Malicious Documents: A Bit Of News
This week I saw again a PDF containing a malicious Word document with macros (a downloader).
The PDF contains JavaScript to extract the malicious Word document and launch Word. The user is prompted before this action takes place, but if you want to mitigate this, you can disable JavaScript. If you use Adobe Reader version 15.009.20069 or later, then the extracted Word document is marked with a mark-of-web, regardless if the containing PDF document is marked as such.
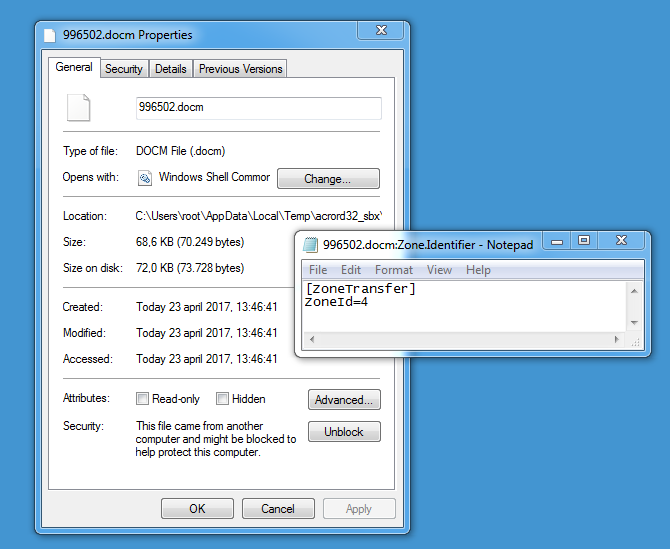
I made a video of the analysis of this document.
There has been a lot of talk about RTF documents exploiting CVE-2017-0199, making Word download and execute an HTML application without requiring any user interaction (except taking the document out of Protected View, depending on the presence of a mark-of-web). And this without VBA macros (RTF does not support VBA macros).
After applying Microsoft's patch for CVE-2017-0199, a downloaded HTA is no longer executed, but it is still downloaded without user interaction. The attention that the RTF auto-update technique received (employed for delivering a CVE-2017-0199 exploit), will certainly stimulate the use of this technique for other purposes, like tracking.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments
Anonymous
Apr 24th 2017
8 years ago
Here is a screenshot of how WordPad behaves after patching:
https://twitter.com/DidierStevens/status/854285408682876929
Anonymous
Apr 24th 2017
8 years ago