The FBI has determined that these calls serve as a diversionary technique. During these TDOS attacks, online trading and other money management accounts are being accessed by the perpetrators who are transferring funds out of those accounts. The perpetrators will obtain account information of their victims in some way and then contact the financial institutions to change their victims’ profile information such as email addresses, telephone numbers and bank account numbers.
The purpose of the malicious phone calls is to occupy the victim phone numbers on record with the financial institutions managing the accounts so that when the institutions contact the victim to verify the changes and transactions, the institution is unable to reach the victim. Consequently, the victim has no idea what has really transpired until it’s too late."
You can see the full article at the NJToday website.
The article warns the receiver of any of these types of calls to be hyper vigilant and keep an eye on all of your personal finances, accounts and make sure that you take advantage of the right to your free credit report annually. All of us should take this advice to heart whether or not you are receiving these harassing calls.

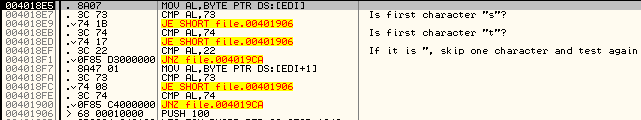
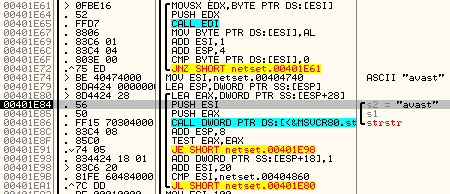
.png)

 if you want to a large financial influence (for instance in a cyber-war scenario), you don't need to control 24B in household assets through malware, you need to control one trader's workstation at a major firm. Yesterday's event shows us just how vulnerable we are - one bad trade, and all the lemmings follow the leader over the cliff! Fund managers would be good targets as well. Through a lever like this, your control is multiplied potentially hundreds of times.
if you want to a large financial influence (for instance in a cyber-war scenario), you don't need to control 24B in household assets through malware, you need to control one trader's workstation at a major firm. Yesterday's event shows us just how vulnerable we are - one bad trade, and all the lemmings follow the leader over the cliff! Fund managers would be good targets as well. Through a lever like this, your control is multiplied potentially hundreds of times.

0 Comments