The Other Side of Critical Control 1: 802.1x Wired Network Access Controls
Today’s story is a short how-to on implementing 802.1x authentication for wired switch ports. In other words, workstations have to authenticate to be allowed on the wired network (just like your wireless network should be configured). I was actually surprised to see 802.1x as part of the CIS Critical Control #1, where you’d expect “hardware inventory” stuff to go – it’s actually CC 1.6, 1.7 and 1.8. But this does make sense, this not only controls where and when your gear can authenticate, but also controls the access that the “not your gear” stuff has (if any) when that stuff tries to connect.
So why do people want this, and why is it part of the Critical Controls? Because it really is about controlling both your known and unknown inventory. Known devices authenticate properly, and are given access to the network. Unknown devices (visitors, or unsanctioned gear of any kind) are either denied access or shuffled off to a jail or guest VLAN. Either way, the access requests for the “unknown” devices are all logged and can then be investigated if that’s the next step in your organization. Only known inventory is allowed access to the network.
Before we dive into this, 802.1x is a method for controlling the access of workstation inventory. I have never seen this deployed for servers. I'm sure that there's a corner case where it makes sense inside of a datacenter, but I haven't found one (please let us know via our comment form if you have). So this configuration is generally for workstations and workstation switches only.
Infrastructure Components
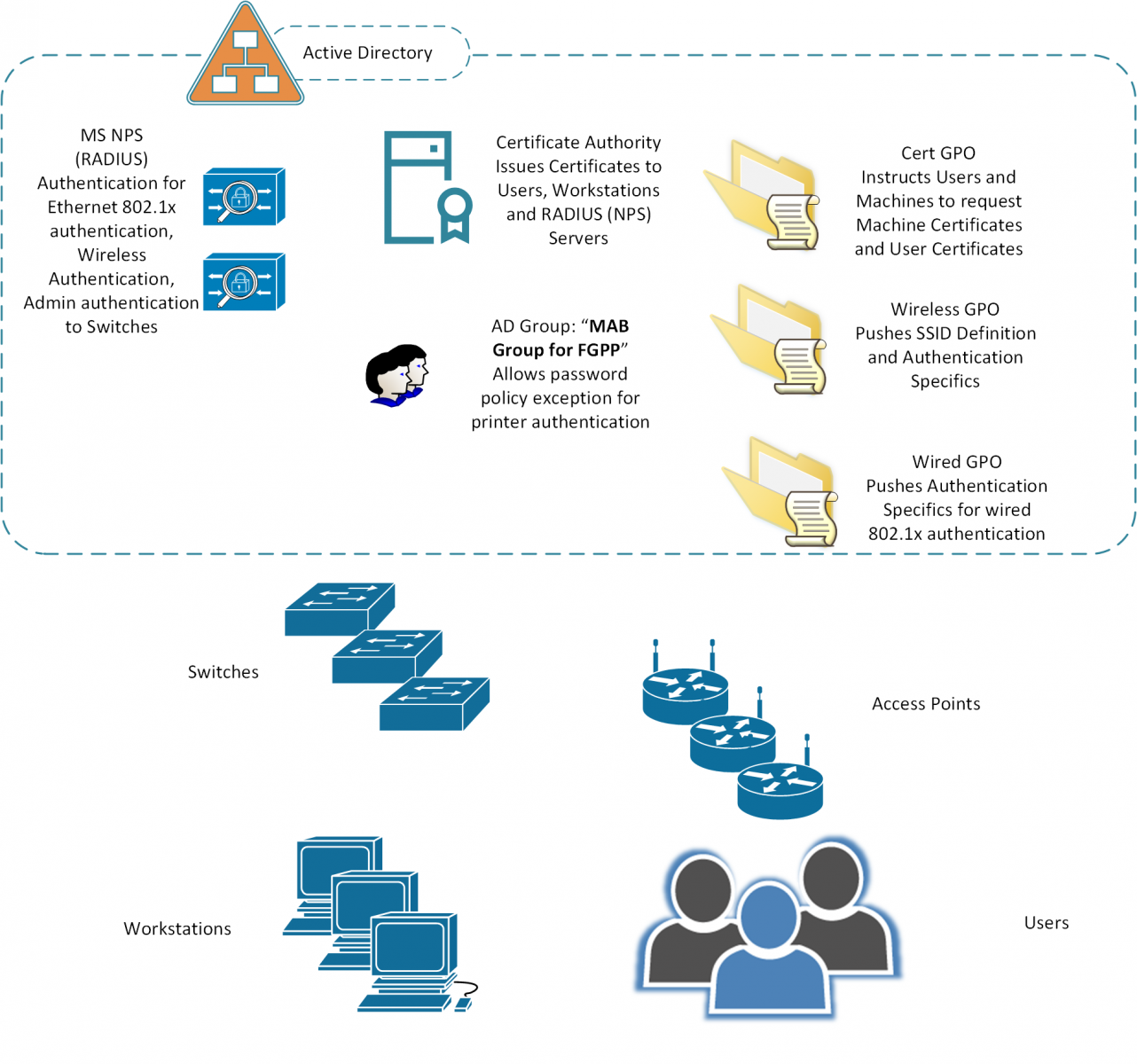
The diagram below outlines the various systems components used in Network Authentication (802.1x) for both wired and wireless networks. The assumptions here are:
- Microsoft Active Directory
- The “free” Microsoft CA and Network Policy Server (RADIUS) are both used
- Group Policies and the other MS automation is used to make the various processes and policies work
Authentication Sequences - Wired Networking
Domain Member Workstations (also anything that's been issued a Cert manually)
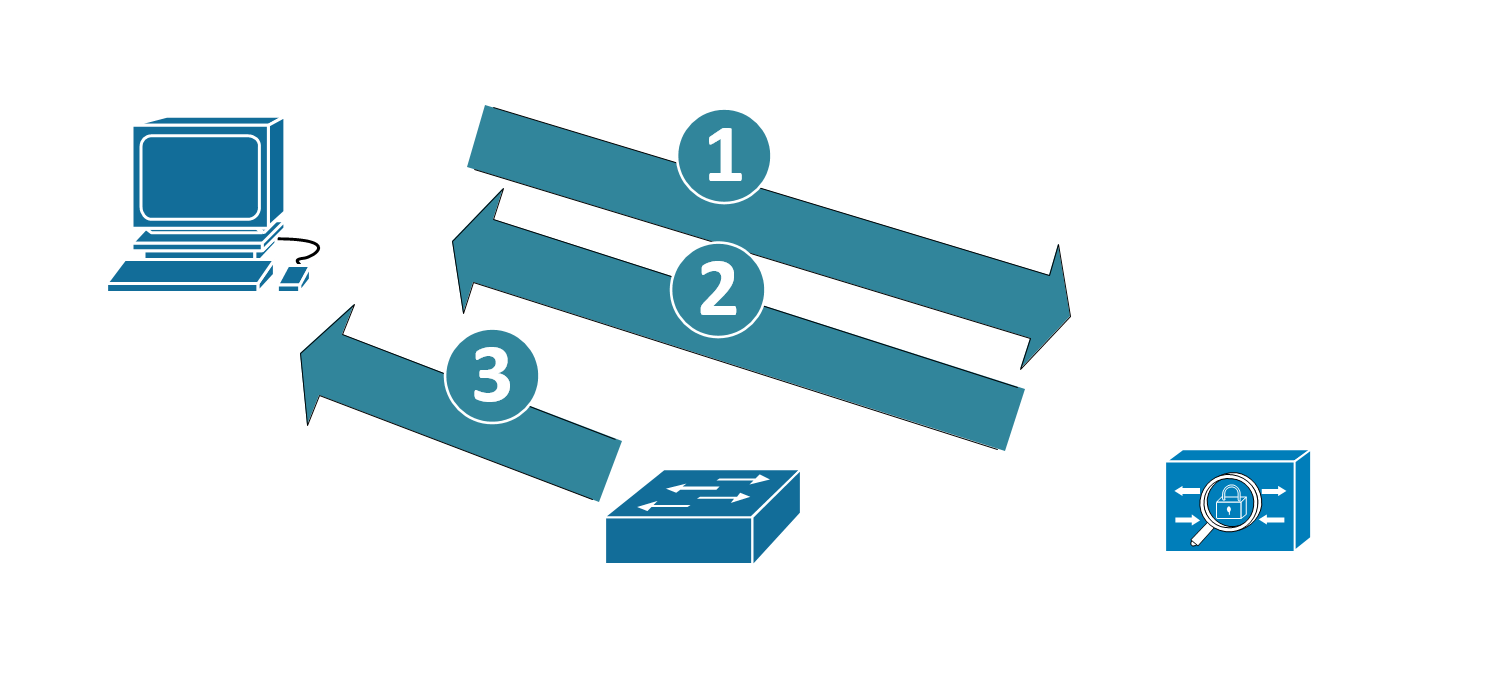
- The workstation uses its certificate to authenticate to the RADIUS Server
- In turn, the RADIUS server also uses its certificate to authenticate to the workstation, to prove that it’s a trusted RADIUS host
- When authentication is complete, the device is permitted
- If required, after the user logs in, the user certificate can be used to authenticate the user to the network as well.
- If the authentication fails, the user is not on the network – they might be in a guest vlan, a “failed authentication” vlan, or simply blocked from network access altogether (read on to the switch config section for more details)
- And yes, the “purist” 802.1x diagram has about 15 more steps and arrows, but I did say “brief” in my description of this article J
MAC Address Authentication / Bypass
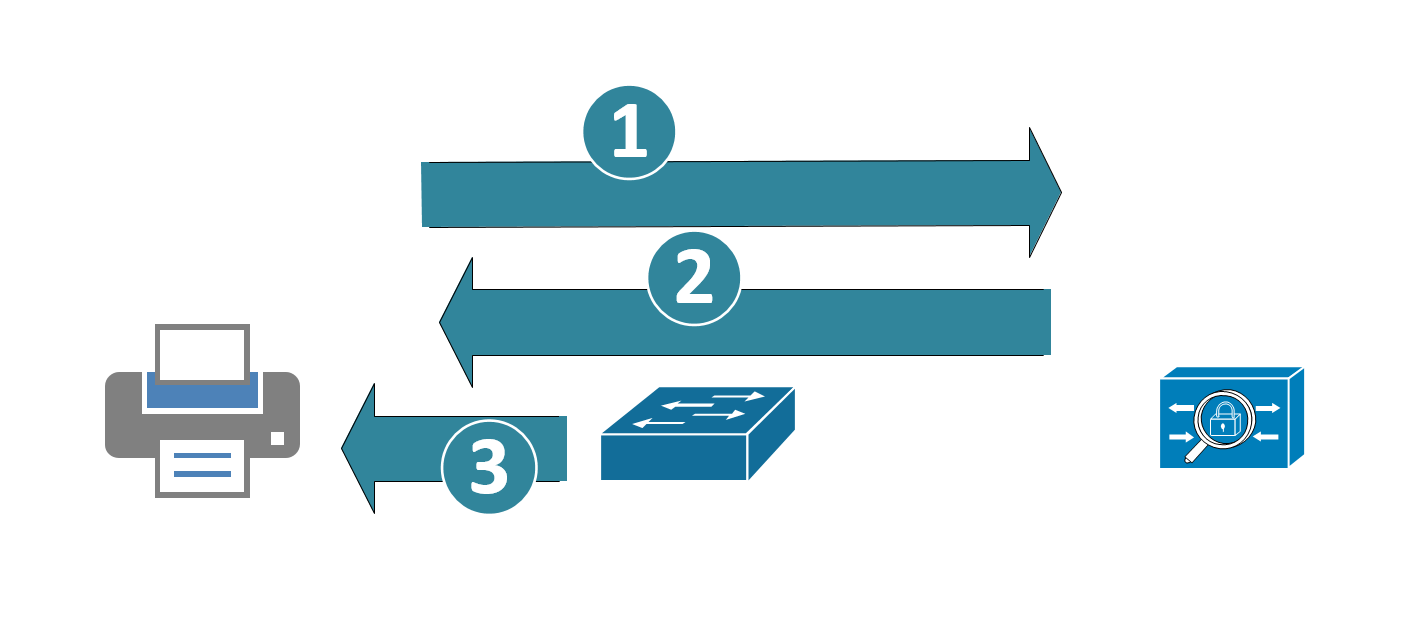
Printers can be issued certificates and work exactly like workstations, but in many cases the printers are outsourced, or if they do own them, a majority of them will be so old (or so cheap) that they won't support 802.1x authentication. In those cases, often the client opts to use MAC Address Bypass (MAB) authentication to authenticate the printers. In this case:
- The switch acts as a “proxy” sort-of. The switch collects the MAC address of the device, then uses it to authenticate to the RADIUS host, using the MAC address for both the userid and password
- The RADIUS server authenticates that to AD. The RADIUS server then permits the access if that account is found.
