Cisco Security Advisories - 29FEB2011
Cisco has issued five security advisories today, including:
- Cisco Cius Denial of Service Vulnerability
- Cisco Unified Communications Manager Skinny Client Control Protocol Vulnerabilities
- Multiple Vulnerabilities in Cisco Unity Connection
- Multiple Vulnerabilities in Cisco Wireless LAN Controllers
- Cisco TelePresence Video Communication Server Session Initiation Protocol Denial of Service Vulnerabilities
Adverse conditions include DoS, directory traversal, command injection, unauthenticated upload, privilege escalation, and protocol manipulation. Test and update as appropriate.
[Update (JBU) ] The "Skinny" vulnerability sounds interesting as it does allow the execution of SQL code on the device. SQL injection via Skinny is certainly an interesting attack vector. Another more serious vulnerability is the configuration access problem and access control bypass in wireless LAN controllers.
ISC Feature of the Week: 404Project Reports
Overview
Previously we featured the 404Project https://isc.sans.edu/diary/ISC+Feature+of+the+Week+The+404Project/12415 As we mentioned, the main purpose of this project is to trend the web pages crawlers and automated bots are trying to access.
We've had a good number of submitters add this script to their error page and have been collecting data for a while now. We made a few summary reports to get started trending the information. The project has been moved to its own space but the old pages should still get you to https://isc.sans.edu/404project/.
Report Information
The summary reports can be viewed at https://isc.sans.edu/404project/reports.html. The page is generated once a day for the previous day's data. The tables have descriptions for each field so I will just list them and summarize here.
Daily Totals
- Complete summary totals for the given date
Top 10 Submitted URLs
- Note the percentage is based on the max a particular URL has been submitted meaning if the submissions that particular day have been the most ever, the graphic will be out at 100%
Top 10 User Agents Submitting
- User Agents with counts and unique submitters and URLs
API Information
We've also added a couple API interfaces if you'd like to view previous data.
https://isc.sans.edu/api/#daily404summary
- Each days totals. Accepts date and limit.
https://isc.sans.edu/api/#daily404detail
- Each days details. Accepts date and limit. (Look for more fields output in the future)
Let us know in the section below if you have suggestion or feedback about these preliminary reports or send us any questions or comments in the contact form at https://isc.sans.edu/contact.html
--
Adam Swanger, Web Developer (GWEB)
Internet Storm Center (http://isc.sans.edu)
0 Comments
COX Network Outage
Based on submissions from users, and reports posted on twitter, COX appears to experience a major outage affecting it's data services. For VoIP customers, voice service appears to be affected as well.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
QOTD from securityburnout.org
In the "too good to pass up on" category we find an article by Iain Thomson in El Reg regarding a survey of stress levels among IT security staff. Iain reports on Jack Daniel's (founder of the Security B-Sides conference) well attended presentation at RSA this morning. The article and the findings speak for themselves, but I had to share one quote with apologies in advance to any CSOs in the readership to whom this may be applicable. Josh Corman, regarding some of the stress-causing factors for security professionals indicated that management is likely part of the problem and suggested the following:
"As an experiment, explain to your children what it is you're trying to explain to your chief security officer. If they get it and he doesn't, then the problem isn't with you."
For the record, I haven't encountered this personally in more than five years (I count myself among the lucky). That said, I have a few friends in the consulting industry who have a much higher ratio of minion to CSO contact than most and have absolute horror stories to share. So let's hear a few, ye who count yourselves as those on the "ragged edge of burnout and cynicism." A few ground rules, and they are absolute: no bad language, no personal or business names, no false statements or exaggeration. As Sgt. Joe Friday said, "Just the facts, ma'am." The comments form is open...
7 Comments
Odd Vanishing Signatures in OS X XProtect
With OS X Snow Leopard, Apple for the first time introduced its own anti malware technology, XProtect. Ever since then, Apple has been pushing new signatures, and XProtect itself has undergone some subtle changes allowing it to pull signature updates more frequently. The list of signatures is still rather small, but unlike other OS X anti virus software, which covers Windows malware as well as OS X malware, XProtect only covers OS X malware. At this point, two larger "families" of OS X malware emerged: The fake anti virus software MacDefender and the malicious "flash updater" Flashback.
Ever since late last year, I am running a cron job on one of my Macs to watch for XProtect updates. The updates are delivered "silently", but the cron job keeps monitoring the definition file and keeps a copy of each version.
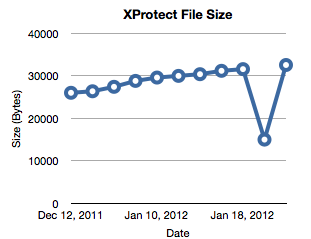
Ever since late last year, I am running a cron job on one of my Macs to watch for XProtect updates. The updates are delivered "silently", but the cron job keeps monitoring the definition file and keeps a copy of each version.
When reviewing the files yesterday, I found an odd behavior: On February 4th, the file "shrunk" by almost half. Instead of 15 signatures, the file contained only 6. On February 7th, the file went back to its old size. Has anybody else seen this? You can find the file in /System/Library/CoreServices/CoreTypes.bundle /Contents/Resources/XProtect.plist . It is a readable XML file. The current size of my file is 32516 Bytes.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
4 Comments
Flashback Trojan in the Wild
A Mac Trojan named Flashback released last year masquerading as a Flash Player installer appears to back under a new variant. A new variant of the Flashback Java Trojan known as Flashback.G is circulating in the wild running on OS X 10.6 (Snow Leopard). According to Intego, if your system has been compromised, Safari and Skype maybe prone to frequent crashes and find a Java applet in ~/Library/Caches.
