Traffic Patterns For CryptoWall 3.0
This is a guest diary submitted by Brad Duncan.
Various sources have reported version 3 of CryptoWall has appeared [1] [2] [3]. This malware is currently seen from exploit kits and phishing emails. CryptoWall is one of many ransomware trojans that encrypt the personal files on your computer and demand a bitcoin payment before you can unlock them.
I got a sample on Wednesday, January 14th 2015 while infecting a virtual machine (VM) from a malicious server hosting the Magnitude exploit kit.
If you're registered with Malwr.com, you can get a copy of this CryptoWall 3.0 sample at:
https://malwr.com/analysis/MDA0MjIzOGFiMzVkNGEzZjg3NzdlNDAxMDljMDQyYWQ/
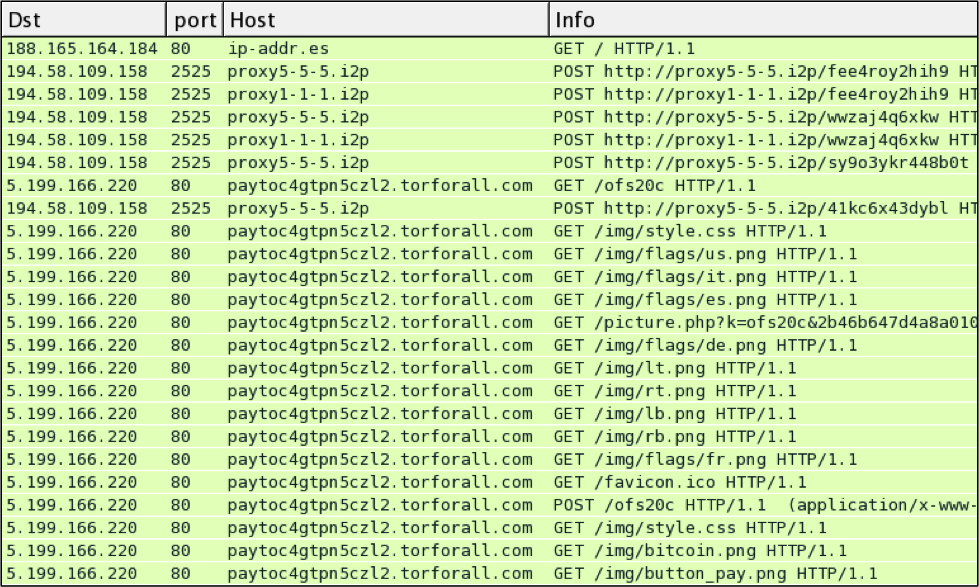
Let's look at the traffic from my infected VM:
In this example, the infected VM checked ip-addr.es to determine its public IP address. Then the VM communicated with a server at 194.58.109.158 over a non-standard HTTP port. In this case it was port 2525, but I saw different ports in other hosts I've infected with this sample.
Finally, the user viewed a web page for the decrypt instructions at 5.199.166.220.
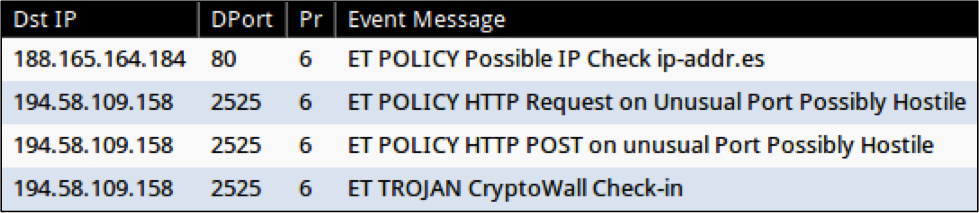
When monitoring the infection traffic with Security Onion [5], we see an EmergingThreats alert for CryptoWall check-in [4].
