Password Protected Malicious Excel Files
We've been seeing quite some malicious Excel files with Excel 4 macros lately.
A variant we are observing now, is password protected Excel 4 maldocs, using the binary file format .xls (and not OOXML, .xlsm).
Password protected .xls files are not completely encrypted. Simply put: it's the data of the BIFF records that is encrypted, but not the record headers themselves.
A password protected .xls file has a FILEPASS record at the beginning of the workbook stream:
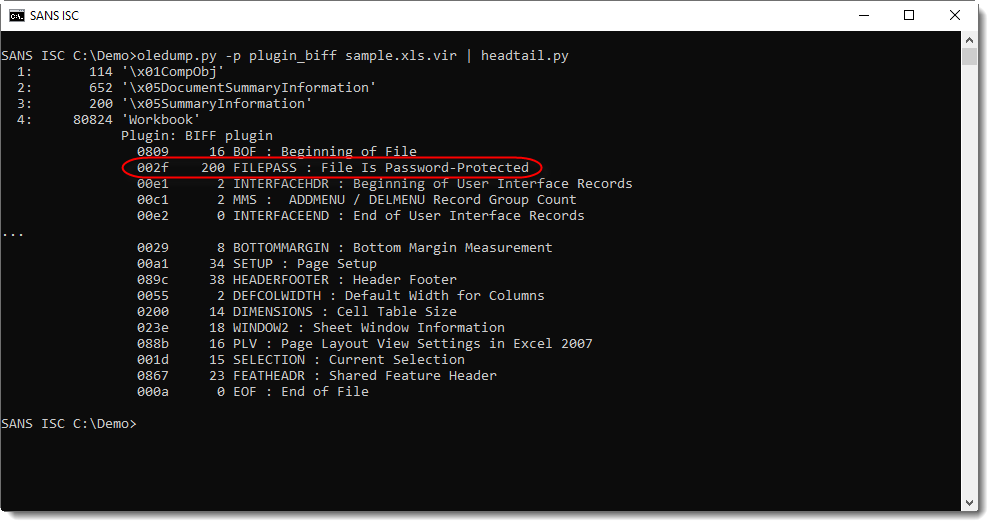
I updated my BIFF plugin (plugin_biff.py) to issue a warning when using option -x to filter for Excel 4 macros: since the data of the BOUNDSHEET records is encrypted, we can no longer detect that a sheet is an Excel 4 macro sheet or another type.
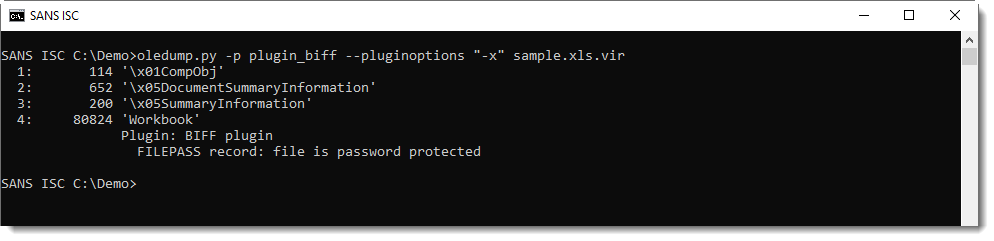
So when you see that an Excel sheet is password protected, you need to decrypt it to perform further analysis:
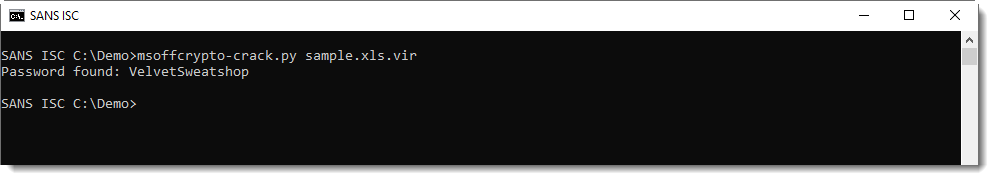
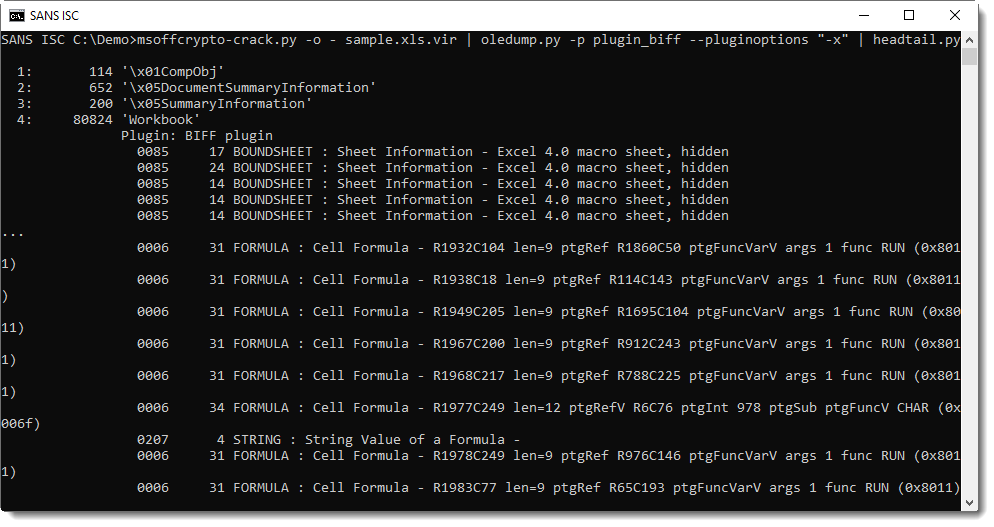
As the password is VelvetSweatshop, the user does not have to enter a password to decrypt the workbook upon opening.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments