Adobe Reader 9.3.3/8.2.3 addressing CVE-2010-1297
Adobe has released the update they promised earlier this month for Reader and Acrobat (flash player 10.0.45.2 code execution).
It addresses the following vulnerabilities including the recently announced CVE-2010-1297 :
CVE-2010-1240, CVE-2010-1285, CVE-2010-1295, CVE-2010-1297, CVE-2010-2168, CVE-2010-2201, CVE-2010-2202,
CVE-2010-2203, CVE-2010-2204, CVE-2010-2205, CVE-2010-2206, CVE-2010-2207, CVE-2010-2208, CVE-2010-2209,
CVE-2010-2210, CVE-2010-2211, CVE-2010-2212
The new version is 9.3.3 and the Security Bulletin is here:
http://www.adobe.com/support/
More details can be found at:
http://blogs.adobe.com/
don smith
Interesting idea to help prevent RogueAV from using SEO without being noticed:)
With the way the RogueAv teams are using SEO to poison search results one of the isc.sans.org readers "Andy" submitted this idea in response to this article by Bojan.
http://isc.sans.edu/diary.html?storyid=9085
"If search engines were to ignore everything that is not "Visible" on a page they crawl, then a lot of this malware
would lose their stealth.
Drop all hidden, non formatted, and even white text on a white background.
It would improve search results."
Google may already be doing something like this as they are not getting hit as hard as some other search engines in the fakeav SEO poisoning attacks.
Thanks Andy.
2 Comments
How to be a better spy: Cyber security lessons from the recent russian spy arrests
On Monday, a number of Russian nationals got arrested for espionage against the US [1]. With all the talk and attention paid to cyber spies, spear phishing, APT and new high tech satellites and drones, it is almost refreshing to see that good old fashioned human spies are still used and apparently found valuable. Skynet hasn't taken over quite yet. However, the story has a few neat cyber security lessons.
Lesson 1: Encrypt your Wifi
The spies evidently used WiFi networks to communicate. However, instead of all of them to connect to a particular access point, they established Ad-Hoc networks. This idea is interesting in so far as it does make remote surveillance of the connection a bit harder. The FBI had to have a listening post close by in order to intercept the connection. It appears the FBI used to be parked close to coffee shops and such frequented by the spies in order to observe them meeting with their embassy contacts. The FBI was able to intercept the communication, and apparently used MAC addresses to track the participant. It is not clear if any kind of encryption was used for the WiFi connection. But Ad-Hoc networking would only allow for WEP unless encrypted chat software is used.
As a "sub lesson" one may take away that you should change your MAC address as a spy to avoid tracking. But it is not clear if this would have made a difference.
One neat side effect of this meeting method: The participants of the meeting never had to acknowledge each other visibly.
Lesson 2: Keep your password secure
The FBI followed these spies for a while already. A few years back, the FBI secretly searched the homes of some of the spies, copying various hard disks in the process. Small problem: The hard disk was encrypted. Luckily, an observant FBI agent noted a piece of paper during the search with a long number / letter combination. Turned out it was the password. This turned out to be critical as it allowed the agents to not only decrypt the hard disk, but after decrypting the hard disk the agents found steganography software and other encryption tools, as well as lists of web sites used to exchange steganographic messages.
Lesson 3: Obscurity != Security
The spies to some extend used steganography to exchange messages. These messages where encoded into an image, and then uploaded to various web sites. As explained above, the FBI was able to obtain a list of these sites and the software used to encode them. However, at least according to some reports, the messages were not encrypted. Typically, if you want to do steganography right, first encrypt the message, then encode it in an image. In particular if you use standard software to perform your steganography. (Update: Some reports mention that the messages had been encrypted before encoding them into the images)
Lesson 4: Perfect forward security
Perfect forward security is an important cryptographic concept. You never want to use an old password to encrypt the new password. If you do, once an attacker figured out one password, they will be able to decrypt all future passwords. It appears that the spies frequently made arrangements about future meetings and communication protocols over insecure channels (like the ad-hoc wifi). In some ways this may also be considered as relying on obscurity again.
[1] http://newyork.fbi.gov/dojpressrel/pressrel10/nyfo062810a.htm
various other news reports like:
http://www.cnn.com/2010/POLITICS/06/28/russian.spying.arrests/index.html?hpt=T1
http://www.guardian.co.uk/world/2010/jun/29/russian-spies-uk-irish-passports
http://www.dailymail.co.uk/news/worldnews/article-1290475/U-S-charges-Russian-spies-FBI-swoop-Cold-War-style-espionage-plot.html
http://www.nytimes.com/2010/06/30/world/europe/30spy.html?hp
http://www.theregister.co.uk/2010/06/29/spy_ring_tech/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Down the RogueAV and Blackhat SEO rabbit hole
Couple of days ago, a fellow handler Joel sent an obfuscated PHP script he acquired. Having a PHP script that is 100KB+ and pretty heavily obfuscated definitely sounds like something I'm interested in, so with couple of extra days I decided to give it some time. At that point in time I did not know that I'm looking at the master PHP script (albeit an old version) that is being used by the RogueAV guys.
I managed to acquire the very latest version of the script that is being used at the moment which provided me with some unique insight into how their operations work. So, I will publish a series of diaries analyzing various parts in the script in next couple of days/weeks (depending on feedback/free time etc). Let's get to work.
First step: poison search engines
If you have been following campaigns by the RogueAV guys you probably noticed that they very quickly poison search engines with the latest events/keywords. The poisoning part is, of course, completely automated and partially done by the script I will talk about.
The scripts that are used are almost exclusively set on compromised web sites. They are mainly interested in web sites running Apache with PHP, of course. It looks like in many cases they are abusing incorrect installations or known vulnerabilities such as open TinyMCE editors. In any case, their goal is to install couple of PHP scripts on those compromised servers. The scripts will allow them to setup poisoning campaigns, offer redirections to other sites serving RogueAV, but at the same time to also conceal their activities as much as possible since they don't want the real owner to find out that his site has been compromised.
This means that the attackers modify the web site, but in such a way that the web site continues to operate normally, unless special parameters/keywords are used! So there are probably thousands of such compromised web sites which the attackers are not using at the moment. Since the scripts allow automatic updates they can use them at any time and configure for a specific campaign in a matter of seconds.
The following figure shows how the SEO part works, with steps described below. While I was researching this I was in contact with some colleagues in CA who posted an article about this back in January (great work by them!) with analysis similar to mine, but the script I analyzed is the latest version used at the moment. You can read CA's article here.
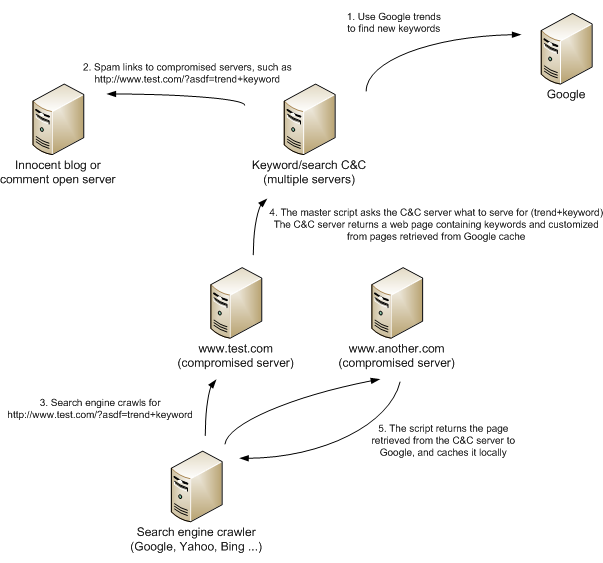
This is what is happening:
- In first step, the master C&C server(s) use Google Trends to collect keywords that are currently hot (interesting).
- The master C&C server(s) now use various methods to spam links to compromised sites containing specially crafted parameters with such keywords.
- Now search engine crawlers either find spammed links or just crawl the compromised web sites again (in which case they get a bit different response – I will cover that in the next diary).
- When the crawler accesses a compromised web site, the master script immediately contacts the C&C server and asks what to return to the crawler. The C&C server creates a web page in real time containing a lot of references to the asked keyword, as well as links to other compromised web sites!
- The custom web page is returned to the crawler and cached locally.
In step 2, besides spammed links, search engine crawlers will also visit compromised web sites. Now an interesting thing happens that helps poison the results: when the script detects a visit from a search engine crawler, but without the required poisoned parameters, the PHP script by the attackers will return the original requested web page, but with concatenated links to other compromised web sites that it has in the local database. This local database can be updated automatically through an interface on the PHP script so the attackers can update the database constantly as well.
