ProxyShell - how many Exchange servers are affected and where are they?
Since the bad guys have started to actively look[1] for machines affected by vulnerabilities that enable one to perform the ProxyShell attack (unauthenticated RCE on an on-premise Exchange server) and since Shodan now detects machines affected by these vulnerabilities as well, I thought it might be interesting to take a look at some of the current Shodan data.
But to put things into context, let us first take a quick look at ProxyShell itself. The attack exploits 3 chained vulnerabilities (CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207) and was originally presented by Orange Tsai at this year’s Pwn2Own. During a talk at BlackHat last week, Orange Tsai disclosed further information about the attack[2], which was shortly followed by the publication of additional technical information about it by other researchers who managed to recreate it[3]. After that, it didn’t take the bad guys long to start looking for vulnerable machines.
Since the attack is not dependent on any memory corruption issues, but only on logic bugs in Exchange components[4], one can expect that most threat actors “worthy” of that title would not have much difficulties in successfully executing it, given the aforementioned availability of information about it. On the other hand, patches for all of the vulnerabilities in question have been released by Microsoft in May[5] and July[6,7] and chances are that most organizations that take security at least somewhat seriously have already applied the patches.
However, considering that Shodan can now give us data about the number of systems that are still affected by the vulnerabilities, we don’t have to depend on guesses... Or – rather – we don’t have to depend on them too much.
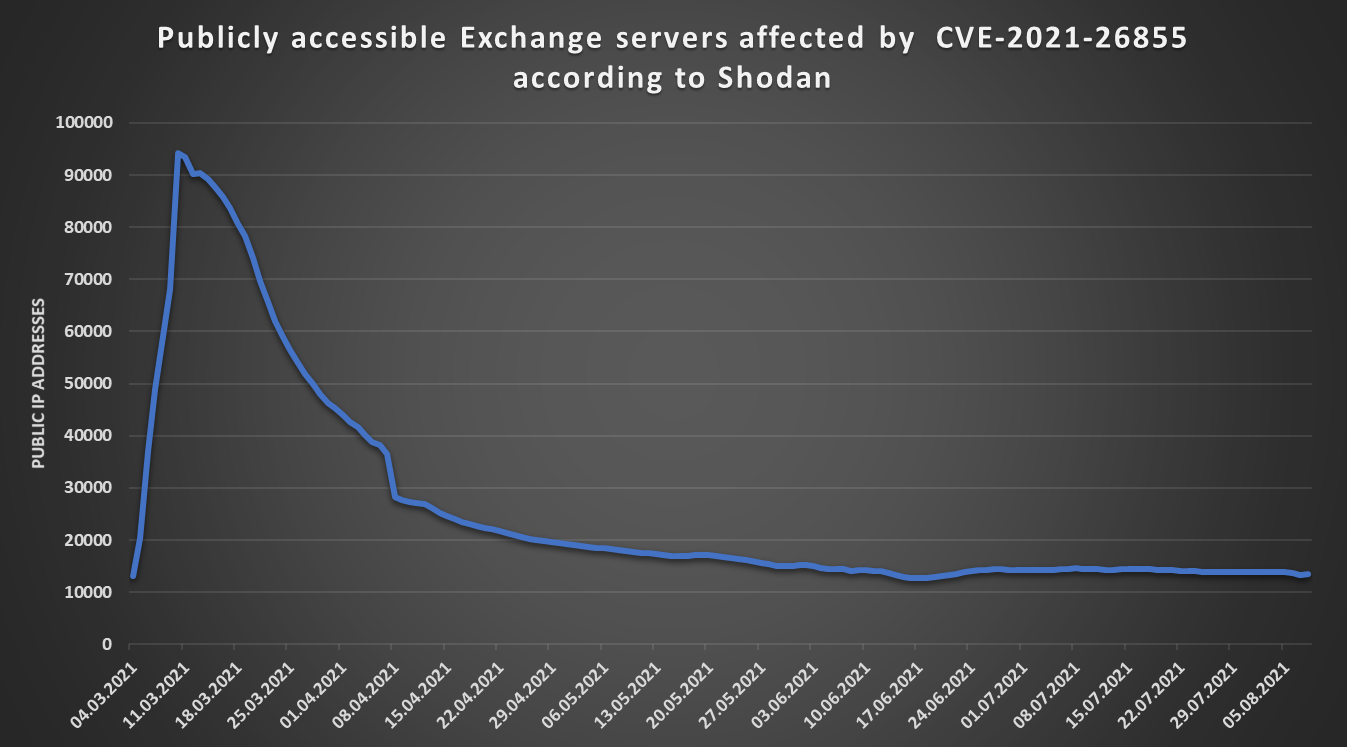
Since the detections for the ProxyShell vulnerabilities are fairly new, Shodan probably didn’t yet have a chance to go through the entire internet with them and one can therefore expect that the number of vulnerable systems it detects will rise sharply in the coming days, as it was when Shodan first started detecting the ProxyLogon vulnerability (CVE-2021-26855).