"It is worth noting that Flashback.G will not install if VirusBarrier X6 is present, or if a number of other security programs are installed on the Mac in question."[1]
[1] http://blog.intego.com/flashback-mac-trojan-horse-infections-increasing-with-new-variant/
[2] http://www.macrumors.com/2012/02/24/flashback-trojan-returns-with-a-multi-pronged-infection-strategy/
[3] http://isc.sans.org/diary/Apple+Improving+OS+X+Anti-Malware+Feature/10951
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
2 Comments
DNS-Changer "clean DNS" extension requested
Brian Krebs published this request for extension by the FBI to continue to operate “clean DNS” servers for another
120 days. The ISC.org team has been running DNS servers that return valid results instead of the invalid results the
rouge DNS servers had been returning. The current order that allowed the isc.org team to run these servers for the FBI expires March 8th 2012.
http://krebsonsecurity.com/wp-content/uploads/2012/02/dnschangerextension.pdf
The operation was known as “Ghost Click”. We covered it here.
http://isc.sans.org/diary/Operation+Ghost+Click+FBI+bags+crime+ring+responsible+for+14+million+in+losses/11986
The isc.sans.edu handlers have written a lot of diaries around dns-changer type malware since 2007.
The requested 120 day extension still needs to be approved by a Judge and would help ISPs that are notifying
customers to notify more customers. Several tools have been shown to assist infected customers clean this up.
Merike Keao from Double Shot Security included a list of tools that help to clean this up in her presentation at NANOG 54.
http://dcwg.org/docs/DNS_Changer_NANOG54.pdf
This presentation has a LOT of good information in it.
The DNS-Changer working group has information on how a Service Provider can obtain a list of infected or affected
customers IP addresses here. http://www.dcwg.org/cleanup.html and lots of other good information at dcwg.org
In addition it appears Estonia may be willing to extradite 6 of the people accused of running the dns-changer network.
http://balticbusinessnews.com/article/2012/2/21/estonian-court-approves-extradition-of-six-persons-to-us-for-cybercrime
0 Comments
ISC Feature of the Week: Handler Diaries
Overview
Internet Storm Center features daily handler diaries with summarizing and analyzing new threats to networks and internet security events. Diaries range from 0day vulnerability announcements to the latest software update releases. If it's security related, we'll probably put up a diary about it!
The ISC homepage https://isc.sans.edu always displays the last 24 hours of diaries. The top and bottom of every diary, wherever it is listed, contains a previous/next navigation link that will iterate through all the diaries in order. You can click the title to view the full diary page.
What's in a Diary?
A Diary title is always an active link so you can right-click and copy to send to a friend or co-worker you think would be interested in the information. Alternatively, there is a "Share" menu to the right of the title if you want to publicly share on any number of social networking sites!!
Under the title you will see the original published date and the last updated date if any changes have been logged to the diary. Below that you will see the name of the handler that authored the diary and version number. The "Rate this diary" is currently disabled but should be back soon.
The number of comments displays how many comments have been added and is a link that will take you straight to the comments section below the diary. You can leave a comment if you are logged to your ISC/DShield account. Not logged in? No worries, just click the link, login and you should be brought right back to leave your comment. The Alias will default to what you have set in Your Information https://isc.sans.edu/myinfo.html but you can change it to whatever you want. Every comment is vetted by the handlers and inappropriate or blatant ads are removed.
The diary content will vary. It can contain anything from just a few lines of text, sometimes with web links, to a full tutorial with illustrated graphics. A handler will have their own custom signature at the end of every diary posted. If an announcement is short and doesn't require a lot of detail, a handler may post a "oneliner" which is highlighted with a different background/border and generally just one sentence.
A Keywords list follows the diary content. This is a individually linked list that will take you to a page displaying a table of all the diaries that contain that same keyword, along with the date published and author.
How can I find past dairies?
The easiest way to find past diaries is to search for keywords as explained here https://isc.sans.edu/diary/ISC+Feature+of+the+Week+ISC+Search/12496. ALL the diaries can be listed by date on the Diary Archives page https://isc.sans.edu/diaryarchive.html. This is useful if you know the general timeframe or title text of a specific diary or just want to skim titles as an entire month is shown at once.
The site footer always contains some of the most recent Diary Archives in the center as well as a link to all the archives page. The homepage also lists some more of the most recent diaries as well as a link to the Diary Archives page https://isc.sans.edu/diaryarchive.html. There is also a link to the archives after every comment section on the diary page.
How can I get these diaries you speak of?
Well, you can make https://isc.sans.edu your default browser page so you don't miss anything.
You can also receive full or title only diaries by subscribing in your favorite RSS reader. The links can be found here https://isc.sans.edu/xml.html#rss
Let us know in the section below if you have suggestion or feeback about our diaries or send us any questions or comments in the contact form at https://isc.sans.edu/contact.html
--
Adam Swanger, Web Developer (GWEB)
Internet Storm Center (http://isc.sans.edu)
0 Comments
Apache 2.4 Features
The Apache Foundation released version 2.4.1 of its popular web server, including a number of interesting changes [1]. Among the features, I would like to highlight some of the security relevant changes:
- more granular logging. Logging is always a tedious and often overlooked security component. Apache 2.4 will allow for log levels to be configured on a per-directory level.
- various changes to timeouts. We had a number of tools over the last few years that attacked web servers by exhausting connections. The new timeout changes may help with that, but over all, I don't think there is a simple fix for this problem.
- changes to the proxy configuration. Some use apache not just as a web server, but as a proxy to restrict access to resources, or as a load balancer. This can help with security, but in the past, bugs in Apache's implementation of these features has caused problems.
- Apache now includes a "mod_session" that will have Apache take care of sessions. This includes support for encrypted sessions, and support for session based authentication. Really have to see how this will all work in more detail. It appears that headers will be used to add data to sessions. This could be a new opportunity to exploit http response splitting. Note that the session information may be stored on the client, not just the server. Unencrypted sessions on the client could pose interesting security issues.
- mod_ssl has been improved to allow it to check for invalid client certificates via OCSP.
Version 2.4.1 is now available for download. I recommend you start testing it, but hold off on using it in production until some of the features have been debugged.
[1] http://httpd.apache.org/docs/2.4/new_features_2_4.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
How to test OS X Mountain Lion's Gatekeeper in Lion
While I started working on comparing various OS X hardening guides (see the prior diary from a couple of days ago), Apple announced one important new security feature in OS X 10.8 (Mountain Lion). The new operating system to be released this summer will include a white listing system based on iOS. iOS has received a lot of criticism for its closed nature, but so far, I have to admit it has worked pretty well. We have heard very little about iOS malware while Android malware appears to start steal the show from Windows malware (it got a while to go, but all the news lately appears to be about Android malware).
iOS uses a pretty simple and effective security model to fight malware: Whitelisting. All software installed on an iOS device has to be digitally signed. In order to be digitally signed, the software has to be reviewed by Apple. Only software that uses standard Apple vetted APIs is considered trustworthy to be signed, making it difficult to sneak in malicious code. If malicious software slips through, it can be recalled later.
Over the last few years, the opposite model, blocklisting ("Anti Malware") has failed spectacularly. Even many desktop users now use third party whitelisting software which is usually more granular then what Apple proposes.
Apple's approach allows for essentially three different "settings":
- Only allow Apple approved software (pretty much what iOS does)
- allow Apple approved software, but also allow software signed with specific additional certificates (you could use this to sign your own software. Kind of like accepting the certificate from an iOS developer for testing)
- allow all software (pretty much "unlocked" in iOS terms)
There are some specific limitations to Apple's approach:
- the signatures are only tested during install. If malicious software passes the install, it will not be inspected further.
- only executables are checked. A malicious PDF may still cause havoc, even if it may no longer be able to then download and install additional malware
The best part in my opinion is that the functionality was already pushed out to systems as part of the last OS X update (10.7.3). So you can already experiment with the feature and see how well it works (or doesn't work). I am running it now for a while off and on and so far, haven't experienced any ill effects, aside from it blocking me once or twice from installing software. Each time, I just disabled it temporarily (which could be considered a weakness).
The command line utility spctl can be used to enable or disable the feature. spctl --enable will enable it, spctl --disable disable it. You need to be root to run the utility.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
DNSChanger resolver shutdown deadline is March 8th
The ISC has written a number of diaries about DNSChanger in the past, including this excellent diary by a number of ISC Handlers, so I am not going to rehash the history.
With the FBI's March 8th deadline for disabling the DNSChanger resolvers rapidly approaching, the predictable fearmongering is beginning in the blogosphere and the regular press. Rest assured that DNSChanger infected a relatively small number of computers compared to most infections, and turning off the temporary resolvers will barely be blip on the Internet. There are some suggestions that the FBI may extend this deadline to permit companies to complete their cleanup. Frankly I am on the fence about whether or not an extension is a good idea. I certainly don't want to entertain the possibility that the companies that I do business with, and entrust my personal information to, may take more than 4 months to cleanup a known malware infection.
The fact is that DNSChanger has provided us a rare opportunity. DNSChanger itself never reached its full potential because of the FBI's intervention, but analysis of DNSChanger infected computers has revealed that computers infected with DNSChanger are nearly always infected with a range of other malware including malware that disables automatic updates and antivirus products. Others have been found with credential stealing Trojans and rootkits. Certainly the detection of this sort of malware should result in immediately taking the computer off the network and rebuilding it.
The symptoms of a DNSChanger malware infection are relatively easy to detect. From shortly after the FBI's Operation Ghost Click was revealed, the DNSChanger Working Group (DCWG) provided instructions on how to determine if your computer is infected, and shadowserver.org has made reports available which permit anyone who owns their own address space to reliably detect the presence of DNSChanger infections, and by extension associated malware.
In the last month or so another way of detecting DNSChanger infected computers has been made available. Several countries have launched eyechart sites which will tell you if the machine you are on is infected with malware. For the most part these sites follow the pattern of dns-ok.CC where CC is the country code of the hosting country. Some that are available are dns-ok.us (U.S.), dns-ok.ca (Canada), dns-ok.de (Germany), dns-ok.be (Belgium) and I am sure many others. They all follow a familiar pattern. If the site is a friendly green your computer is not infected with DNSChanger, a not so friendly red requires further investigation.
One caveat. It appears that in relatively rare circumstances, DNSChanger may infect SOHO routers. So although the eyechart may be red, it may not be the computer you are on that is infected. It may be the router. Either way you know that some investigation is warranted.
Please consider using these available tools to cleanup malware infections on your network...before the FBI turns off the resolvers.
-- Rick Wanner - rwanner at isc dot sans dot org - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
2 Comments
Simple Malware Research Tools
A lot of people ask me what kind of tools I use for malware research.
That's definitely a really broad question, because sometimes each malware may need a different approach. However, there are some simple tools that can help on a first approach and sometimes will give all the answers you need, without the need to go deeper on more complete debuggers and disassemblers as OllyDbg and IDA Pro, which by the way are two great tools!
For this diary I am not considering exploits, like pdf or java exploits, but just plain PE files ( EXE and DLLs).
As part of my "first look kit" I use the pescanner python script from Malware Analysis Cookbook, which the authors made available here .
This script can give you some valuable information about the PE file, like the PE Sections, Version information (if available), and compilation date. Because there are some known bad indicators, the script will also print out the [SUSPICIOUS] word when it finds one of those indicators, such as strange compilation date, and strange entropy values found on the PE Sections.
Once you are used to the analysis, a simple look on this will help you to identify possible malicious files. Since it was based on Ero Carrera's pefile python module, you can modify and add additional features if you think is necessary. One addition I did on mine was to show if the file contains an overlay. On a few situations you should see valid overlay in files, and it is very common to find parasitic virus including its code as an overlay on the PE file.
Another great tool that I use is called HIEW (Hacker's View) hex editor. It is a really complete "old-style" tool. I mean old style because it uses a DOS window, there is no GUI...:)
It has a lot of features, from a complete HEX editor, an ASCII view of the file, and a "Decode" view, where you are presented with a disassembler. It also contains several shortcuts with pre-defined functions, as to show you the basic PE information, the number of sections, the entry point address and much more.
It also allows you to go straight to section you want or jump to a specific address on the file, list the imports and exports and even edit the file.
It is a paid tool available here , but it contains a free version (6.50) which does not contain all features but can definitely give you a feel of it.
There was a open source product called Biew that had almost the same features of Hiew, but seems that it is not being updated since 2009.
Another tool that I've been checking lately is called HT Editor, that is a promissing project. It still doesnt have a lot of feaures but I like it. You may check it here
Enjoy!
