript, you could have a look at JavaScript blockers.
Anonymous
Aug 30th 2018
7 years ago