Microsoft August 2018 Patch Tuesday
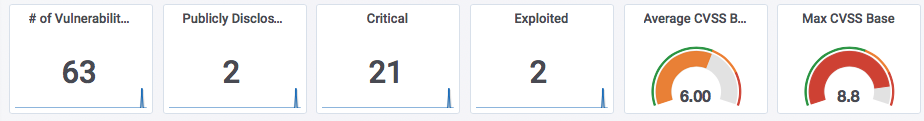
This month, Microsoft fixes 63 vulnerabilities. 2 of which have been publicly disclosed:
CVE-2018-8414 : This is the "Settings.ms" issue. These files were introduced in Windows 8, and they are used to create shortcuts to specific settings pages. The XML instructions for the link can lead to code execution and the user is not warned before opening the files. This has been widely exploited. For details, see the report by SpecterOps: https://posts.specterops.io/the-tale-of-settingcontent-ms-files-f1ea253e4d39
CVE-2018-8373: Not a lot of details here other than the fact that this is yet another scripting engine memory corruption issue. There have been plenty like it, so exploit writers likely have already a game plan how to write yet another exploit for this problem.
Dashboard: https://patchtuesdaydashboard.com
August 2018 Security Updates
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET Framework Information Disclosure Vulnerability | |||||||
| CVE-2018-8360 | No | No | Less Likely | Less Likely | Important | ||
| AD FS Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8340 | No | No | Less Likely | Less Likely | Important | 6.5 | 5.9 |
| August 2018 Adobe Flash Security Update | |||||||
| ADV180020 | No | No | - | - | Critical | ||
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||||
| CVE-2018-8266 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8380 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8381 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8384 | No | No | - | - | Critical | 4.2 | 3.8 |
| Device Guard Code Integrity Policy Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8204 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| CVE-2018-8200 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| Diagnostic Hub Standard Collector Elevation Of Privilege Vulnerability | |||||||
| CVE-2018-0952 | No | No | Less Likely | Less Likely | Important | 6.7 | 6.0 |
| DirectX Graphics Kernel Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8400 | No | No | Less Likely | Less Likely | Important | 7.0 | 6.3 |
| CVE-2018-8401 | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| CVE-2018-8405 | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| CVE-2018-8406 | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| GDI+ Remote Code Execution Vulnerability | |||||||
| CVE-2018-8397 | No | No | - | - | Critical | 8.8 | 7.9 |
| Internet Explorer Remote Code Execution Vulnerability | |||||||
| CVE-2018-8316 | No | No | Less Likely | Less Likely | Important | 6.4 | 5.8 |
| LNK Remote Code Execution Vulnerability | |||||||
| CVE-2018-8345 | No | No | More Likely | More Likely | Critical | 7.5 | 6.7 |
| CVE-2018-8346 | No | No | - | - | Important | 7.5 | 6.7 |
| Microsoft (MAU) Office Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8412 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Browser Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8357 | No | No | Less Likely | Less Likely | Important | 6.4 | 5.8 |
| Microsoft Browser Information Disclosure Vulnerability | |||||||
| CVE-2018-8351 | No | No | - | - | Important | 2.4 | 2.2 |
| Microsoft Browser Memory Corruption Vulnerability | |||||||
| CVE-2018-8403 | No | No | More Likely | More Likely | Critical | 4.2 | 3.8 |
| Microsoft COM for Windows Remote Code Execution Vulnerability | |||||||
| CVE-2018-8349 | No | No | Less Likely | Less Likely | Important | 7.0 | 6.3 |
| Microsoft Cortana Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8253 | No | No | - | - | Important | 4.0 | 3.6 |
| Microsoft Edge Information Disclosure Vulnerability | |||||||
| CVE-2018-8370 | No | No | - | - | Important | 3.1 | 3.1 |
| Microsoft Edge Memory Corruption Vulnerability | |||||||
| CVE-2018-8377 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8387 | No | No | - | - | Critical | 7.5 | 6.7 |
| Microsoft Edge Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8358 | No | No | - | - | Important | 4.7 | 4.2 |
| Microsoft Edge Spoofing Vulnerability | |||||||
| CVE-2018-8383 | No | No | - | - | Important | 4.3 | 3.9 |
| CVE-2018-8388 | No | No | - | - | Low | 5.4 | 4.9 |
| Microsoft Excel Information Disclosure Vulnerability | |||||||
| CVE-2018-8382 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| CVE-2018-8375 | No | No | Less Likely | Less Likely | Important | ||
| CVE-2018-8379 | No | No | More Likely | More Likely | Important | ||
| Microsoft Exchange Memory Corruption Vulnerability | |||||||
| CVE-2018-8302 | No | No | Less Likely | Less Likely | Critical | ||
| Microsoft Exchange Server Tampering Vulnerability | |||||||
| CVE-2018-8374 | No | No | Unlikely | Unlikely | Moderate | ||
| Microsoft Graphics Remote Code Execution Vulnerability | |||||||
| CVE-2018-8344 | No | No | More Likely | More Likely | Critical | 7.8 | 7.0 |
| Microsoft Guidance to mitigate L1TF variant | |||||||
| ADV180018 | No | No | Less Likely | Less Likely | Important | 7.1 | 7.1 |
| Microsoft Office Defense in Depth Update | |||||||
| ADV180021 | No | No | Less Likely | Less Likely | |||
| Microsoft Office Information Disclosure Vulnerability | |||||||
| CVE-2018-8378 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft PowerPoint Remote Code Execution Vulnerability | |||||||
| CVE-2018-8376 | No | No | - | - | Important | ||
| Microsoft SQL Server Remote Code Execution Vulnerability | |||||||
| CVE-2018-8273 | No | No | Less Likely | Less Likely | Critical | ||
| Scripting Engine Memory Corruption Vulnerability | |||||||
| CVE-2018-8371 | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| CVE-2018-8372 | No | No | - | - | Critical | 6.4 | 5.8 |
| CVE-2018-8373 | Yes | Yes | Detected | Less Likely | Critical | 6.4 | 5.8 |
| CVE-2018-8385 | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| CVE-2018-8389 | No | No | More Likely | More Likely | Important | 6.4 | 5.8 |
| CVE-2018-8390 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8353 | No | No | More Likely | More Likely | Important | 6.4 | 5.8 |
| CVE-2018-8355 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8359 | No | No | - | - | Critical | 5.3 | 4.8 |
| Win32k Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8399 | No | No | Less Likely | Less Likely | Important | 7.0 | 6.3 |
| CVE-2018-8404 | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| Windows GDI Information Disclosure Vulnerability | |||||||
| CVE-2018-8394 | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| CVE-2018-8396 | No | No | - | - | Important | 4.7 | 4.2 |
| CVE-2018-8398 | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| Windows Installer Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8339 | No | No | Less Likely | Less Likely | Important | 7.4 | 6.7 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8347 | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| Windows Kernel Information Disclosure Vulnerability | |||||||
| CVE-2018-8341 | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| CVE-2018-8348 | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| Windows NDIS Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8342 | No | No | - | - | Important | 7.0 | 6.3 |
| CVE-2018-8343 | No | No | Less Likely | Less Likely | Important | 7.0 | 6.3 |
| Windows PDF Remote Code Execution Vulnerability | |||||||
| CVE-2018-8350 | No | No | Less Likely | Less Likely | Critical | 4.2 | 3.8 |
| Windows Shell Remote Code Execution Vulnerability | |||||||
| CVE-2018-8414 | Yes | Yes | More Likely | More Likely | Important | 4.8 | 4.8 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|


Comments