German malspam pushes ZLoader malware
Introduction
Today's diary reviews German malicious spam (malspam) from Tuesday 2020-04-07 pushing ZLoader malware. Also known as Terdot or DELoader, ZLoader is the latest version or variant from this family of malware that has been active for years.
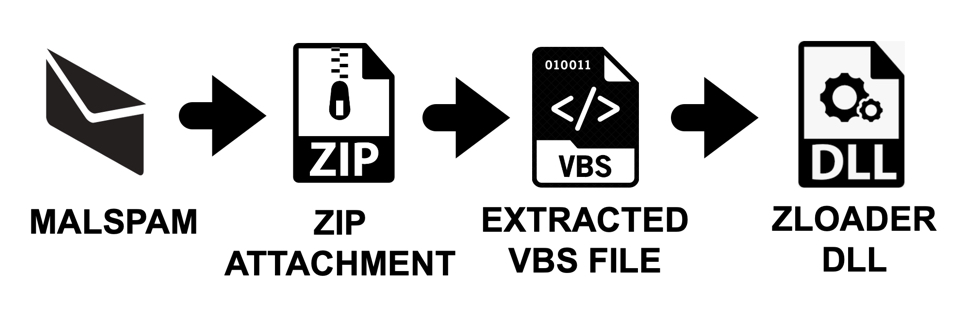
Shown above: Flow chart for this infection chain.
The malspam
I found two emails that contained zip archives for ZLoader. The attachments appear to be invoices for some sort of transaction.
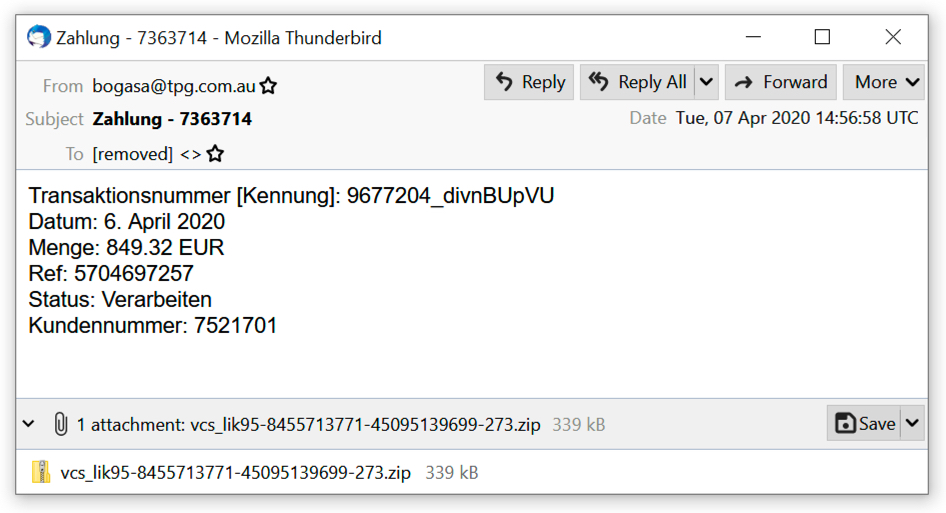
Shown above: First example of malspam pushing ZLoader.
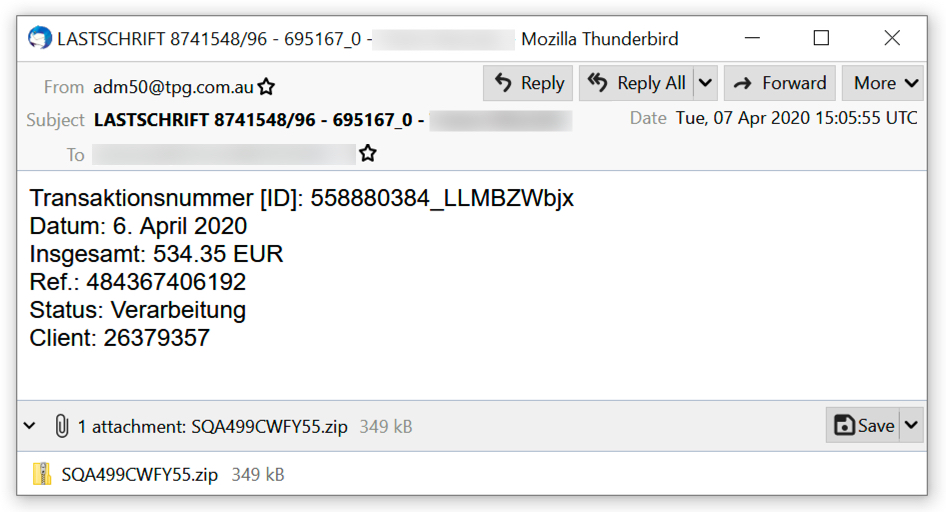
Shown above: Second example of malspam pushing ZLoader.
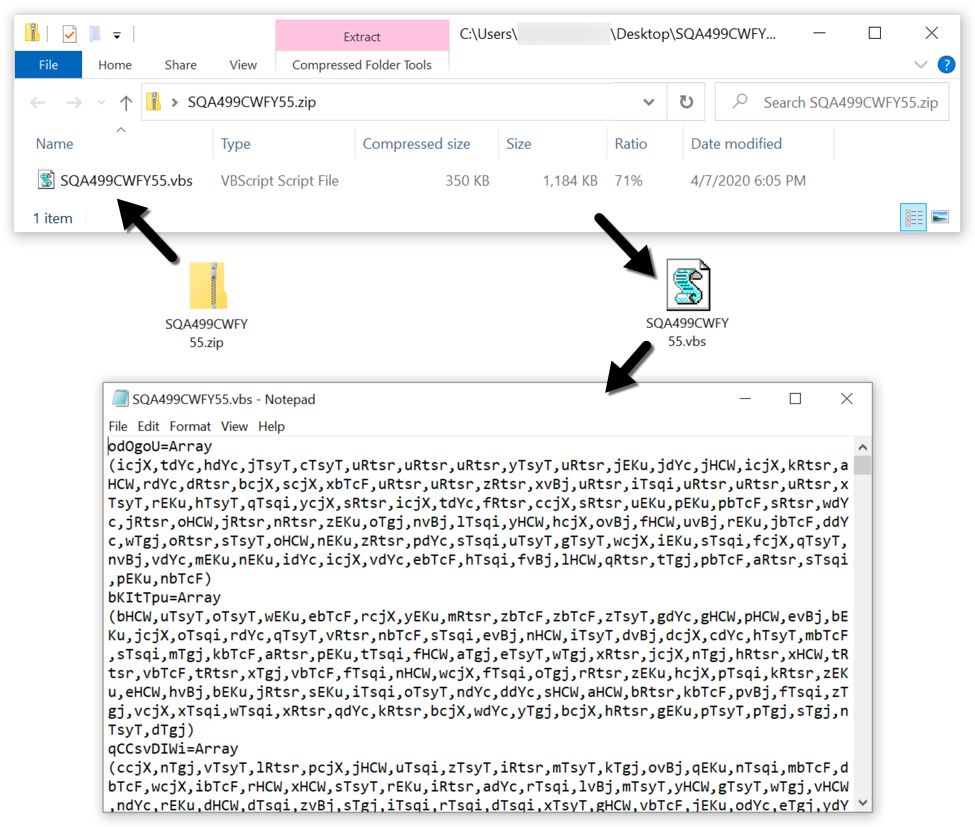
Shown above: Extracting a VBS file from one of the attachments.
The infection traffic
Network traffic caused by a ZLoader infection is all HTTPS, so to view the content, you must have created a decryption key when the infection traffic was first recorded. This is usually done using some sort of Man In The Middle (MITM) setup. I used my account with the Any.Run sandbox to use the MITM method to create a decryption key for the infection traffic (here is the analysis). I have a sanitized copy of the pcap and decryption key here. The following images show how to use the decryption key in Wireshark (in this case, Wireshark version 2.6.8 on a Debian host) to view the HTTPS traffic.
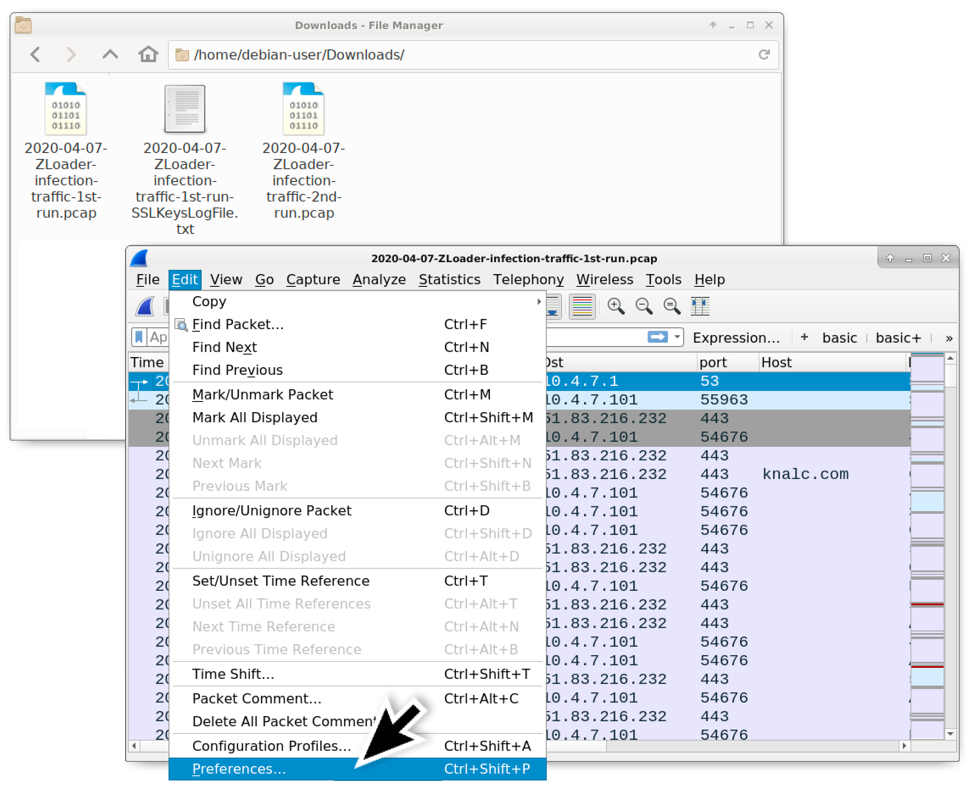
Shown above: After downloading the zip archive of the pcap data from my blog (link), open the first pcap in Wireshark, then go to the Preferences window.
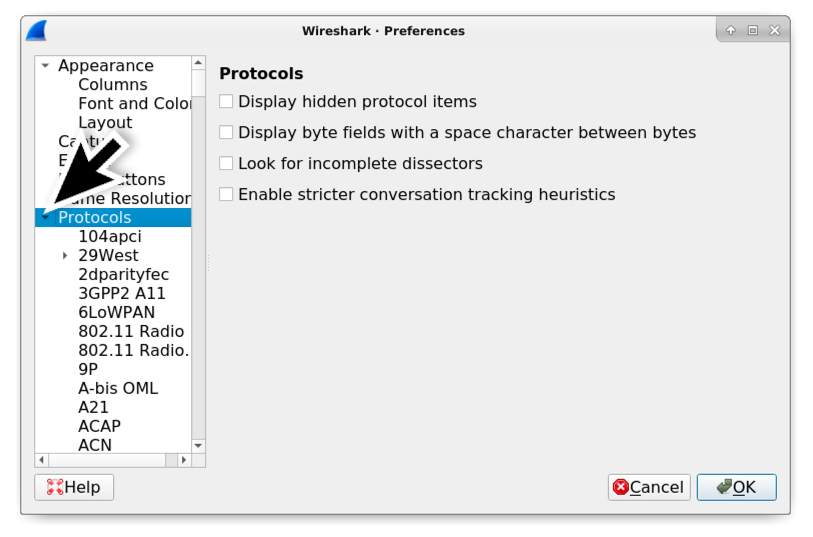
Shown above: In the Preferences window, expand the "Protocols" entry on the left.
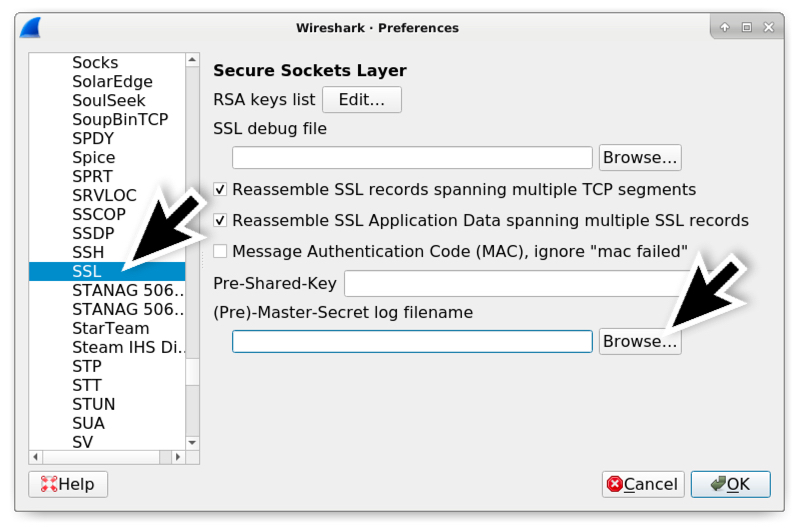
Shown above: If using Wireshark 2.x, scroll down and select SSL under the Protocols section. If using Wireshark 3.x, scroll down and select TLS. Browse for the (Pre)-Master-Secret log filename.
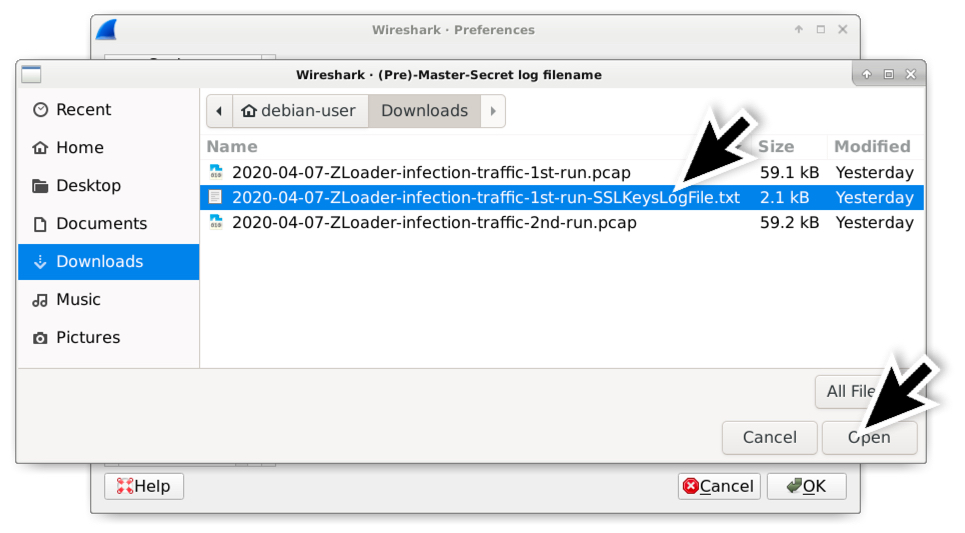
Shown above: Select the appropriate SSLKeysLogFile which should be the only text file in zip archive for the infection traffic.
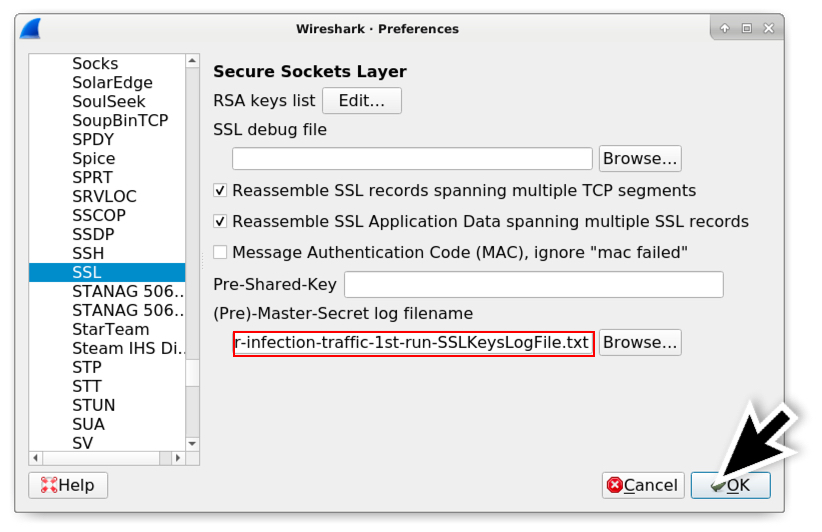
Shown above: Once you've selected the appropriate SSLKeysLogFile, click the OK button.
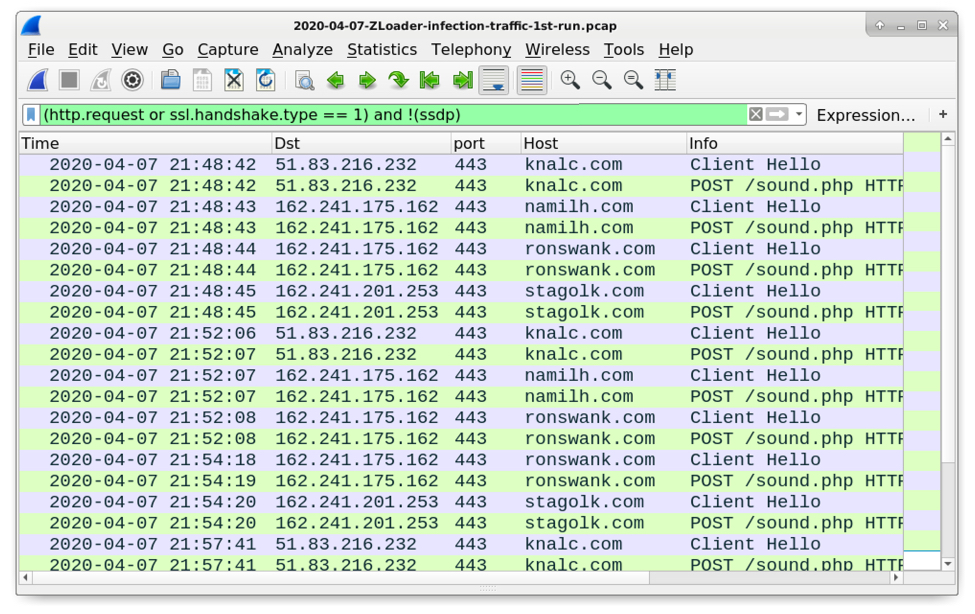
Shown above: Now when you filter on web traffic, Wireshark shows the associated HTTP requests within the HTTPS traffic.
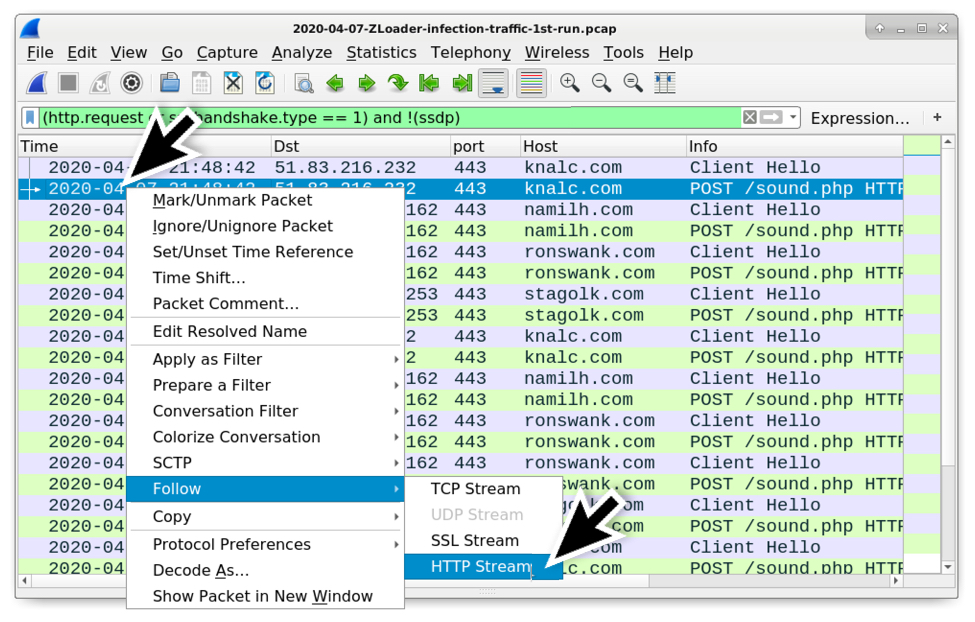
Shown above: After filtering on web traffic, now you can follow the HTTP stream for the HTTP requests that show up in the column display. Note: Follow HTTP stream, not TCP stream.
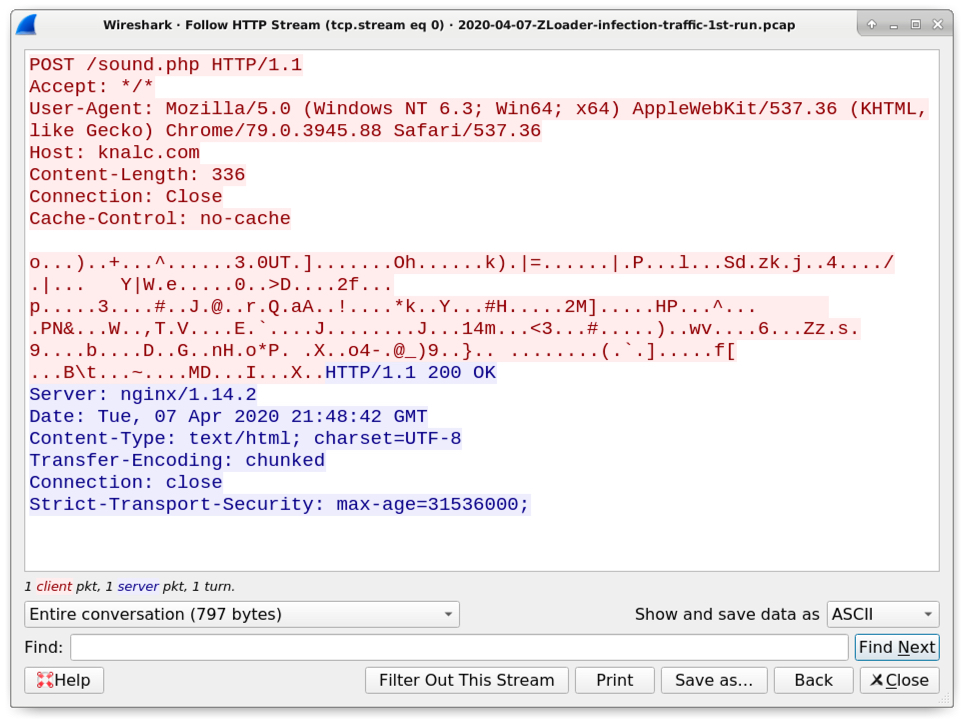
Shown above: An example of HTTP data within the HTTPS traffic caused by a ZLoader infection.
Forensics on an infected Windows host
The initial ZLoader DLL file is dropped to the infected user's AppData\Local\Temp directory. Even though this is a DLL, the file is initially dropped with an ".exe" file extension. But it is run as a DLL using rundll32.exe with DllRegisterServer as the entry point. When executed, ZLoader creates several folders under the infected user's AppData\Roaming directory and copies itself under one of those newly-created folders to become persistent. ZLoader is kept persistent through an update to the Windows registry.
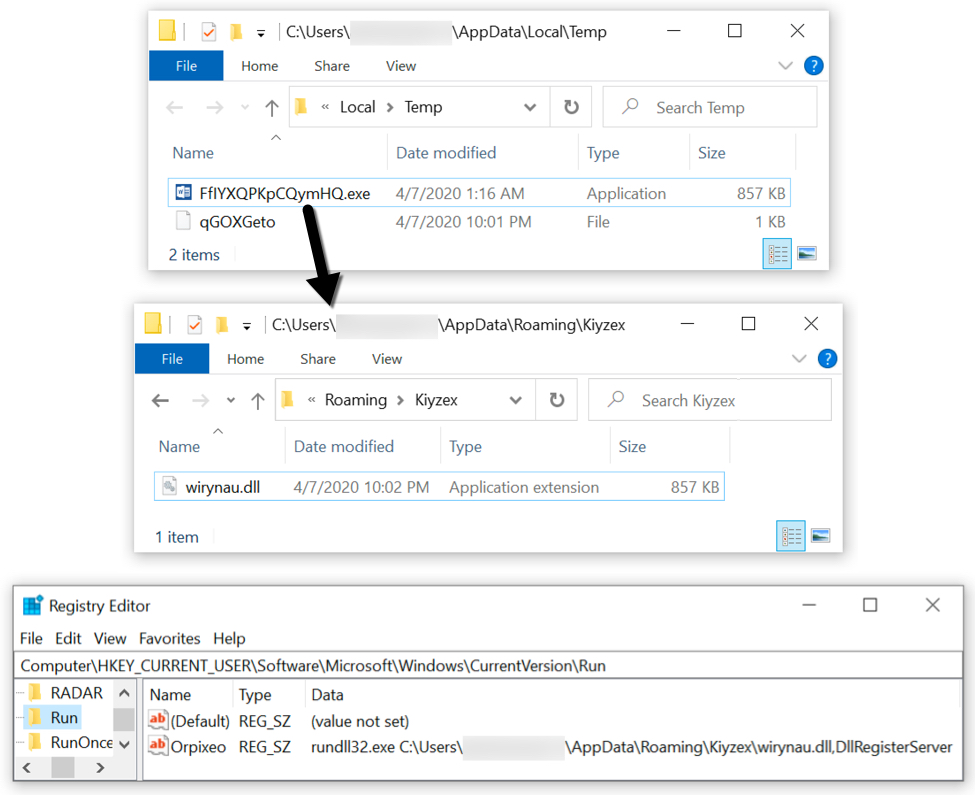
Shown above: A sample of ZLoader on my infected lab host.
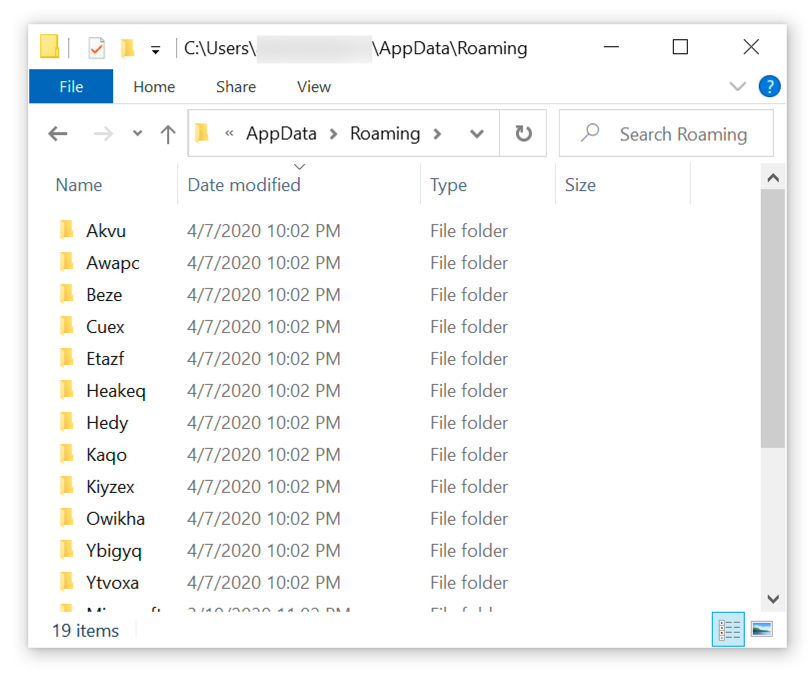
Shown above: Under the user's AppData\Roaming directory, we also find several decoy folders created during this ZLoader infection.
Indicators of Compromise (IoCs)
The following are email headers and attachment info from the two examples of ZLoader malspam I found through VirusTotal.
Email example 1 of 2:
- Received: from web-atmail1.tpgi.com.au (web-atmail1.tpgi.com.au [203.12.160.53])
- Date: Tue, 07 Apr 2020 14:56:58 UTC
- From: [email protected]
- Subject: Zahlung - 7363714
- Attachment name: vcs_lik95-8455713771-45095139699-273.zip
Example 2 of 2:
- Received: from web-atmail2.tpgi.com.au (web-atmail2.tpgi.com.au [203.12.160.131])
- Date: Wed, 08 Apr 2020 01:05:55 +1000
- From: [email protected]
- Subject: LASTSCHRIFT 8741548/96 - 695167_0 - [name removed]
- Attachment name: SQA499CWFY55.zip
The following information is from malware associated with the ZLoader infection from Tuesday 2020-04-07:
SHA256 hash: 763d2b64b0876a922ae47bd76114d9619376b9683216c35131d7e810fce9d630
- File size: 346,978 bytes
- File name: vcs_lik95-8455713771-45095139699-273.zip
- File description: Zip archive attached to first malspam example
SHA256 hash: 9d359f1af657d29feb6f009791bc5140359b0cbb53db8ca508aecd3a35a5719b
- File size: 1,196,653 bytes
- File name: vcs_lik95-8455713771-45095139699-273.vbs
- File description: VBS file extracted from zip archive attached to first malspam example
SHA256 hash: 64aa5ded721d64197e138b7d30c08f75efdea280df768fd12291aaaa3ab00570
- File size: 357,876 bytes
- File name: SQA499CWFY55.zip
- File description: Zip archive attached to second malspam example
SHA256 hash: 2fb86ee7329ab7f43d99812e15f113901629c73b99b703f335b131dd30f20ac4
- File size: 1,211,873 bytes
- File name: SQA499CWFY55.vbs
- File description: VBS file extracted from zip archive attached to second malspam example
SHA256 hash: 8d5a770975e52ce1048534372207336f6cc657b43887daa49994e63e8d7f6ce1
- File size: 877,056 bytes
- Initial file location: C:\Users\[username]\AppData\Local\Temp\FfIYXQPKpCQymHQ.exe
- Persistent file location: C:\Users\[username]\AppData\Roaming\Kiyzex\wirynau.dll
- File description: ZLoader malware DLL binary
- To run this DLL: rundll32.exe wirynau.dll,DllRegisterServer
- Note 1: The initial file name is different for each VBS file
- Note 2: The persistent file name and path under the Roaming folder is different each infection
The following are indicators of traffic from an infected Windows host:
- 51.83.216[.]232 port 443 (HTTPS) - knalc[.]com - POST /sound.php
- 162.241.175[.]162 port 443 (HTTPS) - namilh[.]com - POST /sound.php
- 162.241.175[.]162 port 443 (HTTPS) - ronswank[.]com - POST /sound.php
- 162.241.201[.]253 port 443 (HTTPS) - stagolk[.]com - POST /sound.php
- DNS query for mioniough[.]com (did not resolve to an IP address)
