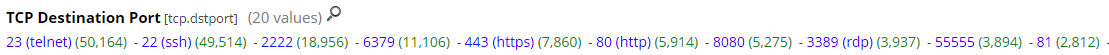
10 Most Popular Targeted Ports in the Past 3 Weeks
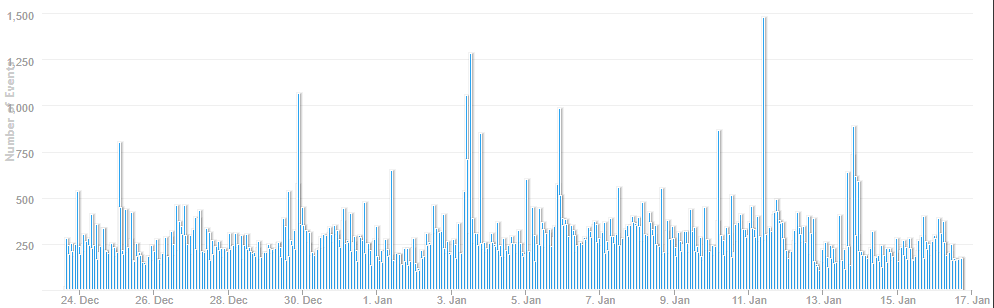
A review of all inbound connection over the past 3 weeks against my honeypot shows the top 2 targeted services were no surprise; a large amount of SSH (22, 2222) activity followed by Telnet (23) which Shodan still identifies over 2.7M hosts exposed to the Internet.
I previous did a diary [5,6] comparing SSH ports & banners as well as Telnet and RDP [7] on which the type of activity being logged hasn't really changed over time. One port that I was surprised to see as part of my top 5 was 6379, "Redis is an open source (BSD licensed), in-memory data structure store, used as a database, cache, and message broker."[8]
Indicators
218.92.0.202 (12,081)
159.223.46.162 (11,814)
218.92.0.203 (10,138)
185.36.81.60 (4,554)
213.100.222.21 (1,867)
92.255.85.135 (1,550)
161.35.77.239 (1,499)
92.255.85.237 (1,479)
185.161.70.44 (1,238)
128.199.116.10 (1,202)
[1] https://www.shodan.io/search?query=port:23
[2] https://www.shodan.io/search?query=port:22
[3] https://www.shodan.io/search?query=port:2222
[4] https://www.shodan.io/search?query=port:6379
[5] https://isc.sans.edu/diary/24724
[6] https://isc.sans.edu/diary/23201
[7] https://isc.sans.edu/diary/26492
[8] https://redis.io/topics/introduction
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu




Comments