Targeting VoIP: Increase in SIP Connections on UDP port 5060
We observed an increase on UDP connections that use UDP port 5060. This port is typically used for VoIP connections using the SIP protocol. The activity is indicative of attempts to locate weakly-configured IP PBX system, probably to brute-force SIP passwords. Once the attacker has access to the account, they may use it to make or resell unauthorized calls. The attacker may also use the access to conduct a voice phishing (vishing) campaign.
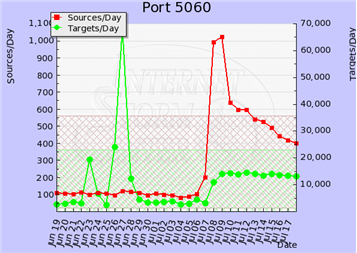
We observed a similar up-tick a few months ago. At the time, the activity was attributed to SIP brute-forcing that probably originated from systems running in Amazon's EC2 cloud.
As described on the Digium blog, publicly-accessible SIP systems are seeing large numbers of brute-force attacks. Systems with weak SIP credentials will be compromised, similarly to how email accounts can be compromised by guessing the credentials "The significant difference is that when someone takes over a SIP platform to make outbound calls, there is usually a direct monetary cost, which gets people’s attention very quickly."
One way to review your SIP exposure is to use the free SIPVicious toolkit. Interestingly, SIPVicious now includes a tool for crashing unauthorized SIPVicious scans.
A few security recommendations for those using the popular Asterisk IP PBX tool:
Thanks to Adam Fathauer and Thomas B. Rücker for sharing the details of some of the malicious acrivities with us! Also, thanks to ISC handler Donals Smith for his insights on this topic.
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches how to analyze and combat at SANS Institute. You can find him on Twitter.



Comments
http://bit.ly/bRFNCr
Regards
eromang
Jul 19th 2010
1 decade ago
Frank
Jul 19th 2010
1 decade ago
The traffic looks much like this:
4.167702 125.88.104.106 -> A.B.251.96 SIP Request: OPTIONS sip:100@A.B.251.96
4.270501 218.249.87.134 -> A.B.177.156 SIP Request: OPTIONS sip:100@A.B.177.156
4.277701 221.231.150.67 -> A.B.146.16 SIP Request: OPTIONS sip:100@A.B.146.16
4.341854 61.50.220.70 -> A.B.113.119 SIP Request: OPTIONS sip:100@A.B.113.119
4.357409 61.233.9.12 -> A.B.76.31 SIP Request: OPTIONS sip:100@A.B.76.31
Jens
Jul 20th 2010
1 decade ago