Sage 2.0 Ransomware
Introduction
On Friday 2017-01-20, I checked a malicious spam (malspam) campaign that normally distributes Cerber ransomware. That Friday it delivered ransomware I'd never seen before called "Sage." More specifically, it was "Sage 2.0."
Shown above: It's always fun to find ransomawre that's not Cerber or Locky.
Sage is yet another family of ransomware in an already crowded field. It was noted on BleepingComputer forums back in December 2016 [1, 2], and Sage is a variant of CryLocker [3]. Unfortunately, I can't find an in-depth write-up on Sage that I like. With that in mind, this diary examines Sage 2.0.
The malspam
Emails from this particular campaign generally have no subject lines, and they always have no message text. The only content is a zip attachment containing a Word document with a malicious macro that downloads and installs ransomware. Sometimes, I'll see a .js file instead of a Word document, but it does the same thing.

Shown above: Data from a spreadsheet tracking the malspam (1 of 3).
Often, the recipient's name is part of the attachment's file name. I replace those names with [recipient] before I share any info. A more interesting fact is the attachments are often double-zipped. They contain another zip archive before you get to the Word document or .js file.
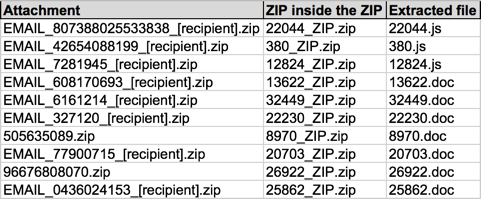
Shown above: Data from a spreadsheet tracking the malspam (2 of 3).
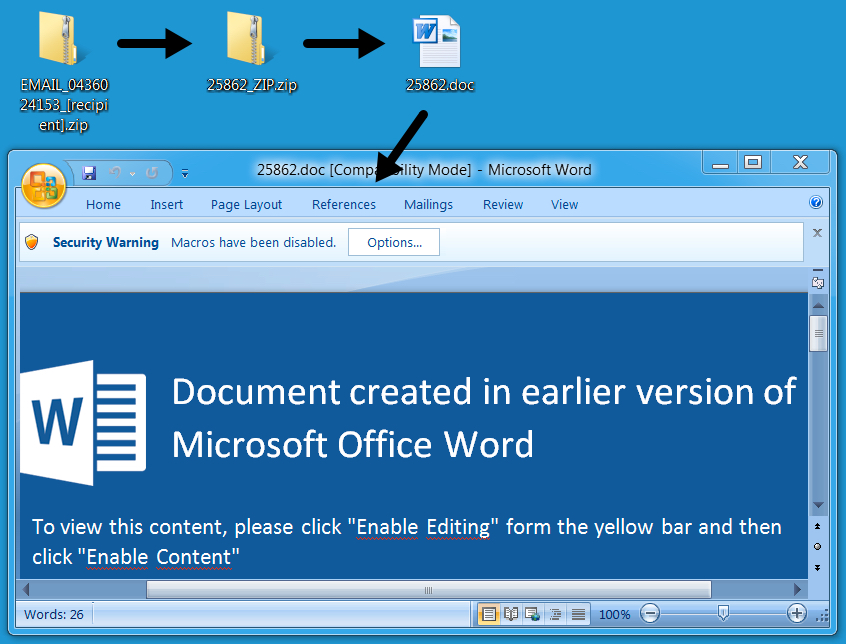
Shown above: Example of a Word document with a malicious macro.
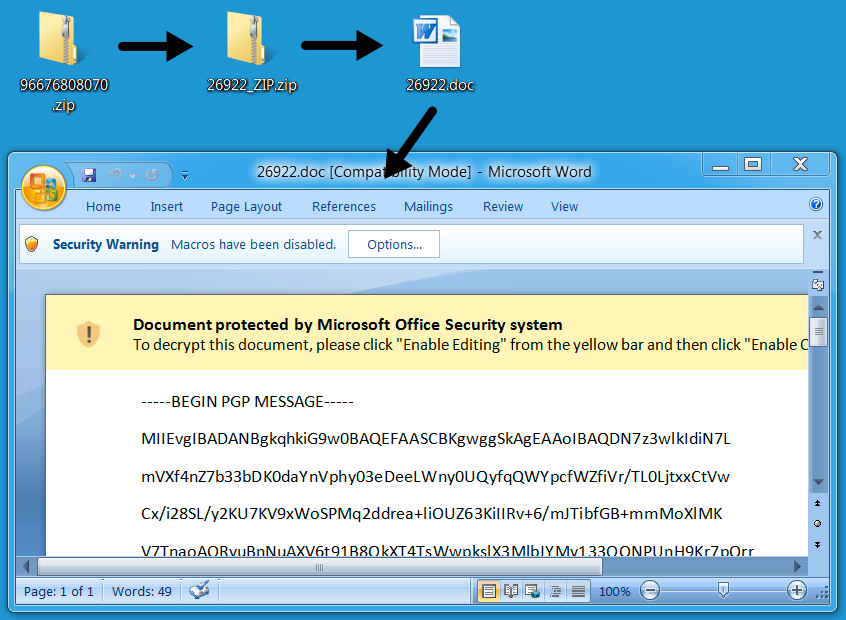
Shown above: Another example of the Word document with a malicious macro.
The Word document macros or .js files are designed to download and install ransomware. In most cases on Friday, the ransomware was Sage 2.0.
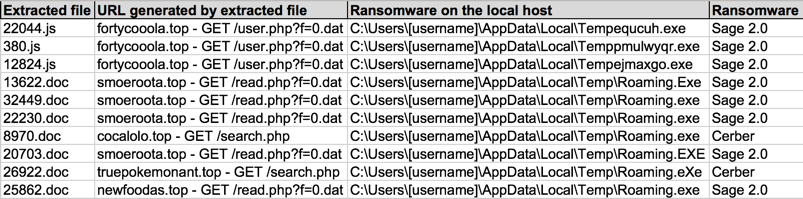
Shown above: Data from a spreadsheet tracking the malspam (3 of 3), mostly Sage 2.0.
The infected host
Under default settings, an infected Windows 7 host will present a UAC window before Sage continues any further. It keeps appearing until you click yes.
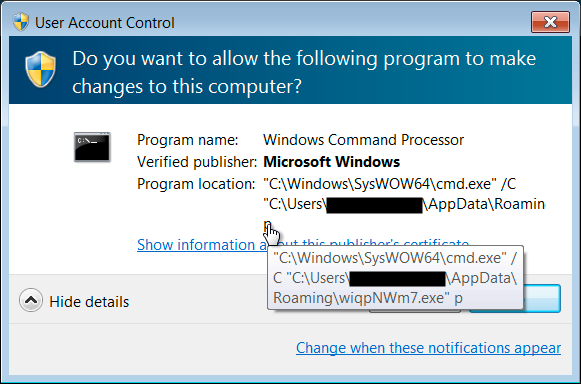
Shown above: UAC pop-up caused by Sage.
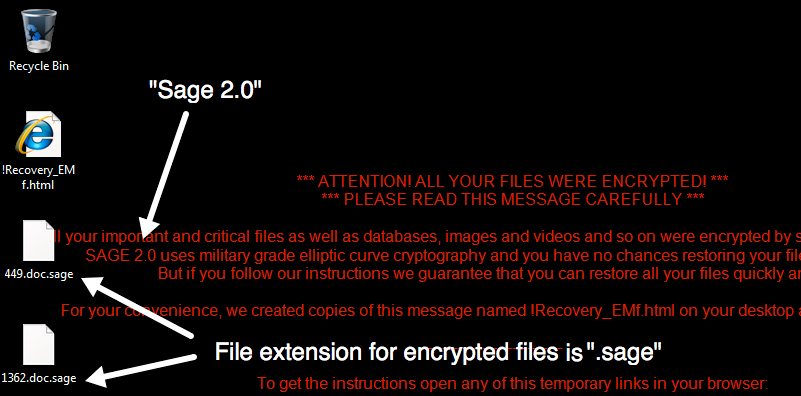
The infected Windows host has an image of the decryption instructions as the desktop background. There's also an HTML file with the same instructions dropped to the desktop. The same HTML file is also dropped to any directory with encrypted files. ".sage" is the suffix for all encrypted files.
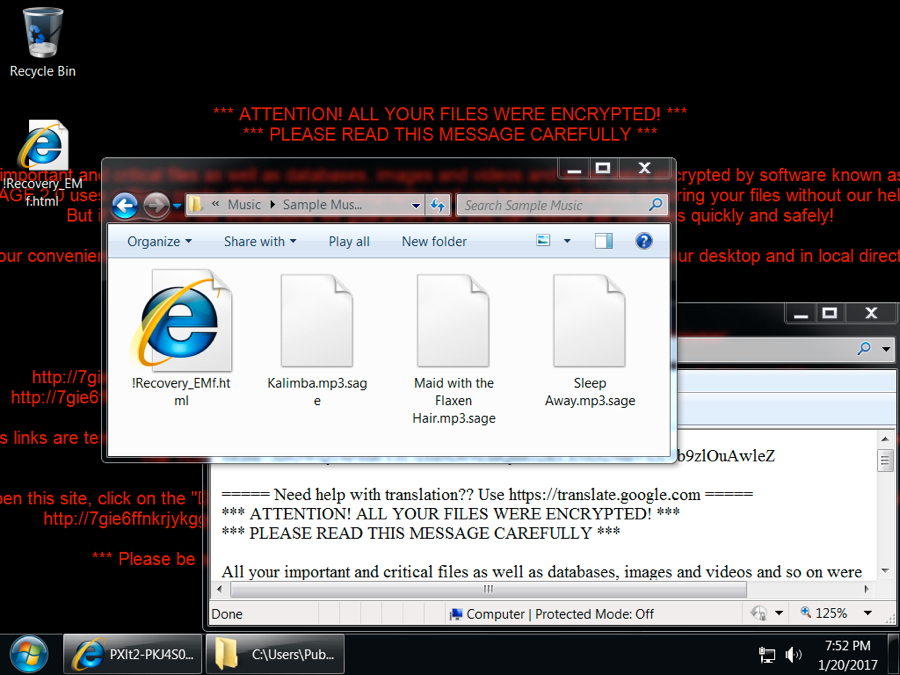
Shown above: Desktop of an infected Windows host.
Sage ransomware is kept persistent by a scheduled task, and it's stored as an executable in the user's AppData\Roaming directory.
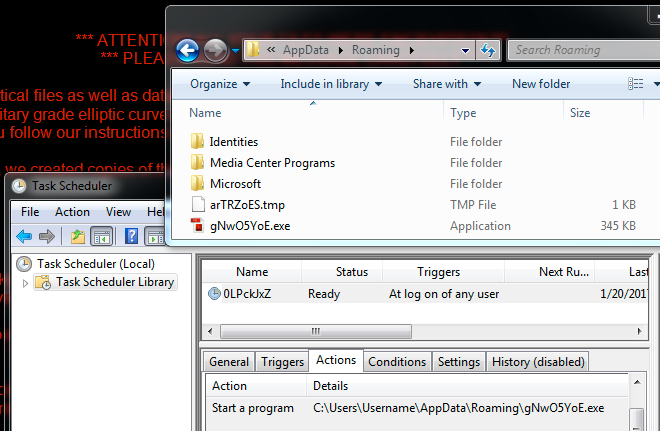
Shown above: Sage ransomware and it's scheduled task for persistence.
Following the decryption instructions should take you to a Tor-based domain with a decryptor screen. On Friday, the cost to decrypt the files was $2,000 US dollars (or 2.22188 bitcoin).
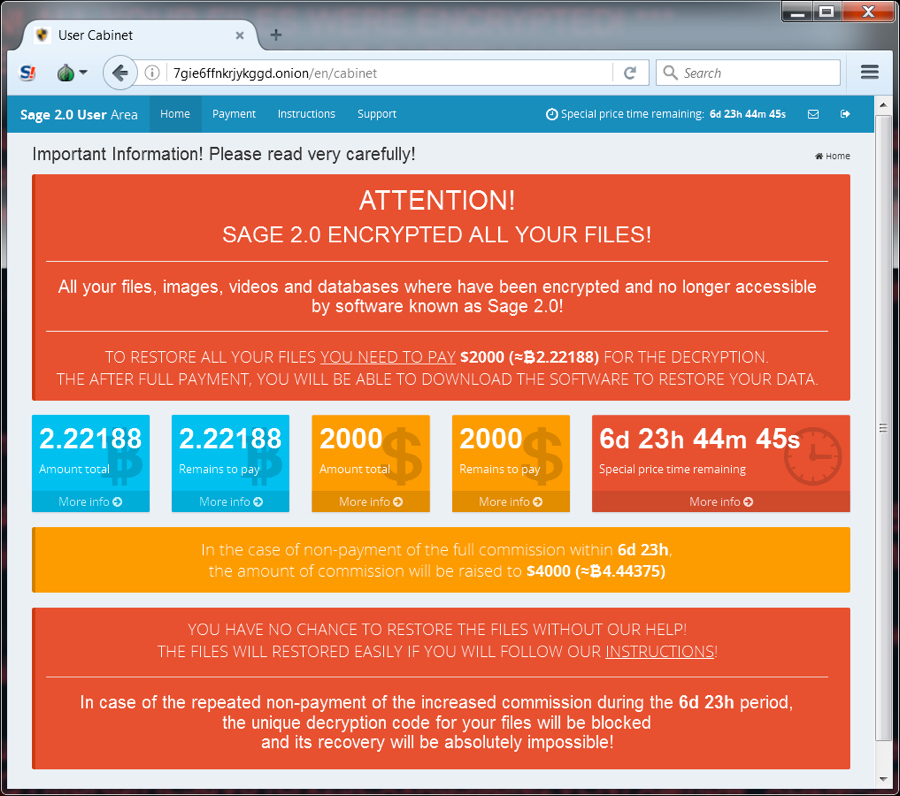
Shown above: The Sage 2.0 decryptor.
Sage 2.0 traffic
Sage ransomware generates post-infection traffic. In the image below, an initial HTTP GET request to smoeroota.top was caused by a .js file retrieving the ransomware. The remaining HTTP POST requests are callback traffic generated by Sage 2.0 from the infected Windows host.
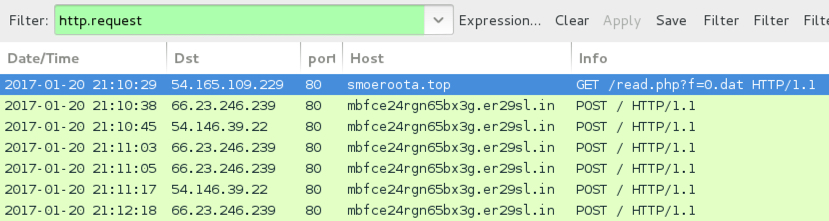
Shown above: Screenshot of the infection traffic, filtered in Wireshark.
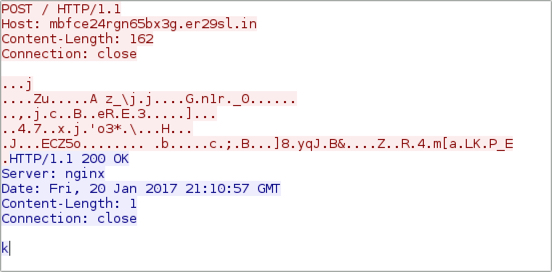
Shown above: TCP stream of an HTTP request for the post-infection traffic.
When the callback domains for Sage didn't resolve in DNS, the infected host sent UDP packets sent to over 7,000 IP addresses. I think this could be UDP-based peer-to-peer (P2P) traffic, and it appears to be somehow encoded or encrypted. BleepingComputer's September 2016 write-up on CryLocker shows the same type of UDP post-infection traffic, but CryLocker's traffic was not encrypted [4].
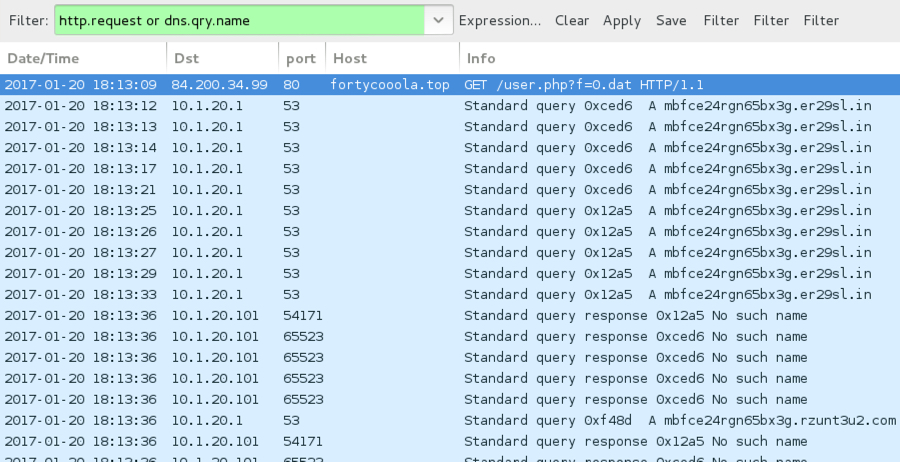
Shown above: An HTTP request for the Sage 2.0 binary, followed by callback domains not resolving in DNS.
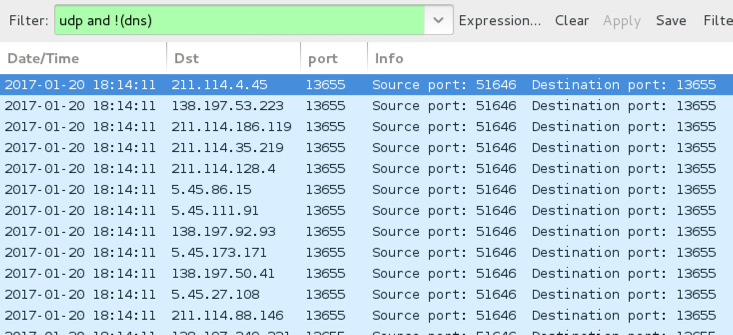
Shown above: UDP traffic caused by Sage 2.0 when callback domains were unavailable.
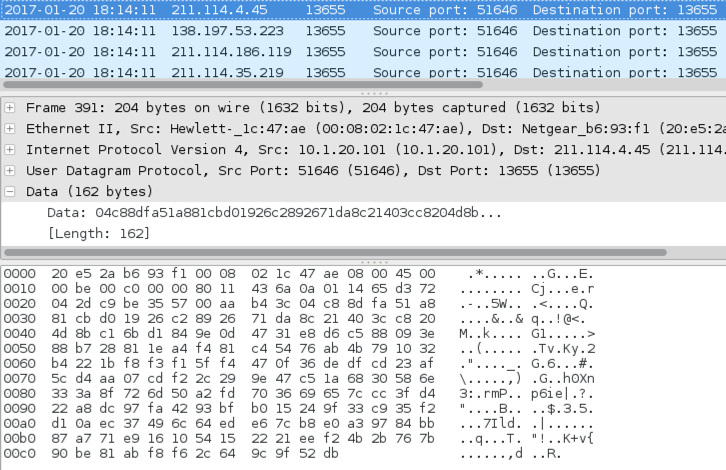
Shown above: Examining one of the UDP packets.