- DNS query for ergensu[.]com (did not resolve to an IP address)
Note: Infection traffic cycled through the above URLs and domain queries 3 times, then it started generating DNS queries for random 20-character alphabetic strings with .com as the top level domain (TLD). I've included some examples below.
- DNS query for jgqhigsjkulmsvvhshmk[.]com (response: No such name)
- DNS query for wapjdxlstholqwakofgi[.]com (response: No such name)
- DNS query for aiavxvlshmkweccksfky[.]com (response: No such name)
- DNS query for liswrfujohqsnbnohetn[.]com (response: No such name)
- DNS query for hciqylualwcnyvajdkqq[.]com (response: No such name)
- DNS query for pdtlshacpbacpnhcndpd[.]com (response: No such name)
- DNS query for kdacggcctwcavdgvpbmk[.]com (response: No such name)
- DNS query for wapwtpwciertrhkdaxrp[.]com (response: No such name)
- DNS query for shyjgiyhyegxeqqpdtya[.]com (response: No such name)
- DNS query for gccggcctwcerlshacpba[.]com (response: No such name)
- DNS query for cpnhcndpdkylibtlbeco[.]com (response: No such name)
- DNS query for bxhwpdkqdakbplfvfqwn[.]com (response: No such name)
- DNS query for bioonshmwrbecckfcavh[.]com (response: No such name)
Certificate issuer data for HTTPS traffic to knalc[.]com on 51.83.216[.]232:
- id-at-countryName=FR
- id-at-stateOrProvinceName=Paris
- id-at-localityName=Paris
- id-at-organizationName=orangeltd
- id-at-organizationalUnitName=site
- id-at-commonName=51.83.216.232
- pkcs-9-at-emailAddress=[email protected]
Certificate issuer data for HTTPS traffic to namilh[.]com and ronswank[.]com, both on 162.241.175[.]162, and stagolk[.]com on 162.241.201[.]253:
- id-at-countryName=AU
- id-at-stateOrProvinceName=Sydney
- id-at-localityName=Sydney
- id-at-organizationName=floraltd
- id-at-organizationalUnitName=site
- id-at-commonName=162.241.67.88
- pkcs-9-at-emailAddress=admin@flora/net
Final words
As usual, these types of infections are not very effective against a fully-patched and up-to-date computer running the latest version of Microsoft Windows. The default virus & threat protection settings should stop these samples of ZLoader from infecting a Windows 10 host. Real-time protection and Tamper Protection are designed to prevent such activity.
However, this remains a cat-and-mouse game, where malware authors are constantly adjusting their malware in an attempt to escape detection. With the low cost of distribution through email, and with poor security practices among potential victims, campaigns like those pushing ZLoader will remain cost-effective. I expect we will continue to see ZLoader in the coming weeks and months.
The emails, pcaps, malware, and a list of the above IoCs are available here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments