Nim Strings
On Tuesday's Stormcast, Johannes talked about malware written in the Nim Programming language.
Internally, strings in the Nim programming language are stored inside a structure (STRING_LITERAL) that consists of 2 integers followed by the string.
Both integers represent the length of the string, although the second integer has one bit set to indicate it is a string literal.
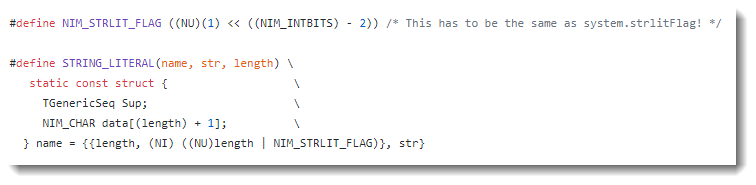
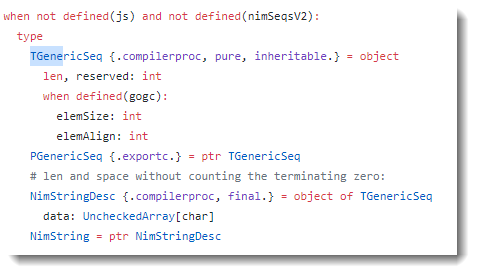
Here is an example of a program I wrote and compiled to a 32-bit PE file:
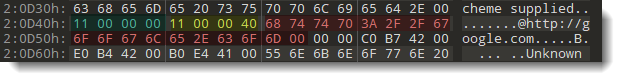
In red is the string itself (17 bytes long, 0x11). Green is the first integer: the length of the string (0x00000011) encoded as a little-endian 32-bit integer (0x11000000). Yellow is the second integer: the length of the string encoded as a little-endian 32-bit integer with the 3rd most-significant bit set (0x00000011 + x40000000 -> 0x11000040).
I wrote a Python script to extract these strings. It's beta: I still have to decided if and how to integrate this in my strings.py tool).
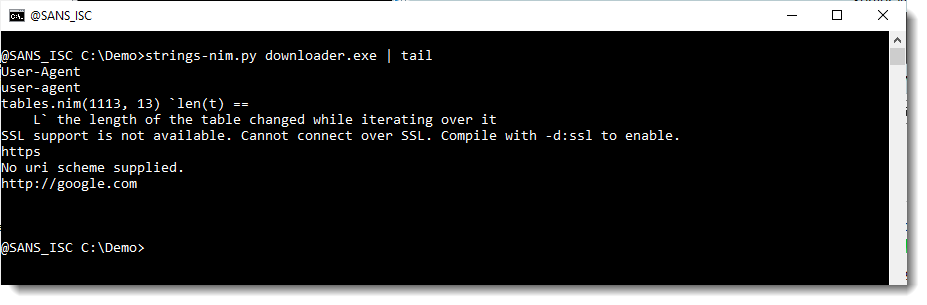
Unlike the classic tool strings, this tool will also extract strings that contain non-printable characters.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com

Comments