------------------------------------------------------------
Pedro Bueno (pbueno /%%/ isc. sans. org)
Twitter: http://twitter.com/besecure
0 Comments
The Ultimate OS X Hardening Guide Collection
Many security professionals tend to use OS X systems. Maybe for the nice and shiny looks, or the Unix under pinnings that make it a great platform to run current tools. However, the operating system itself isn't exactly "secure out of the box" and like all operating systems can profit from some additional hardening tricks.
I have recently looked over a number of OS X hardening guides, and found that not many specifically address the latest version of OS X (Lion, 10.7), nor are they necessarily well maintained. Instead of coming up with another (soon to be outdated) guide, I am trying to come up with a "meta guide". If you know of a good hardening guide for OS X: Please let me know. Also, if there are any tricks that you find useful (or things that fired back and didn't work at all): Let me know too.
Most notably: Apple released a guide for each version of OS X up to Snow Leopard, but I can't find one for Lion. Does it exist?
Here are some of the guides that I have sound so far:
Apple: http://www.apple.com/support/security/guides/
NSA Guide: http://www.nsa.gov/ia/_files/factsheets/macosx_hardening_tips.pdf
Mac Shadows: http://www.macshadows.com/kb/index.php?title=Hardening_Mac_OS_X
Univ. Texas: https://wikis.utexas.edu/display/ISO/Mac+OS+X+Server+Hardening+Checklist
Center for Internet Security: http://benchmarks.cisecurity.org/en-us/?route=downloads.browse.category.benchmarks.os.unix.osx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
7 Comments
It is time to update your Web Browser
Both Firefox and Chrome have release updates this week. Firefox has released 10.2 and Chrome is up to 17.0.963.56. Firefox has released a couple of updates in quick succession with an impressive list of bugs being fixed. Check out this list : http://www.mozilla.org/en-US/firefox/10.0/releasenotes/buglist.html Consider doing an update soon.
Firefox
Download: http://www.firefox.com
Release Notes: http://www.mozilla.org/en-US/firefox/10.0.2/releasenotes/
Chrome
Download: https://www.google.com/chrome
Release Notes: http://googlechromereleases.blogspot.com/2012/02/chrome-stable-update.html
5 Comments
Intersting Facebook SPAM
Facebook is kind of training its user base that it is OK to click on links in emails, as long as they look like pretty buttons. When there is a friend request, or a comment has been added, in the interest of making sure that you get the message it is emailed. It was probably only a matter of time before Facebook like SPAM/PHISH email started arriving.
When I received the following, I must confess I nearly clicked it automatically, before I noticed the actual link.
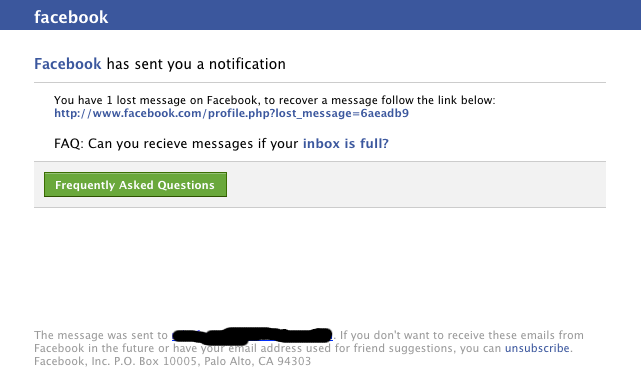
When I did click the link, I got a second surprise. To be honest I was expecting a facebook login page, failing that I was expecting malware, but what I ended up with was this. Plain old SPAM
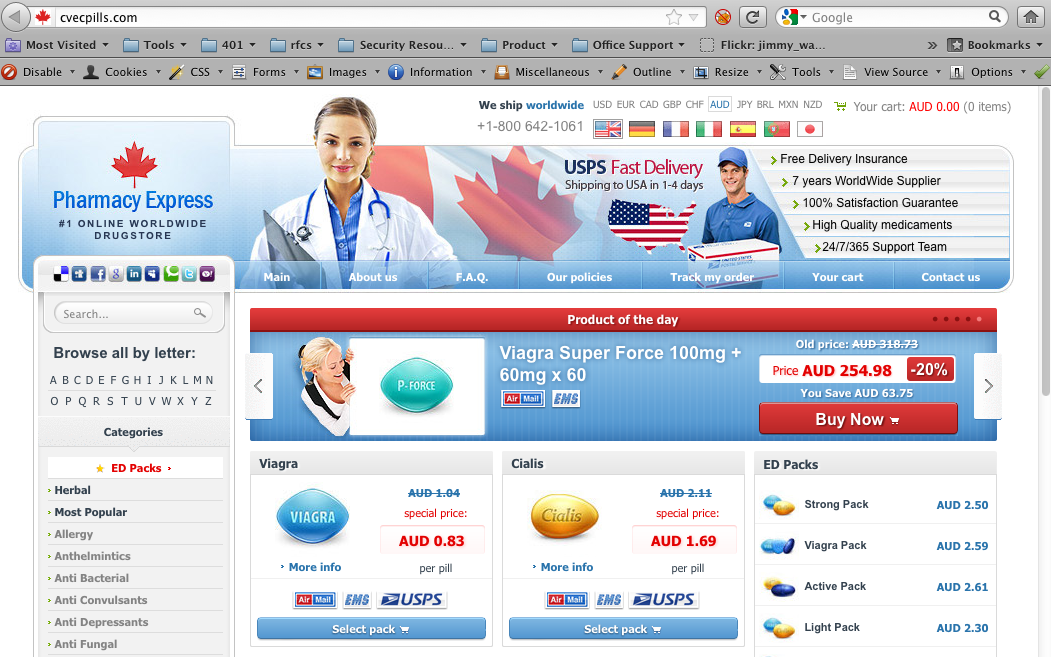
Not terribly exciting I agree. What caught my eye however was that the SPAM email looked darn close to the real thing, the emails Facebook users get every day.
If you have a user base that uses Facebook, you may wish to bring this to their attention. At the moment it is only SPAM, but it doesn't have to be.
If you are into blocking, this particular SPAM run ends up on 115.145.129.35 (South Korea), loads medicalaf.ru (In China) which redirects to cvecpills.com (In Romania). Not a bad method to get some distance between the emil and the eventual landing page. Allows them to switch targets easily.
Mark H - Shearwater
5 Comments
Java Update for February
The February Critical Patch Update for Java SE was recently released from Oracle. February has brought the release of 14 patches from Oracle that are categorized as Critical. As stated on the release page "All of these vulnerabilities may be remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password."
This alone is reason enough to fast track this package into your change management solution and deploy as quickly as possible.
Tony Carothers
tony d0t carothers at gmail
0 Comments
Adobe Flash Player Update
On Tuesday, Adobe released an update for Shockwave Player (APSB12-02) and RoboHelp for Word (APSB12-04). The odd question on tuesday was: What happened to APSB12-03. Today, we learned the answer: Another bulletin from Adobe, APSB12-03, accompanied by a patch for Adobe's Flash player.
Sadly, with the odd release date, this bulletin has fallen a bit between the cracks. However, you should apply the patch *QUICKLY* as at least one of the vulnerabilities has already been exploited in the wild.
http://www.adobe.com/support/security/bulletins/apsb12-03.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
ISC Feature of the Week: XML Feeds
Overview
You can subscribe to ISC content from our XML Feeds page at isc.sans.edu/xml.html Here we list feeds available for you to subscribe to in your favorite RSS reader.
Features
RSS Feeds
The Handler Diaries are available in summary and full text. There is also a consolidated news feed which includes recent posts from numerous security feeds.
Audio Feeds
This section provides RSS as well as iTunes feed links for the ISC Monthly Threat Update podcast and the ISC Daily Stormcast
NOTE: This month starts back the posting of an audio version of the Monthly Threat Update webcast!!
Text Feeds
Lists a subset of ISC content feeds for ports, IPs and the recommended DShield.org blocklist.
E-mail Alerts
This links to our Pager/E-mail Notifications page which has additional options to get our content "pushed" to you.
Let us know in the section below of any feeds you think would improve this page or send us any questions or comments in the contact form at https://isc.sans.edu/contact.html
--
Adam Swanger, Web Developer (GWEB)
Internet Storm Center (http://isc.sans.edu)
0 Comments
Problem with Microsoft Antivirus regarding malware from google website
In my company, we began experiencing a problem when the users tried to access http://www.google.com.co though our Forefront TMG proxy. Every corporate user saw the following message:
This really looked strange, specially coming from google. I captured some packets and queried about the http get operations and got the following:
Got three operations: one from the main query, second one retrieving a javascript file and a third one unknown. First one looked normal as always, so I started analyzing second one. The MD5 for the javascript file is 886e4780fc0af43a19eb4dcd55b728d7. I looked up the resulting MD5 and got nothing. I uploaded the script to jsunpack and got nothing:
Also tried VirusTotal to scan the URL (http://www.google.com.co) and also got nothing:
I started analysis for http get number three. Wireshark shows some compressed content, so I took it from the capture and decompressed:
The compressed file has md5 1375a0f59d52d862a1297df7566c6894, the uncompressed file has md5 c4c490a2a55a16492c068ec50827958b and when loaded starts a download from http://ssl.gstatic.com/gb/js/sem_480d0cc56e70fa5af3dda306c8bc7ce6.js. I analyzed that javascript and wepawet and jsunpack shows nothing abnormal.
This problem has been confirmed in Microsoft website. I will update the diary when I have more information about it.
UPDATE: As of 20:11 GMT-5 Feb 14 2012, we received confirmation from Microsoft stating that this problem is a false positive and will be corrected in the next update for the antivirus.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail:msantand at isc dot sans dot org
3 Comments
February 2012 Microsoft Black Tuesday
Overview of the February 2012 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS12-008 | Code Execution Vulnerabilities in Windows Kernel-Mode Drivers (Replaces MS11-087) |
|||||
| win32k.sys CVE-2011-5046 CVE-2012-0154 |
KB 2660465 | disclosed vuln. | Severity:Critical Exploitability: Likely |
Critical | Critical | |
| MS12-009 | Elevation of privilege vulnerabilities in ancillary function driver (Replaces MS11-046, MS11-080) |
|||||
| Ancillary Function Driver CVE-2012-0148 CVE-2012-0149 |
KB 2645640 | no. | Severity:Important Exploitability: Likely |
Important | Important | |
| MS12-010 | Cumulative Patch for Internet Explorer (Replaces MS11-099) |
|||||
| Internet Explorer CVE-2012-0010 CVE-2012-0011 CVE-2012-0012 CVE-2012-0155 |
KB 2647516 | no. | Severity:Critical Exploitability: Likely |
Critical | Important | |
| MS12-011 | Sharepoint Elevation of Privileges Vulnerabilities |
|||||
| Sharepoint CVE-2012-0017 CVE-2012-0144 CVE-2012-0145 |
KB 2663841 | no. | Severity:Important Exploitability: - |
N/A | Important | |
| MS12-012 | Remote code execution vulnerability in color control panel |
|||||
| Color Control Panel CVE-2010-5082 |
KB 2643719 | no. | Severity:Important Exploitability: Likely |
Critical | Important | |
| MS12-013 | Vulnerability in C Run-Time Library Could Allow Remote Code Execution | |||||
| C Run Time Library CVE-2010-3138 |
KB 2654428 | no | Severity:Critical Exploitability: Likely |
Critical | Critical | |
| MS12-014 | Vulnerability in Indeo Codec Could Allow Remote Code Execution | |||||
| Indeo Audio Codec CVE-2010-3138 |
KB 2661637 | no | Severity:Important Exploitability: Likely |
Important | N/A | |
| MS12-015 | Vulnerabilities in Microsoft Visio Viewer 2010 Could Allow Remote Code Execution (Replaces MS11-089) |
|||||
| Microsoft Office Suites and Software CVE-2012-0019 CVE-2012-0020 CVE-2012-0136 CVE-2012-0137 CVE-2012-0138 |
KB 2663510 | no. | Severity:Important Exploitability: Likely |
Important | N/A | |
| MS12-016 | Vulnerabilities in .NET Framework and Microsoft Silverlight Could Allow Remote Code Execution (Replaces MS11-069) |
|||||
| .NET Framework CVE-2012-0014 CVE-2012-0015 |
KB 2651026 | no. | Severity:Critical Exploitability: Likely |
Critical | Critical | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
4 Comments
Adobe Shockwave Player and RoboHelp for Word Patches
Adobe released two security bulletins for today's patch tuesday kickoff:
APSB12-02 [1]: Security update for Adobe Shockwave Player
This patch fixes a total of 9 vulnerabilities that affect Shockwave Player 11.6.3.633 and earlier on Windows and OS X. After the update is applied, you should be at version 11.6.4.634. Adobe rates these vulnerabilities critical as some of them allow the execution of arbitrary code.
APSB12-04 [2]: Security update for RoboHelp for Word
RoboHelp is not as commonly installed as other Adobe products. This patch fixes one vulnerability that is considered important. The vulnerability introduces a cross site scripting flaw in output generated by RoboHelp. I am not that familiar with the product, but even though Adobe doesn't specify it, it sounds like it may be necessary to re-create RoboHelp output after the update is applied to avoid the XSS issue in content generated with older versions.
[1] http://www.adobe.com/support/security/bulletins/apsb12-02.html
[2] http://www.adobe.com/support/security/bulletins/apsb12-04.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
KPN (Dutch Telecommunications company) Hack
KPN is a Dutch Telecommunications company which has not been having a good lately. They hit the national news a few days ago (http://nos.nl/artikel/338769-computersysteem-kpn-gehackt.html because of a breach in the organisation. The article is in Dutch, but in a nutshell it boils down to the following. on January 20 it was discovered that there had been a breach and they worked hard to fix the problem. A week later it turns out that their efforts were unsuccessful and the attackers still had access to the environment. That is when the breach was disclosed to the authorities.
It is also mentioned in the article that KPN could not confirm that customer information had been taken. A quick check on paste bin however will confirm that quite quickly. Interestingly KPN disabled over 2 million email accounts (http://www.reuters.com/article/2012/02/10/kpn-idUSL5E8DACNB20120210) as a precaution (mostly coming back online today).
Also interesting is that KPN has stopped issuing certificates after detecting a DDOS tool on their server (http://www.ehackingnews.com/2011/11/ssl-certificate-authority-kpn-stopped.html) This is managed by the division that was formerly known as Getronics (currently up for sale to Aurelius AG, http://www.kpn.com/Artikel/KPN-to-sell-Getronics-International.htm). A breach at another certificate authority Diginotar last year resulted in one less company. Not good. The new managing director (announced Feb 9) will have his work cut out to restore some faith. Are the two related? not sure, the systems may be completely separate.
There are probably a few lessons we can take away from KPN's misery. Firstly, when doing incident response, do it well. The problem was finally resolved after getting "outside specialist assistance". To me that reads along the lines of, we had a go ourselves and it didn't quite work out. Which is a shame. But it highlights an issue that we come across all the time. Do you know how to make a incident responder or digital forensics person cry? Just utter the phrase "we poked around ourselves for a bit". If you have the skills, go for it, but know when to ask for help and know when to stop. Having an incident response plan that clearly states what to do and what not to do helps a lot.
On the positive they did discover the issue in the first place.
If you are a KPN client. you'll want to change your passwords and if your password is used anywhere else you'll want to change those as well.
If you are at all worried about a breach in your organisation have a look at the processes you have in place the deploy, secure and maintain your infrastructure. How would you detect and if discovered deal with a breach? Have you basic security strategy in place. Not a sexy message, or even ground breaking, yet many of us still live in straw houses, or at least our servers do.
Mark H
1 Comments
DNS Ghost Domains, How I loath you so!
One of our handlers posted this to our list and I though I would share (thanks Swa). The CVE has concluded that the NDSS Conference presentation of "Ghost Domain Names; Revoked Yet Still Resolvable" [1] to be verifiable but the CVE is protocol drive. The below links will provide more detail. [2]
[1] http://www.internetsociety.org/events/ndss-symposium-2012/symposium-program/feb08
[2] https://www.isc.org/software/bind/advisories/cve-2012-1033
Richard Porter
--- ISC Handler on Duty
1 Comments
Chrome to stop checking Certificate Revocation List (CRL)?
There was a post on Ars Technica yesterday, that led back to another blog post from Sunday that suggests that Google Chrome will stop doing CRL checks at some point in the not too distant future. This has led to some interesting debate because the CRL mechanism has largely been ineffective. For a public key infrastructure (PKI) such as HTTPS to work, there must be an effective way of verifying the validity of the certificates. Due to the number of Certificate Authority (CA) breaches in recent years we'd all like a fast and effective method of taking compromised certificates out of play. During the highest profile breaches, all the major browser vendors simply pushed new versions of the browser with the root certificates from the breached CAs removed, in part because the browsers by design fail open (allow the connection) if they are unable to verify the certificate. So, is this a big deal? Is it the right way to go? Is it time to rethink/redesign/replace SSL or HTTPS? What do you think?
References
http://arstechnica.com/business/guides/2012/02/google-strips-chrome-of-ssl-revocation-checking.ars
http://www.imperialviolet.org/2012/02/05/crlsets.html
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
16 Comments
ISC Feature of the Week: Security Dashboard
Overview
The ISC Security Dashboard can be found at https://isc.sans.edu/dashboard.html or https://www.dshield.org/dashboard.html and is an ideal tool for viewing summary DShield report data, ISC site content and related security information all in one place. Some places to use the page could be simply an open browser tab, an embedded web page, a control center monitor and more! Let us know where you use the dashboard in the comments section below.
Features
The first section on the page contains the current UTC date/time and Refresh options. You can click to Refresh immediately or select to let the page auto-refresh every 5, 10, 20, 30 or 60 minutes. Additionally, when you select an interval, the reload will display a link you can bookmark to easily return to that timed refresh rate.
Row 1:
Column 1: World Map Country Report from https://isc.sans.edu/countryreport.html
Column 2: Latest Diaries from https://isc.sans.edu/diary.html and the ISC Search box that goes to https://isc.sans.edu/search.html
Column 3: Top 10 Source IPs from https://isc.sans.edu/reports.html#top10source
Row 2:
DShield live banner, showing Top attacked and port attacked, that links to https://www.dshield.org
Row 3:
Column 1: Top 10 Ports from https://isc.sans.edu/reports.html#top10ports
Column 2: Latest StormCast from https://isc.sans.edu/podcast.html#stormcast and ISC/DShield Google Groups link/box for subscribing to http://groups.google.com/group/iscdshield
Column 3: Top 10 Rising Ports Trends graph from https://isc.sans.edu/trends.html (NOTE: This graphic has location-sensitive click-able hot spots. Try it out!)
Row 4: Select Security News feeds
Row 5:
Column 1: Latest sans_isc tweets from https://twitter.com/sans_isc
Column 2: Select SANS Reading Room Papers from http://www.sans.org/reading_room
Column 3: Twitter list of tweets from ISC Handlers
Planned future improvements include html5 update which will allow blocks to be re-ordered and block location preferences saved to your ISC profile.
Let us know in the section below where you use, or are planning to use, the dashboard or if there's content you think would be a valuable addition to this page or send us any questions or comments in the contact form https://isc.sans.edu/contact.html
--
Adam Swanger, Web Developer (GWEB)
Internet Storm Center (http://isc.sans.edu)
1 Comments
Secure E-Mail Access
Recently attacks by the "not so sophisticated persistent threat" focused on e-mail security. In many cases, e-mail credentials were either brute forced, or retrieved from compromised databases (in some of these cases, password re-use was a contributing factor).
During Wednesday's threat update webcast, I would like to do a segment focusing on e-mail security, and was wondering what our readers do to secure e-mail. Some of the challenges I see:
- the use of "cloud based" e-mail services like gmail.
- mobile access to e-mail
- access to e-mail from multiple devices
- e-mail encryption and authentication (PGP/S-Mime)
- e-mail forwarding security (if someone has e-mail forwarded to a personal e-mail address)
Please let me know if you have any novel ideas to address these problems that I should cover, or if you would like me to cover any additional questions.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
10 Comments
Book Review: Practical Packet Analysis, 2nd ed
A few months ago, the good folks at No Starch Press sent me a review copy of Chris Sanders' book Practical Packet Analysis, Using Wireshark to Solve Real-world Problems, 2nd Edition. While this isn't something we normally do here, since it has been a rather slow day at the Internet Storm Center, I thought this would be a great opportunity to share a short review of the book. As many of our regular readers are probably aware, I tend to use command-line tools such as tcpdump, snort, tshark, scapy, or even Perl to perform packet analysis. I prefer the command-line tools because when possible I like to script my analysis and GUI tools don't lend themselves to that.
This book (actually, starting with the 1st edition) was one that had been on my list of books I wanted to read for quite some time, but I had never gotten around to buying it, so I jumped at this opportunity when it presented itself. I really wanted to love the book, but wasn't quite able to get there. A couple of small technical errors bothered me (probably more than they should have) and I was a little confused at who the target audience was (for example, if the book is targeted at newbies, it doesn't make sense to me to introduce filters before explaining the structure of IP packets including the IP, TCP, and UDP headers; if aimed at experienced networking folks, why bother with explaining the OSI model again). Even so, I did like the book. Starting with chapter 8 is where I think the book really becomes worthwhile. I especially like the idea of using "real-world scenarios" (even if sometimes a bit contrived) to teach the features of a tool. This is often one of the best ways to teach new techniques or concepts. I learned some new tricks for both wireshark and tshark which itself would have made it worth the price to me. I'm not going to give it stars or anything, but I do recommend this book to folks that aren't wireshark experts (and even those who have plenty of wireshark experience may pick up a new trick or two).
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
0 Comments
Cybersecurity Legislation Components
As many of us have seen in the media recently, the United States and other world governments are deeply entrenched in discussions over proposed cybersecurity legislation. There are many different flavors of legislation currently being discussed by governments across the globe, of which I don’t intend to cover here. In the US it appears the government has finally started to address cybersecurity issues that have been discussed in this forum for years. One piece of the legislation currently being discussed is a proposal sponsored by Rep. Dan Lungren (R-Calif.) is House Resolution 3674 - the Promoting and Enhancing Cybersecurity and Information Sharing Enhancement Act of 2011 or PrECISE. The thrust of the bill is “to amend the current Homeland Security Act of 2002" which will give additional authority to the US Government in the national cybersecurity effort.
I want to highlight some of the ideas being presented in this bill and how they are going to be a huge win for the cyber security community. These are just a few of the items being discussed, but these will pay huge dividends in the security effort.
The coordination and sharing of information between the civilian and government agencies is one of the topics some of the bills being considered address, and is a critical component in the cybersecurity effort. As it is written in PrECISE SEC. 2. Sec.226 (2) “foster the development, in conjunction with other governmental entities and the private sector, of essential information security technologies and capabilities for protecting Federal systems and critical infrastructure information systems, including comprehensive protective capabilities and other technological solutions”. Organizations that have previously developed implementation strategies for information systems have a leg up on organizations that have not. The Black Hat community has excelled at this type of sharing, and has been an excellent vehicle for their efforts. They are not impeded by corporate policy, federal guidelines, or other governing regulations.
The silos of information that exist in the enterprise today have also led to silos of security information. The production, collection, and correlation of that information is often difficult because different vendor technologies, implemented at different stages, lead to disparate systems. PrECISE SEC. 2, Sec 226 Para. (3) states the need to “acquire, integrate, and facilitate the adoption of new cybersecurity technologies and practices in a technologically and vendor-neutral manner to keep pace with emerging terrorist and other cybersecurity threats”. There are many great minds and methods to approach this, and the solution will not be easy. It is a critical solution that needs to be addressed.
User awareness and education is critical for every aspect of information security. With the increase of reliance on technology throughout, the importance of user education increases accordingly. PrECISE SEC. 2, Sec 226 Para.(6) states “develop and lead a nationwide awareness and outreach effort to educate the public about--
-(A) the importance of cybersecurity and cyber ethics;
-(B) ways to promote cybersecurity best practices at home and in the workplace; and
-(C) training opportunities to support the development of an effective national cybersecurity workforce and educational paths to cybersecurity professions”
User education and awareness training, coupled with the information sharing efforts mentioned in Para. (2) will go a long way towards improving the overall security of the information and systems we use every day.
I am excited to see the governments taking cybersecurity seriously, and hope the politicians can produce something that is useable and applicable to the world today. The implementation of some of the ideas discussed in this bill will be a huge undertaking, and needs to be done.As a society we have moved beyond the point where cybersecurity is merely desirable by the people who rely on technology. it is a fundamental need, and in some instances, desperately.
Tony Carothers
tony d0t carothers at g_mail
2 Comments
Apple Security Advisory 2012-001 v1.1
Earlier today, Apple announced v 1.1 of the Security update 2012-001. The advisory announced the availability of Security Update for Mac OSX 10.6.8 that addresses a compatibility issue, and the removal of security fixes that were present in original update for Snow Leopard. I am not confident why Apple removed security fixes from the original release, but maybe one of our readers can help us understand the issues behind the ImageIO security fix removal.
Below is the security advisory and we will link to the advisory once it is available on Apple's website.
"APPLE-SA-2012-02-03-1 Security Update 2012-001 v1.1
Security Update 2012-001 v1.1 is now available
for Mac OS X v10.6.8 systems to address a compatibility
issue.
Version 1.1 of this update removes the ImageIO security
fixes released in Security Update 2012-001.
OS X Lion systems are not affected by this change."
Scott Fendley ISC Handler
2 Comments
Sophos 2012 Security Threat Report
Last week Sophos released it 2012 Security Threat Report which highlighted some key finding from 2011:
- Smartphones and tablets causing significant security challenges
- Major data breaches and targeted attacks on high-profile companies and agencies
- Hacktivism -> A shift from hacking for money to hacking as a form of protest or to prove a point
- Conficker worm is still the most commonly encountered pieces of malicious software seen is Sophos customers
- Fake antivirus software is still the most common type of malware but in second half of the year appears to be on the decline
- Spearphishing attacks on the rise
Despite all this, some successes "On March 16, 2011 a coordinated effort known as Operation b107 between Microsoft, FireEye, U.S. federal law enforcement agents and the University of Washington knocked Rustock offline." [1] The entire report available here.
Handler Mark published a diary on some of the things to take in consideration "When your service provider has a breach". [3]
[1] http://www.sophos.com/en-us/security-news-trends/reports/security-threat-report/html-07.aspx
[2] http://www.sophos.com/en-us/security-news-trends/reports/security-threat-report/html-01.aspx
[3] https://isc.sans.edu/diary.html?storyid=10651
[4] http://www.sophos.com/medialibrary/PDFs/other/SophosSecurityThreatReport2012.pdf
Data breach diaries reported by ISC in 2011:
[1] Wordpress.com https://isc.sans.edu/diary.html?storyid=10729
[2] RSA Breach https://isc.sans.edu/diary.html?storyid=10609
[3] Lockheed Marting https://isc.sans.edu/diary.html?storyid=10939
[4] Sega Pass https://isc.sans.edu/diary.html?storyid=11065
[5] SonyPictures https://isc.sans.edu/diary.html?storyid=10996
[6] DigiNotar SSL Breach (result = bankruptcy) https://isc.sans.edu/diary.html?storyid=11479
[7] GlobalSign https://isc.sans.edu/diary.html?storyid=12205
[8] Stratfor Global Intelligence https://isc.sans.edu/diary.html?storyid=12271
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
Critical PHP bug patched
Just about a month ago, PHP 5.3.9 was released, which included a patch for the "hash collision" problem. The basic hash collision problem affected various languages, including php and .Net (Microsoft fixed the issue in an out of band patch 2011-100 in late December).
PHP fixed the issue not by introducing a new hash function, but instead it limited the number of input parameters. Just like the php hardening patch suhosin did all along, PHP now supported a "max_input_var" parameter to limit the number of input parameters a request may send. The default limit was set to 1,000, plenty for most web applications.
Sadly, the fix was implemented incorrectly, and introduced a more severe vulnerability, a remote code execution vulnerability. Thats right: An attacker could craft a request, that will execute code on a web server running PHP 5.3.9.
Today, the PHP team released PHP 5.3.10 to address the issue.
If you are running PHP 5.3.9: PATCH NOW! This is a very critical bug
If you are running PHP 5.3.8: DO NOT UPGRADE TO 5.3.9. I would actually recommend that you wait.
Additionally, try to enable Suhosin if at all possible. There is a slight performance hit, but it is unlikely to break your web application unless you are already tight in resources. Many Linux distributions include Suhosin, so it may be pretty easy to set up.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Apple and Apache security fixes and releases
Apple updates released today:
- security update 2012-001 for Snow Leopard (Mac OS X 10.6) and Snow Leopard server
- update for Lion and Lion server (Mac OS X 10.7.2 -> 10.7.3)
- remote desktop 3.5.2 client
- server admin tools 10.7.3
0 Comments
ISC Feature of the Week: ISC Search
Overview
Can't find that one ISC diary, about that one thing, that one time...last week or even a couple years ago? We recently enhanced the diary tag search functions on the site. We added a more granular search to the terms being queried in order to return more related results. The integrated Google search is unchanged.
What to search
- Search String: The system will display links to Diary Tag matches and also list Google integrated search results.
- Port Number: The system will recognize a valid port and forward you directly to the Port Information page.
- IP: (ipv4 only at the moment) The system will recognize a valid IP and forward you directly to the IP Information page.
Where to Search
- The most visible search box is always at the top of the right column
- The footer has a search box below the Diary Archives list.
- Search directly on the ISC search page https://isc.sans.edu/search.html
Post suggestions or comments in the section below or send us any questions or comments in the contact form https://isc.sans.edu/contact.html
--
Adam Swanger, Web Developer (GWEB)
Internet Storm Center (http://isc.sans.edu)
0 Comments



1 Comments