Mr Jones wants you to appear in court!
Wondering what the Costco / Walmart malware (yesterday's diary) was up to, we ran it in a lab environment. It happily connected to its Command&Control (C&C), and soon after started spamming the next round of bait. The upcoming scam email apparently looks like this:
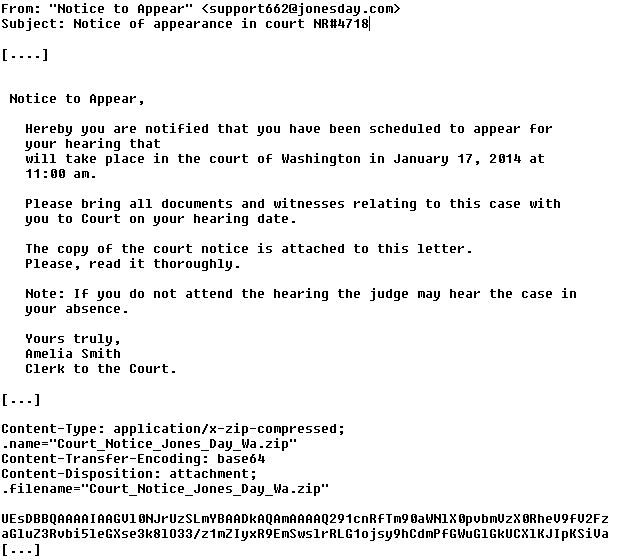
and it comes complete with an EXE, named something like "Court_Notice_Jones_Day_Washington.exe", current MD5 84fae8803a2fcba2d5f868644cb55dd6 (Virustotal)
The C&C of the original Costco sample was at 89.32.145.12:443 and 188.40.130.18:8080. A supplemental binary was pulled from 50.31.146.101:8080. If you have additional information on this scam or yesterday's Costco/Walmart version, please share in the comments below. Thanks to Francis Trudeau of Emerging Threats for help with the analysis and gathering the C&C traffic.


Comments
Asprox shifted to spamming with malware attachments about halfway thru December.
http://techhelplist.com/index.php/tech-tutorials/41-misc/438-asprox-botnet-trojan-run-malware-spamming-1
Aside from the Asprox IP addresses:
the consistency in Envelope headers, From headers, and HELO, as apposed to the aexp-nacha-whatever from Cutwails. The kuluoz/dofoiol trojans. The Message-ID header has the netbios name of the infected windows computer, giving that touch of personal interest.
The http get /hexadecimal hash and POST encrypted key.bin and data.bin.
http://stopmalvertising.com/malware-reports/analysis-of-asprox-and-its-new-encryption-scheme.html
The beauty contest winner "my CV" emails and these fake JonesDay.com emails have another commonality --
http://techhelplist.com/index.php/spam-list/437-please-look-my-cv-virus
http://techhelplist.com/index.php/spam-list/439-hearing-of-your-case-in-court-nr-virus
The wholesome all-American 50's white-woman names:
Ruth Tailor
Ruth Mason
Karen Tailor
Alena Mason
Emily Mason
Dorothy Smith
Occasionally you find commonality in Asprox's language: the "you should download it", matter-of-fact style was in several Asprox fake airline emails that came out like 6 months apart.
Anonymous
Dec 24th 2013
1 decade ago
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"ET CURRENT_EVENTS Kuluoz/Asprox Activity Dec 23 2013"; flow:established,to_server; content:!"Referer|3a|"; http_header; pcre:"/^\/[A-Za-z0-9]{8,}+$/U"; content:"User-Agent|3a 20|Mozilla/5.0 (Windows NT 6.1|3b| WOW64|3b| rv|3a|25.0) Gecko/20100101 Firefox/25.0"; http_header; fast_pattern:64,20; content:!"Host|3a|"; http_header; depth:5; pcre:"/^Host\x3a\x20\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}(?:\x3a\d{1,5})\r$/Hmi"; reference:md5,a3e0f51356d48124fba25485d1871b28; reference:url,www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp-asprox-reborn.pdf; classtype:trojan-activity; sid:2017895; rev:2;)
This alerts on the initial call back POST on port 8080:
POST /A5B3CAE4DF83F1B95E128FCD1059612F65094B3160 HTTP/1.1
Accept: */*
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:25.0) Gecko/20100101 Firefox/25.0
Host: 178.18.113.28:8080
Content-Length: 317
Cache-Control: no-cache
Anonymous
Dec 26th 2013
1 decade ago
Here are the relative distributions of each, where the first number is the number of spam samples collected in the Malcovery Security Spam Data Mine. The second column is the domain name used, the third is the MD5 of the .zip attachment, and lastly, in 15 minute increments, the first and last time period in which spam bearing this attachment was seen.
11633 | jonesday.com | 442e746ad1d185dd1683b1aa964f6e56 (2013-12-23 07:45 to 2013-12-23 21:00)
5979 | jonesday.com | 267d9f829ea2e3620ee62c52fcb4ebe9 (2013-12-23 16:30 to 2013-12-24 05:15)
4365 | lw.com | b2f8e5d86d7c50b5017e88527d8ce334 (2013-12-24 07:45 to 2013-12-24 20:00)
142 | lw.com | 76cdb2bad9582d23c1f6f4d868218d6c (2013-12-24 08:00 to 2013-12-24 16:00)
651 | lw.com | 0f0bb7b4f67b3bd90e944fcf7473b9d8 (2013-12-24 14:15 to 2013-12-24 20:00)
3054 | hoganlovells.com | 30336df44c6808175bf4a7c212d3e2f8 (2013-12-25 14:15 to 2013-12-26 03:00)
3236 | hoganlovells.com | f97795c2124f60596eb8faf18307ac35 (2013-12-25 05:15 to 2013-12-25 23:00)
3500 | mwe.com | d181af2b32830119c0538851a8b53af8 (2013-12-26 06:00 to 2013-12-26 16:30)
484 | mwe.com | 7c572385f09773237805a52e2fc106e9 (2013-12-26 12:00 to 2013-12-26 17:15)
samples are available to qualified researchers. More details here:
http://garwarner.blogspot.com/2013/12/asprox-spamming-court-related-malware.html
Gary Warner
[email protected]
www.malcovery.com
Anonymous
Dec 27th 2013
1 decade ago
Current detection is rather abysmal:
https://www.virustotal.com/en/file/ae516b62225b253e2839509d3280540ac575071a19545dc7754e7aef26fb2c86/analysis/1388159409/
Anonymous
Dec 27th 2013
1 decade ago