OAUTH phishing against Google Docs ? beware!
We got several reports (thanks to Seren Thompson, Tahir Khan and Harry Vann) about OAUTH phishing attacks against Google users. The phishing attack arrives, of course, as an e-mail where it appears that a user (potentially even one on your contact list, so it looks very legitimate) has shared a document.
An image of such an e-mail is shown below:
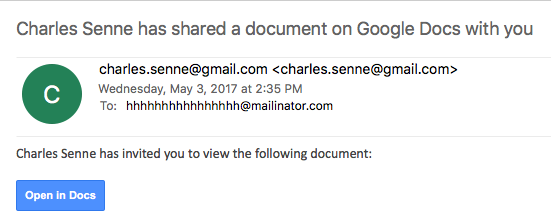
If you click on the link (Open in Docs), you will be redirected to the OAUTH2 service on accounts.google.com – the target URL will look like this:
hxxs://accounts.google.com/o/oauth2/auth?client_id=1535050614-8i934kb9l0snc0iocqb0iv27lli0r858.apps.googleusercontent.com&scope=https%3A%2F%2Fmail.google.com%2F+https%3A%2F%2Fwww.googleapis.com%2Fauth%2Fcontacts&immediate=false&include_granted_scopes=true&response_type=token&redirect_uri=hxxps%3A%2F%2Fgoogledocs.g-docs.win%2Fg.php&customparam=customparam
In browser, this is what you get:
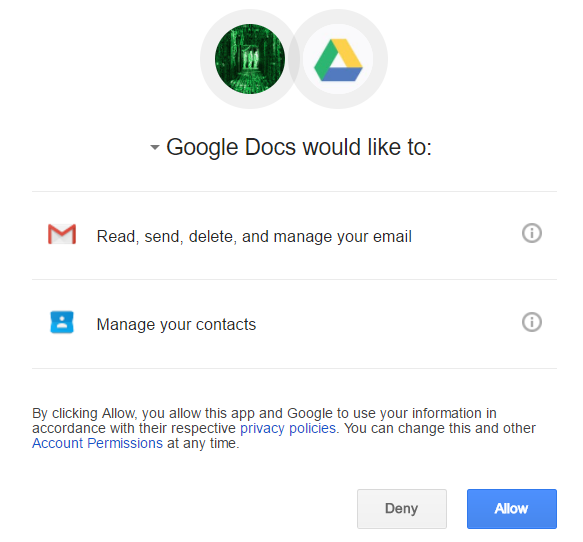
As you can see, it appears as Google Docs wants full access to my Gmail as well as my contacts. Of course, this is not real Google Docs – the attacker has simply named his “application” Google Docs – this can be verified by clicking on the Google Docs text where the real web site behind this and developer info is shown:
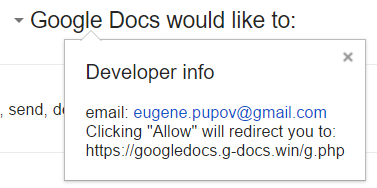
Obviously, once you allow access it is game over - the attacker probably uses the phishied Gmail account to further distribute phishing e-mails - we'll see if we can get more details.
So far at least the following domains are included:
googledocs.g-docs.win
googledocs.g-docs.pro
The domains are definitely malicious – the URL leads to jsserver.info where a fake alert that the computer is infected is shown.
UPDATE:
There are more domains - they all just change the TLD's for googledocs.g-docs.X or googledocs.docscloud.X. Most of them (if not all) appear to have been taken down (thanks @Jofo).
It also appears that Google has reacted quickly and are now recognizing e-mails containing malicious (phishing) URL's so the message "Be careful with this message. Similar messages were used to steal people's personal information. Unless you trust the sender, don't click links or reply with personal information." will be shown when such an e-mail is opened.
Finally, if you accidentally clicked on "Allow", go to https://myaccount.google.com/u/0/permissions?pli=1 to revoke permissions.
| Web App Penetration Testing and Ethical Hacking | Washington | Jul 14th - Jul 19th 2025 |



Comments
Anonymous
May 3rd 2017
8 years ago
Anonymous
May 3rd 2017
8 years ago
When a user enters their information on the OAUTH phishing page and compromises their account - the malicious actor's script then sends the OAUTH phishing page email from the newly acquired account to all of the account's contacts. Thus, this script is spreading based on each account compromised, appearing to be coming from a known source - leads to a more effective click through rate.
Why harvest hundreds of thousands of email accounts when you can just compromise an account and start a "Ponzi" scheme type of "Contacts" abuse.
@TheSecureStoic
Traven
Anonymous
May 3rd 2017
8 years ago
I'm surprised Google doesn't have restricted words or phrases for apps; calling it "Google Docs" probably fooled a lot of people into accepting the permissions.
Anonymous
May 3rd 2017
8 years ago
Anonymous
May 3rd 2017
8 years ago
I was a young admin when the Iloveyou virus was spreading like wild fire across the internet. A simple vb script that anyone with a little training could have made demonstrated that Microsoft's handy scripting language and application api could be easily used for evil.
Anonymous
May 4th 2017
8 years ago