More Free File Sharing Services Abuse
A few months ago, I wrote a diary about online services used to exfiltrate data[1]. In this diary, I mentioned some well-known services. One of them was catbox.moe[2]. Recently, I found a sample that was trying to download some payload from this website. I performed a quick research and collected more samples!
I collected (and stopped because it was a constant flood!) 612 URLs pointing to direct downloads (hxxps://files[.]catbox[.]moe/xxxxxx). Some where popular and used by multiple samples:
remnux@remnux:~/malwarezoo/catmoe-research$ cat urls.txt | sort | uniq -c | sort -rn| head -10 23 hxxps://files[.]catbox[.]moe/a1z5ds.dll 20 hxxps://files[.]catbox[.]moe/63g8p0.dll 16 hxxps://files[.]catbox[.]moe/h7b4e4.dll 13 hxxps://files[.]catbox[.]moe/mqhwlv.sys 13 hxxps://files[.]catbox[.]moe/j5s1uy.bin 13 hxxps://files[.]catbox[.]moe/3ps4f5.dll 10 hxxps://files[.]catbox[.]moe/5ikx0w.dll 9 hxxps://files[.]catbox[.]moe/l3whjb.wav 9 hxxps://files[.]catbox[.]moe/1z3yes.cmd 7 hxxps://files[.]catbox[.]moe/eaek1u.dll
What are the most popular file types?
remnux@remnux:~/malwarezoo/catmoe-research$ file *| cut -d “:” -f 2 | sort | uniq -c | head -30 55 PE32+ executable (DLL) (GUI) x86-64, for MS Windows 29 PE32+ executable (native) x86-64, for MS Windows 21 ASCII text, with no line terminators 20 PE32+ executable (DLL) (console) x86-64, for MS Windows 20 PE32+ executable (console) x86-64, for MS Windows 11 data 10 RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, mono 48000 Hz 9 DOS batch file, ASCII text, with CRLF line terminators 9 ASCII text, with CRLF line terminators 8 DOS batch file, ASCII text, with very long lines, with CRLF line terminators 5 RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, stereo 44100 Hz 5 RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, mono 44100 Hz 3 Zip archive data, at least v2.0 to extract 3 RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, stereo 48000 Hz 3 ASCII text, with very long lines, with CRLF line terminators 2 RAR archive data, v5 2 PNG image data, 800 x 450, 8-bit/color RGB, non-interlaced 2 PNG image data, 500 x 500, 8-bit/color RGBA, non-interlaced 2 PNG image data, 1080 x 1080, 8-bit/color RGB, non-interlaced 2 PE32+ executable (GUI) x86-64, for MS Windows 2 PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed 2 PE32+ executable (DLL) (EFI application) x86-64, for MS Windows 2 PE32 executable (console) Intel 80386, for MS Windows 2 MS-DOS executable PE32 executable (GUI) Intel 80386, for MS Windows, MZ for MS-DOS 2 JPEG image data, Exif standard 2 ISO Media, MP4 Base Media v1 [IS0 14496-12 2 empty 2 DOS batch file, UTF-8 Unicode text, with CRLF line terminators 2 DOS batch file, ASCII text, with CRLF line terminators, with escape sequences
Note that PE files should NOT be available on catbox.moe:
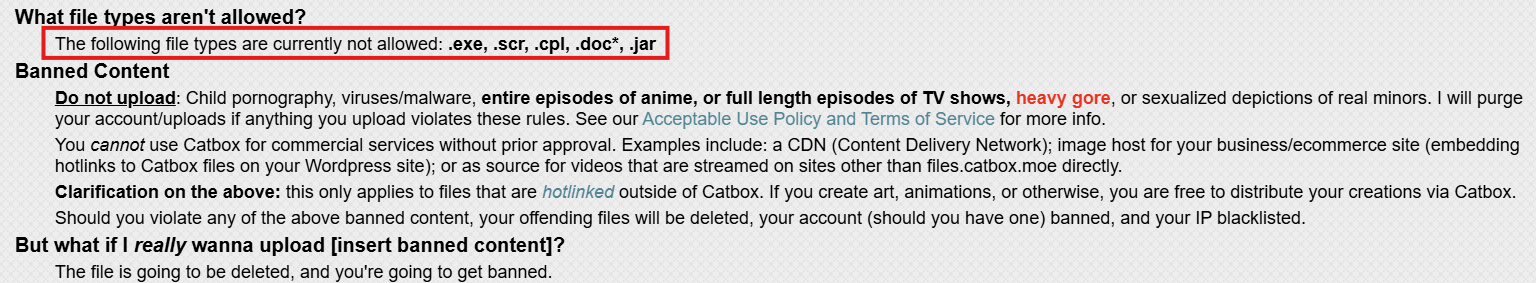
I hope they don't just filter files based on the extension! Conclusion: if you don't use such online services, any traffic to them can be considered as suspicious.
[1] https://isc.sans.edu/diary/Online+Services+Again+Abused+to+Exfiltrate+Data/31862
[2] https://catbox.moe/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments