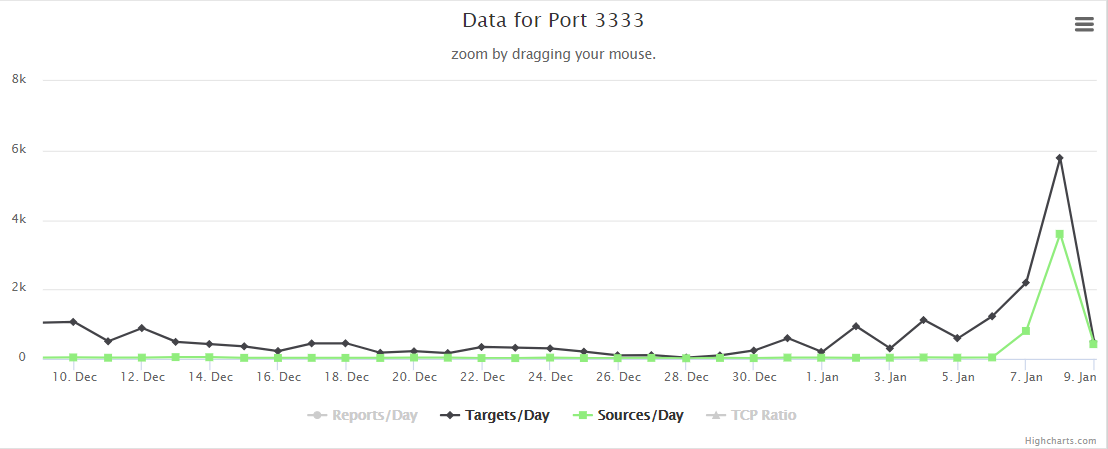
What is going on with port 3333?
We've seen a spike over the last day or so in reports of apparent scanning on TCP port 3333. I have serious doubts that anyone is actually looking for DEC Notes which is the registered IANA use for this port. While we're getting our own honeypots set up, I figured I'd ask our readers, do you have packets and/or any idea what is going on here? Please let us know in the comments or via our contact page. Thanx in advance.
Update: 2018-01-09 03:00 The original version of this diary inadvertantly said the traffic was UDP, the traffic that I am seeing in my logs at home is actually TCP. My apologies for the confusion.
Update: 2018-01-10 00:00 UTC The recurring theme in comments and email we've received suggests that some of the recent Monero miner malware samples are sending their results back to C2 servers on port 3333, so perhaps folks are trying to find and steal the illgotten cryptocurrency. I still haven't examined any traffic captured by our honeypots to confirm or refute that that is what they are looking for.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
Upcoming Courses Taught By Jim Clausing
| LINUX Incident Response and Threat Hunting | London | Jul 7th - Jul 12th 2025 |




Comments
185.62.188.88
5.188.86.157
77.72.85.106
109.248.9.248
5.188.203.54
191.101.167.167
77.72.85.105
51.15.93.216
181.214.87.239
77.72.85.106
5.188.86.156
181.214.87.11
77.72.85.10
77.72.82.72
this is what we see hitting this port from 01/16 - 01/22
Anonymous
Jan 23rd 2018
7 years ago
https://gophish.gitbooks.io/user-guide/content/installation.html
Anonymous
Jan 24th 2018
7 years ago