Here we can see such a web page requested first time normally (normal user agent, main index.html requested) and second time pretending to be a search engine crawler. Notice the difference in size of the returned file:
$ ls -l index.html*
-rw-rw-r-- 1 nobody nobody 38383 Jun 26 12:53 index.html-normal
-rw-rw-r-- 1 nobody nobody 95703 Jun 26 14:47 index.html-crawler
And this is what gets appended in raw HTML:
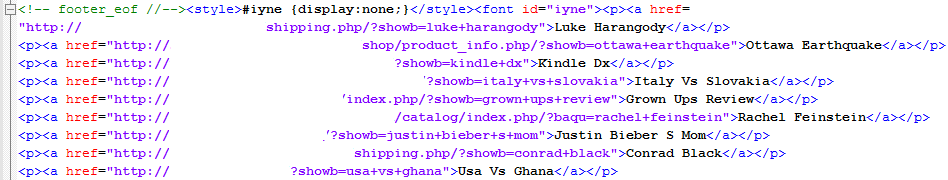
(compromised sites deliberately removed as they are still live).
By doing this they are getting all compromised sites linked to each other, hopefully increasing their rating with various search engines. See the style setup as display:none? This makes sure that if someone renders this web page through a browser that the inserted links will be invisible. They are not invisible to a crawler, of course.
Redirecting to RogueAV
Now, after all this poisoning, if a normal user (plain user agent) accesses the web site directly, he will just get the same cached web page that the crawler got. However, if the web site is accessed by clicking the link that appeared as a search result in any search engine (Google, Yahoo, Bing ...), such a request will have a corresponding referrer set and the script will redirect the user to another web site that will serve (you guessed it) RogueAV, as shown in the figure below:
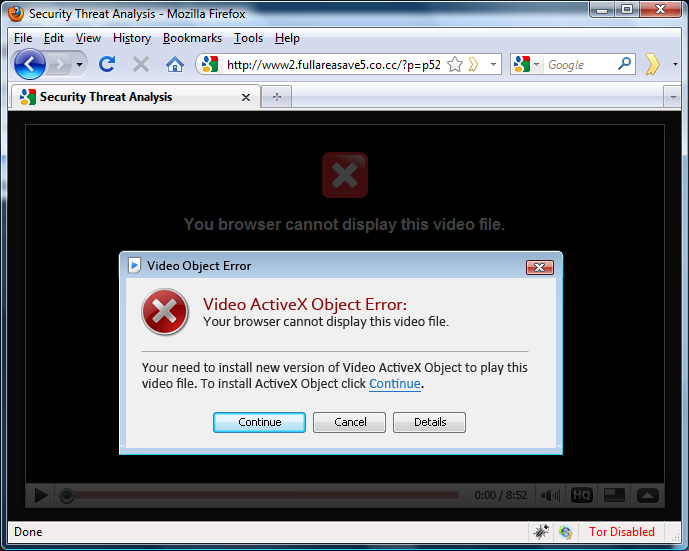
This time they are trying to get the user to install it by displaying an ActiveX error.
With this I will end with the first diary. In the next diary I'll go deeper into analyzing interesting details found in the script (will be posted on Thursday).
If you would like me to go into more details with anything let us know through our contact form.
--
Bojan
INFIGO IS
1 Comments
Study of clickjacking vulerabilities on popular sites
If you are looking for some activity on this sunday afternoon (2:37 PM GMT-5 here in Medellín, Colombia), I strongly suggest you to review the excellent paper published by Gustav Rydstedt, Elie Bursztein, Dan Boneh from Stanford University about clickjacking attacks and how to put in place proper defense against them.
Download the paper here: http://seclab.stanford.edu/websec/framebusting/framebust.pdf
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
socat to Simulate a Website
Last week I published a diary on DNS Sinkhole. If you are looking at tracking the clients that are redirected into your sinkhole address, the method I have been successfully using is with a multipurpose relay tool, called socat (SOcket CAT) .
In order to capture the host information (true website name) the client is attempting to access, I have been using socat to simulate various web server ports (80, 443, 7070, 8080, etc) and you can capture that information with your favorite IDS or using a simple Snort signature. It is much easier then to figure out what site the client was attempting to connect to and figure out if the client is already infected. A direct client outbound connection might indicate the client is attempting to contact a C&C and already compromised while a web site redirect is potentially malicious but blocked by the sinkhole.
Socat as a Web Site Simulator
socat TCP-LISTEN:80,bind=192.168.25.5,fork,reuseaddr,crlf SYSTEM:"echo HTTP/1.0 200; echo Content-Type: text/plain; echo;" &
This first socat example is used to simulate a web server listener on TCP port 80. The same line can be copied several times with different ports using the same address to simulate your web port list.
socat openssl-listen:443,bind=192.168.25.5,fork,reuseaddr,verify=1,cert=/home/certs/sinkhole32.pem PIPE=echo &
This second socat example is used to simulate a SSL server with a certificate and will need to capture the full packet stream and have the SSL certificate private key to be able to read it. This works best with a signed SSL certificate by a known CA which the browser will recognized as signed and valid. If you collect full packets (i.e. for example, using Sguil), you can then use Wireshark to examine the SSL packets and find which site the client was attempting to reach. You can create your own self-signed certificate with OpenSSL but the client will surely give a message that you are attempting to use an untrusted SSL certificate and most likely won't get the host name.
Header Review
Here is an example of a client redirected to the socat web site simulator while attempting to reach 00g00.ca.
-------------------------------------
GET / HTTP/1.1
Accept: application/x-ms-application, image/jpeg, application/xaml+xml, image/gif, image/pjpeg, application/x-ms-xbap, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, application/x-shockwave-flash, */*
Accept-Language: en-CA
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Accept-Encoding: gzip, deflate
Host: 00g00.ru
Connection: Keep-Alive
The socat binary is included in the DNS Sinkhole ISO and these two example are in the rc.local script. More information is available about socat's other features here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
2 Comments
Live CD for Remote Incident Handling
This paper was written by Bert Hayes. Bert Hayes is a security professional at the University of Texas. When Bert originally wrote this paper, he submitted it to me for the SANS Gold process, and I helped push the paper in the right direction, however, while it was an excellent paper and well written, it didn't really meet the criteria we were looking for.
However, I thought "Wow, what a great idea, what a great paper. I am sure a lot of organizations will benefit from this."
Of course Bert nor the Internet Storm Center can be held liable for any damage you to do a computer while using this, <just to get that disclaimer out of the way>, and it's recommended that if you are going to use the contents of the computer you are doing the investigation on for a prosecution, don't use this. (Changing the state of the data on the drive during a forensic investigation is generally frowned upon.
But, as I said, this is a great paper and you should definitely download it and give it a read.
Enjoy
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
2 Comments
Thunderbird 3.1 available for download!
According to Mozilla, the following updates are in Thunderbird 3.1:
- New Quick Filter toolbar
- New Migration Assistant
- Saved Files Manager
- Several fixes to improve upgrading from Thunderbird 2
- Several design improvements and corrections to the interface
- Stability, memory, and password handling improvements
So if you use Thunderbird, start your upgrade engine now. Available here. Or if you wan the local language version for our Non-English speaking customers: here.
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
0 Comments
The Great "Flash Stock Crash" of May 2010
Otto sent this article into us, and while it's not generally security related, I do feel as if it's interesting to the readers and it does relate to computers and automation in general.
Remember when the stock market (DJIA) took a dip on May 6th, 2010? Lost about 600 points? Here is a very interesting write up of the crash with charts:
http://www.nanex.net/20100506/FlashCrashAnalysis_Intro.html
There is also a "Complete Text" link on the page where you can read the full write up. Interesting stuff.
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
0 Comments
Help your competitor - Advise them of vulnerability
Tom Bicer wrote in to tell us about some interesting development amongst the SSL certificate providers. Comodo made a press release announcing that they found some vulnerabilities related to Verisign's certificate and had advised Verisign on the vulnerabilities. The vulnerability at least led to potential security issues at one of Verisign's customer (a bank). The vulnerability was discovered using publicly available information. Comodo definitely was careful in the wording of this press release, no details of the vulnerability was released. They also stated that they followed CCSS's (Common Computing Security Standards Forum) guideline in releasing the vulnerability information.
While it seems that Comodo is doing everything right, it still brings the question - Should you test your competitor's products/ stuff? And - How do you handle the announcement so it doesn't look like you are doing leveraging your competitor's security weakness in marketing? There are no good answers to those questions, it's all dependent on the situation. It's all a very fine line. It's hard to balance the bragging rights by the finder of a vulnerability before the announcement of actual vulnerability by the vendor. In some cases, vulnerabilities are never released by the vendor. Bottom line, credit to the finder of vulnerability should be given.
1 Comments
Microsoft Non-Security Updates
As a number of readers have reported, Microsoft released a few non-security updates on Tuesday via Windows Update/Automatic Updates. Most of our readers will recognize that the 4th Tuesday of the month is when Microsoft usually releases non-security updates. From the results of a couple of computers here in my office, the updates involve the .NET Framework versions 3.x and 2.x. As with all updates, please remember to test the update in your respective environment prior to wholesale deployment. More information on the .NET Framework update available at KB982524.
Scott Fendley ISC Handler
7 Comments
IPv6 Support in iOS 4
On monday, Apple released iOS 4 to the masses. Among numerous security fixes, one other feature that caught my interest was the availability of IPv6. The iPhone was one of a few holdouts in the mobile phone world that did not yet support IPv6. In some ways, the iPhone and similar devices is just why people feel we may need IPv6. Features like VoIP calling (e.g. Apple's new "Facetime" protocol) can work with NAT, but may possibly work better if the device has a globally routable IP address which may not be available in IPv4.
Screenshot of iOS 4 beta versions showed a new configuration setting for IPv6, allowing users to turn IPv6 support on and off. The final version as delivered to customers on Monday, no longer has this switch. Instead, IPv6 support is always turned on. In order to be functional, it does need to be connected to an IPv6 capable network.
In my tests, I connected the iPhone's WiFi network to my home network, which supports IPv6 and uses a router that advertises itself via IPv6 router advertisements. The iPhone did pick up an IPv6 address. The IPv6 address selected by the iPhone was derived from the MAC address (EUI-64). I personally would have preferred a privacy enhanced address.
iOS 4 does not appear to support any tunneling protocols. It will only use IPv6 in a dual stack configuration. I am going to update this diary as I get to experiment more with it.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Opera Browser Update
In other news, Opera Software released version 10.54 of their web browser on June 21st. One of the vulnerabilities corrected in this release involves the font handling flaw discussed in the advisory at http://www.opera.com/support/kb/view/954/. In addition, Opera corrected several other critical vulnerabilities which will be disclosed in the future. If you prefer to use the Opera web browser to the other mainstream alternates, it is recommended that you apply the update in the near future. More information is available in the release notes.
Thanks to Frank who noted the update a short while ago.
Scott Fendley --ISC Handler on Duty
0 Comments
Mozilla Firefox Updates
Earlier today, Mozilla released the newest version of Firefox.
Firefox 3.6.4 corrects 7 vulnerabilities which range from critical issues such as denial of service or arbitrary code execution bugs along with a few lower level issues. The full list of vulnerabilities corrected is located in the release notes. In addition, this release of Firefox provides much better handling of plugin crashes. Should a plugin crash or freeze while viewing a website, Firefox now allows the plugin to crash without taking down the entire browser. This is a very useful feature for those of us who keep many many tabs or windows open during the course of the day and get very irritated when you open that one website that has some odd flash or quicktime media that causes the plugin to abnormally end. YAY!
Firefox 3.5.10 also was released and corrects for 9 vulnerabilities of which 6 are rated as critical. The 3.5.x tree of Firefox will continue to receive security updates for 2 more months, so it is time to prepare to jump to 3.6.x very soon. More details on the security issues are listed in the release notes.
Thanks to all of our readers who were on top of these releases tonight and alerted us of them.
Scott Fendley -- ISC Handler on Duty
1 Comments
Problems With Lenovo Support
If you visited the Lenovo support site over the last few days, you may want to check out this link that Jim sent in. Lenovo Support Website Loads Malicious IFrame, Infects Visitors With Trojan
Christopher Carboni - Handler On Duty
0 Comments
Thoughts on Malware for Mobile Devices
One of the reasons that I love going to conferences is that it really makes me think. Being around some of the best minds in information security. talking to people, listening to thier views and re-evaluating my own opinions based on any new information is a big takeaway for me.
For those who were not at SANSFire this year and didn't otherwise follow the Handler's annual State of the Internet Panel, one of the questions asked of the panel was (and I'm paraphrasing because I can't remember the exact word for word question) "Every year we hear a prediction that this will be the year that mobile malware becomes wide spread. Do you think that will happen this year?"
I remember giving some answer along the lines of "Well, we've already had a few examples" and one of the other Handlers cited the malware infested apps that became available (breifly) from the iTunes Store. The panel concluded and we all went about our business but something was nagging me. Something just didn't feel right.
I started talking to a few friends discussing mobile security and then looked at my own devices.
How would I really know if there was malware on my smart phone?
Malware authors have become increasingly good at hiding the presence of malware on infected systems and I didn't have anti virus on my phone, a problem which has since been corrected. But given the problems with signature based AV protection, do I really have confidence that I'm protected?
How do we really know that mobile malware is not widespread right now?
Please take a moment and answer the poll that I've posted and if you have some creative ways you're protecting your mobile devices, send them in and I'll post them.
Christopher Carboni - Handler On Duty
8 Comments
GoDaddy Scam/Phish/Spam
A number of readers (and myself included) have received an email claiming to be from GoDaddy. The email is grammatically correct, and appears quite genuine. The subject is "GoDaddy.com Order Confirmation" and interestingly the images within the HTML are pulled from imagesak.godaddy.com, excepting one which came from "hxxp://img.securepaynet.net/bbimage.aspx?pl=somecodeandmyemailaddress". The links in the emails I have seen point to "hxxp://dextersss-com-ua.1gb.ua/zzx.htm" among others. The phishing site and IP address and domain registration are in the Ukraine.
Thanks to Christopher and Dwight!
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
3 Comments
Father's Day Tips
Happy Father's Day to all of the dads out there!
Here's something you can give dear old dad on his special day - sit down with him and walk him through some pointers on how to keep his computer and his personal information safe. If you are over at dad's today spending some time, be sure to give his computer a good tune up while you are there.
Below are some ideas for things to pass along. You might have to do a few of these things for him or perhaps teach him the steps if he's interested, If you've got other tips that would be useful for your dad, please use the comment feature at the bottom to add to the list.
Dad's Computer
1. Keep it updated, which means the operating system, any programs he has installed, and most importantly – his antivirus software. Turn on the auto-update feature and let his computer take care of updating itself automatically. Be sure to reboot if it asks you to.
2. Uninstall any software that dad does not use. Old programs often have security problems, and if dad's not going to use an application anymore, why not free up the space on his hard drive while at the same time making his computer more secure?
3. Make sure that his screen-saver requires a password to reactivate. Too often (particularly in shared environments with family members or office mates) a creative friend might send embarrassing emails from dad's computer or might accidentally download malicious software.
4. If dad has a laptop, be sure that the built-in disk encryption feature is running. This will protect him should his laptop be stolen. Also, invest in a cable lock so that his laptop can be physically secured while he's temporarily away from the computer. Laptops can be stolen in just a few seconds.
Dad's Websites
5. Warn dad to be careful with what he puts on social networking sites about himself, his friends, and his co-workers. Remember – once on the Internet, always on the Internet, especially photographs.
6. Show him how to use website passwords that are complex but easy for him to remember. Tell him that if possible, use a “passphrase” rather than a “password” – something like “Thisismybankpassw0rd” is much harder to crack or guess than “75yt*$AS” (20 characters versus 8 characters.)
7. Remind dad to pay close attention to where he is online. Many phishing sites appear to be legitimate but if he looks closely at the address bar he may see that he are not really at his bank or site that he thought he was going to. Think twice before entering any personal information at a new web site – does this company really need to know the things it is asking for?
Dad's Personal Information
8. Be very careful with peer-to-peer (P2P) or file-sharing programs. They should never be used on office computers, and if dad has them at home pay close attention to which parts of his hard drives are shared to others by these programs. Under no circumstances should he put office information on his personal computer, especially if he uses P2P software at home to share files with his friends.
9. If dad uses “reply to all” in emails, remind him to check each of the email addresses to make sure he know where his email is going. Also, tell him to BE VERY CAREFUL if he replies to a posting from a listserver or online group – his reply may go to the entire group rather than just the person he thought he was writing back to.
10. Dad should know who to call or contact if he thinks he has become a victim of online crime. Events happen fast online and he often will not have much time to call for help before it is too late. In addition, show him how to keep a backup copy of all of his personal information (passwords, credit card numbers, bank account information, emergency phone numbers, etc.) on a physical piece of paper that is locked in a fireproof container.
Marcus H. Sachs
Director, SANS Internet Storm Center
3 Comments
DNS Sinkhole ISO Available for Download
In January, I posted a diary on how to configure a basic DNS Sinkhole using BIND. Last week, during the SANSFire conference, I did a talk on DNS Sinkhole and made an ISO available for download. It is a ready to install DNS Sinkhole server for those who would like to test and/or deploy one in their network as an internal forwarder. I also indicated that inserting a DNS sinkhole in a network is like putting a NIDS/NIPS inline with potentially several thousand signatures (DNS domains). After you loaded your DNS sinkhole list, it hijacks the client’s DNS requests to known malicious sites responding with an IP address you control instead of its true address. It could also be used to enforce corporate policies (hacking, adults, gaming, social, etc) with the creation of separate sinkhole lists.
However, for maximum efficiency, it is important to only allow the DNS Sinkhole server to forward outbound requests (block all other outbound DNS request form internal servers/clients) otherwise, there are known cases where malware has been coded with its own DNS server/changer to evaded detection. Handler Bojan Zdrnja posted a diary here regarding this type of evasion.
The installation document is located in the rel_note directory of the CD and is available online here. This document provides all the information needed to install and configure the server. There are two ISO available for download:
- a 32-bit version can be downloaded here
- a 64-bit version can be downloaded here
The script to load the sinkhole list is located in the /root/scripts directory and is called sinkhole_parser.sh. This script contains a menu to download from 3 lists (Malware Domain Blocklist, ZeuS tracker and Malware Threat Center SRI). Any of these lists can be commented out in the script. They are merged, parsed and duplicates are removed to create a single list of 20,000+ sites. The sites are saved in a file in /var/named/site_specific_sinkhole.conf which can be loaded via the script in the DNS Sinkhole (server support either Bind or PowerDNS, see the release notes for configuration). I may add to the script other lists later.
Warning: If you are using any of the above lists, there is always the possibility that a site that you do business with may have been added to the sinkhole list because it has been detected serving malware.
There are various ways to capture the sinkhole data such as setting up a web server, IDS alerts, netflow, etc to find which clients were redirected to the sinkhole for signs of system compromise.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
4 Comments
IMPORTANT INFORMATION: Distributed SSH Brute Force Attacks
Based on an analysis of the logs for my SSH honeypot, it appears that this latest spate of SSH brute force attacks are using keyboard-interactive authentication, rather than the standard password authentication.
2010-05-21 19:29:11+0000 203.185.xxx.xxx trying auth password
2010-05-23 19:31:57+0000 200.175.xxx.xxx trying auth password
2010-05-25 01:02:57+0000 122.155.xxx.xxx trying auth password
2010-05-25 01:09:06+0000 75.156.xxx.xxx trying auth none
2010-05-25 01:09:07+0000 75.156.xxx.xxx trying auth password
2010-05-25 05:08:07+0000 68.40.xxx.xxx trying auth password
2010-05-29 14:39:51+0000 122.226.xxx.xxx trying auth password
2010-06-02 06:27:31+0000 217.25.xxx.xxx trying auth password
2010-06-03 11:32:22+0000 62.83.xxx.xxx trying auth none
2010-06-03 11:32:24+0000 62.83.xxx.xxx trying auth password
2010-06-11 08:44:52+0000 222.173.xxx.xxx trying auth password
2010-06-11 15:42:46+0000 220.163.xxx.xxx trying auth password
2010-06-13 22:14:15+0000 67.228.xxx.xxx trying auth password
2010-06-15 01:21:39+0000 211.254.xxx.xxx trying auth password
2010-06-15 02:09:01+0000 202.98.xxx.xxx trying auth password
2010-06-15 19:53:49+0000 89.128.xxx.xxx trying auth none
2010-06-15 19:53:51+0000 89.128.xxx.xxx trying auth password
2010-06-15 20:10:45+0000 89.133.xxx.xxx trying auth password
2010-06-16 18:20:54+0000 165.98.xxx.xxx trying auth keyboard-interactive
2010-06-16 18:33:35+0000 64.122.xxx.xxx trying auth keyboard-interactive
2010-06-16 19:05:53+0000 59.124.xxx.xxx trying auth password
2010-06-16 19:06:47+0000 220.73.xxx.xxx trying auth keyboard-interactive
2010-06-16 19:28:54+0000 219.159.xxx.xxx trying auth keyboard-interactive
2010-06-16 19:47:52+0000 80.94.xxx.xxx trying auth keyboard-interactive
2010-06-16 19:57:57+0000 203.15.xxx.xxx trying auth keyboard-interactive
2010-06-16 20:18:00+0000 119.161.xxx.xxx trying auth keyboard-interactive
2010-06-16 20:27:40+0000 82.91.xxx.xxx trying auth keyboard-interactive
2010-06-16 20:47:02+0000 190.12.xxx.xxx trying auth keyboard-interactive
2010-06-16 21:27:00+0000 200.40.xxx.xxx trying auth keyboard-interactive
2010-06-17 16:59:36+0000 210.82.xxx.xxx trying auth password
Understand: If you have disabled password authentication in your ssh_config by uncommenting the line:
PasswordAuthentication no
that *WILL NOT* protect you against this latest round of attacks.
In order to disable keyboard-interactive logins, you must also uncomment the line:
ChallengeResponseAuthentication no
NOTE: DO NOT DO THIS unless you understand what you're doing and know that it will not break anything (I don't want a bunch of emails saying "I got in trouble because I did what Liston said...")
To test if your server is configured correctly, log in using the command line version of ssh with the "-v" option. That will spit out a whole bunch of debugging information. The important line is this:
debug1: Authentications that can continue: publickey,password,keyboard-interactive
If you see something like that, then you're not only vulnerable to standard password brute force attacks, but this newer keyboard-interactive attack as well.
Tom Liston
Handler - SANS Internet Storm Center
Senior Security Analyst - InGuardians, Inc.
9 Comments
Distributed SSH Brute Force Attempts on the rise again
SSH brute force attempts seem to be on the rise again, at the SANS Internet Storm Center we have received a number of reports that a number of networks are seeing them. The source IP addresses vary with each new attempted username in the wordlist, which would indicate that the attempts are distributed through botnet(s). It only takes a single user with a weak password for a breach to occur, then with that foothold escalation and further attacks are likely next. This is certainly not a new phenomenon, however I think it is a good time to raise awareness about it once again.
Reader xemaps wrote in with this log snippet:
"Whole day my server has been targeted by a botnet, attacker also changed ip each new dictionary user."
Jun 17 23:02:03 pro sshd[17444]: Invalid user mailer from 217.37.x.x
Jun 17 23:03:24 pro sshd[17460]: Invalid user mailer from 87.66.x.x
Jun 17 23:05:27 pro sshd[17617]: Invalid user mailman from 89.97.x.x
Jun 17 23:09:30 pro sshd[17639]: Invalid user mailtest from 62.2.x.x
Jun 17 23:15:44 pro sshd[17894]: Invalid user maker from 83.236.x.x
Jun 17 23:16:47 pro sshd[17925]: Invalid user mama from 84.73.x.x
Reader Ingvar wrote in with a similar pattern:
"On my home system I have seen these login attempts that start with user "aaa" and goes on alphabetically from over 1000 different hosts around the world (judging from the DenyHosts reports). Normally I only see single-digit attempts per day."
Jun 17 02:14:56 MyHost sshd[808]: error: PAM: authentication error for illegal user aaa from 151.100.x.x
Jun 17 02:23:11 MyHost sshd[870]: error: PAM: authentication error for illegal user aabakken from 150.254.x.x
Jun 17 02:24:57 MyHost sshd[875]: error: PAM: authentication error for illegal user aapo from 173.33.x.x
Jun 17 02:35:23 MyHost sshd[885]: error: PAM: authentication error for illegal user abakus from 121.160.x.x
Jun 17 02:37:32 MyHost sshd[895]: error: PAM: authentication error for illegal user abas from 190.200.x.x
Jun 17 02:38:18 MyHost sshd[900]: error: PAM: authentication error for illegal user abc from 193.251.x.x
Last year ISC Handler Rick wrote up a diary for Cyber Security Awareness Month - Day 17 - Port 22/SSH about SSH brute force attempts and some safeguards that can be implemented. Here is a brief summary:
- Deploy the SSH server on a port other than 22/TCP
- Deploy one of the SSH brute force prevention tools
- Disallow remote root logins
- Set PasswordAuthentication to "no" and use keys
- If you must use passwords, ensure that they are all complex
- Use AllowGroups to limit access to a specific group of users
- Use as a chroot jail for SSH if possible
- Limit the IP ranges that can connect to SSH
If you have any comments, additional examples of safeguards, or additional information please let us know here.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
13 Comments
End of the road for Cisco CSA
Cisco announces the end-of-sale and end-of life dates for the Cisco Security Agent. There is no replacement available for the Cisco Security Agent at this time.
http://www.cisco.com/en/US/
(Sales end this December, Maintenance the following December, and it will no longer be supported after December 2013).
Thanks Brian!
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
2 Comments
FYI - Another bogus site
Just a quick word of caution.... Be careful what you type. We have just received information from one of our
readers, thanks Aaron, that w w w . malware domain lists . com is masquerading as legitimate site
www.malwaredomainlist.com (without the s). A quick check finds articles referencing this bad
boy site as part of the Personal Antivirus infector group.
Deb Hale Long Lines, LLC
2 Comments
Internet Fraud Alert Kicks Off Today
Microsoft and the National Cyber-Forensics and Training Alliance (NCFTA), with the support of
Accuity, the American Bankers Association, Anti-Phishing Working Group, Citizens Bank, eBay Inc.,
Federal Trade Commission, National Consumers League and PayPal are introducing a new program to
help identify potential fraudulent financial activity due to online fraud and to notify the
institutions involved that their customers personal identity may be at risk of abuse. This
program:
"Will offer a trusted and effective mechanism for participating researchers to report stolen
credentials discovered online - "
The program was unveiled today and will go into effect immediately. For more information see:
http://www.microsoft.com/Presspass/press/2010/jun10/06-17FraudAlertPR.mspx
Deb Hale Long Lines, LLC
7 Comments
Digital Copy Machines - Security Risk?
I just happened upon a CBS News video that gave me pause for thought. This once posted back in April however
I missed it until now.
http://www.cbsnews.com/video/watch/?id=6412572n
The video talks about the fact that "modern" digital copy machines, those sold after 2002, contain a hard
drive. These hard drives store the images copied. These machines are traded in for new models and then
refurbed and resold. However, the hard drives more than likely are not getting scrubbed to remove the content.
One of the copy machines in the video not only contained content on the hard drive but also still had documents
left on the copy bed.
This brings up some interesting discussions. What is on your copymachine hard drive? When it is sent in for
repair what information may be gleaned from a quick glance at the drive? Is your copy machine another potential
target to aid in identity theft?
Food for thought. Should there be processes and procedures in place for the disposal of these devices? Do you
know what other devices in your organization contain a hard drive or other storage device? Is there a process
for cleaning before disposal?
Let me know what you think? What does your company do if anything to ensure that no confidential data is
leaked by disposal of old equipment?
Deb Hale Long Lines, LLC
9 Comments
Adobe Flash Player 10.1 - Security Update Available
Please patch those flash players as soon as possible.
Last week Handler Deb Hale posted a diary speaking to some Adobe proof of concept malware in the wild.
http://isc.sans.edu/diary.html?storyid=8932
Here is the summary from the Adobe Security Bulletin.
http://www.adobe.com/support/security/bulletins/apsb10-14.html
Critical vulnerabilities have been identified in Adobe Flash Player
version 10.0.45.2 and earlier. These vulnerabilities could cause the
application to crash and could potentially allow an attacker to take
control of the affected system.
Adobe recommends users of Adobe Flash Player 10.0.45.2 and earlier
versions update to Adobe Flash Player 10.1.53.64. Adobe recommends users
of Adobe AIR 1.5.3.9130 and earlier versions update to Adobe AIR
2.0.2.12610.
Flash Player 10.1 - Release Notes
http://kb2.adobe.com/cps/838/cpsid_83808.html
US-CERT Technical Cyber Security Alert
http://www.us-cert.gov/cas/techalerts/TA10-159A.html
Thanks goes to Joe D. for supporting the Internet Storm Center and giving us a heads up on this security update.
Kevin Shortt
ISC Handler on Duty
UPDATE: Joe D. followed up with the following note:
"On the Adobe website, it is just identified as version 10.1; once installed, it is identified as version 10.1.53.64."
UPDATE 2: Thanks for the note Deapesh.
It is noteworthy that this Security Update was released by Adobe on June 10, 2010.
3 Comments
Maltego 3
Paterva has released Maltego 3.
Thanks to Joe for giving us a heads up on this release.
http://www.paterva.com/web5/client/download.php#Community
Kevin Shortt
ISC Handler on Duty
0 Comments
iPhone 4 Order Security Breach Exposes Private Information
Well, seems to be if you order an iPhone 4 you might get access to private information of other AT&T customers. The exposed information includes private addresses, phone calls, and bills.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Apple releases advisory for Mac OS X - Multiple vulnerabilities discovered
Apple released today an advisory for multiple vulnerabilities discovered in Mac OS X. Impacted programs includes CUPS, Desktop Services, Folder Manager, Help Viewer, iChat, ImageIO, Kerberos, libcurl, Network Autorization, Open Directory, Printer Setup, Printing, Ruby, SMB File Server, Squirrelmail, and Wiki Server. Mac users: please download the Mac OS X Server v10.6.4 Update Mac mini (Mid 2010) at http://support.apple.com/downloads/DL1055/en_US/MacOSXSrvUp10.6.4MacminiMid2010.dmg. Better to patch quickly before an exploit goes outside the wild.
More information for the advisory at http://support.apple.com/kb/HT4188.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
2 Comments
Microsoft Windows Help and Support Center vulnerability (CVE 2010-1885) exploit in the wild
Reader Jack showed us notifications that the vulnerability for Microsoft Windows Help and Support Center is being exploited in the wild. More information for this vulnerability at http://www.microsoft.com/technet/security/advisory/2219475.mspx.
To fix this problem, please visit http://support.microsoft.com/kb/2219475 and look for the "Enable this fix" image. It will download a MSI that unregisters the HCP protocol as a workaround, because there is currently no patch available.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Mastercard delivering cards with OTP device included
I live in a country where credit and debit card fraud is pretty high and unfortunately banks have not provided secure means to avoid credit and debit card cloning. In USA, I have seen OTP devices to access online banking, but credit cards are pretty much the same. I learned that Mastercard will provide credit cards with OTP included. This is great news because will decrease bank fraud a lot.
More information at http://www.slashgear.com/mastercard-trialling-smart-credit-cards-with-display-keypads-1089351/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
3 Comments
TCP evasions for IDS/IPS
Judy Novak posted on her blog an excellent article of IDS/IPS evations on TCP, showing a real example when linux runs on the destination host. Check it out at http://www.packetstan.com.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Rogue facebook application acting like a worm
Reader Freddie showed us a Sophos report of an application that has gone rogue by spamming your contacts once you add it to your profile. The application claims to give you access to a video named "Teacher nearly killed this boy".
Facebook users: please be careful on the links you visit and applications you add to your profile, even if they claim to give you access to "shocking" content like this one. Always use applications that comes from a trusted source or you might be helping without knowing a future malware to spread around the world.
More information at: http://www.sophos.com/blogs/gc/g/2010/06/14/teacher-killed-boy-rogue-spamming-facebook-app-large/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Small lot of Olympus Stylus Tough 6010 shipped with malware
Reader Edward pointed us a interesting link showing there is a small lot of Olympus Stylus Tough 6010 shipped with a malware inside their internal memory. More information at: http://www.sophos.com/blogs/gc/g/2010/06/08/olympus-stylus-tough-camera-carries-malware-infection/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
Python on a microcontroller?
I saw this interesting project that wants to create a python virtual machine to run inside a microcontroller without an underlying OS. This could be the gate to obtain soon a "python" hardware processor.
More information at: http://code.google.com/p/python-on-a-chip/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
Metasploit 101
Are you a security professional that needs to learn the basis of metasploit but haven't found a source? Darknet consulting (http://darknet-consulting.com/) has done a nice video that shows how to use it.
Download the video here: http://darknet-consulting.com/video/vector2/meta101.wmv
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Another way to get protection for application-level attacks
I am a fan of modsecurity (http://www.modsecurity.org/) as a fast and cheap way to get decent protection for application layer attacks. But, as you know, risks are increasing and when the risk analysis performed to your organization shows that application disruptions have a big impact to the core business, it's time to strengthen controls and think about delivering protection from the code itself. I have found useful PHPIDS library, which detects XSS, SQL Injection, header injection, directory traversal, DoS and LDAP attacks. Since it works from code, you can get the output and send it to your favorite alert vault to correlate security events.
Version 0.6.4 was recently released. More information at http://php-ids.org/2010/06/06/phpids-0-6-4-is-ready/
Want to use same functionality in perl? Try http://search.cpan.org/dist/CGI-IDS/lib/CGI/IDS.pm. It is based on php-ids.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
New way of social engineering on IRC
Many researchers have tried unsuccessfuly to use artificial intelligence (AI) to program bots to interact with humans and gather information, because the human party detects the bot very soon and drop the conversation. Well, there is now a man-in-the-middle bot that relays messages between two people to avoid detection by the parties involved in the conversations. Also detects gender of the people involved in the conversation and alters the messages accordingly. Pretty cool stuff.
Want to read the paper? Check the following document: http://seclab.tuwien.ac.at/papers/autosoc-leet2010.pdf
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
UnRealCD compromised by Trojan
As Syzop over at UnRealCD put it..."This is very embarassing". It appears that the popular UnRealCD IRC Server has been compromised with a Trojan since November 2009. If you are the keeper of one of the many UnRealCD instances I suggest you upgrade ASAP, and it probably wouldn't be a bad idea to take a long hard look at your server for other indications of compromise.
More information over at the UnRealCD forums.
Thanks to reader Colin for the heads-up!
-- Rick Wanner - rwanner at isc dot sans dot org - http://rwanner.blogspot.com/
0 Comments
World cup football South Africa 2010
All eyes will be on South Africa for the next few weeks whilst the FIFA World Cup unfolds. However with an event reportedly bigger than the Olympics. It is likely that scams, spam and other money making efforts will target the event or at least will use the interest in the event to hide and do their thing. A little reminder to staff to be vigilant and a little less eager to click that OK button will go a long way. As always if you see something interesting, let us know via the contact form.
As for my pick a Brazil - Spain final ;-)
Mark
(8 minutes to go)
Update
The first few SPAM emails have already been sighted (in fact yesterday) subject along the lines of "FIFA World Cup South Africa._. bad news" and attachment, news.html. Typically these redirect to another site.
