Maldoc Falsely Represented as DOCX Invoice Redirecting to Fake Apple Store
This is a phishing document received today pretending to be an invoice (Word Document) from Apple Support but initial analysis shows it is a PDF document.
Using Unix command file to verify the file type: BgtCyNSnF4ZIpxYsNfvqsVB3TxfwkH6cuywkUcuLc.docx: PDF document, version 1.7
MD5: 756b20a4e96cdce0882bbff696313ccc BgtCyNSnF4ZIpxYsNfvqsVB3TxfwkH6cuywkUcuLc.docx
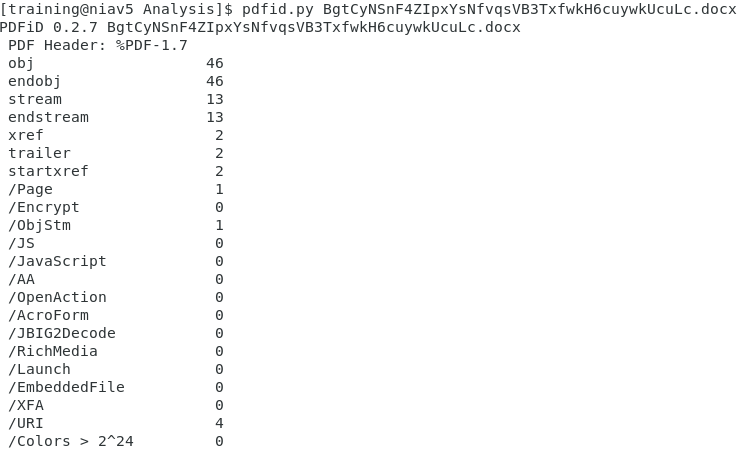
First, using pdfid.py:
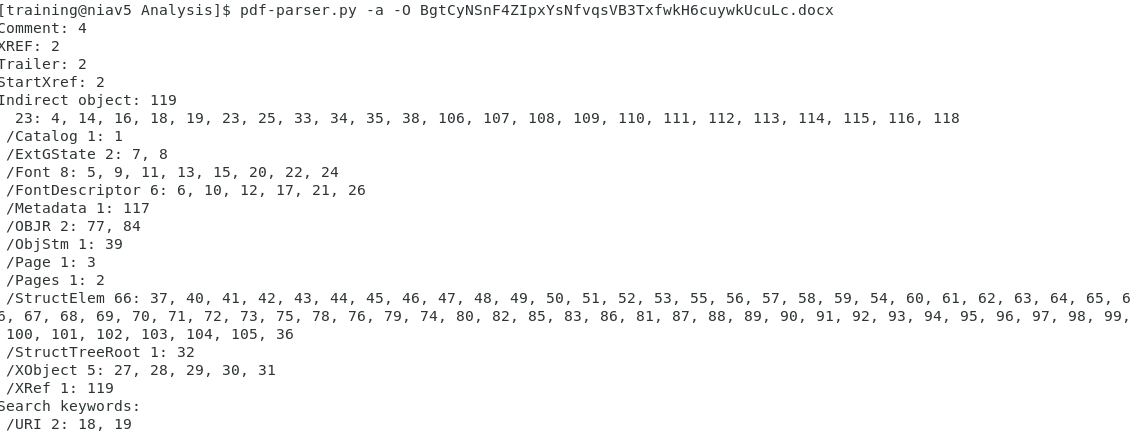
Something caught my eye where is shows /URI 4 items and some stream objects. Using the pdf-parser.py against the file like this:
Again, I see the file appears to have some URLs (/URI). With another pass, this time to get the URLs:
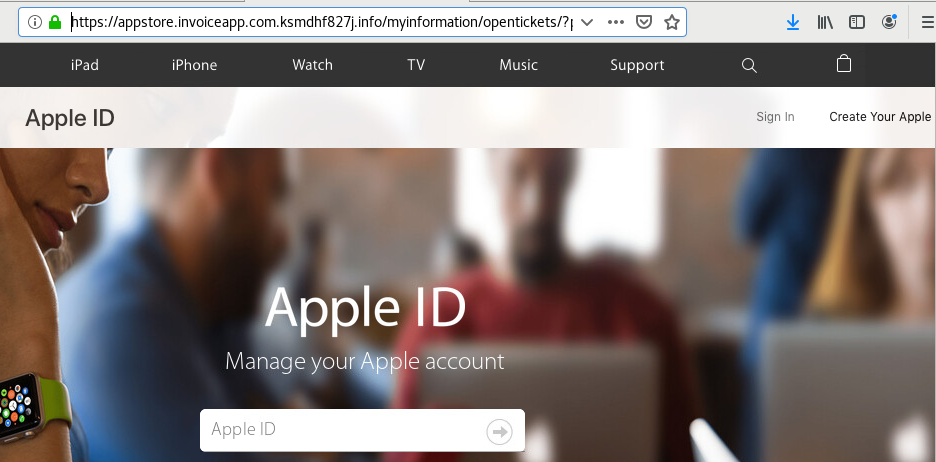
The URL isn't used to download malware to the host but to entice the user to login a fake Apple store to steal the user credentials.
Since the SSL certificate is valid (green lock), I open it up to see how long it has been register. Based on the certificate information, the certificate was issued 5 days ago by cPanel and active for the same amount of time:
[1] https[:]//appstore[.]invoiceapp[.]com.ksmdhf827j[.]info
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

.PNG)


Comments