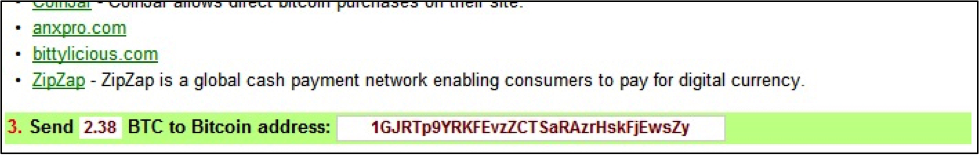
The decryption instructions specify the following bitcoin account for a ransom payment: 1GJRTp9YRKFEvzZCTSaRAzrHskFjEwsZy
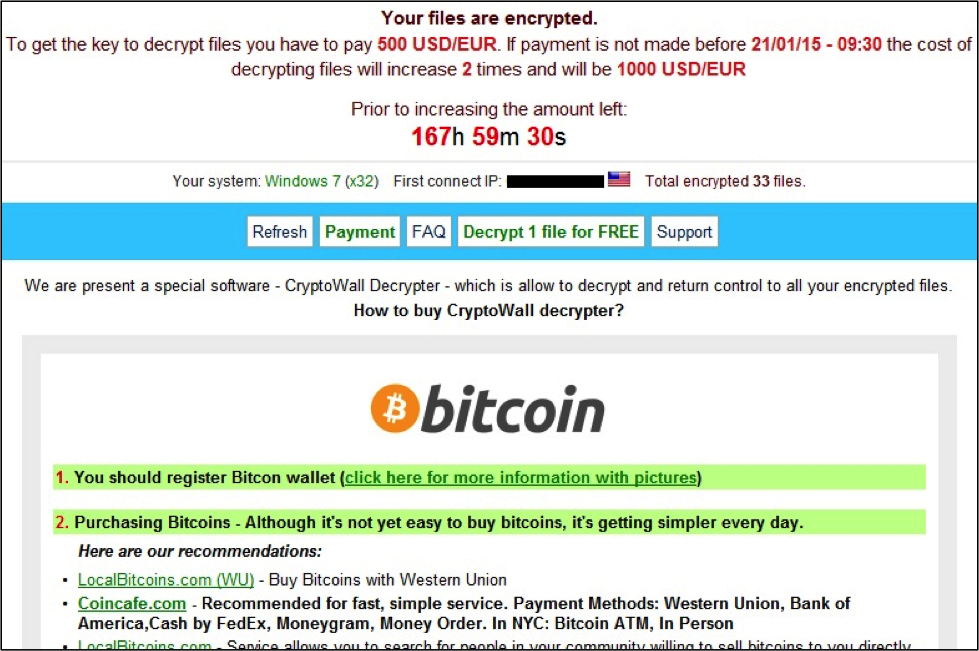
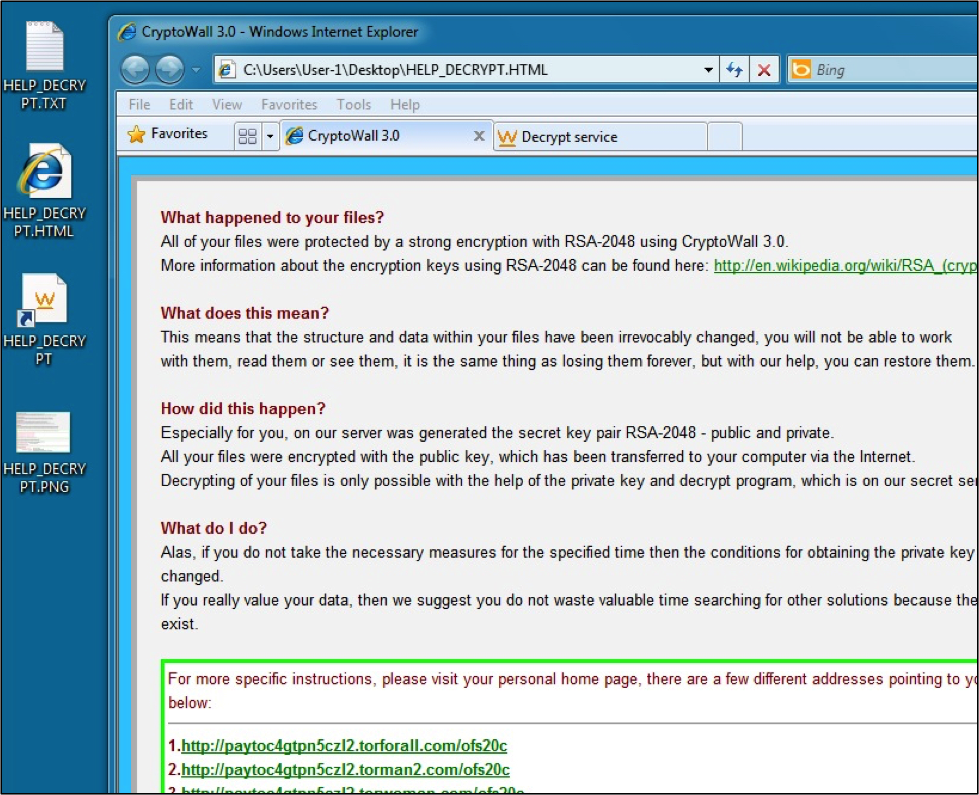
Here's what the user would see on their desktop screen:
----------
Brad Duncan is a Security Researcher at Rackspace, and he runs a blog on malware traffic analysis at http://www.malware-traffic-analysis.net
References:
[1] http://malware.dontneedcoffee.com/2015/01/guess-whos-back-again-cryptowall-30.html
[2] http://www.bleepingcomputer.com/forums/t/563169/after-a-brief-hiatus-malware-developers-release-cryptowall-3/
[3] https://forums.malwarebytes.org/index.php?/topic/163485-cryptowall-30/
[4] http://doc.emergingthreats.net/2018452
[5] http://blog.securityonion.net/p/securityonion.html
| Application Security: Securing Web Apps, APIs, and Microservices | Washington | Jul 14th - Jul 19th 2025 |



Comments
Anonymous
Jan 19th 2015
1 decade ago
Anonymous
Jan 19th 2015
1 decade ago
https://www.virustotal.com/en/file/9e06d2ce0741e039311261acc3d3acbaba12e02af8a8f163be926ca90230fa89/analysis/
Anonymous
Jan 19th 2015
1 decade ago
Anonymous
Jan 19th 2015
1 decade ago
Anonymous
Jan 27th 2015
1 decade ago