Indicators of Compromise (IOCs)
Below are IOCs for Sage 2.0 from Friday 2017-01-20:
Ransomware downloads caused by Word document macros or .js files:
- 54.165.109.229 port 80 - smoeroota.top - GET /read.php?f=0.dat
- 54.165.109.229 port 80 - newfoodas.top - GET /read.php?f=0.dat
- 84.200.34.99 port 80 - fortycooola.top - GET /user.php?f=0.dat
Post-infection traffic:
- 54.146.39.22 port 80 - mbfce24rgn65bx3g.er29sl.in - POST /
- 66.23.246.239 port 80 - mbfce24rgn65bx3g.er29sl.in - POST /
- mbfce24rgn65bx3g.rzunt3u2.com (DNS queries did not resolve)
- Various IP addresses, UDP port 13655 - possible P2P traffic
Tor-based domains to view the decryption instructions:
- 7gie6ffnkrjykggd.rzunt3u2.com
- 7gie6ffnkrjykggd.er29sl.in
- 7gie6ffnkrjykggd.onion
SHA256 hashes for the Sage 2.0 ransomware samples:
- 0ecf3617c1d3313fdb41729c95215c4d2575b4b11666c1e9341f149d02405c05 (352,328 bytes)
- 362baeb80b854c201c4e7a1cfd3332fd58201e845f6aebe7def05ff0e00bf339 (352,328 bytes)
- 3b4e0460d4a5d876e7e64bb706f7fdbbc6934e2dea7fa06e34ce01de8b78934c (352,328 bytes)
- 8a0a191d055b4b4dd15c66bfb9df223b384abb75d4bb438594231788fb556bc2 (352,328 bytes)
- ccd6a495dfb2c5e26cd65e34c9569615428801e01fd89ead8d5ce1e70c680850 (352,328 bytes)
Examples of locations on the infected Windows host where Sage 2.0 was made persistent:
- C:\Users\[username]\AppData\Roaming\gNwO5YoE.exe
- C:\Users\[username]\AppData\Roaming\wiqpNWm7.exe
- NOTE: File names appear to consists 8 random alphabetic characters with an .exe suffix.
Final words
An important note: URLs for the ransomware download will send Cerber one day, but the same URLs can send something like Sage ransomware the next.
I'm not sure how widely-distributed Sage ransomware is. I've only seen it from this one malspam campaign, and I've only seen it one day so far. I'm also not sure how effective this particular campaign is. It seems these emails can easily be blocked, so few end users may have actually seen Sage 2.0.
Still, Sage is another name in the wide variety of existing ransomware families. This illustrates how profitable ransomware remains for cyber criminals.
Pcaps, emails, malware, and artifacts for this diary are available here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://www.bleepingcomputer.com/forums/t/634978/sage-file-sample-extension-sage/
[2] https://www.bleepingcomputer.com/forums/t/634747/sage-ransomware-sage-support-help-topic/
[3] https://www.pcrisk.com/removal-guides/10732-sage-ransomware
[4] https://www.bleepingcomputer.com/news/security/the-crylocker-ransomware-communicates-using-udp-and-stores-data-on-imgur-com/


Comments
Regards
Anonymous
Jan 23rd 2017
9 years ago
How are you able to differentiate the malspam campaigns and how are you able to say that this campaign normally distributes Cerber ransomware?
The thing in this case is indeed an infection with Cerber at the first day, but executing it now, the payload for Sage 2.0 is downloaded and executed.
The confusion in this thing is perfect because two different variants of Ransomware are distributed the same way ...
Cheers
Anonymous
Jan 23rd 2017
9 years ago
http://malware-traffic-analysis.net/2017/01/04/index2.html
http://malware-traffic-analysis.net/2017/01/05/index2.html
http://malware-traffic-analysis.net/2017/01/09/index2.html
http://malware-traffic-analysis.net/2017/01/13/index4.html
http://malware-traffic-analysis.net/2017/01/17/index.html
http://malware-traffic-analysis.net/2017/01/18/index.html
http://malware-traffic-analysis.net/2017/01/18/index2.html
Ultimately, ransomware is just another form of malware, and it can be distributed the same way any other malware is. This particular malspam campaign has a history of occasionally changing the ransomware sent from the URLs generated by those Word documents or JS file.
Anonymous
Jan 23rd 2017
9 years ago
Anonymous
Jan 23rd 2017
9 years ago
This particular campaign that I'm tracking is not targeted, and it spreads a wide net. It's a botnet-based campaign from what I can tell, and it continues to spew massive amounts of malspam out on a daily basis. Once again, it's not targeting people. It's only using publicly-known email addresses that somehow get circulated on spammers' lists.
Sorry I can't be of more help.
Anonymous
Jan 23rd 2017
9 years ago
Anonymous
Jan 24th 2017
9 years ago
Thanks!
Cmlbalhll
Anonymous
Feb 3rd 2017
9 years ago
Anonymous
Feb 13th 2017
9 years ago
Anonymous
May 2nd 2017
8 years ago