Sigcheck and virustotal-search
In my last diary entry I mentioned offline use of Sysinternal tools with my tool virustotal-search.
So you want to use sigcheck but you can't connect the machine to the Internet. Then you can use sigcheck's option -h to calculate cryptographic hashes of the files it checks, and option -c to produce a CSV output (-ct for CSV with a tab separator). If you want, you can limit sigcheck's scanning to executable files only with option -e.
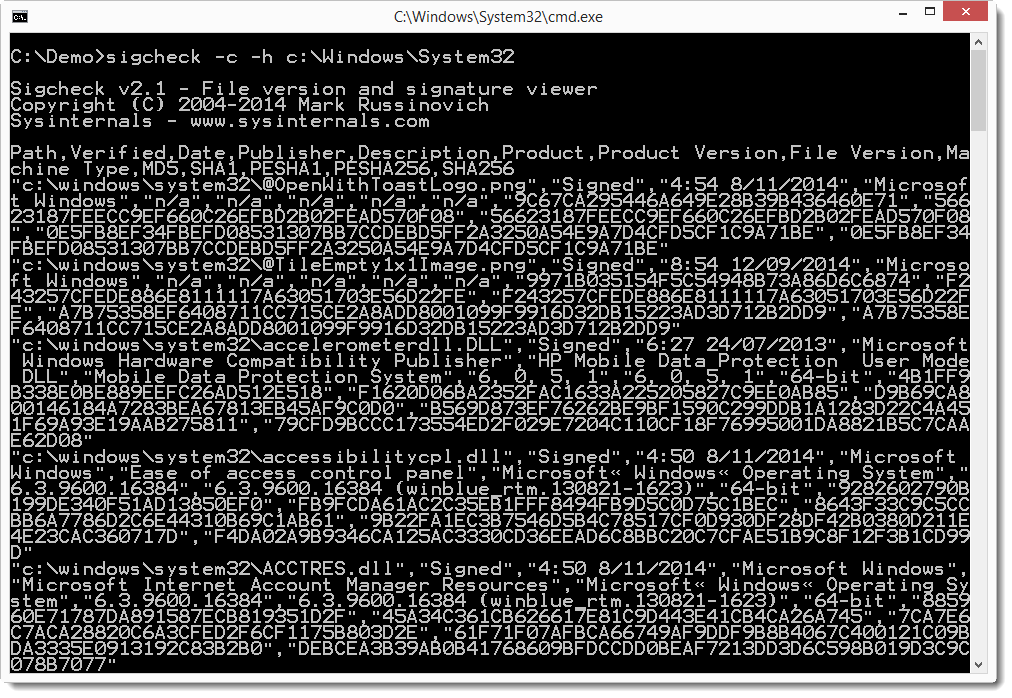
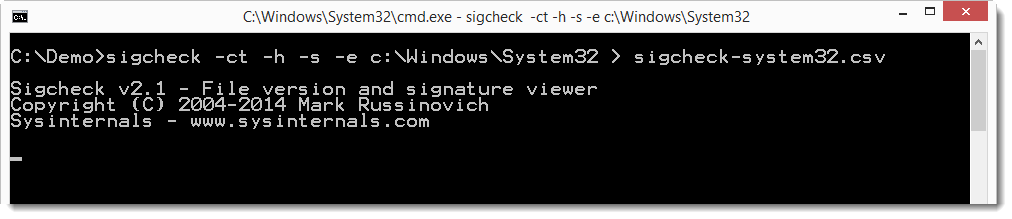
To extract a unique list of MD5 hashes, you can use this pipe of awk, tail, sed and sort (for a tab separated CSV file):
awk -F '\t' '{print $10}' sigcheck-system32.csv | tail -n +2 | sed 's/"//g' | sort -u
And then you can use virustotal-search to submit the hashes.
If you suspect the machine is infected with malware that has rootkit features, then don't boot from the suspect disk, but mount the disk on another machine or boot from a Live CD and use sigcheck to scan the disk.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments
thought i'd share it :)
Anonymous
Aug 6th 2015
9 years ago
Anonymous
Aug 6th 2015
9 years ago
Certainly sigcheck is a great little tool, but for those wanting to keep it all powershell all the time, here's something that can augment checking executables:
This link:
https://etechgoodness.wordpress.com/2014/12/11/powershell-determine-if-an-exe-is-32-or-64-bit-and-other-tricks/
Describes this Gallery download:
https://gallery.technet.microsoft.com/scriptcenter/Identify-16-bit-32-bit-and-522eae75
That, combined with "get-childitem -file -recurse" and get-filehash should yield what's wanted.
I'll have to see if I can generalize this to simply detecting whether or not a file is an executable.
Kurt
Anonymous
Aug 6th 2015
9 years ago