- The switch port permits the device (or denies if the account does not authenticate)
The problem with this is that MAC address spoofing is not a challenge for most attackers. In fact, you could likely automate something like this with a Raspberry Pi (discover the printer address, and present it out a second Ethernet – or even just act as a transparent bridge).
Wired Telepohones
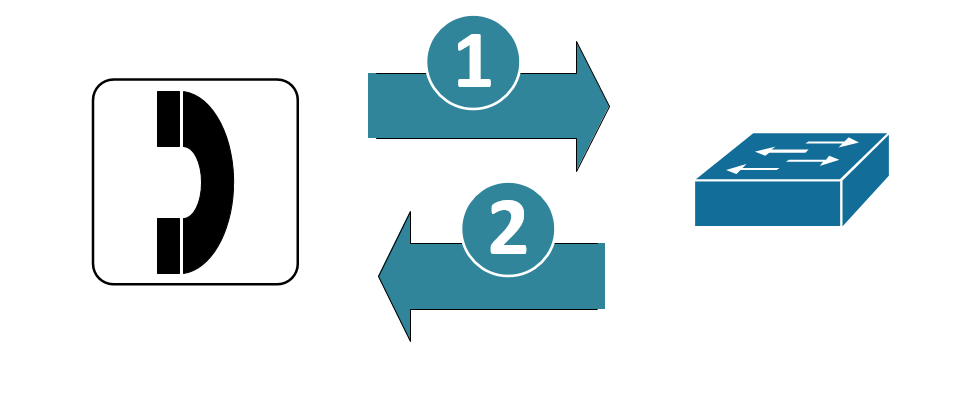
Cisco wired telephone handsets identify themselves as such using CDP (Cisco Discovery Protocol) and LLDP (Link Layer Discover Protocol). In many implementations the switch port “trusts” the handsets, and places them on a dedicated voice VLAN. Telephone handsets do not authenticate in this implementation.
The problem here is obvious, the handsets are simply trusted – and both CDP and LLDP are easily spoofed.
Wired handsets (Cisco in particular, but certainly most other major brands as well) can be issued certificates by their management application – the Cisco implementation uses “LSC” (Locally Significant Certificates). In some cases the management app can work as a subordinate CA to the enterprise CA (which in our fictitious company is a Microsoft Certificate Server). In other cases, the voip management app is a CA all on its own, in that design you’d need a separate policy in NPS, or maybe even a separate RADIUS host for the phones.