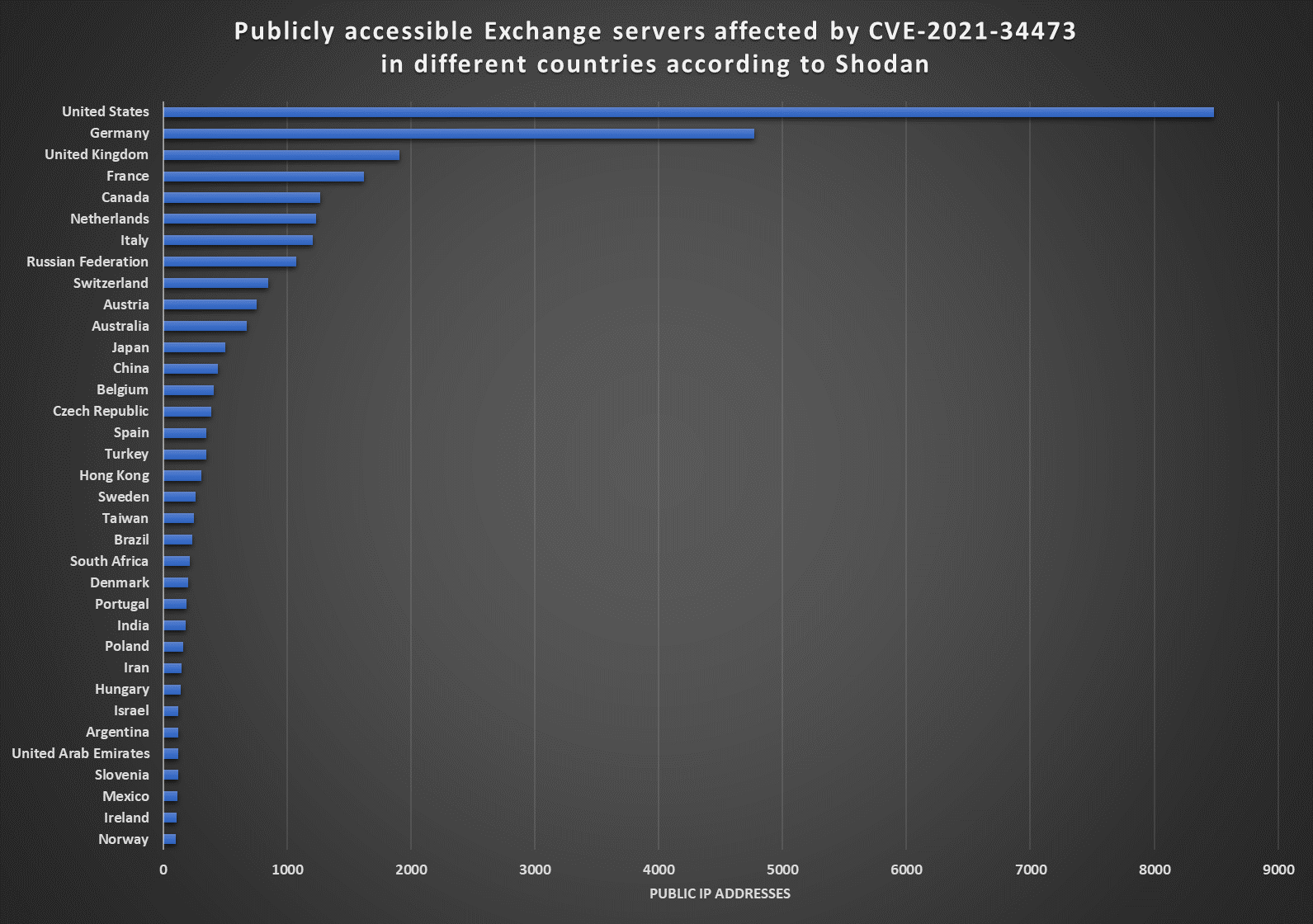
In any case, at the time of writing, Shodan detects about 30 400 machines affected by the three vulnerabilities. You may see all countries that have more than 100 detections of CVE-2021-34473 at this point in the following chart.
We’ll have to see whether the aforementioned prediction of mine turns true and whether there will be any further significant increases in the numbers. If so, I’ll try to let you know in some future diary…
[1] https://www.bleepingcomputer.com/news/microsoft/microsoft-exchange-servers-scanned-for-proxyshell-vulnerability-patch-now/
[2] https://www.blackhat.com/us-21/briefings/schedule/index.html#proxylogon-is-just-the-tip-of-the-iceberg-a-new-attack-surface-on-microsoft-exchange-server-23442
[3] https://peterjson.medium.com/reproducing-the-proxyshell-pwn2own-exploit-49743a4ea9a1
[4] https://blog.orange.tw/2021/08/proxylogon-a-new-attack-surface-on-ms-exchange-part-1.html
[5] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31207
[6] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34473
[7] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523



Comments