Retrieving malware over Tor on Windows
I found an easier way to retrieve malware over Tor on Windows, using free open-source software.
Tallow uses Tor and WinDivert to redirect network connections over the Tor network.
After starting Tallow, press the Tor button:
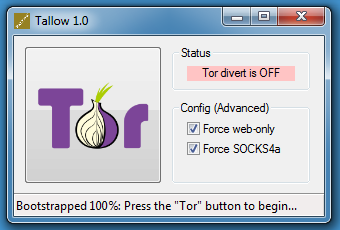
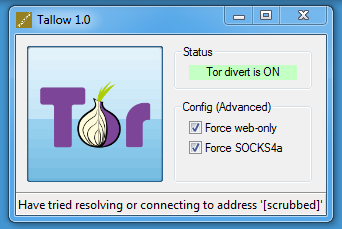
Then you can use wget on Windows:
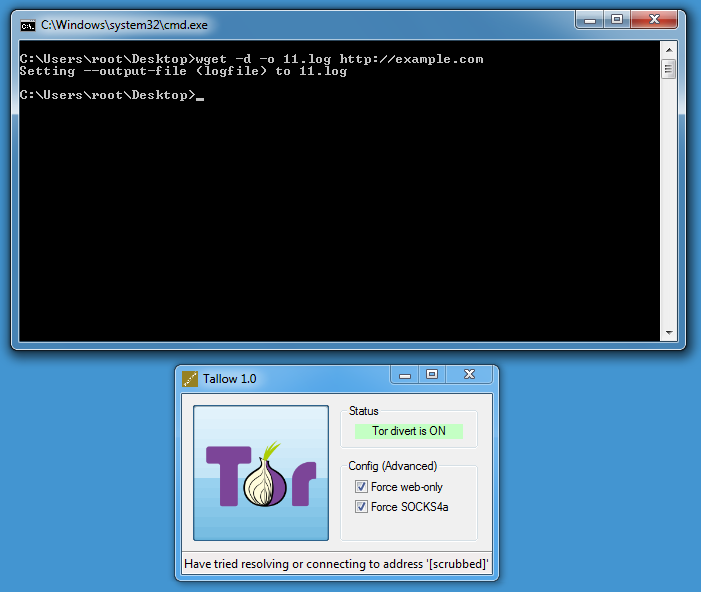
DEBUG output created by Wget 1.11.4 on Windows-MSVC.
--2018-02-25 23:56:22-- http://example.com/
Resolving example.com... seconds 0.00, 44.223.23.63
Caching example.com => 44.223.23.63
Connecting to example.com|44.223.23.63|:80... seconds 0.00, connected.
Created socket 300.
Releasing 0x0142ea78 (new refcount 1).---request begin---
GET / HTTP/1.0User-Agent: Wget/1.11.4
Accept: */*
Host: example.com
Connection: Keep-Alive
---request end---
HTTP request sent, awaiting response...
---response begin---
HTTP/1.0 200 OKCache-Control: max-age=604800
Content-Type: text/html
Date: Sun, 25 Feb 2018 22:56:24 GMT
Etag: "1541025663+gzip+ident"
Expires: Sun, 04 Mar 2018 22:56:24 GMT
Last-Modified: Fri, 09 Aug 2013 23:54:35 GMT
Server: ECS (lga/1386)
Vary: Accept-Encoding
X-Cache: HIT
Content-Length: 1270
Connection: keep-alive
---response end---
200 OK
Registered socket 300 for persistent reuse.
Length: 1270 (1.2K) [text/html]
Saving to: `index.html'0K . 100% 32.1M=0s
2018-02-25 23:56:23 (32.1 MB/s) - `index.html' saved [1270/1270]
Onion services can be accessed too:
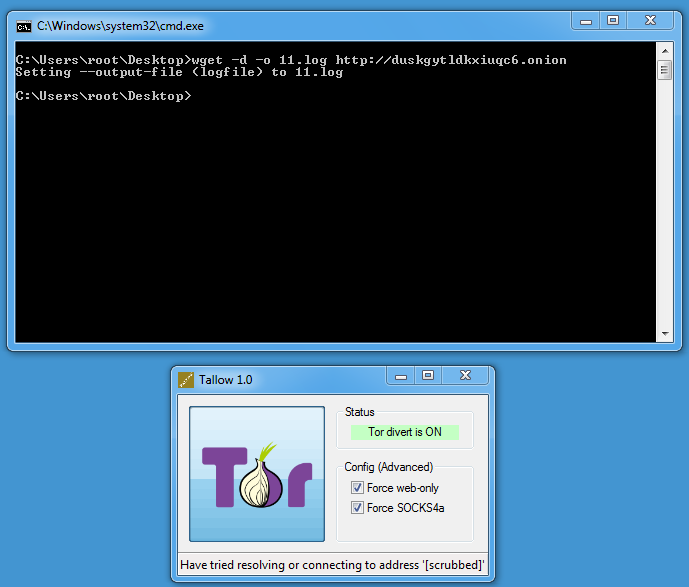
By default, Tallow only allows TCP connections on port 80 and 443 (Force web-only). Disable this toggle if you need to access other ports.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments
Only fools use a completely outdated and vulnerable version of wget to retrieve malware.
Complete fools let their vulnerable version of wget send its version per "User-Agent:" to servers which may take advantage of its vulnerabilities.
Anonymous
Feb 26th 2018
7 years ago
Anonymous
Feb 26th 2018
7 years ago
Anonymous
Feb 26th 2018
7 years ago
https://reqrypt.org/download/TallowBundle-1.0-install.exe ??????
Anonymous
Feb 26th 2018
7 years ago
https://reqrypt.org/download/TallowBundle-1.0-install.exe ??????[/quote]
Not "any", but "many" explanations:
1. the executable installer is vulnerable, it allows escalation of privilege;
2. the PE checksum stored in the header differs from the actual checksum;
3. no authenticode signature, so no proof of authenticity possible.
Stay far away from such crap!
Anonymous
Feb 27th 2018
7 years ago
Except for complete idiots straw does not replace an argument; not even a full-grown strawmen does, although these are routinely used to brake camels backs.
Anonymous
Feb 28th 2018
7 years ago
I'm pretty sure most people coding malware sites are one of several things:
A. Lazy
B. Not as smart as you give them credit for.
C. 85% cut and paste
D. Did I say lazy?
Yes they are mainly just that lazy. Hardly doubt that the sheeple they are hoarding in, or planning on give them cause to write a header user agent directive and/or subroutine
Besides.... From https://www.gnu.org/software/wget/manual/wget.html
‘-U agent-string’
‘--user-agent=agent-string’
Identify as agent-string to the HTTP server.
The HTTP protocol allows the clients to identify themselves using a User-Agent header field. This enables distinguishing the WWW software, usually for statistical purposes or for tracing of protocol violations. Wget normally identifies as ‘Wget/version’, version being the current version number of Wget.
However, some sites have been known to impose the policy of tailoring the output according to the User-Agent-supplied information. While this is not such a bad idea in theory, it has been abused by servers denying information to clients other than (historically) Netscape or, more frequently, Microsoft Internet Explorer. This option allows you to change the User-Agent line issued by Wget. Use of this option is discouraged, unless you really know what you are doing.
Specifying empty user agent with ‘--user-agent=""’ instructs Wget not to send the User-Agent header in HTTP requests.
Anonymous
Mar 1st 2018
7 years ago