CERTIFICATE GOTCHAS
|
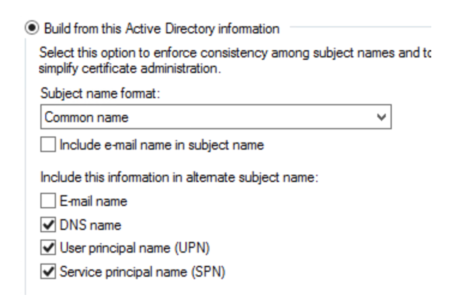
Machine Certificates In the MS Certificate Authority, ensure that the machine certificate template specifies the FQDN of the host in its SAN (Subject Alternative Name) field. Without this, Windows 10 stations will fail on authentication, as they present their FQDN as their station name (earlier versions of Windows presented their CN – common name).Certificate Authority. What this normally means is that in the SAN field, you specify the DNS name, UPN and SPN. |
|
|
User Certificates Similarly, the fields for the User Certificates are important – use the Fully Distinguished name and (at least) the UPN in the SAN field: |
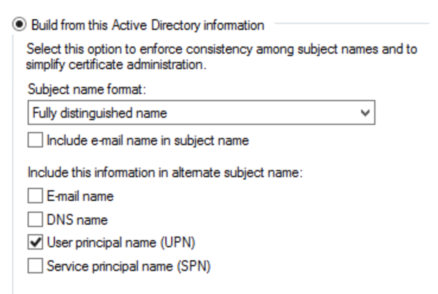 |
|
RADIUS Server Certificates You might think that a standard Server Certificate would work here, but the CA Template for RADIUS servers *must* be based on the “RAS and IAS Servers” template, or it just plain won’t work. |
Group Policies
User and Computer Certificates
This GPO forces Users and Computers to request Certificates from the Certificate Authority. This process initiates a “CSR” (Certificate Signing Request). The CA automatically processes all CSRs from domain member workstations and users, and issues the requested certificate. Push this certificate out first, and ensure that most or (preferably) all workstations have their certs before you proceed on.
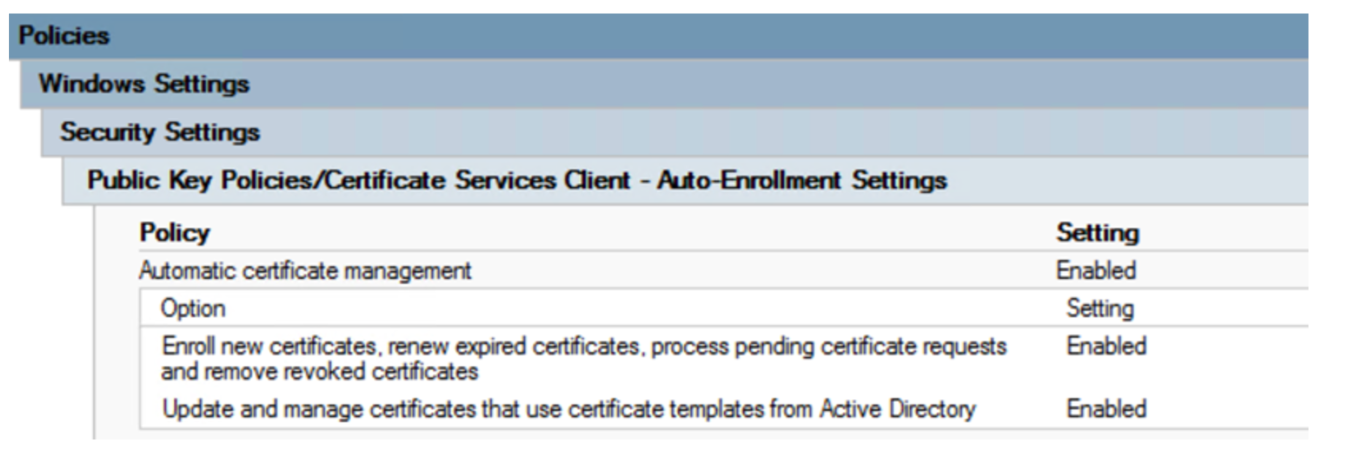
Wired Authentication GPO
This GPO governs authentication of wired workstations, using the 802.1x protocol.
The key points in this GPO are:
- 802.1x is authenticated
- Certificates are used for authentication (the selection for “Smart Card or Certificate” is made)
- Only the Computer Certificate is used
- The CA is authenticated, and only the enterprise CA can be used
- The user is never prompted to allow certificates from other CAs
- Disabling the enforcement of 802.1x at the client allows the use of this workstation on other networks (home Ethernet networks for instance)
This GPO also needs to be pushed out with some “wait time” factored in, before you can configure your switches. This ensures that when you set the enforcement on the switch policy, the workstations are able to authenticate. This GPO starts a new service on the workstations, “Wired AutoConfig”. Checking for this service in a running state is a handy way to ensure that your workstations are “ready to roll” for 802.1x.
The fun part here is that if machines don’t reboot or cycle power after they get this GPO, the service won’t start. And with Windows 7 and 10, it’s really common now to see machines only reboot for patches – people just seem to lock, sleep or hibernate them anymore. You may need to enforce a reboot or manually start the service with a script to get this step completed.
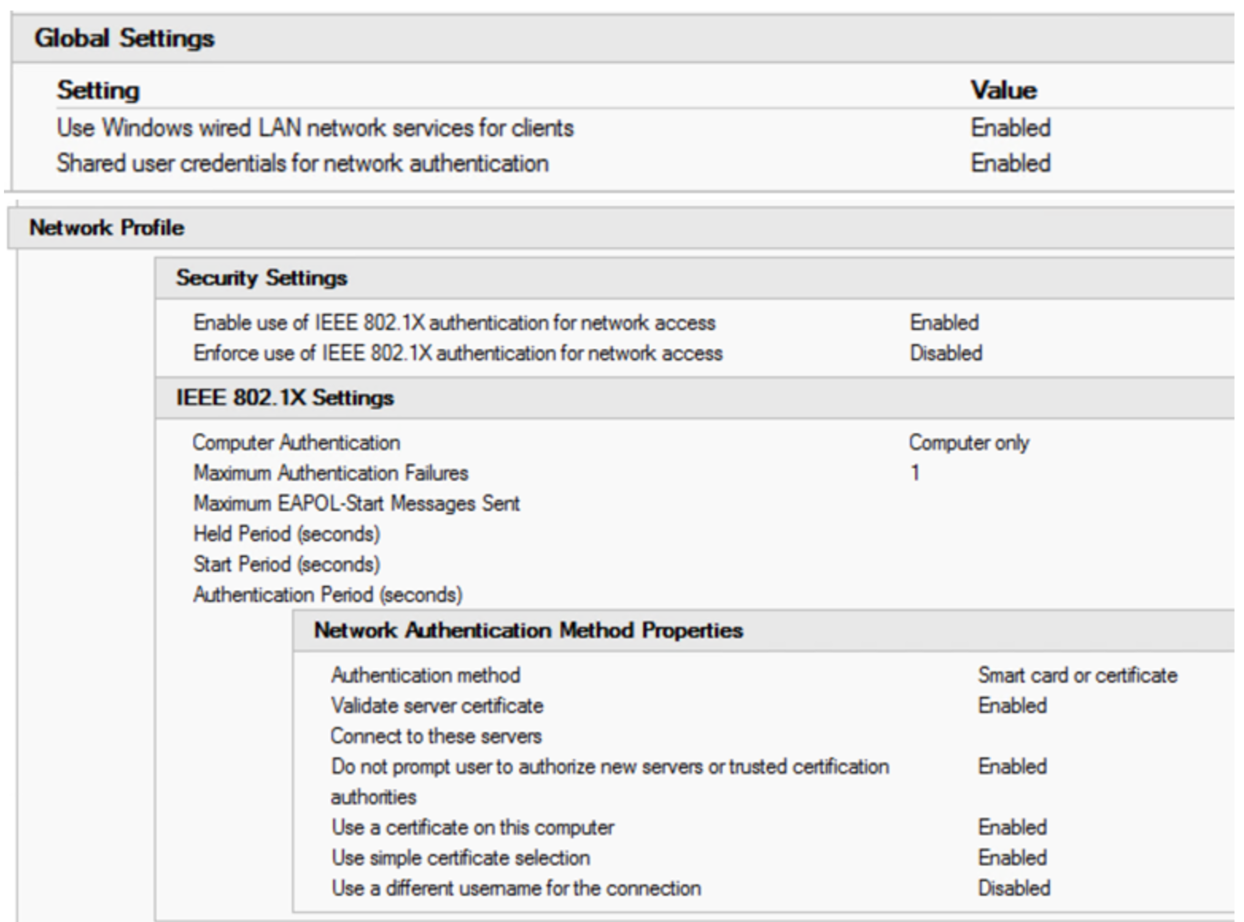
RADIUS Server Configuration
Wired Authentication using 802.1x
The radius policy for wired 802.1x is set up with:
Conditions:
- NAS Port Type = Ethernet
- Windows Groups = Domain Computers OR Domain Users
- Authentication Type = EAP
- Client Friendly Name = <a regex that encompasses your workstation switch names>
- You can see above that the 1980’s (or pick your decade) mantra “Naming Conventions are important” is still alive and well!
Settings:
- EAP Configuration = Configured
- Ignore User Dial-in Properties = True
- Access Permission = Grant Access
- EAP Method = Microsoft Smart Card or other Certificate
- NAP Enforcement = Allow Full Network access (you can set an ACL if you want)
- Tunnel Medium-Tyupe = 802
- Tunnel-Pvt-Group-ID = <the VLAN number to assign for successful authentication>
- Tunnel Type = VLAN
Not that you can also set a VLAN for non-compliant hosts, normally this is set on the switch port, and is set to some internet-only “guest” VLAN, or else a “jail” VLAN where there are just enough resources for the helpdesk to remediate your computer (see the switch section of this article for those settings)
MAC Address Bypass (MAB) - Printer Authentication
If you choose to implement MAB, you’ll need to define a group that the printer “accounts” will be in. Using Fine Grained Password Policy (FGPP), you’ll want to relax your password policy enforcement for these accounts. Also set those accounts so they can’t actually login to the domain.
The printers get the same policy as the workstations in NPS, except:
- Set the authentication type as unencrypted / PAP instead of EAP
- The membership should be to your MAB / FGPP group rather than the entire domain
- This policy will need to be ordered before the Wired NPS Policy
Printer Password Policy
The default domain policy enforces a password policy, which denies accounts the use of their account name as their password – for instance the user “Joe User”, with the userid of “juser”, cannot use “juser” as their password.
To make things work for MAC address authentication, use a “fine grained password policy” (FGPP) that relaxes this requirement for printer accounts, which use their MAC address for both userid and password in the MAB (MAC Address Bypass) implementation. This policy is illustrated below, and is applied only to the group “MAB Group for FGPP”, which is also shown:
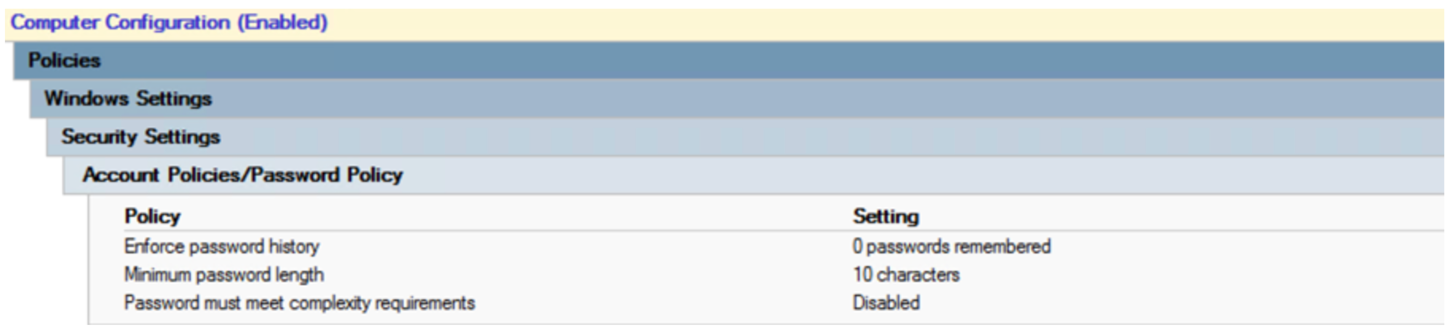
Apply this policy to the OU or the AD Group that the printers are in.
Switch Configuration
Of course you can do 802.1x authentication on just about any name-brand switch. I chose a Cisco switch as an example for this story - all features are implemented, and the config is fairly simple. Other switch vendor configurations will be similar(ish) to this.
First, the switch configuration is set up to allow 802.1x authentication, and the authentication source is pointed to (at least) 2 RADIUS hosts.
radius server RADIUS01
address ipv4 <radius server ip 01> auth-port 1812 acct-port 1813
key <some key>
radius server RADIUS02
address ipv4 <radius server ip 02> auth-port 1812 acct-port 1813
key <some key>
aaa group server radius RADIUSGROUP
server name RADIUS01
server name RADIUS02
dot1x system-auth-control
aaa authentication dot1x default group RADIUSGROUP
aaa accounting dot1x default start-stop group RADIUSGROUP
Next, the individual ports are configured. A typical workstation / phone / printer port is shown here:
|
interface GigabitEthernetx/0/y |
|
|
description some description goes here |
|
|
switchport access vlan 101 |
The “native vlan”, also the VLAN assigned for successful 802.1x authentication |
|
switchport mode access |
|
|
switchport voice vlan 105 |
Voice VLAN |
|
trust device cisco-phone |
This tells 802.1x to “trust” phones. Not recommended, use LSC (Locally Significant Certificates) or equivalent instead. If LSCs are used, this line should be removed |
|
authentication event fail action next-method |
Fail to successive authentication methods (see below) |
|
authentication event server dead action authorize voice |
Allow voice VLAN access even if RADIUS servers are down |
|
authentication order dot1x mab |
Try 802.1x authentication first, then MAB |
|
authentication priority dot1x mab |
|
|
authentication port-control auto |
|
|
authentication periodic |
Re-authenticate periodically |
|
authentication timer reauthenticate server |
|
|
mab |
Allow MAB (MAC Address Bypass) |
|
dot1x pae authenticator |
Enable 802.1x port authentication |
|
dot1x timeout server-timeout 30 |
|
|
dot1x timeout tx-period 10 |
|
|
dot1x max-req 3 |
|
|
dot1x max-reauth-req 10 |
|
|
auto qos voip cisco-phone |
|
|
spanning-tree portfast |
abbreviated STP negotiation for workstations |
|
spanning-tree bpduguard enable |
Prevents people from bolting their own switches to this port. |
|
|
|
|
OPTIONAL: |
|
|
These two commands cover the two cases of “didn’t authenticate” – either the client isn’t 802.1x capable or it is, but failed the authentication. |
|
|
dot1x guest-vlan <vlan number> |
The guest VLAN is where you end up if the client isn’t 802.1x capable (which is the default windows configuration), and if you fail any configured MAC address bypass. |
|
dot1x auth-fail vlan <vlan number> |
If your station is 802.1x capable and fails authentication, then your end up in the “authenticated failed” vlan. |
Again, I did cover off the configuration for both MAC Address authentication and “trust the phones”. Neither is recommended if you are truly trying to secure things. However, in an open office environment with controlled access (visitor signin and locked doors), you can make the case that there are at least some compensating controls to hinder a physical pen-tester or on-premise attacker.
Given how hard the telephony and printer vendors make 802.1x, customers often take these two “shortcuts”. Just be sure that everyone knows what they’re giving up when they go there!
Do you have any success stories (or "down in flames" stories) of 802.1x authentication projects you've seen? Please, share using our comment form!
===============
Rob VandenBrink
rob <at> coherentsecurity.com



Comments
Thanks
Bill
Anonymous
Jul 18th 2019
5 years ago
A PDF Document would be great :)
Anonymous
Jul 18th 2019
5 years ago
Yeah so, I remember helping with a 802.1x implementation at a small office a number of years back. I remember it being fairly tedius/time consuming to get done. The one memory that really stands out was a few old HP printers that we simply could not get to authenticate. Other than that, it worked well, allowing us to check off another important box in our compliance list. BTW - The mention of PAP brings back memories of dial-up days, i.e., PAP/CHAP ;-)
Anonymous
Jul 19th 2019
5 years ago