0 Comments
Microsoft Security Advisory 2219475
Microsoft has issued a Security Advisory for the vulnerability in the Windows Help and Support
Centre function that is delivered with supported editions of Windows XP and Windows Server 2003.
The information is referenced under CVE-2010-1885.
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-1885
Full information for the advisory can be found at:
http://www.microsoft.com/technet/security/advisory/2219475.mspx
Deb Hale Long Lines, LLC
1 Comments
Microsoft Help Centre Handling of Escape Sequences May Lead to Exploit
It appears that a problem has been discovered with Microsoft Help Centre that may lead to problems for
for those who are using it.
http://archives.neohapsis.com/archives/fulldisclosure/2010-06/0197.html
According to the information provided by Microsoft on this issue:
"We are aware of a publicly disclosed vulnerability affecting Windows XP and Windows Server 2003.
We are not aware of any current exploitation of this issue and customers running Windows Vista,
Windows 7, Windows Server 2008, and Windows Server 2008 R2, are not vulnerable to this
issue, or at risk of attack."
Microsoft warns that the analysis from the original disclosure of the event is incomplete and the
workaround provided by Google is incomplete. They have made recommendations for and have
given the steps to unregister the hcp protocol to protect from exploitation. See the information for
mitigation at:
http://blogs.technet.com/b/msrc/archive/2010/06/10/windows-help-vulnerability-disclosure.aspx
Deb Hale Long Lines, LLC
0 Comments
Wireshark 1.2.9 Now Available
Wireshark has released an update. This update corrects some vulnerabilities found
in earlier versions. Thanks to J. for sending this information to us.
http://www.wireshark.org/download.html
http://www.securityfocus.com/bid/40728/discuss
Deb Hale Long Lines, LLC
0 Comments
Top 5 Social Networking Media Risks
Computerworld this week posted a rather thought provoking article on the risks that Social Networking
sites may pose on a company or organization. We all know that even if we tell the employees that
discussion of work related issues is strictly forbidden that there is a good possibility that it will slip
through. We also know that social networking sites are laden with badware/malware and viruses.
That is the nature of the beast. But are there other issues to consider. My company has been
discussing just this issue at length. We have a policy but we know that it is not near comprehensive
enough.
Take a look at this article if you are interested.
Deb Hale Long Lines, LLC
0 Comments
Another Morning of Fun
Some of you may have noticed that I was a little slow in getting started this morning.
I wasn't prompt with replying to your emails. For that I apologize. I thought it would be
good if I explained why.
At my day job/paid job one of my responsibilities is handling abuse complaints, another
responsibility is cleaning up mail servers that are doing bad things. The two usually go
hand and hand and generally are due to something one or more of the users did. Today
was no exception. I logged into my email this morning and immediately knew I had a
problem. I knew how the first half of my day was going to go. I had several hundred
abuse reports for one of my mail servers. I immediately began to investigate what
was going on with the server. I soon discovered that I had over 33,000 emails queued
up and a bunch of bounces for undeliverable emails to domains like hotmail, yahoo,
comcast, aol, etc. I began to review the emails and soon realized that someone had
logged into the webmail on the server with userid's on the box and sent emails. All of
the emails indicated the webaccess came from ip's in 41.138.x.x which happens to be
in Africnic's world. This particular server is a local server and I knew that it was highly
unlikely that someone would be legitmately logging in from Africa. I immediately blocked
the CIDR from accessing the server and cleaned up the emails so that no more would
get out. After the cleanup was done I began reviewing the logs for the webmail service.
Sure enough, I discovered that 3 valid userid's had indeed been used to login to the server
from the 41.138.x.x ip's. I immediately changed the passwords on the 3 accounts so that the
spammers could not login again from a different CIDR. Once the passwords were changed
I notified the customers of the situation.
I soon discovered that yesterday an email had been sent to the users on this adomain.net
(name changed to protect the domain). Here is what the email said:
Dear adomain.net Subscriber,
We are currently carrying-out a maintenance process to your adomain.net account, to
complete this, you must reply to this mail immediately, and enter your User Name
here (,,,,,,,,) And Password here (.......) if you are the rightful owner of
this account.
This process we help us to fight against spam mails. Failure to summit your password,
will render your email address in-active from our database.
NOTE: If your have done this before, you may ignore this mail. You will be send a
password reset messenge in next seven (7) working days after undergoing this process
for security reasons.
Thank you for using adomain.net!
THE adomain.net TEAM
Inspite of multiple warnings in the past to the users on this domain, three of them responded
to the email. Those three logins were then used last night to login to the webmail and send
the emails. Now some of you reading this are probably just shaking your head and wondering
why end users are so gullible. Well, I am with you on that. If you read the content of the email
you will soon realize that the email contained a number of grammatical errors and it is pretty
obvious that it is a poor attempt at English grammar. Most of us would just ignore the email and
delete it. Not these users... They fell for it hook, line and sinker.
I put this out for you because we have received inquiries from several other folks today about this
or a similar phish. Remind your employees/users that these emails are bogus and bad - not to
respond to them. If you are on any of my mail servers.... I thank you heartedly. This mornings
little investigation and cleanup took out 3 otherwise product hours from my day.
Deb Hale Long Lines, LLC
3 Comments
iPad Owners Exposed
Some of you may have seen the article about an iPad security breach. Some of the information floating around is leading readers to believe that it is an
iPhone software problem. It is not, the issue is with a web application not the iPhone or iPad software.
http://www.sophos.com/blogs/duck/g/2010/06/10/apples-worst-security-breach/
"Apparently, the breach was the result of a web application vulnerability on an AT&T site. This allowed a malcontent to guess
at an AT&T SIM card identifier (the so-called ICC-ID) and – if the ICC-ID was issued to an iPad – to use it to retrieve the email address
of the iTunes account associated with the device."
The fact that this happened is bad, however the amount of incorrect information circulating the Net is even worse. For the whole story see the
Sophos blog.
Another take on the situation:
http://www.wired.com/threatlevel/
Deb Hale Long Lines, LLC
0 Comments
Best Practice to Prevent PDF Attacks
I subscribe to Search Security at Tech Target and receive newsletters from them on a regular basis. It just so happens the one that I received
today had an article about how Enterprise can prevent an attack due to PDF hacks. I just read through the article and found it a very good refresher
on best practices for protecting against any malware spread by using any number of compromised attachments.
It is human nature I guess, that we open attachments from folks we know and unfortunately even some we don't know. Often times these attachments
contain more than we bargained for. Because Adobe is on every computer in the world (ok - maybe an exaggeration) it is a really big target. And
because it is a really big target there are a number of vulnerabilities associated with one component or another. The article from Tech Target states:
"According to McAfee Inc. Avert Labs, as of Q1 2010, malicious malformed
PDF files are now involved with 28% of all malware directly connected to exploits."
Considering the number of different possible attack vectors this 28% is huge. The article goes through some very common sense tips for protecting
your organization. This article though focusing on misused PDF's can be used to protect against other potential attack vectors.
Some may say this is old news and common sense and I won't disagree. But sometimes the old makes things new again.
http://searchsecurity.techtarget.com/tip/0,289483,sid14_gci1513908,00.html?track=NL-422&ad=769731&asrc=EM_NLT_11739094&uid=6115703
Deb Hale Long Lines, LLC
4 Comments
Mass Infection of IIS/ASP Sites
Sucuri.net has released a report about a large number of sites that have been hacked and contain a malware script. A quick Google today indicates that
there are currently 111,000 sites still infected. It appears that this is only impacting websites hosted on Windows servers. The situation is being investigated.
For those who are hosting there websites on Windows IIS/ASP you may find more information here.
http://blog.sucuri.net/2010/06/mass-infection-of-iisasp-sites-robint-us.html
http://nsmjunkie.blogspot.com/2010/06/anatomy-of-latest-mass-iisasp-infection.html - link removed...it triggers some Anti-virus.
Update: Paul at Sophos logs has released some additional information regarding this exploit and Infection. Thanks Paul.
http://www.sophos.com/blogs/sophoslabs/?p=9941
Deb Hale Long Lines, LLC
8 Comments
Adobe POC in the Wild
On June 5th Handler Guy posted a diary about a Security Advisor for Adobe Products. http://isc.sans.edu/diary.html?date=2010-06-05
We have received notification that a proof of concept (POC) has been found in malware taken from the wild and is currently being exploited.
For those that are Adobe users please patch before it is too late.
Thanks to our readers who brought this to our attention.
Update: For more information see US-CERT Technical Cyber Security Alert TA10-159A. http://www.us-cert.gov/cas/techalerts/TA10-159A.html
Thanks to those of you who have pointed out that I made a mistake in the Diary. It appears that there is not a patch available rather currently
just mitigation steps. It looks like the patch will be released for Flash Player soon and for Reader and Acrobat later in the month.
Deb Hale Long Lines, LLC
It appears that the Security Update has been released by Adobe. Thanks to Juha-Matti for providing this information.
http://www.adobe.com/support/security/bulletins/apsb10-14.html
5 Comments
June 2010 Microsoft Black Tuesday Summary
Overview of the June 2010 Microsoft Patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS10-032 | Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (Replaces MS09-065 ) | |||||
| Windows Kernel CVE-2010-0484 CVE-2010-0485 CVE-2010-1255 |
KB 979559 | no known exploits. | Severity:Important Exploitability: 1,1,1 |
Critical | Critical | |
| MS10-033 | Vulnerabilities in Media Decompression Could Allow Remote Code Execution (Replaces MS09-028 MS09-047 MS08-033 ) | |||||
| DirectShow, DirectX, Windows Media Format Runtime, COM CVE-2010-1879 CVE-2010-1880 |
KB 979902 | no known exploits. | Severity:Critical Exploitability: 1,1 |
Critical | Critical | |
| MS10-034 | Cumulative Security Update of ActiveX Kill Bits (Replaces MS10-008 ) | |||||
| ActiveX, Internet Explorer 8 CVE-2010-0252 CVE-2010-0811 |
KB 980195 | no known exploits. | Severity:Critical Exploitability: 1,1 |
Critical | Important | |
| MS10-035 | Cumulative Security Update for Internet Explorer (Replaces MS10-018 ) | |||||
| Internet Explorer CVE-2010-0255 CVE-2010-1257 CVE-2010-1259 CVE-2010-1260 CVE-2010-1261 CVE-2010-1262 |
KB 982381 | no known exploits. | Severity:Critical Exploitability: 2,3,1,?,?,1 |
Critical | Important | |
| MS10-036 | Vulnerabilities in COM validation in Microsoft Office Could Allow Remote Code Execution (Replaces MS08-055 MS10-017 MS10-028 MS09-068 MS09-017 MS10-023 MS10-004 MS09-027 ) | |||||
| Microsoft Office CVE-2010-1263 |
KB 983285 | no known exploits. | Severity:Important Exploitability: 1 |
Critical | Important | |
| MS10-037 | Vulnerability in the OpenType Compact Font Format (CFF) Driver Could Allow Elevation of Privilege | |||||
| Windows Kernel CVE-2010-0819 |
KB 980218 | no known exploits. | Severity:Important Exploitability: 2 |
Critical | Critical | |
| MS10-038 | Vulnerabilities in Microsoft Office Excel Could Allow Remote Code Execution (Replaces MS10-017 ) | |||||
| Excel CVE-2010-0821 CVE-2010-0822 CVE-2010-0823 CVE-2010-0824 CVE-2010-1245 CVE-2010-1246 CVE-2010-1247 CVE-2010-1248 CVE-2010-1249 CVE-2010-1250 CVE-2010-1251 CVE-2010-1252 CVE-2010-1253 CVE-2010-1254 |
KB 2027452 | no known exploits. | Severity:Important Exploitability: 2,1,2,1,1,1,1,1,1,1,2,2,1,1 |
Critical | Important | |
| MS10-039 | Vulnerabilities in Microsoft SharePoint Could Allow Elevation of Privilege (Replaces MS08-077 ) | |||||
| MS Infopath, Sharepoint Services CVE-2010-0817 CVE-2010-1257 CVE-2010-1264 |
KB 2028554 | no known exploits. | Severity:Important Exploitability: 1,3,3 |
Important | Critical | |
| MS10-040 | Remote Code Execution Vulnerability in IIS | |||||
| IIS CVE-2010-1256 |
KB 982666 | no known exploits. | Severity:Important Exploitability: 2 |
Important | Critical | |
| MS10-041 | .Net Framework Data Tampering (Replaces MS09-061 ) | |||||
| .Net CVE-2009-0217 |
KB 981343 | exploits available. | Severity:Important Exploitability: 3 |
Important | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
4 Comments
Internet Storm Center panel tonight at SANSFIRE
If you happen to be at SANSFIRE, don't miss the Internet Storm Center panel at Francis Scott Key 12 room 7:00 PM EDT. If you are not there and want to follow this event live on twitter, please visit http://twitter.com/sans_isc_fast.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
Software Restriction Policy to keep malware away
Windows is an operating system that has controls that preserve the safety of equipment. These security policies are configured using Global Policy Objects that apply to all computers in the domain. There is a specific group of these directives called Software Restriction Policies, which have the ability to restrict the type of software running on computers. It is a cheap and quick way to set restrictions on the ability of users to execute programs.
We have received a report of a piece of malware that poses as a flash postcard downloaded from the Tarjetasnico website (http://tarjetasnico.com). This malware is responsible for disabling any existing restrictions on the computer configured inside the Software Restriction Policy and also downloads the real malware from a website in Germany.
The initial program is run and sets up the following registry key:
| Registry Path | Key | Value |
|---|---|---|
| HKLM\Software\Policies\Microsoft\Windows\Safer\CodeIdentifiers | DefaultLevel | 262144 |
The number 262144 indicates a SAFER_LEVELID_FULLYTRUSTED level, which means that all execution policy are Unrestricted, so that any program can be run no matter of what restrictions are in place.
Please enforce the permissions to this registry key and its value of 0 on computers of your company so it cannot be modified by users and restriction policies remain active.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
Nice OS X exploit tutorial
For all those who love pen testing, there is an excellent tutorial on how to write an exploit for OS X. The tutorial explains how to write the exploit to the Evocam buffer overflow.
http://www.offensive-security.com/vulndev/evocam-remote-buffer-overflow-on-osx/
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
0 Comments
Security Advisory for Flash Player, Adobe Reader and Acrobat
Adobe has released an advisory that a critical vulnerability exists for Windows, Macintosh, Linux and Solaris in the Adobe Flash Player version 10.0.45.2 and earlier as well as in the authplay.dll component that ships with Adobe Reader and Acrobat 9.x for Windows, Macintosh and UNIX operating systems. This vulnerability (CVE-2010-1297) could cause a crash and potentially allow an attacker to take control of the affected system.
Adobe has received reports indicating this vulnerability is being actively exploited in the wild against Adobe Flash Player, Adobe Reader and Acrobat. The original security bulletin and suggested mitigations by Adobe is posted here.
Affected Versions
- Adobe Flash Player 10.0.45.2, 9.0.262, and earlier 10.0.x and 9.0.x versions for Windows, Macintosh, Linux and Solaris
- Adobe Reader and Acrobat 9.3.2 and earlier 9.x versions for Windows, Macintosh and UNIX
Not Vulnerable
- Flash Player 10.1 Release Candidate, can be downloaded here
- Adobe Reader and Acrobat 8.x are confirmed not vulnerable
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
7 Comments
OpenOffice.org 3.2.1 Fixes Bugs and Vulnerabilities
OpenOffice's latest version is available for Windows, Mac OS, Linux and Solaris systems. This release fixes 5 potential vulnerabilities, adds more stability and speed but no new features. The security bulletin is posted here.
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
New Honeynet Project Forensic Challenge
For those of you who, like me, are fans of the various challenges, the Honeynet Project has released challenge 4 in their 2010 forensics series.
To quote from the challenge page: Challenge 4 - VoIP ... takes you into the world of voice communications on the Internet. VoIP with SIP is becoming the de-facto standard for voice communication on the Internet. As this technology becomes more common, malicious parties have more opportunities and stronger motives to take control of these systems to conduct nefarious activities. This Challenge is designed to examine and explore some of attributes of the SIP and RTP protocols. Enjoy the challenge."
Have fun!
-- Rick Wanner - rwanner at isc dot sans dot org
0 Comments
Changes to Internet Storm Center Host Name
The Internet Storm Center has been known under a number of different domain names. Starting with "incidents.org", moving to "isc.incidents.org" and "isc.sans.org" we accumulated some history. These days, the Internet Storm Center is operated by the SANS Technology Institute, which uses "sans.edu". To finally reflect this change, we will be using "isc.sans.edu" as our primary host name going forward.
All old domains will work as before, but in order to clean up some of the cruft, I am going to implement redirects (301) to clean the old domains from search engines. We obtains a multiple domain (UCC) SSL certificate to support SSL for all the old domain names.
If you log in, you HAVE to use the isc.sans.edu site. Cookies are set only for isc.sans.edu. Of course, please report any problems you may have.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Microsoft Patch Tuesday June 2010 Pre-Release
Microsoft announced today they will be releasing a total of 10 bulletins addressing 34 vulnerabilities rated important (7) to critical (3) that could allow for remote code execution. Six bulletins affecting all Windows versions (2 critical and 4 important), two affecting Microsoft office XP, 2003 and 2007 (2 important), one affects Windows and Office (important) and one affects Internet Explorer (critical). More details available here.
Two other publicly known security issues will be addressed this month:
Vulnerability in Microsoft SharePoint - Security Advisory 983438
Vulnerability in Internet Explorer - Security Advisory 980088
[1] Microsoft Security Response Center Blog
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
Top 10 Things you may not know about tcpdump
"tcpdump" is one of those utilities we take for granted. Ask in any networking class, and more or less everybody has used it before and knows how to use it. tcpdump was first written in 1987 as a research project. Since then, the library behind it (libpcap) and the tool itself have been ported to more or less any operating system out there and have been incorporated into too many tools to count (Bill Stearn tried [1]).
What is often overlooked: tcpdump is still actively developed. Right now, the latest version is 4.1.1 with libpcap version 1.1.1 [2]. Many operating systems use version 4.0 now by default.
So what changed? What are the things you may not know about tcpdump? Here are some of the favorite items I ran into and please fill free to submit more.
- snaplength: it is no longer 68 bytes! New versions of tcpdump (>= 4.0) default to a snaplength of 64k. No more need to use -s 0 (but it doesn't hurt).
- IPv6 support: the ip[] filter works for all versions of IP BUT IPv6. Also, tcpdump will happily treat packets as IPv4 if the first 4 bits are anything but '6'. If you want to filter for IPv6, use 'ip6'.
- The -E option will decrypt IPSEC traffic. You need to know the shared secret or secret key of course and not all algorithms are supported.
- -Z username will drop root privileges and run tcpdump as "username" after it started. (many versions now do this by default using a "pcap" user).
- portrange: a macro that can be used to filter a range of ports (e.g. portrange 0-1023).
- less/greater: filter packets by length.
- new versions of tcpdump will print more then one line if the '-v' switch is used (breaks a lot of old shell scripts that use grep and such to filter)
- there are now a number of macros for common offsets. For example tcp[tcpflags] is equivalent to tcp[13].
- the "proto" macro will only match the next header field in the IPv6 header, which may not be the transport layer protocol that you expect from IPv4.
- the -C option can be used to rotate files after they reach a number of mbytes (don't confuse with lower case -c).
Know any more "hidden and forgotten features"? Let us know....
[1] http://www.stearns.org/doc/pcap-apps.html
[2] http://www.tcpdump.org
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
5 Comments
Clickjacking attacks on Facebook's Like plugin
In last couple of days there has been an outbreak of clickjacking attacks on Facebook's "Like" plugin. For those unfamiliar with Facebook, this plugin allows users to mark certain pages as interesting, and subsequently in their profile a statement will appear that they "like" certain content.
Since we received a lot of e-mails from our readers about these attacks (and certainly some media covered variants of them), I decided to analyze one which is still up and working as I found it pretty interesting.
The main idea of this attack is to get a user to click on a hidden link while the user thinks he is actually clicking on something else – this is the basis for clickjacking attacks. So, let's see how it's done in Facebook's example.
The main malicious web page tries to entice the user to click on it to see the rest of the so called "best passport application rejection in history". The web page just contains a single JPG image and you can see below what it looks like:

Now, what happens behind the scenes is pretty interesting. The HTML source contains two obfuscated JavaScript elements and an iframe that do all the work.
Let's first see what the iframe does:
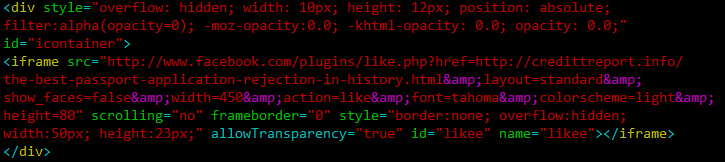
The div tag sets this iframe completely invisible (and the attacker makes sure that this works in every browser by using all the possible opacity combinations). Then the iframe points to the Like plugin at Facebook, and sets the href parameter to the target web site (the credittreport.info site).
This is what shows in the iframe:
![]()
Yes, there are 15,687 people "infected" with this.
Now comes the interesting part – how to make the user click on this, relatively small icon. The second obfuscated JavaScript element tells the rest of the story:
Let's analyze this JavaScript code. In line 2 they get the "icontainer" element – this element holds the iframe, you can see in the iframe code above that the div tag uses the id "icontainer". The standardbody object will contain the document body. Now, let's skip to line 21 – this line defines a handler for mouse movement. So, every time the mouse is moved, this function, starting with line 22 is called. The function checks if the iflag variable is 0 (and it is, until the user clicks on the hidden element). If the variable is 0, the mouse movement handler will call the mouseFollower() function. And this is the main trick – the mouseFollower() function actually moves the iframe to follow the mouse! So the attackers made sure that no matter where you click on the web page, you will land on the hidden Facebook button and "infect" yourself by posting a message on your profile saying that you like this malicious site. When a friend of yours click on that link, he/she will be taken to this web page again and no matter where they click, they will end up doing the same! If you close the window, nothing will happen.
Attacks such as this one have become increasingly popular lately, so be careful what you click on, no matter if it's in Facebook or not. If you are a Facebook user, be especially careful of all links, especially those that require you to click on something else to see the real content.
While this isn't really a vulnerability in Facebook, it does appear that their team will have to step up and implement some controls to prevent clickjacking attacks such as this one.
-- Bojan
INFIGO IS
7 Comments
New Mac malware - OSX/Onionspy
A new strain of MAC Malware is being reported by Intego - OSX/OpinionSpy.
You can find details here:
http://blog.intego.com/2010/06/01/intego-security-alert-osxopinionspy-spyware-installed-by-freely-distributed-mac-applications/
http://webcache.googleusercontent.com/search?q=cache:tWyWhF_d-30J:blog.intego.com/+flv+mp3+intego&cd=1&hl=en&ct=clnk&gl=ca&client=firefox-a
So far, it has been seen on a number of screensavers, and a small java/php app generally named "mac_flv_to_mp3.php" or similar, but be cautious on downloads, it's a simple bolt-on, so be on the lookout for it elsewhere.
The neat thing about this malware is that it passes most static scan tests - the downloaded software itself is clean, the malware is downloaded as part of the installation process. This highlights the requirement for an on-access virus scanner for your OSX computers. I hate to bring "that advertisement" up again, but the "viruses? oh, mac's don't have that problem" statement was both not true and a huge red flag for malware authors.
Thanks to several readers for both pointing us to this article, and shooting us a copy of the actual code !
=============== Rob VandenBrink Metafore
8 Comments
SPAM pretending to be from Habitat for Humanity
I received a disturbing (to me) piece of SPAM this morning:
As happens occasionally, this one sailed through our SPAM filter, but it got my attention for a number of reasons
The spelling and grammar are pretty good - this does not look like your typical spam
- It doesn't ask for money
- It does ask for your personal information
- It pretends to come from a charity that has a long history of delivering services via volunteering.
- After a bit of digging, this looks like a new specimen, just cropping up over the last few days (I could be wrong on this, please correct me if so)
- I think it bothers me so much at a personal level because H for H is a favourite charity of mine - where else can you do so much good, and get to use your power tools at the same time?
As you'd expect, the text of the "reply to" looks like a legit-sounding address, but under the text, the actual link goes to a bogus gmail account.
So, I thought - what to do? I haven't been an admin responsible for a corporate mail server in several years - is this kind of spam normal these days? My best answer to this question was "ask the readers at ISC" - any comments that any of you might have on this spam-bit, or any trend that it may represent would be very much appreciated. Please use the comment button, and pass along any info you may have.
As a trend, we see that SPAM tends to follow the news. I'd expect that we're seeing SPAM about the BP oil disaster in the Gulf of Mexico, and also about the Pacaya volcano eruption near Guatemala City. Are you seeing spam taking advantage of these events?
Just to feed the discussion a bit more - what's next? Will we be seeing SPAM from bogus medical labs - "There may be an issue with your recent blood test, please enter your information to verify" or some-such? How far will these low-lifes go to get our info or cash?
I'd like to say I'm disappointed in our fellow online denizens, but really the worse these get, the more I almost seem to expect them.
Please comment, let us know what you're seeing out there spam-wise !
=============== Rob VandenBrink Metafore ===============
6 Comments
Upswing in port 23/TCP scanning
Reader Tom wrote in that he has noticed an upswing of scanning for port 23/TCP to a honeypot system. They are completing the 3 way handshake, then sending a FIN to shut it down. Dshield data confirms that others are seeing the same.  Let us know if you are seeing anything interesting at our contact us page.
Let us know if you are seeing anything interesting at our contact us page.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
SPF how useful is it?
Chris wrote in and mentioned a talk at Auscert which highlighted that (Sender Policy Framework) SPF would have helped in the instance of an intrusion and suggested a diary outlining some of the things that can and can't be achieved using SPF. I have my own experiences with SPF and the effectiveness, but I'd like to hear you experiences with SPF, good or bad. so I can write a more complete diary on the topic.
For those that are not familiar with SPF. The idea behind it is to create a DNS entry that specifies those machines in your network that are allowed to send email from your domain. The receiving mail server checks this record and if it does not match it will drop the message. There is a little bit more to it, but hat is the crux of it. So if you have had any experiences with SPF (good or bad) please let me know via the contact form or directly markh.isc at gmail.com.
Thanks Chris for the idea and thanks in advance for your contributions. I'm aiming to get a diary out on this later this month.
Cheers
Mark H
15 Comments



1 Comments